SINGAPORE——With the recent spate of headlines regarding hardware implants and attacks targeting vulnerabilities in chips and processors, there are a lot of questions surrounding the integrity of the supply chain and the sanctity of hardware. Enterprise defenders have bigger headaches than worrying about the possibility of technically complex hardware-based attacks.
When it comes to hardware-based attacks, there is a big difference between potentially and actuality, Joe Fitzpatrick, a hardware researcher and trainer with Securing Hardware, told attendees at Kaspersky Security Analyst Summit. Just because something can be malicious doesn’t mean it will be bad. It can be an accident, or it may be due to non-security reasons.
Consider the original supply chain challenge—the problem of counterfeit products. These devices cost a bit less to make because they are using components other than what is specified, and may impact performance and operations. Products with counterfeit components may not be as a power-efficient or may not last as long. Counterfeits may disrupt operations (the component in question doesn’t operate very well outside of a specific temperature band but the environment is a really hot one) and pose a bigger risk to the business than the security damage a deliberate hardware implant may cause.

Joe Fitzpatrick had three very important lessons about how defenders should consider supply chain attacks.
Focus on Real Risks
Maintaining the integrity of the supply chain—ensuring that the product is behaving as designed, and that it has all the components it is supposed to have—is hard, even before considering the security impact of the changes. The idea that foreign governments may have added backdoors to software and hardware to get visibility into corporate networks is a serious security issue. Even so, most organizations have far more immediate concerns than launching full-scale investigations to analyze their equipment because of the 2018 report that nation-state actors had allegedly implanted chips on servers sold by Super Micro Computer, Fitzpatrick said.
“Does your threat model include $5 or $100 attacks? If not, why are you worrying about $1 million attacks?” Fitzpatrick said.
Fitzpatrick described “$5 dollar attacks” as the kind of hardware modifications that tricks the system into doing something it wasn’t originally designed to do. For example, modding a game console lets users play older games on the system that it otherwise wouldn’t. Another example is disabling the controls on a network switch limiting the number of ports or restricting the network speed. The “$10 to $100” range would be something like a Raspberry Pi hooked up to a network port in the server room as part of a Red Team exercise to gain access to the network.
There are far more of these low-cost attacks than there are technically complex ones. Enterprise defenders need to focus on issues that actually pose a risk to the organization, and not the potential one that sounds extremely scary.
“Ripping servers is a waste of time,” Fitzpatrick said, referring to concerns over the integrity of Super Micro servers. The more important question here is whether or not the enterprise has a hardware acceptance criteria when buying equipment from suppliers. Enterprises need to have conversations with their suppliers about what kind of supply chain security controls are in place to make sure they are really buying what they think they are buying.
“When you buy a computer, do you look inside? Some companies say yes, but most don’t,” Fitzpatrick said.

Joe Fitzpatrick speaks at Kaspersky Security Analyst Summit in Singapore.
Attacks in Context
When it comes to supply chain attacks, it is easy to forget that there are different levels of complexity, and different levels of difficulty in execution, independent researcher Andrew “Bunnie” Huang told attendees at the Kaspersky Security Analyst Summit. Some hardware modifications are extremely easy to execute, but they will also be easy to detect. Those are the ones that cost a handful of dollars to create and seconds to implement. On the other end of the scale, there are modifications that are extremely difficult to detect and require extremely expensive tools to even investigate. However, those will also be likely difficult to execute. Those will cost a million dollars and take months. The middle range, are those attacks that cost in the tens of thousands of dollars and a few weeks to execute.
The type of hardware tampering described in Bloomberg’s SuperMicro story is “literally one of the easiest things to detect,” Huang said. “You can just see it on the x-ray.”
While hardware implants—and other hardware-based attacks—are technically possible and security professionals should be aware of how potentially attacks can unfold, “validating hardware is harder than you think,” Fitzpatrick said.
“I have been telling you how hardware is going to undermine all of us,” Fitzpatrick said, but “we have a bigger risk with software.”

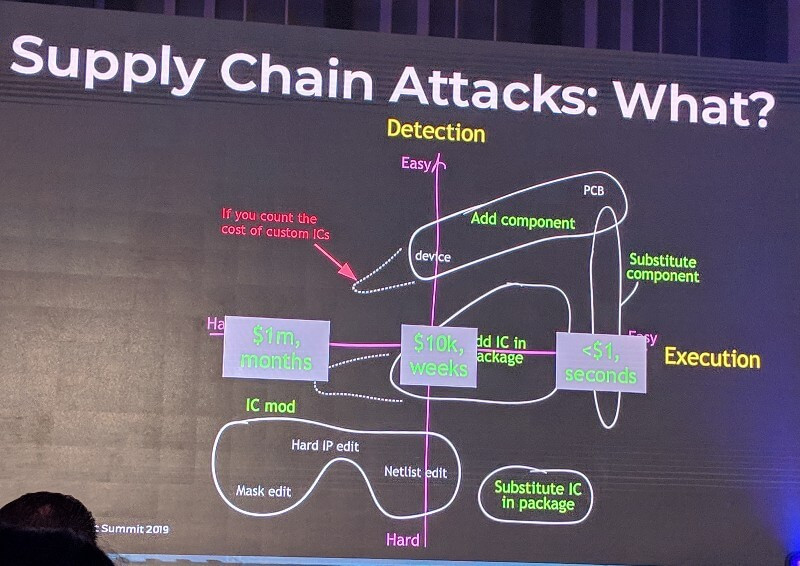
Andrew "Bunnie" Huang described different types of supply chain attacks, and categorized them by how easily they could be executed and detected. Source: Kaspersky Security Analyst Summit 2019.

