An analysis of real-world industrial networks found that industrial control systems and industrial internet-of-things are dangerously soft targets, with issues such as passwords being transmitted as plaintext making them susceptible to attacks.
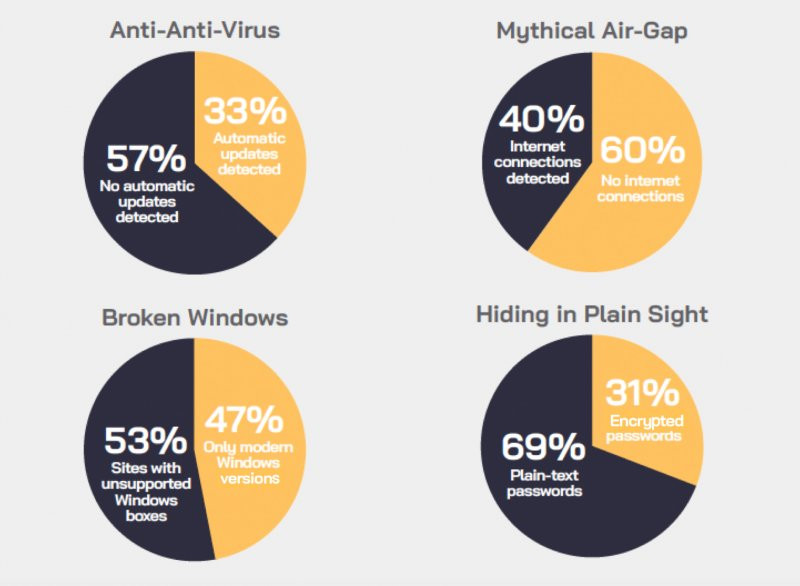
Many ICS and IIoT devices continue to rely heavily on legacy network protocols such as SNMP and FTP, and the fact that these protocols don’t encrypt their transmissions means the device credentials are transmitted as plaintext, said industrial security company CyberX in its latest Global ICS and IIoT Report. Based on analyzing network traffic from more than 850 production industrial sites around the world, the report found that 69 percent of industrial exposed passwords as plaintext within their networks. For example, SNMP v1, 2, and 2c communicate authentication information in the clear, which means attackers already on the network conducting reconnaissance can potentially capture these passwords. The passwords typically control access to older devices that can't be upgraded to modern protocols such as SNMP v3 or SFTP.
With the passwords in hand, the attackers can access critical systems and move deeper into the network.
A common perception in ICS security is that systems are air-gapped and thus safe from Internet-based attacks. The idea is that if systems aren’t accessible from the Internet, then there aren’t many opportunities for attackers to get onto the network in order to see the exposed credentials. Except for the fact that air-gapping is a myth for many industrial networks. CyberX found that 40 percent of industrial sites had at least one system directly connected to the Internet. Many of these operational technology networks may be connected to the corporate network for various reasons, such as delivering regular software updates or to sync and analyze the data being collected by the sensors. As a result, many administrators may be unaware that the systems could be accessed over the Internet.
Even if the devices themselves weren’t directly connected to the Internet, many of them are remotely accessible using remote management and access protocols such as RDP, VNC, and SSH. There was at least one remotely accessible device in 84 percent of the industrial networks, CyberX found. Remote management means administrators can configure and troubleshoot devices without having to be physically in front of them, but that also means attackers with stolen credentials can also access and manipulate the equipment.
Attackers are increasingly taking advantage of the fact that there are so many exposed systems on the Internet. According to Kaspersky Lab, the Internet was the source in 27.3 percent of attacks against ICS systems in the first half of 2018. Most of the attempts to infect industrial systems tended to be part of random attacks rather than targeted operations, Kaspersky said in its Threat Landscape for Industrial Automation Systems report.
“An interface between the industrial network and the corporate network is needed both to control industrial processes and to provide administration for industrial networks and systems,” Kaspersky said in the report.
Another common networking issue was related to the presence of wireless access points in industrial networks. Misconfigured WAPs can be accessed by unauthorized laptops and mobile devices, allowing attackers to potentially capture traffic, map the network, and launch attacks against specific endpoints on the network.
CyberX found WAP in 16 percent of industrial sites.
"We’re not here to create FUD, but we think it’s important for business leaders to have a data-driven view of ICS risk so they can ask the right questions,” said Dan Shugrue, senior director of industrial cybersecurity for CyberX.
There was a some good news amidst CyberX’s sobering analysis. While 53 percent of sites still had systems running outdated operating systems such as Windows XP, the number is significantly lower than last year, where three out of four sites had systems running legacy Windows systems. The improvement “may be directly tied” to WannaCry and NotPetya attacks. A number of manufacturing and transport organizations were heavily impacted by the attacks, giving other organizations a clear demonstration of the risks to their production environments.
Cyberx calculates the median risk across all of the ICS customer sites, and that figure seems to be improving. The median risk across customer sites was 70, an improvement over last year's 61. The median risk remains lower than the minimum recommended score of 80, but more organizations seem to be improving their overall security. The industries considered to have the most security maturity were assessed at the highest, with oil and gas industry having a risk score of 81, and the energy and utilities industry with a risk score of 79.
ICS operators should consider implementing measures such as continuous monitoring, more granular network segmentation, and threat modeling to prioritize mitigation efforts.
“Reducing ICS risk is a journey — most of these ICS networks were designed decades ago, long before cybersecurity was a key design priority,” Shugrue said.
SEO header image by Crystal Kwon on Unsplash.
CyberX report shows the air-gap remains a myth in ICS networks.
