At Google I/O 2016, there was a lot of excitement about the pending release of the latest Android operating system Android N and its many features. Dave Burke, VP of Engineering (Android) at Google, announced that among those features would be automatic system updates.
With automatic updates, your phone will automatically download the newest software update available in the background and install it the next time you restart it. So automatic updates sound great, but you might be asking, what’s the big deal? In order to answer that question, let me provide a brief background on the history of updating when it comes to Android devices.
Background
The first Android operating system was released in September 2008, and it wasn’t until roughly seven years later, in the aftermath of the Stagefright bug, that Google and other Original Equipment Manufacturers (OEMs) began releasing monthly security updates. During the preceding seven years, Google, OEMs and carriers were often lackadaisical when it came to delivering security updates in a timely manner.
In addition to releasing monthly security updates in response to Stagefright, Google also introduced the Android security patch level API to make checking if an Android device is up-to-date as simple as knowing today’s date.
Duo Labs’ Findings
It has been nine months since Google began these monthly updates, and we at Duo Labs are interested in how this change in security policy has impacted the masses. The following were some of the key findings from our data analysis:
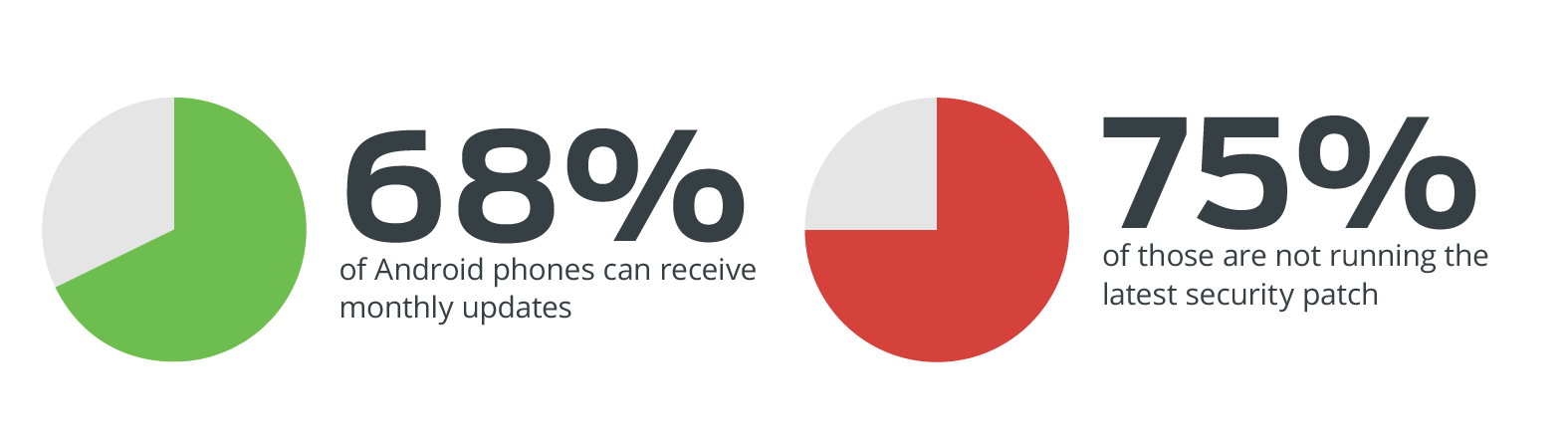
- 68% of Android devices are able to receive the monthly security patch.
- As of April 30, only 25% of those devices were running the latest security patch.
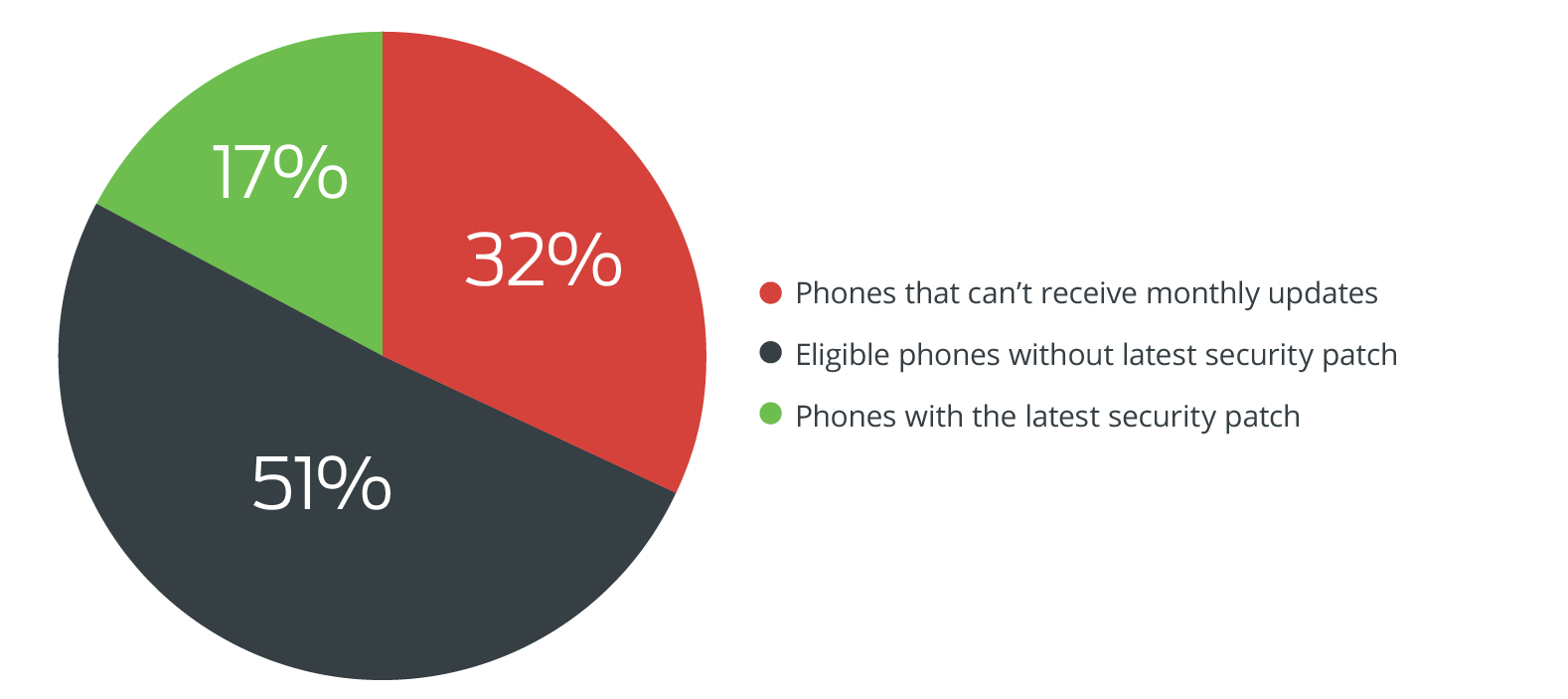
- 3 out of 10 Android devices hadn’t applied a security patch that has been released since the start of 2016, thus leaving them susceptible to exploits for 24 critical vulnerabilities.
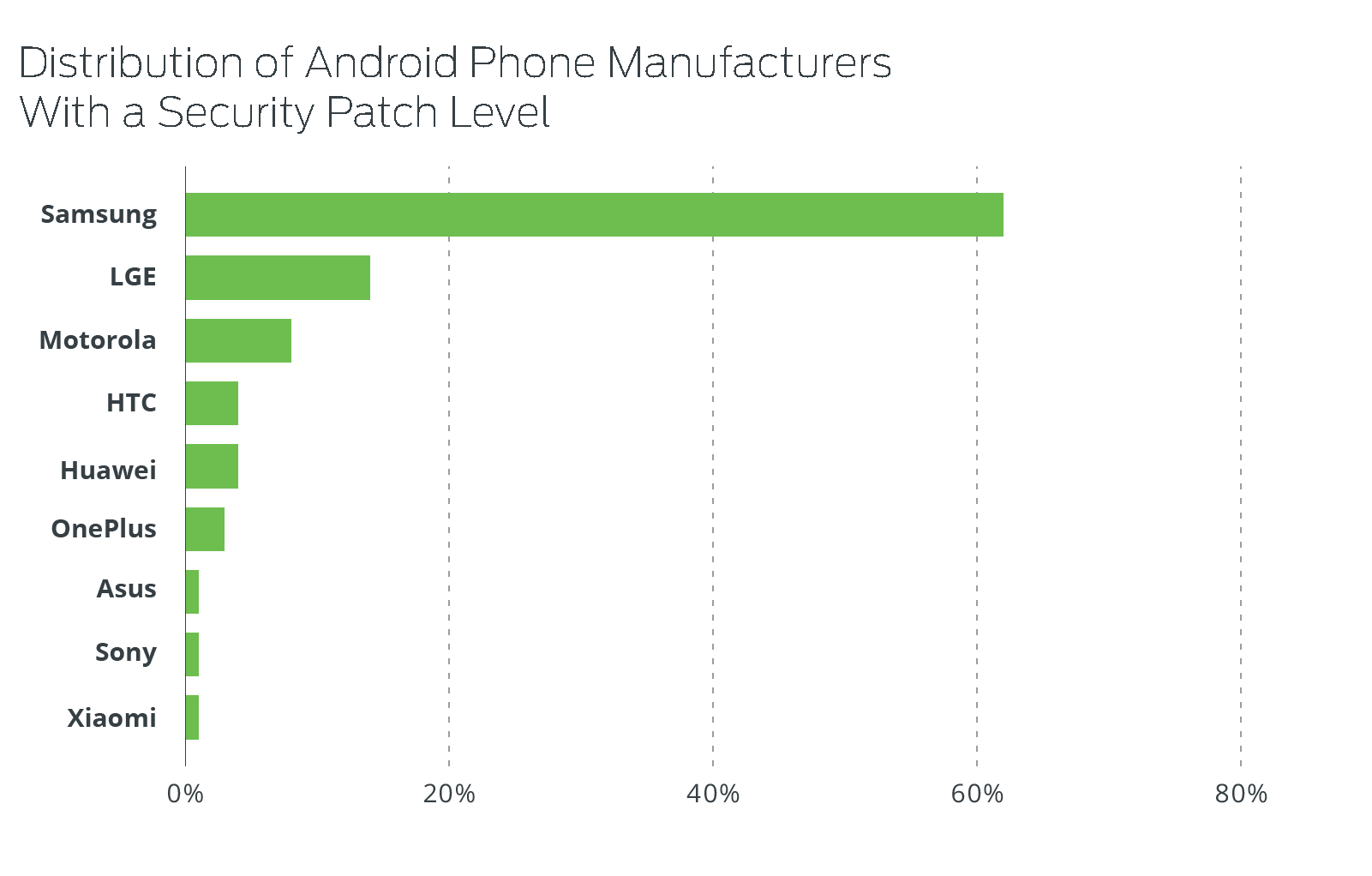
As we mentioned earlier, Google is not the only one involved in the monthly patching process. OEMs and carriers play a large role in how quickly updates are released to the devices they sell.
Despite Samsung making up 62 percent of the Android devices in our dataset that could receive monthly Android updates, only 15 percent of eligible phones had applied the latest security patch, placing them fifth among the nine OEMs in our sample.
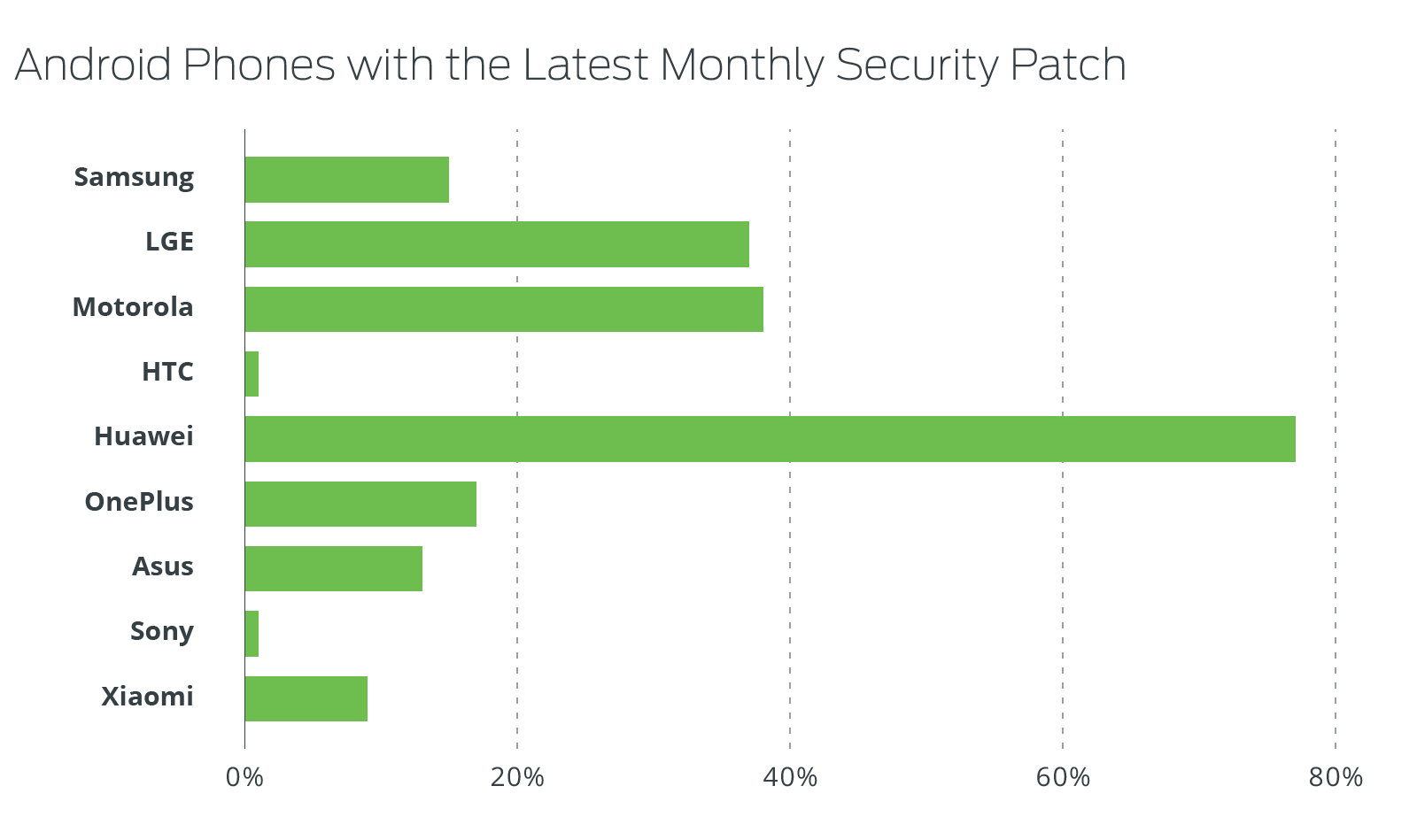
In stark contrast, 77 percent of Huawei phones that are able to receive security updates were running the most recent security patch. This high percentage can be attributed to the large number of Nexus 6Ps which receive monthly updates from Google.
Business Implications
We’ve noted how users are slow to apply security patches, but how does that affect anyone outside of the device owner? The advent of BYOD makes it paramount that IT administrators have insight into the security posture of the phones connecting to the network. Having devices that are one or two security patches behind could severely threaten the security of an entire enterprise.
With that being said, it’s not just gloom and doom. There are few simple steps you can take to protect your company:
- Buy nexus phones that receive monthly updates.
- Educate users about the importance of applying security updates in a timely manner and supply them with helpful information on how to successfully upgrade their devices.
- Notify users that a security update has been released and encourage them to upgrade.
- Make use of an endpoint security solution that will provide you the patch level of devices on the network.
Manufactures and carriers alike should work to bring automatic updates to their customers. By doing so, they would alleviate the burden customers and IT administrators have of manually applying updates, shorten the window of time attackers have to exploit vulnerabilities after they’ve been disclosed and bring better operating system performance to their user without sacrificing business productivity.
