Zero Trust.
Complete Confidence.
Allow secure connections to all applications – cloud and on-premises – based on the trustworthiness of users and devices. Set and enforce risk-based, adaptive access policies. And get enhanced visibility into users' devices and activities.
Let's talkUser Behavior & Device Health
By verifying both the identity of a user and the security posture of their device, you can employ a zero-trust security model that assures no traffic within your enterprise’s network is any more trustworthy than traffic coming from outside your network.

Cloud, Mobility & BYOD
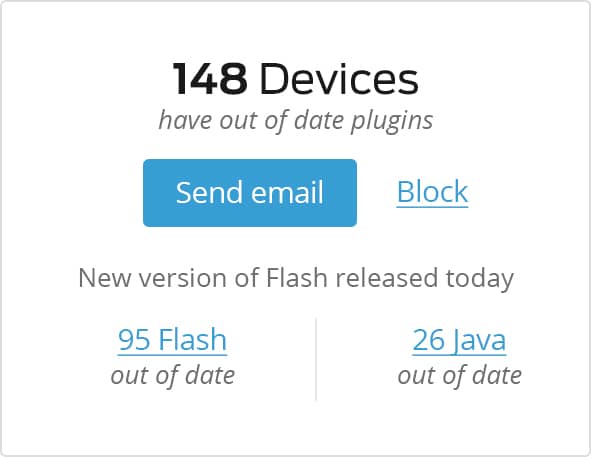
As more enterprise applications enable mobile workflows, employee reliance on using personal devices for work will continue to increase. Embrace mobility and BYOD and keep your users happy with seamless, secure access. Duo Beyond grants access to cloud and on-premises apps without clunky VPNs or MDM solutions.
-
We were previously trying to do this through a combination of five other products. The fact that one product can provide this level of granular access control is really awesome.
— Steve Myers, Head of Security, KAYAK
-
Duo Beyond creates an invisible and open gate that authorized users with trusted devices never have to see, the gate only materializes and closes when the device trust standards are not met.
— Dan Regan, Cloud Security Engineer, Zenefits -
“Duo increased our security and was an easy tool to deploy; every organization should consider them immediately.”
— Chad Spiers, Director of Information Security, Sentara Health