Original Equipment Manufacturers (OEM) refer to the first boot of a new PC as the out-of-box experience (OOBE). As you battle your way through modal dialogues for questionable software, and agree to some exciting 30 day antivirus trials, it's pretty forgivable to want to throw your brand new computer through the nearest window.
Today, Duo Labs is publishing our take on the OOBE; Out-of-Box Exploitation: A Security Analysis of OEM Updaters. Shovelware, crapware, bloatware, “value added” - it goes by a lot of names - whatever you call it, most of it is junk (please, OEMs, make it stop). The worst part is that OEM software is making us vulnerable and invading our privacy. Issues like Superfish and eDellRoot make us less secure and are often easy to abuse in practice. With that in mind, Duo Labs decided to dig in to see how ugly things can get.
One of the major things we found was the presence of third-party update tools. Every OEM we looked at included one (or more) with their default configuration. We also noticed that Microsoft Signature Edition systems also often included OEM update tools, potentially making their distribution larger than other OEM software.
Updaters are an obvious target for a network attacker, this is a no-brainer. There have been plenty of attacks published against updaters and package management tools in the past, so we can expect OEM’s to learn from this, right?
Spoiler: we broke all of them (some worse than others). Every single vendor had at least one vulnerability that could allow for a man-in-the-middle (MITM) attacker to execute arbitrary code as SYSTEM. We’d like to pat ourselves on the back for all the great bugs we found, but the reality is, it's far too easy.
Here is a quick breakdown of basic features from some of the updaters we looked at:
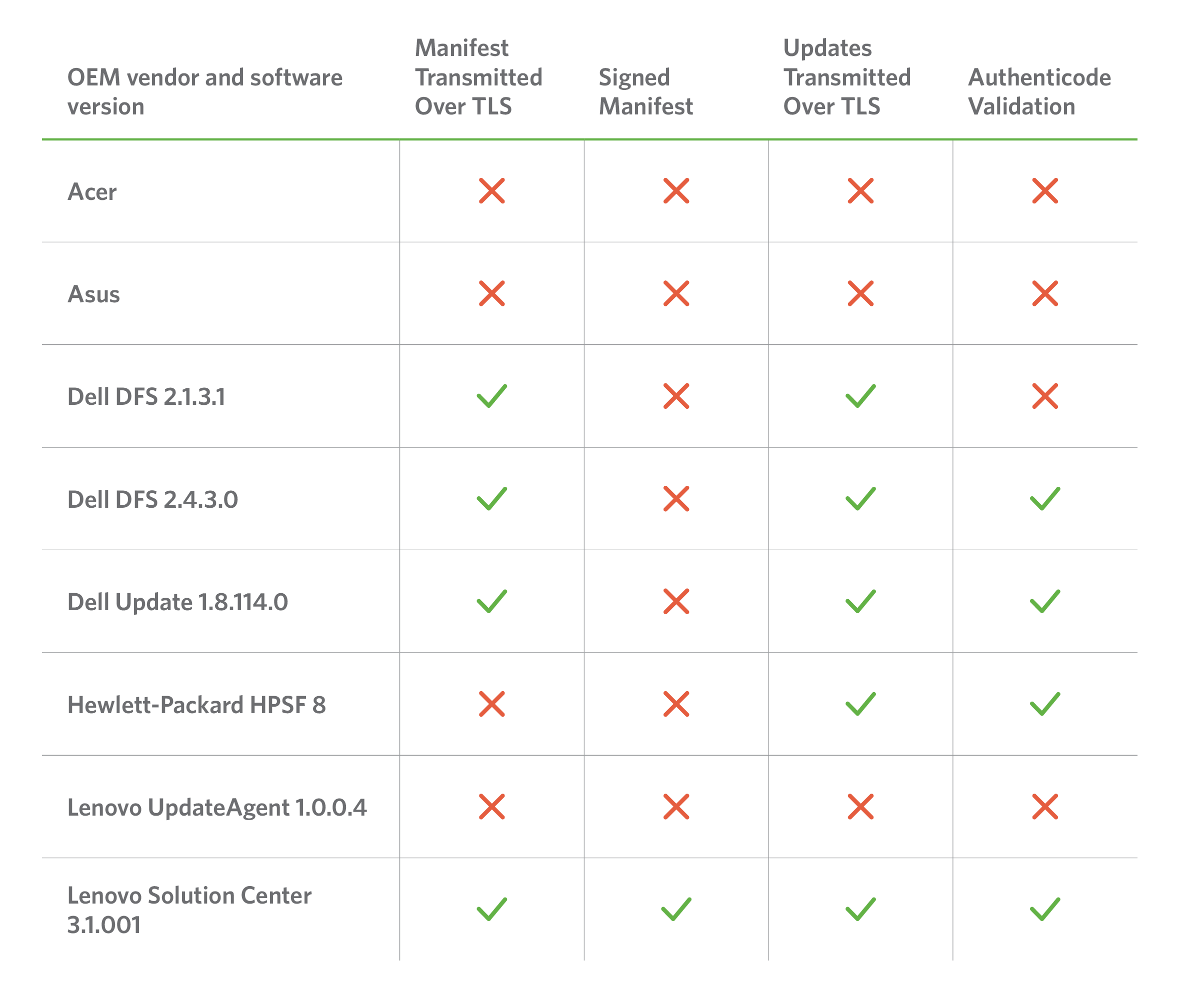
Some vendors made no attempts to harden their updaters, while others tried to, but were tripped up by a variety of implementation flaws and configuration issues. In total, we identified and reported twelve unique vulnerabilities across all of the vendors, and identified a number of concerning trends:
- Every vendor shipped with a preinstalled updater that had at least one vulnerability resulting in arbitrary remote code execution as SYSTEM, allowing for a complete compromise of the affected machine.
- Vendors often failed to make even basic use of TLS, properly validate update integrity, or verify the authenticity of update manifest contents.
- Vendors sometimes had multiple software updaters for different purposes and different implementations; some more secure than others.
- The large attack surface presented by ancillary OEM software components makes updater-specific bugs easier to exploit in practice by providing the missing pieces of the puzzle through other tools bundled with their systems.
- The level of sophistication required to exploit most of the vulnerabilities we found is somewhere between that possessed by a coffee stain on the Duo lunch room floor and your average potted plant - meaning, trivial.
The most notable vulnerabilities we found can be summarized as follows:
- Dell: One high-risk vulnerability involving lack of certificate best practices, known as eDellroot.
- Hewlett Packard: Two high-risk vulnerabilities that could have resulted in arbitrary code execution on affected systems. In addition, five medium-to-low risk vulnerabilities were also identified.
- Asus: One high-risk vulnerability that allow for arbitrary code execution as well as one medium severity local privilege escalation.
- Acer: Two high-risk vulnerabilities that allow for arbitrary code execution.
- Lenovo: One high-risk vulnerability that allows for arbitrary code execution.
Download Out-of-Box Exploitation: A Security Analysis of OEM Updaters to read our complete analysis and deep dive into the issues we identified, including more about the vulnerabilities we found.
