The goal for secure software isn’t to never have vulnerabilities, but to be able to find vulnerabilities as soon as possible so that they can be fixed. GitHub has expanded its code scanning capabilities to make it easier for developers to identify flaws in projects that are managed on its platform.
The code scanning feature automatically checks the code for common errors that lead to security vulnerabilities every time the developer pushes the code (git push) from the local repository to the GitHub repository. The scan results would be displayed in pull requests, so that anyone using the code would be warned of issues upfront. The code scanning service provides information about which line of code contains a potential vulnerability, why it may be exploitable, and suggestions on how to fix it.
Code scanning should sound familiar, because GitHub has been working on various iterations of this feature over the past year. The feature is based on the CodeQL code analysis engine that came with GitHub’s Semmle acquisition last fall. CodeQL is an object-oriented query language that can identify variations of a vulnerability in the codebase. The code analysis engine was previously available to all public repositories and enterprise customers through GitHub Actions. As part of the Security Lab initiative, security researchers could use CodeQL for free to look for vulnerabilities in open source software.
Secret scanning is another beta feature GitHub announced that is a continuation of something the company has been working on for a while. Secret scanning (previously called token scanning looks for potentially sensitive data in code, such as tokens, private encryption keys, and user credentials. That includes scanning public repositories for credentials for other service providers, such as Alibaba Cloud, Amazon Web Services, Azure, GitHub, Google Cloud, Slack, Mailgun, Twilio, and Stripe that may have been accidentally committed to the project. Available for public repositories since 2018, the feature is now available for private repositories, as well.
GitHub announced the Advanced Security offering at its Satellite virtual event this week. The feature will be available for free for open source projects in public repositories, and as a paid add-on for enterprise customers who want to enable it for private repositories. Advanced Security can be used by developers to help find vulnerabilities during development as well as by security researchers to find and report vulnerabilities in open source projects.
Since code scanning is still a beta feature, GitHub users need to sign up to enable it for their accounts. There is currently a multi-day wait list to have the feature enabled on the account.
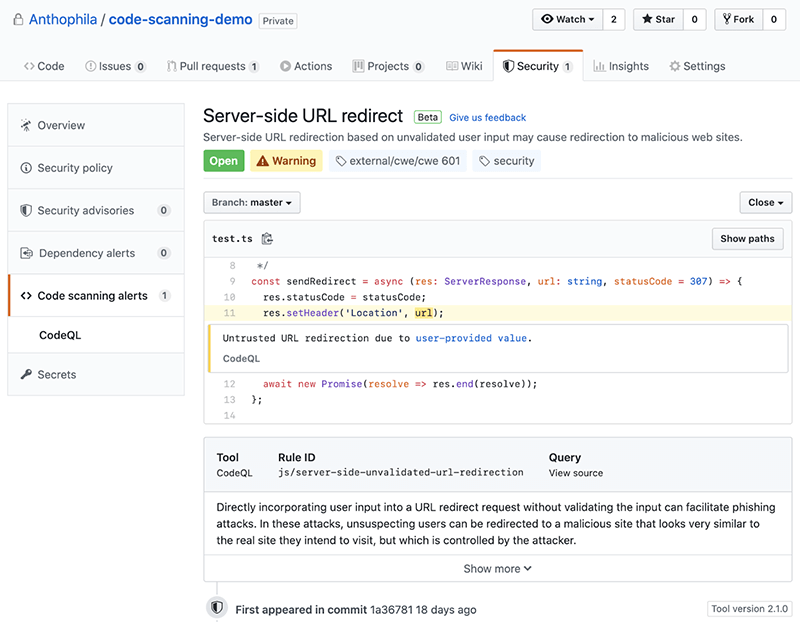
The results of the code scanning show which line the issue can be found and the nature of the vulnerability. Source: GitHub
On the surface, GitHub’s Advanced Security sounds like just another feature announcement, but it points to a bigger trend of integrating security tools into the developer’s workflow. There are plenty of stand-alone tools that scan code for vulnerabilities, and attempts to integrate scanners with coding IDEs to display errors right in the editors. However, all those tools expect the developers to know about security and using them.
The thing about open source projects is that anyone can look over the code to find vulnerabilities, but there is no way to guarantee that someone with the right expertise is actually looking at the code. Many developers may not have the secure coding knowledge to avoid some of the more common mistakes, and unless someone sends a vulnerability report, they would never know about the flaws that need to be addressed. Project maintainers may also not know who is using the code and needs to be notified when issues are fixed.
GitHub has automated some of these tasks, such as the fact that it automatically notifies project owners if any of the dependencies they are using in their code have a vulnerability or has been updated with a new version.
And now with scanning results showing up directly in the pull requests, development teams who may not have the time or skills (and knowledge) to look through the codebase for vulnerabilities know what to fix. This brings secure coding to a broader group of developers without changing their workflow to install or run extra tools. They just have to enable the feature in their accounts.
It also benefits large development teams with millions of lines of code, because the analysis engine can look for similar vulnerabilities in different parts of the codebase, even if the actual code blocks are slightly different. This lets developers identify and eliminate classes of vulnerabilities from their software.
Just because GitHub is taking on the challenge of scanning code for vulnerabilities doesn’t mean everything is set in the world of secure software. Developers still have to fix the issues that are displayed in the pull request. Project maintainers have to communicate to downstream users when issues are resolved. And even though a significant number of open source projects are maintained on GitHub, there are plenty that aren’t, and those project maintainers will still need to have a way to receive and act on vulnerability reports as well as do their own security scanning.
