Less than 10 percent of active Google accounts use two-step verification (2SV) to secure access to their services, like Gmail, according to a Google Software Engineer Grzegorz Milka’s presentation at the USENIX Enigma 2018 security conference as reported by The Register.
A Google and University of California research paper published last November, Data Breaches, Phishing or Malware? Understanding the Risks of Stolen Credentials found that only 3.1 percent of users enabled two-factor authentication after successfully recovering their hijacked Gmail account. The discrepancy between security-aware and regular users is noted:
While experts commonly favor using two-factor authentication or password managers, these tools are virtually absent from the security posture of regular users.
Google’s longitudinal measurement study analyzed millions of keylogger and phishing kit victims from March 2016 - March 2017, including 1.9 billion usernames and passwords exposed as the result of data breaches.
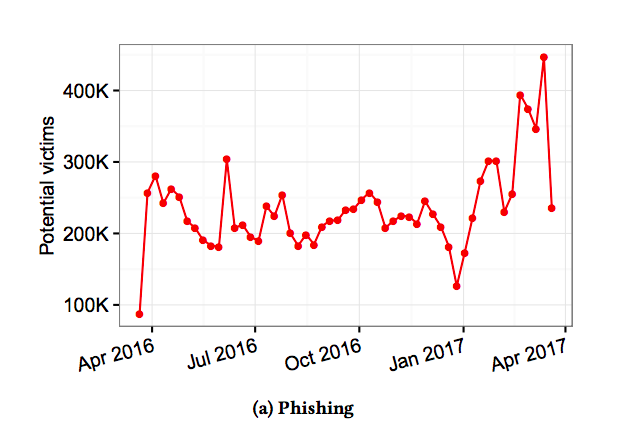 Source: Google
Source: Google
What is Two-Step Verification?
Two-step verification (2SV) is a term used interchangeably by tech giants such as Google and Apple for two-factor authentication (2FA), the technology that adds another layer of security to logins. Primary authentication typically consists of a username and password, while secondary authentication can be carried out through a variety of different methods.
Apple has updated their support documentation to state:
Two-step verification is an older security method that is available to users who don’t have Apple devices, can’t update their devices, or are otherwise ineligible for two-factor authentication.
By this definition, they equate SMS-based 2FA with the term ‘two-step verification.’ They also provide newer documentation on using two-factor authentication to protect your Apple ID.
The Most Secure Two-Factor Authentication Methods
One method requires downloading a free authenticator app for your smartphone that generates unique, time-based passcodes you can type or copy and paste into your Gmail login page. This allows you to verify your identity with not only your password, but also with a secondary, physical device.
For enterprise-level or more advanced users interested in the most secure option available, using a physical USB device plugged into your computer to verify your identity provides protection against phishing attempts. By tapping it once, you can complete 2FA and log into your Gmail securely.

Source: Yubikey
Either of these methods take just seconds to complete login, are free or require a nominal amount of money and setup time (less than $20 for individual users and cheaper in bulk for enterprise users), and the small extra step is well worth it to keep your account (and data and access to other accounts) safe from theft.
So Many Ways to Phish
The main objective of a phishing email attempt is to steal information, through some means. One way is to send a user a phishing email with a link to a fake login page that spoofs a legitimate website with a message that urges the user to log in. The credentials are then forwarded to the phisher.
Another way to steal credentials and other data is to send an email with exploit kit or malware attachments that, when opened, check the user’s computer for certain versions of software. Then, if conditions are present, the malware will download and execute. The malware may include a keylogger or other type of malicious software that tracks every keystroke of the user, sending this data to the phisher.
Phishing Kits
A phishing kit is a bundle of site resources that can make campaigns more efficient and reusable, enabling non-technical phishers the ability to create spoofed websites and launch a phishing attack. For more information about phishing kits, read Phish in a Barrel: Hunting and Analyzing Phishing Kits at Scale.
Google’s report analyzed a sample of 10,037 phishing kits and about 3.8 million credentials that belonged to victims of the kits. They found that the most popular phishing kit was used by almost 3,000 attackers to steal 1.4 million credentials - this kit included a website that emulated Gmail, Yahoo and Hotmail logins. By far, Gmail was the most popular email provider used by phishers as exfiltration points to receive stolen credentials (72.3%).
The top phishing kits impersonate many other brands, including file storage services (Dropbox, Office 365), webmail providers (Workspace Webmail, AOL) and business services (Docusign, ZoomInfo).
Phishing kits collect not only credentials, but also additional information such as geolocation data, secret questions and device-related details.
This type of info can be used to bypass login challenges for services that attempt to detect suspicious login attempts.
The Consequences of Getting Access to Your Gmail
Why would an attacker want to access your Gmail account? As detailed by Google's Enigma presentation, an account hijacker could export your list of contacts (consisting of family, friends and coworkers) and send them phishing links to potentially gain access to their accounts.
According to Google’s report, a hijacker can also reset your passwords to other services, download all of the your private data and remotely wipe data and backups.
Once compromised, hijackers will often search the email history of accounts for financial data and use the accounts for spamming/phishing their contacts. They also searched inboxes for financial records and credentials related to third-party services.
Google’s report referenced another report from 2014, Consequences of Connectivity: Characterizing Account Hijacking on Twitter that found 13.8 million compromised Twitter accounts were used to infect other users as well as to post spam. However, most users can avoid an account compromise by enabling two-step verification, aka, two-factor authentication.
