Next Tuesday, Microsoft will drop support for their browser, Internet Explorer (IE), versions 8, 9 and 10. That means they’ll issue their last set of patches, and no longer release any updates (including security updates) for IE on the most popular versions of Windows (7, 8.1, and 10).
Users of these browsers will be notified that these IE versions have reached “end of life” (EOL), prompting them to upgrade to IE 11 or Edge to continue using a supported Microsoft browser.
This feels like normal behavior - as other companies often sunset older versions of software as time goes on. So, just how serious is this situation? Will these older versions of IE quietly fade into the night?
Summary of Browser Findings
To answer these questions, we took a look at our user data to get an idea of current IE users and the extent of the impact. Here’s a summary of our top findings*:
- 44 percent of IE/Edge browser users are still running IE 8, 9, or 10 - all unsupported as of January 12th
- The most popular version of IE currently in use is IE 11
- Edge adoption is still relatively low - the ratio of Edge users to IE users is 1 in 15
- In most cases, these users are still on Windows 7, which is out of its mainstream support cycle from Microsoft
- When it comes to overall browser use, the highest percentage of users are on Google Chrome
*Note: Windows server support is a different story - in this blog, we’re only talking about clients.
In the past 45 days, we saw that the most popular type of IE browser used to access Duo’s services is IE 11 - a positive finding. Although it’s the last version of IE that will ever be released as Microsoft transitions to the Edge browser, it’ll continue to receive monthly security updates and bug fixes for some time.
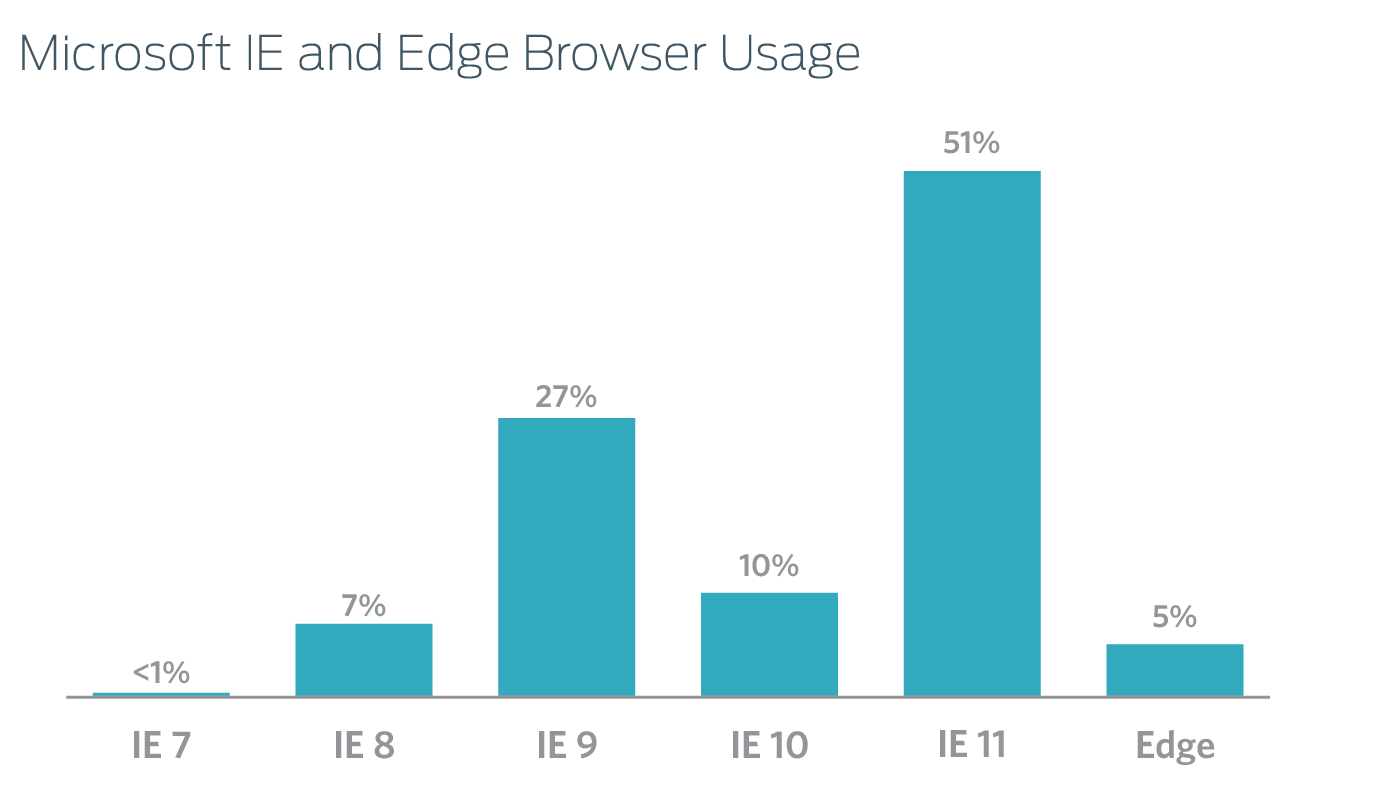
However, we also found that 44 percent of Microsoft browser users run IE 8 (~7%), IE 9 (27%) or IE 10 (~10%) - most of whom are on Windows 7 or newer. That means they’ll be left without security updates following the final update to these browsers next week. Many of these legacy browsers have been under attack for years, and now they won’t be protected against any new threats.
Unfortunately, the extended notice of this impending drop of support seems to have done little to drive users toward the new Edge browser platform. In fact, the ratio of Edge users to IE users is actually only around 1 in 15.
We also found that many of the users still operating on these soon-to-be legacy browser platforms are indeed on Windows 7, which is out of its mainstream support cycle from Microsoft and for which the minimum supported IE browser will be IE 11 after Tuesday.
Generally, these findings show that a large portion of the Microsoft ecosystem remains trapped in a significantly outdated and dangerous combination of an OS that is now in an extended (as opposed to mainstream) support cycle and a set of very outdated browsers which, in the case of IE 8, were released nearly 7 years ago.
Given that Automatic Updates on the Windows platform should have advanced many of these users at least to Internet Explorer 11, the data suggests that the large pool of users stagnating on old browser platforms are likely not enabling Automatic Updates and likely have numerous other missing OS patches as well.
For those users already running Windows 10, where Edge becomes an option for browser choice alongside a provided installation of IE 11 for compatibility purposes, Edge adoption is still extremely low. In fact, 36% of Windows 10 devices that interacted with Duo were using Chrome, 28% were using IE 11, and Edge was running in third place with only 21% of browsers on Windows 10.
So, What’s the Problem?
For the IT professional, this is a major concern. Not only do those running IE 8, 9, and 10 simply run outdated software, they also run software that has a lengthy history of software vulnerabilities targeted by attackers.
In the past three years alone, there have been an average of over 160 new documented vulnerabilities per year in IE browsers. Many of these vulnerabilities are major risks that allowed attackers to remote code execution, which can be used to take complete control of the affected machine.
Users and IT professionals should expect this trend to continue. Attackers are well aware that both Microsoft will be ending support for these browser versions and that they are still hugely prevalent in the wild. Adversaries will seek to take advantage of this opportunity.
IE Vulnerabilities Target Every Version
One example is an IE zero-day exploit (Trojan.APT.9002) that was being actively used in the wild in a campaign dubbed Operation Ephemeral Hydra by FireEye. The exploit was a combination of an information leakage vulnerability and an IE memory access vulnerability that allowed an attacker to execute code on an affected machine.
The memory access vulnerability targeted Windows XP with IE 7 and 8, and on Windows 7. The exploit targeted nearly all versions of IE, from 7-10.
Yet another remote code execution vulnerability allowed an attacker to infect IE users via links to the attacker’s website, or by opening malicious attachments through email. Once infected, an attacker could gain the same user rights as the current user - that means, if an administrator was infected, the attacker could have the same rights to install programs, alter data, or create new accounts.
This vulnerability affects all versions of IE, with Microsoft urging users to update in an emergency patch release notice.
What to do About IT?
All it takes is one vulnerable device accessing your network to put your entire organization at risk of a data breach. But with visibility into the types of risky devices accessing your network, you can create and enforce data-driven policies to secure your company.
At Duo, we believe in shifting a larger focus to mobile device security. Our Duo Access offers IT admins visibility into all mobile endpoints accessing their corporate resources. Endpoint visibility is key to enabling our customers to create controls and policies that work for their specific environments, and to protect against risks introduced by out-of-date devices.
We hope that publishing this data will encourage organizations to have conversations about device security earlier and more often.
Here’s a few practical tips to address these issues in your organization:
Educate your users on the importance of running updates and enabling Automatic Updates. Keeping devices up-to-date is critical to preventing compromise by attackers. Using current and supported software ensures users will continue to receive security updates and bug fixes for the software they use most - their browser!
In the case of Internet Explorer and Edge, automatic updates should occur along with monthly patch cycles. However, we also suggest considering switching to browser platforms that are updated frequently and automatically, such as Google Chrome - which is already the leading browser platform by a thin margin according to our data. Users and IT departments should strive to run current, supported operating systems and applications to prevent compromises in their environment.
Carefully weigh the balance between legacy compatibility and security. Many users will argue that web applications they use frequently are designed to be used on older platforms. But using a less-secure browser in today’s security climate in order to support a legacy interface can ultimately be more costly than updating the application or working with a vendor to provider support for newer software in the event of a compromise.
Consider compliance concerns. Microsoft draws attention to an important consideration in their EOL support announcement that running outdated software may actually have compliance impacts in enterprise environments. In addition to generally running with an open attack surface, there could very well be regulatory and compliance concerns associated with running unsupported software.
Stay tuned to our Duo Labs blogs as we continue our series of analytics and important security findings and share them with the broader community.
