Documentation
Duo Authentication for Microsoft Remote Desktop Web and Remote Desktop Gateway on Windows 2016 and Later
Last Updated: January 29th, 2024Contents
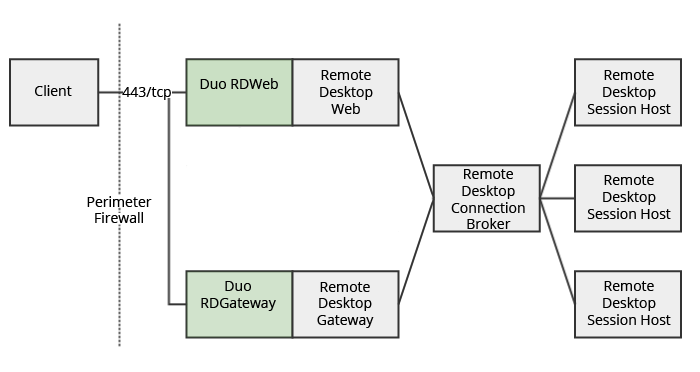
Duo integrates with Remote Desktop Web Access and Remote Desktop Gateway to add Duo protection to RD Web and RD Gateway logons. Duo for RD Web offers inline user enrollment, self-service device management, and support for a variety of authentication methods — such as passkeys and security keys, Duo Push, or Verified Duo Push — in the Universal Prompt
Overview
Duo Authentication for Microsoft Remote Desktop Web Access adds two-factor authentication protection to RD Web portal browser logons. When logging on to the RD Web portal, users receive the Duo enrollment or authentication page after primary authentication.
Duo Authentication for Remote Desktop Gateway adds two-factor authentication to your RemoteApp connections launched from RD Web, and blocks any connections to your Remote Desktop Gateway server(s) from users who have not completed two-factor authentication when all connection requests are proxied through a Remote Desktop Gateway. This configuration does not support passcodes or inline self-enrollment, and instead sends an automatic Duo Push or phone call authentication request.
Users need to perform Duo 2FA authentication at the RD Web server when logging on via the browser, and then approve another Duo request when launching the first RemoteApp of that session. Subsequent RemoteApp launches do not require additional Duo authentication during the same session.
Remote applications may no longer be launched from the "RemoteApp and Desktop Connections" app feed after Duo is installed on your RD Web server.
Before you begin deploying Duo in your RDS environment, please read our Duo 2FA for Microsoft Remote Desktop Services overview to understand the capabilities and limitations of the different deployment options.
Installing Duo's RD Gateway plugin disables Remote Desktop Connection Authorization Policies (RD CAP) and Resource Authorization Policies (RD RAP). The CAPs and RAPs become inaccessible from the Remote Desktop Gateway Manager and previously configured policy settings are ignored by Remote Desktop Gateway. If operational requirements mandate continued use of RD CAPs/RAPs, you may want to consider installing Duo for Windows Logon at your RDS Session Hosts instead. This alternative also supports passcode authentication.
Deployment Tip
Set your application's New User Policy to "Allow Access" while testing. Enrolled users must complete two-factor authentication, while all other users are transparently let through.
Then (when you're ready) change the "New user policy" to "Require Enrollment." This forces all your users to authenticate to Duo (or enroll after RD Web logon).
TLS Requirements
Effective June 30, 2023, Duo no longer supports TLS 1.0 or 1.1 connections or insecure TLS/SSL cipher suites.
The current versions of Duo for RD Web and Duo for RD Gateway support TLS 1.2 when installed on RDS servers running a version of Windows that also supports and uses TLS 1.2 or higher.
See the article Guide to TLS support for Duo applications and TLS 1.0 and 1.1 end of support for more information.
RD Web Installation
Follow the Duo Authentication for RD Web installation instructions to install Duo on your RD Web role servers.
If a single server holds both the RD Web and RD Gateway roles then you will install Duo for RD Gateway next on the same server where you install Duo for RD Web.
RD Gateway Installation
Follow the Duo Authentication for RD Gateway installation instructions to install Duo your RD Gateway role servers.
If a single server holds both the RD Web and RD Gateway roles then you install Duo for RD Gateway on the same server where you already installed Duo for RD Web.
Test Your Setup
With Duo protection installed on both RD Web and RD Gateway, users perform Duo authentication at both RD Web and RD Gateway logon.
To test your setup, log into Remote Desktop Web Access. Successful verification of your username and password redirects you to Duo. Complete Duo two-factor authentication when prompted and then you'll return to RD Web to complete the login process.
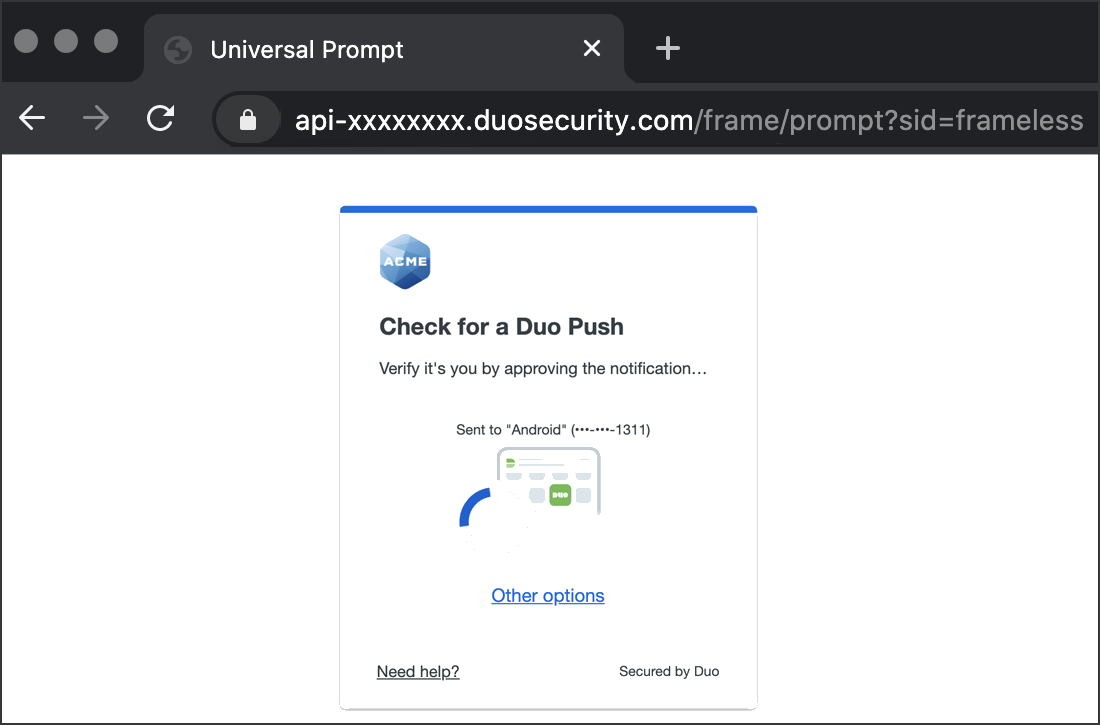
*Universal Prompt experience shown.
Once logged in to RD Web, launch a RemoteApp. Enter your primary Windows credentials if prompted to do so by the Remote Desktop client. You'll receive an additional Duo authentication request via automatic Duo Push or phone call.
Update Duo for RD Web or RD Gateway
You can upgrade your Duo installation over the existing version; there's no need to uninstall first.
Refer to the update instructions for each application:
Troubleshooting
Need some help? Take a look at the RDS Frequently Asked Questions (FAQ) page or try searching our RDS Knowledge Base articles or Community discussions. For further assistance, contact Support.
