Researchers have linked the Magecart group known for its supply-chain attacks to Cabanak, an advanced threat group.
Magecart Group 5 uses the same domains that have also been used in phishing campaigns that pushed the Dridex banking Trojan, Malwarebytes researchers said. The Dridex phishing campaigns are believed to be the work of the infamous Carbanak (FIN7) attack group. The Carbanak group also uses the Carbanak custom backdoor to target internal banking infrastructure and ATMs. Europol said Carbanak has struck banks in more than 40 countries.
“We spent some time digging into a number of Magecart domains registered via the well-known Chinese registrar BIZCN/CNOBIN, [which is] essentially a bulletproof registrar,” Malwarebytes researchers said. “We narrowed down the domains to a smaller subset previously identified as being used by Magecart Group 5.”
Magecart is an amorphous group consisting of a dozen or so attack groups that inject malicious JavaScript code into online payment pages (ecommerce checkout pages) to steal payment card information (name, address, credit card numbers, expiration date, and CVV). RiskIQ recently said its research team had identified a little over 2 million instances of Magecart’s JavaScript binaries, with over 18,000 hosts directly breached.
“Victimology helps us to get a better idea of the threat actor behind attacks. For instance, we see many compromises that affect a small subset of merchants that are probably tied to less sophisticated criminals, often using a simple skimmer or a kit,” Malwarebytes researchers wrote.
Some Magecart factions target specific platforms while others target third-party libraries to compromise all the sites that rely on that component. Group 5 is known for targeting the supply chain and was recently seen testing code targeting the kind of routers typically used to operate public Wi-Fi networks. The group targeted the third-party chat feature on Ticketmaster's website in that breach.
A supply chain attack that targets a single site or component in order to compromise all other sites downstream that rely on that site/component has more in common with advanced threat actors than the typical financially-motivated cybercriminal, Malwarebytes said. Bigger breaches that "reel in a much larger prize" tend to tbe the work of experienced advanced threat groups with well-established ties with the criminal underground, the researchers said.
In the case of the domains, Magecart Group 5 used privacy protection services with eight of the top-level domains, but overlooked one. Malwarebytes researchers Jérôme Segura, William Tsing, and Adam Thomas were able to see that domain's WHOIS data prior to GDPR going into effect (which hid registry data), and saw the name, address, and contact information of operators in Beijing. Using the exposed email address, the researchers were able to find other domains, several of which were used in the Dridex campaigns. One was a corporate eFax campaign targeting Germans. Two were phishing campaigns spoofing OnePosting and Xero accounting services.
“If we pivot from [the] email address, we can identify other domains, and in particular several that connect to Dridex phishing campaigns,” researchers explained.
Researchers also found a phone number in common between the two groups. Security blogger Brian Krebs had previously mentioned a phone number that was used by Carbanak, and that same phone number was used to register one of Magecart domains.
“As Magecart activity increases and new groups emerge, it can sometimes be helpful to go back in time in order to examine bread crumbs that may have been left behind,” researchers said. "Looking back means we can spot recurring themes."
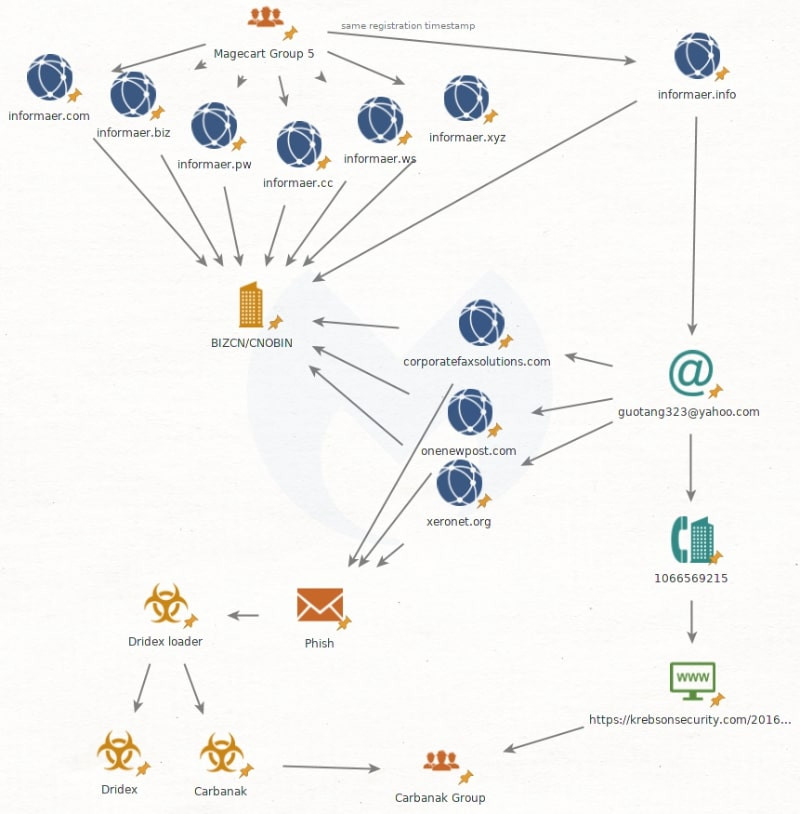
Malwarebytes researchers illustrated the connections between Magecart Group 5 and Carbanak.
