A recently patched, high-severity Windows vulnerability, CVE-2017-0199, is being used in phishing attacks to deliver malware to users.
CVE-2017-0199 exploits a flaw in the Windows Object Linking and Embedding (OLE) Microsoft Office interface, allowing an attacker to take control of systems, steal or destroy data, and retrieve malicious files from a remote server and install them on a victim’s computer.
In a report from Kaspersky Lab, the number of attacked Microsoft Office users rose to 1.5 million in Q2 of this year. They found that 71% of all attacks on Microsoft Office users were carried out using this specific vulnerability, despite it being patched in April.
Targeting Electronics Manufacturing Companies
A new attack in the wild is using the vulnerability to target mainly electronics manufacturing companies. A phishing email appeared to be sent from a cable manufacturing provider, containing a malicious PowerPoint Slideshow (.ppsx) attachment, according to Trend Micro researchers.
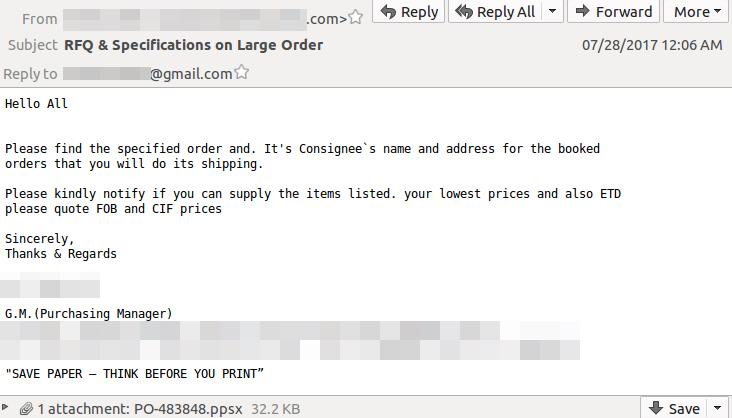
Source: Trend Micro
Once a user opens the PowerPoint file, the PowerPoint Show animations feature runs, downloading an XML file that runs PowerShell commands to download and execute a remote access Trojan (RAT).
In another analysis of a separate attack using the same Windows vulnerability, a phishing email refers to a Microsoft Word attachment as a purchase order, urging the reader to open and reply in order to make the shipment.
Attackers combined the use of an older vulnerability with a newer one, likely to avoid a Word user prompt that could tip off user suspicion, according to the Talos blog, which outlines the technical reasons why the attack wasn’t successful.
Update Microsoft Systems To Protect Them
While phishing still targets the weakest link - the user - there are still other defenses organizations can take to reduce the impact or success of a phishing attempt. One way is to practice basic security hygiene by patching your systems with the latest updates in order to protect against these attacks. This particular CVE is addressed by Microsoft’s April updates.
In an analysis of Duo’s data on devices across enterprises in every industry, we found that 59% of endpoints are running an older version of the Microsoft operating system, Windows 7. Older versions, if not patched, may leave enterprises vulnerable to known flaws that make it easier to compromise machines and steal data. Get more device insights in The 2017 Duo Trusted Access Report.

Microsoft has announced the end of support for Windows 7 by Jan. 14, 2020, and warns against using it; urging enterprises to migrate to Windows 10. The software giant cites higher operating costs, increased maintenance, and time lost due to attacks on its long-outdated security architecture as reasons to make the switch.
Learn more about how phishing attacks work in The Trouble With Phishing, a guide that details the problems around phishing, how it works, and how Duo can be leveraged as a solution.
