SINGAPORE——A large underground marketplace is taking carding and identity theft to the next level, as buyers can browse and purchase victims’ digital fingerprints that can be used to fool anti-fraud systems along with the stolen credit card numbers and user credentials.
The Genesis marketplace sells more than 60,000 “digital masks” which can be used for credit card fraud, Kaspersky Lab security researcher and evangelist Sergey Lozhkin said at the Kaspersky Security Analyst Summit. Prices range from as low as $5 to as much as $200 per account, according to the level of information available. Masks with data elements that can be used on multiple services and applications will be more expensive than those with fewer pieces of user information.
The digital mask is a “unique, trusted customer profile based on known device and behavior characteristics,” Lozhkin said.
Financial services organizations rely on digital fingerprints, or detailed customer profiles generated from user information and behavioral characteristics, to confirm the user performing the transaction is the account owner and not an imposter. For example, if the user tries to log in to a bank account from a new computer or a new geographic location, most banks nowadays pose a challenge by asking the user to verify something, such as entering a code that is sent to either the user’s phone or email Inbox or answering a security challenge question. If the user tries to change the shipping address on an Amazon order, the site’s anti-fraud tools may ask the user to re-enter the credit card information instead of using the saved card. These are all ways for the anti-fraud tools to make sure the unusual—potentially suspicious—event is not fraudulent.
"When a bad guy enters your credit card information, in most cases he won't succeed because the anti-fraud [system] will find him out as he's trying to enter multiple cards from one device," Lozhkin said.
Data points go far beyond login credentials—anti-fraud systems collect pieces such as screen size and resolution, user timezone, running processes, battery state, device operating system, the browser being used, installed plugins, the GPU on the device, and DNS information. Online behavior patterns include mouse movements, what kind of links get clicked on, and how the page is scrolled. The cookies saved on the user’s computer and even what tabs are open in the browser can be part of the user’s digital profile.
Criminals armed with this level of user information become digital doppelgangers, capable of fooling financial institutions’ anti-fraud systems, Lozhkin said. This kind of information can be copied or generated fresh, and Genesis, which researchers discovered in February, is the largest marketplace offering them for sale.
Genesis also offers a plugin for Chrmoium-based browsers that downloads and installs the digital mask into the attacker’s browser. With the plugin, the attacker can use a saved fingerprint, change an existing fingerprint, or generate a brand new one. The plugin can play a series of actions that spoofs the victim’s user behavior online, such as what links the user would click on and what parts of the page the user looks at. Buyers use the tool to search for specific types of stolen accounts by filtering on different types of criteria, such as sitename (eBay, Amazon, Chase), type of fingerprint data to use, and regional location.
With just one click, the attacker can launch the mask through a browser and proxy connection, Lozhkin said.
Threat intelligence company Digital Shadows found Genesis a year ago when the marketplace was still in beta and had information for approximately 1,500 users. The store claimed to be "the result of research conducted across the antifraud technologies used by 283 major banks and payments systems," the Digital Shadows Analyst Team wote at the time. The rate of growth (almost 4,000 percent) indicates the marketplace's rapid popularity in just a year.
The marketplace is going after Russian-language speaking buyers, Lozhkin said, noting that while the victims span the globe, the marketplace's page are all in Russian. At the time of Digital Shadows' report, none of the victims were Russian.
If the user has enabled two-factor authentication on the accounts, then the attacker won’t be able to get far even with the digital mask, Lozhkin said. Unfortunately, that isn’t as reassuring as it sounds, because so many sites and applications still don’t offer users the option to enable two-factor authentication. Major European banks, for the most part, have users confirm transactions by sending SMS messages. That level of two-factor authentication isn’t that widespread on American banks.
Financial institutions need to introduce more verification methods, such as biometrics. “In my opinion, this will require more proofs at every step,” Lozhkin said, noting that it shouldn’t matter if the user looks legitimate. Transactions should still require confirmation steps.
Lozhkin has notified law enforcement officials about the marketplace. His hope is that law enforcement will eventually be able to shut it down the same way the xDedic marketplace was shut down earlier this year.
Much of the research over the past few years have focused on sophisticated and complex attacks, but the fact remains that financial fraud remains the “easiest and most effective way” for cybercriminals to make money, Lozhkin said. Carding hasn’t really changed over the past two decades, and the techniques that make Genesis possible aren’t that new. What’s disconcerting is how these masks have become a commodity.
“So many fancy, so many sophisticated threats, but we haven’t even solved the basic problem,” Lozhkin said. “Carding is not dead.”
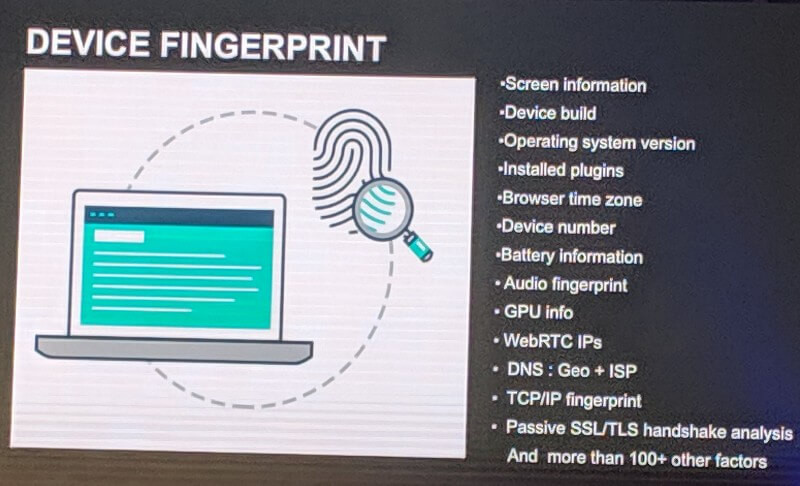
Digital masks are made up of many different pieces of information, including device information and user behavior characteristics. Source: Kaspersky Lab.

