Google introduced a new Chrome extension which will automatically and securely check whether user passwords have been exposed in a data breach.
Called Password Checkup, the Chrome extension is Google's attempt to address the problem of password reuse on the Web. When the user attempts to log in to a website or application via the Chrome browser, the extension checks the password against an internal Google database containing billions of already-compromised login credentials. If the password has been compromised, the user will be alerted and prompted to create a new password.
"If we detect that a username and password on a site you use is one of over 4 billion credentials that we know have been compromised, the extension will trigger an automatic warning and suggest that you change your password," wrote Google research scientist Kurt Thomas and product manager Adam Dawes in the announcement.
Google said most U.S. websites are supported.
In the event of a data breach where passwords are stolen, users who already use unique passwords for each web application or service have less to worry about compared to those who reuse passwords. All they have to do is change that one password. Reusing passwords means having to change the password for every site that used the now-breached password.
Attackers take credentials stolen in data breaches and try to use them on popular online services, such as email, social media, retail, and financial services accounts to see if they can get access. The more places a password is used, the more likely these attackers will succeed in their attempts.
The number of password breaches also makes it difficult for individual users to stay on top of every incident and make sure they are changing the passwords right away. And just because the breach was a long time ago doesn’t mean the criminals won’t try. There is a collection of 2.2 billion passwords, some dating as far back as 2008, being passed around on criminal forums. Even if less than 1 percent of the passwords were still valid, that’s millions of accounts that could potentially be taken over.
Despite frequent reminders to not reuse passwords, the problem is still prevalent. A Harris Poll commissioned by Google surveyed 3,000 adults in the United States to understand what they think about online security and what they actually do. While 69 percent of people in the poll thought they did a good job protecting their online accounts, their actual behaviors suggested otherwise. Even though 59 percent felt their accounts were safer than those of the “average Internet user,” 65 percent reused the same password across multiple sites. The poll found that 51 percent had a favorite password they used for most sites. Only 24 percent of users in the poll said they used a password manager.
This service would help improve overall online security, but Google doesn’t ask users to hand over passwords to other sites—that would be asking for too much trust. Instead, Password Checkup relies on a combination of anonymization and cryptography to ensure that user credentials are not visible to Google. User credentials being entered on the site—either manually by the user into the login screen or by Chrome’s built-in password manager—are anonymized with an Argon2 hash function to create a search key for the password database, and also encrypted with elliptic curve cryptography. A technique called blinding create a secret search index to use on the database. The passwords are stored in the database in a hashed and encrypted form so someone at Google won’t be able to look at the values. The alerts are local to the machine the extension is visible on, so Google won’t be able to track which passwords had to be changed.
"We built Password Checkup so that no one, including Google, can learn your account details," Dawes and Thomas wrote.
Google isn’t really breaking new ground with checking passwords against a database of passwords collected from previous data breaches. Facebook, Netflix, and Microsoft are known for checking user credentials against known breaches. If the user tries to use a password combination that was already in a breach to log in to the sites, the sites alert the user and prompt for a change. Google does the same for its G Suite users—except it references its own internal database that Google’s threat research team compiled by trawling through data dumps and criminal forums. The database has currently over 4 billion compromised credentials.
"We already automatically reset the password on your Google Account if it may have been exposed in a third party data breach—a security measure that reduces the risk of your account getting hacked by a factor of ten," Thomas and Dawes wrote.
What the company is doing differently with Password Checkup is that it is providing the checking service for sites and applications outside its own ecosystem.
Mozilla does something similar with Firefox Monitor service, which notifies users if the site they are visiting has been part of a data breach. Firefox Monitor relies on security researcher Troy Hunt’s Have I Been Pwned to find out if user information has been compromised. Password managers such as LastPass and 1Password also rely on the Have I Been Pwned database.
Checking against known data breaches rather than dictionaries or lists of commonly used passwords is more effective “because it checks what real people have actually used in the past,” cryptography expert Kenn White wrote on Twitter. White noted that the latest NIST 800-53 guidance on “memorized secrets” recommends checking public breach databases.
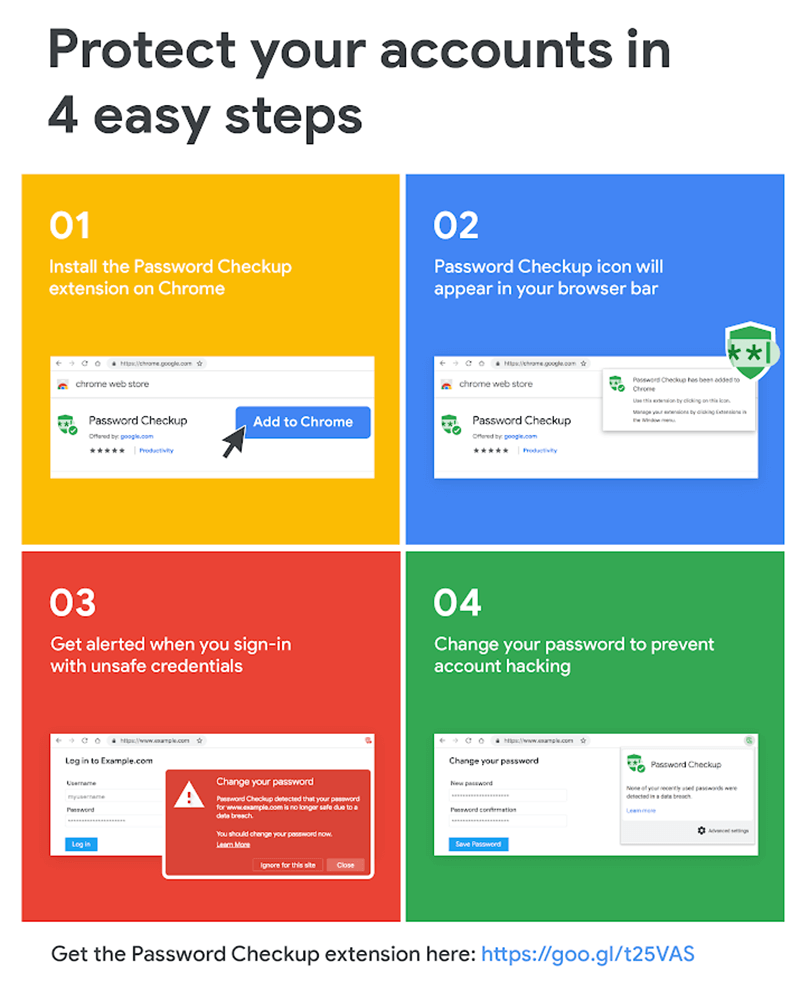
As a Chrome extension, Password Checkup prompts users to change passwords if the login combination has been used and compromised elsewhere. (Image source: Google)
