Love’em or hate’em, there is no getting rid of the Internet of Things. Household appliances, consumer electronics, industrial systems, toys, even healthcare devices, are hitting the market with some kind of Internet connectivity. Instead of hating on them, let’s get them secure.
At a IoT security workshop during last week’s Security Analyst Summit, participants were given 30 minutes to work in teams and design a product that could be used to protect an average home. The assumption was the household had a few laptops, an entertainment system, a network attached storage box, mobile devices, and a smartlock for the door. Throw in a toy or two. All these devices were connected to a router/modem provided by the Internet Service Provider. The teams were to design something that could protect the devices could be connected to the router that could provide protection.
They solved all the security challenges of IoT. Except one.
Each team had a Raspberry Pi on the workbench, but the teams just had to design on paper and not worry about actually programming the Pi. One team designed an Internet Gateway, which would sit behind the router/modem and handle all the internal security for the home user. The other team designed a Smart Hub, which would keep all IoT devices on a network separate from laptops and storage devices.
The designs were awesome and sound from a security perspective. They solved all the security challenges of IoT. Except one. None of them would be usable by non-security users, said David Jacoby, a senior security researcher at Kaspersky Lab’s Global Research and Analysis Team. An average household would not be able to stay on top of network segmentation, VLANs, and monitoring the network. Even with the best user interface, it would still be too complicated.
"We have no idea how to do this,” Jacoby said.
The Internet of Things is an overused term, but it pretty much refers to anything that has an Internet connection, such as a home camera that lets you use your phone to see how your dog is doing, or sensors that transmit your electricity usage back to the power company. Very few of these devices have any kind of security controls: no data encryption, weak or no passwords, and no software update mechanisms. The team designs focused on protecting these devices from the big, bad attackers on the Internet.
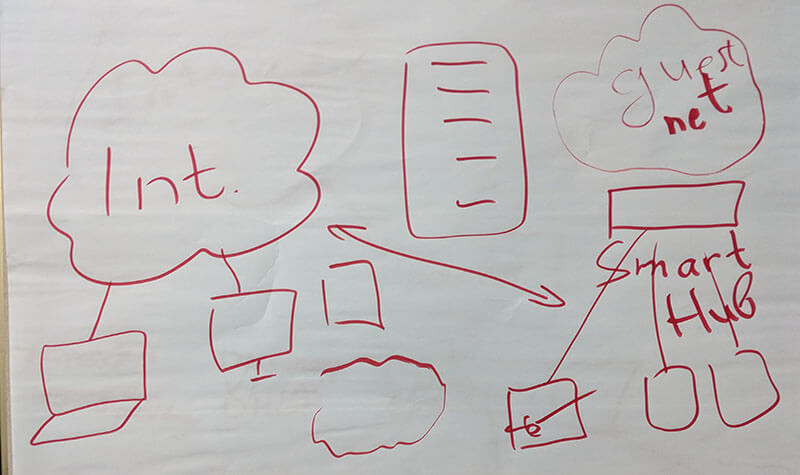

One team designed a Smart Hub, and the other designed an Internet Gateway. They were both sound from a security perspective, but that meant they were both too complicated for a consumer market.
The Internet Gateway segmented the network for laptops, smart devices, and guest devices, and had firewall rules to block certain types of inbound connections. To be honest, it sounded a lot like the BitDefender Box, except a lot more robust and with more features. The Smart Hub created a parallel network for visitors devices. There were restrictions on what the devices connected to the Smart Hub could see or do. Both teams offered users a way to tell what devices were even on the network in the first place.
Jacoby pointed out that the teams had completely ignored the fact that there were no standards in how IoT devices connected to the network. Routers, depending on the manufacturer and model, have different interfaces. Some devices have to be set up with a mobile app. Others are connected directly through a laptop to be configured. The proposals all assumed the devices were homogenous in how they connected to the network and how they were managed. Even the term “average household” was misleading because every home has different devices.
“These ideas don’t scale,” Jacoby said.
The workshop was humbling. The teams argued about the best approach, and it was hard to come up with a consensus design. There were great ideas, but quickly veered into too-complicated, and would not work for every household, every combination of devices, for every skill level. More importantly, the ideas depended on an ideal scenario--that vendors would standardize interfaces, manufacturers would follow industry best practices, and that our device would recognize different devices from every manufacturer. In retrospect, that was one of the hard things about living with the BitDefender Box--that there were some brands and models it had no idea what to do with.
Even the term “average household” was misleading because every home has different devices.
According to Jacoby, the best protection right now is to make sure each router has an extremely long and complicated password as the default password. Print it on a label, slap it on the router, and attackers can’t brute-force default passwords because they are strong and unique to each one. This keeps the routers, and all the devices at home connected to the routers, away from botnets. Relying on users to change the default password during setup wouldn’t be good enough, because there’s no guarantee users would set up a strong enough password.
The reality is that there are thousands and thousands of connected devices, and most of them will never be secure. If someone comes along and overwrites the firmware with something else, many of us will never know. The industry can rail against the device manufacturers and say IoT devices have to be secure until they are hoarse, but bottom line, that’s never going to happen. So if people are going to have IoT security, the industry is going to have to step up and provide something capable of securing these devices.
Except it isn’t that easy, and it’s time to recognize that this will be a hard problem to solve.
“At the end of the day, the best security minds can’t figure it out,” Jacoby said.