From a vulnerability management perspective, it makes sense for defenders to be aware of which vulnerabilities have publicly available exploit code. Increasingly, much of that code is beginning to appear on GitHub.
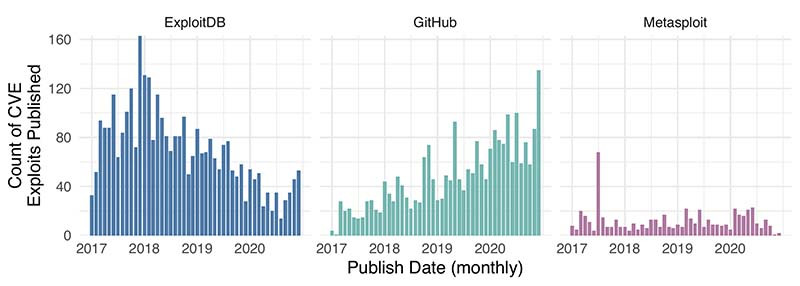
Exploit DB was a “prominent source” in early research and among academic circles, but the number of exploits being posted to this database has been declining since 2017, Cyentia Institute’s Jay Jacobs wrote. In contrast, the number of exploits published on GitHub each month has been steadily increasing.
When vulnerabilities are published, the clock starts ticking on when exploit code would become available. Vulnerabilities with published exploit code are as much as seven times as likely to be exploited in the wild, past research has shown. There are clues where the code is published can affect whether it will be exploited. Cyentia also found that how the code is published has an impact: “weaponized” exploit code, such as in the form of a Metasploit module, increases the odds of that vulnerability being exploited in the wild from about 3.7 percent to 37.1 percent, Jacobs said.
The overall trend for the three major sites for exploit code (a larger chart from Cyentiais pretty striking. The number of exploits published on Exploit DB shows it is still a good source of keeping track of different vulnerabilities, but the number published monthly has been declining since 2018. The number of exploits published on Exploit DB ranged from more than 120 per month to around 60 over the course of 2018, but in 2020, that range was more than 20 to fewer than 60. Contrast that to GitHub, where the monthly numbers have been steadily increasingly each month, each year. The number of exploits published on GitHub ranged from 20 to 40 for most of 2018, but ranged from 60 to over 120 in 2020.
The number of exploit codes — the modules — published on Metasploit has been constant.
That Metasploit chart is pretty interesting. Metasploit modules help defenders find holes that need attention, and also help confirm that the mitigations are working correctly. However, because the framework makes it easier to execute the exploits, there is an undeserved impression that Metasploit encourages attacks. But the fact that the numbers on Metasploit is pretty constant may suggest that attack groups aren’t waiting with bated breath for the next Metasploit module to be available before starting their campaigns.
But, back to vulnerability management. The thing about exploits on Exploit DB is that it was clear what it was. As Jaccobs noted, however, publishing of exploits is largely adhoc and unstructured. Proofs-of-concept and ready-to-weaponize exploit code can be published in various forms outside of dedicated forums and databases—they can appear as blog posts, or even on Twitter. The shift towards publishing exploits on GitHub exacerbates the situation even more, since it would be difficult to regularly look through various repositories to find published code. (Don't worry, Cyentia is working on a classifier for this.)
“Anyone can create a GitHub repository and there are no rules, limitations or standards for what a working exploit will look like once published to github,” Jacobs said.