Charting a Course to Zero Trust Maturity: 5 Steps to Securing User Access to Apps
When organizations started to embark on zero trust security back in 2020, it was in response to a dramatic and unforeseen change – the public health crisis. This made zero trust access a ‘must have’ exercise just to keep businesses operational. Securing remote user access became the first use case for adopting zero trust security principles.
At the time, expediency rather than zero trust maturity became the guiding principle. Since then, teams have had years to adjust to this new reality, yet the attackers have as well. Threat actors have dramatically escalated their attacks – targeting security controls like multi-factor authentication (MFA), conducting wily social engineering attacks and extorting businesses large and small with ransomware.
To achieve more resilience in this heightened risk environment, stepping up zero trust maturity is essential. In other words, it’s not just about implementing MFA to verify user trust, it’s about using phishing-resistant MFA with risk-based authentication, device posture checks and other security controls.
So how does one go from MFA to full zero trust maturity? What does that journey look like?
TL,DR: Check out our on-demand webinar Your Zero Trust Roadmap, where we outline the five key steps to secure user access to apps.
Charting an outcome-driven zero trust program
Disclaimer: The word ‘journey’ can annoy many seasoned IT and cybersecurity pros. And I get it. Saying ‘zero trust is a journey’ is far too easy for marketers like me, but for practitioners trying to eliminate excessive trust – everywhere – it just adds to the already Sisyphean vibe.

That’s why it’s important to break zero trust down into iterative steps. But before you can even start, plan your destination. What are the outcomes your team is seeking? Outcome-driven zero trust programs work far better than simply looking to plug holes with single product purchases.
For example, outcomes like adapting to external events, creating a security culture, and cost-effective programs, all improve when organizations make progress towards zero trust security (based on survey responses from 4,751 active information security and privacy professionals from 26 countries).
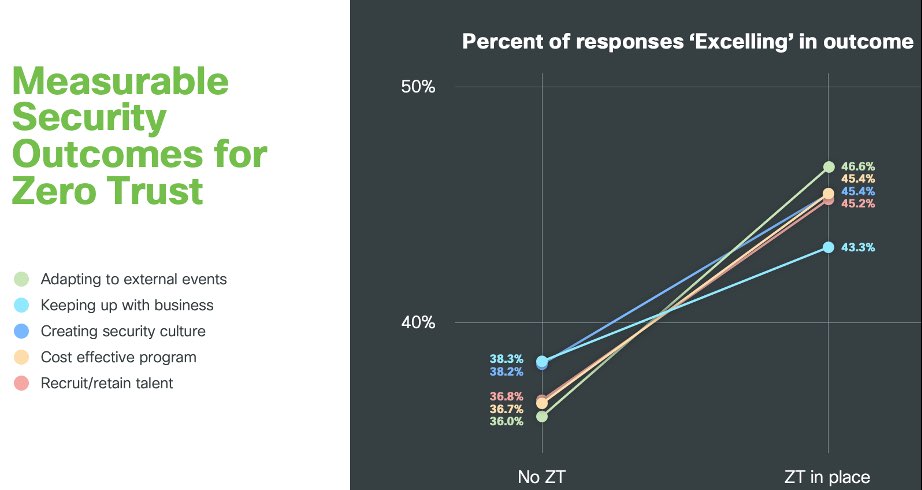
Clearly, it’s essential to have a well-defined plan to unlock these outcomes. When it comes to securing user access to applications, here are the five phases we recommend implementing when adopting zero trust, sprinkled in with some wisdom from Duo customers.
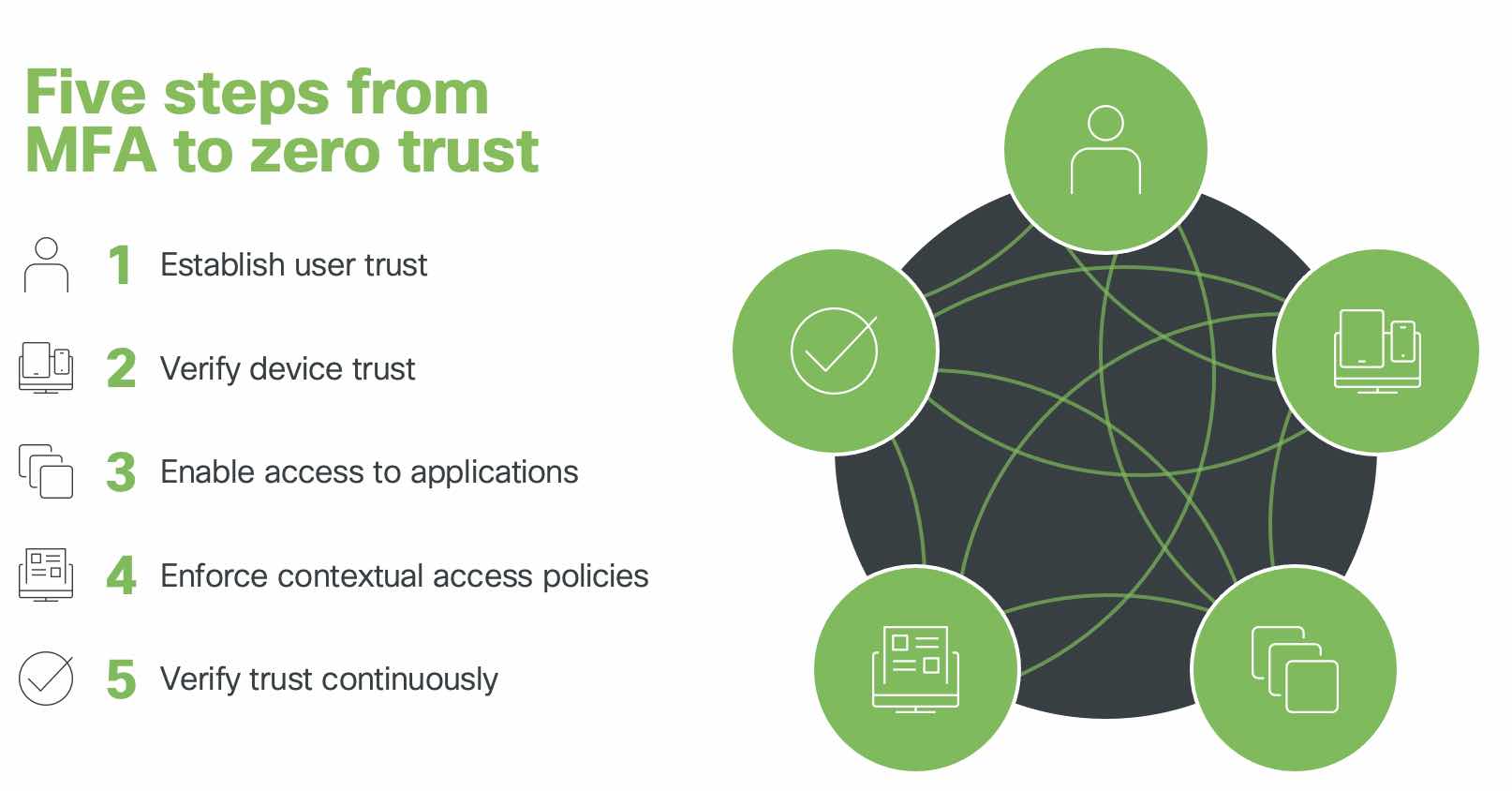
Phase 1: Establishing user trust
Establish user trust using phishing-resistant multi-factor authentication (MFA) to verify users truly are who they say they are. Make it easy for users to strongly authenticate – on managed and unmanaged devices, and whether they’re employees or contractors (e.g. BYOD).
“We have a layered approach to securing our networks and MFA is a critical layer of our security program.”– Todd Deering, Information Security Architect, City and County of Denver
Phase 2: Verifying device trust
Verify device trust with posture checks and block unwanted access with a trusted endpoint policy. Guide users in fixing device trust issues on their own before gaining access to apps, and without having to call the helpdesk.
“Duo became the link we needed to make our security philosophy really work. We now know that if folks were downloading reports or manipulating data in a cloud application, that they were doing it from a safe device, and that their identity had been confirmed with MFA.”– Richard Hall, Senior Director IT Infrastructure and Operations, Financial Force
Phase 3: Enabling access to apps
Enable access to applications with VPN-less access (e.g., ZTNA) – regardless of location or protocol. Shrink the attack surface by reducing password usage with passwordless SSO and make it faster and more convenient for users to get to the apps they need – whether SaaS-based or private.
“Duo is unique in that it allows us to not only protect our website, but to protect our SSH connections and a wide variety of other assets as well.”– Paul Pieralde, Principal Product Security Engineer, Eventbrite
Phase 4: Enforcing contextual access
Enforce contextual access policies with risk-based authentication. Increase device visibility, and adapt access dynamically based on user or device behavior. Step up access based on increased risk and ease up access requirements based on lowered risk.
“Depending on the application and risk context, the university has enforced Duo’s adaptive access policies, such as ensuring that authenticator devices have screen lock enabled, enabling ‘Remember Me’ device policies for specific applications and checking every device that enters the network.”– Infosec Team, University of British Columbia
Phase 5: Verifying trust
Verify trust continuously with Wi-Fi profile analysis, historical authentication analysis, and more. Respect the user’s privacy and productivity by anonymizing location data and eliminating unnecessary decisions when continually verifying trust.
“People were coming in every day and signing into five, six, seven apps and I felt I could make that easier while building in security. Whenever I can help solve business problems and layer some security in, that’s a pretty big win.”– Jason Waits, Chief Information Security Officer (CISO), Inductive Automation
Ready to start charting your zero trust program?
For more information, check out our on-demand webinar Your Zero Trust Roadmap. Or, download our white paper How to go from MFA to Zero Trust.
For strategic guidance and access to hands-on labs, register for one of our free Zero Trust Workshops. You’ll learn how to build a zero trust strategy and install and configure Duo, Umbrella, and other Cisco zero trust technologies.

