Kaspersky researchers have found links between a malicious campaign targeting Android users in Southeast Asia and the OceanLotus advanced persistent threat group.
The PhantomLance espionage campaign relied on dozens of spyware apps within the official Google Play marketplace as well as third-party marketplaces such as APKpure, Kaspersky researchers Alexey Firsh and Lev Pikman wrote on Securelist. While the campaign was first detected in 2019, the researchers believe the campaign has been active since at least 2016. One of the domains used in the campaign was registered in December 2015.
The most recent sample appeared on Google Play in November 2019. While all the apps have been removed from the marketplaces, the researchers believe the campaign is still ongoing, Firsh said during a presentation at the SAS@home virtual conference.
The initial spyware app was discovered by Dr. Web in July 2019, and Kaspersky researchers were able to find other apps in Google Play and other marketplaces that shared multiple code similarities. The apps used in this campaign were different from other types of Trojans that typically get uploaded to Google Play because they were focused on stealing information, not displaying ads or stealing money. The main purpose of the spyware apps was to gather information from the targeted device, such as geolocation, call logs, contacts, and SMS messages. The app also gathered a list of installed apps and device information such as the handset model and operating system version. The spyware could use the collected information to download and execute malicious payloads tailored for that device environment, as well as upload files to remote servers.
“PhantomLance has been going on for over five years and the threat actors managed to bypass the app stores’ filters several times, using advanced techniques to achieve their goals,” Firsh said.
The original version of the apps uploaded to the marketplaces did not contain any malicious code, most likely to make it easier to pass the marketplace’s filters and automated checks. Once the app was on the marketplace, the attackers updated the code to include malicious payloads and droppers to execute the payloads. Adding the different malicious features across different versions helps the apps bypass the marketplace filters, the researchers said.
The latest Google Play sample included a clear payload. Other versions the researchers analyzed utilized an interim step to drop an additional executable file on the Android device.
The manifest file for the apps don’t list all the permissions it requests because the Android permissions are requested dynamically and hidden inside the executable. In cases where the Android devices had been rooted, the malware is able to access an undocumented API function to get the necesary permissions.
“If the root privileges are accessible on the device, the malware can use a reflection call to the undocumented API function ‘setUidMode’ to get permissions it needs without user involvement,” the researchers said.
The attackers behind this campaign put in some effort to make the apps look legitimate, such as building fake developer profiles associated with legitimate-looking GitHub accounts.
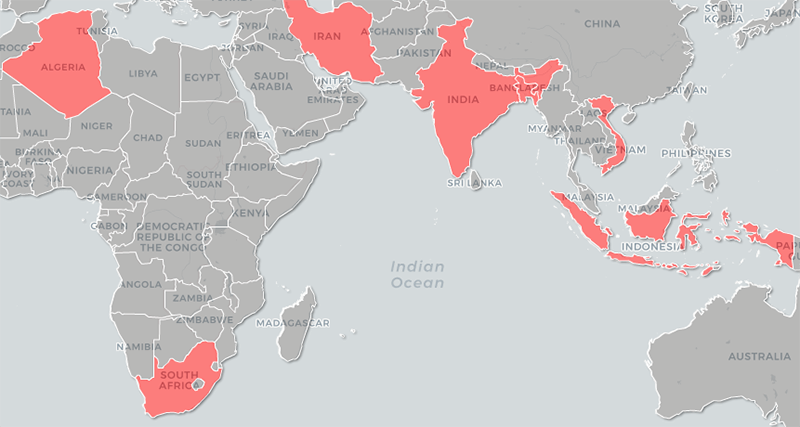
The PhantomLance campaign has primarily targeted Android users in Southeast Asia, although there have been infections in other regions. Source: Kaspersky
Usually, attackers who successfully upload a malicious app into an official app store like Google Play “invest considerable resources” to promote the app to get more victims to download and install the app. In this case, however, the attackers appeared to be interested in only a specific set of victims.
There have been around 300 infection attempts on Android devices in countries such as India, Vietnam, Bangladesh, and Indonesia since 2016, according to statistics collected by Kaspersky Security Network. There were also some victims in Nepal, Myanmar, and Malaysia, the researchers said. Vietnam had the greatest number of attempted attacks, and some of the samples the researchers found were exclusively made for Vietnamese victims.
The spyware apps were at least 20 percent similar to those used in an older Android campaign associated with OceanLotus (APT32), a threat group believed to have ties to the Vietnamese government. OceanLotus (APT32 or APT-C-00) has been linked to Android campaigns targeting corporate and government organizations in Vietnam and China between 2014 and 2017. Code similarities Kaspersky researchers found include macOS backdoors and infrastructure overlaps with Windows backdoors. As a result of these commonalities, Kaspersky researchers have “medium confidence” that OceanLotus is behind the PhantomLance, and that it is the successor to the earlier campaign.
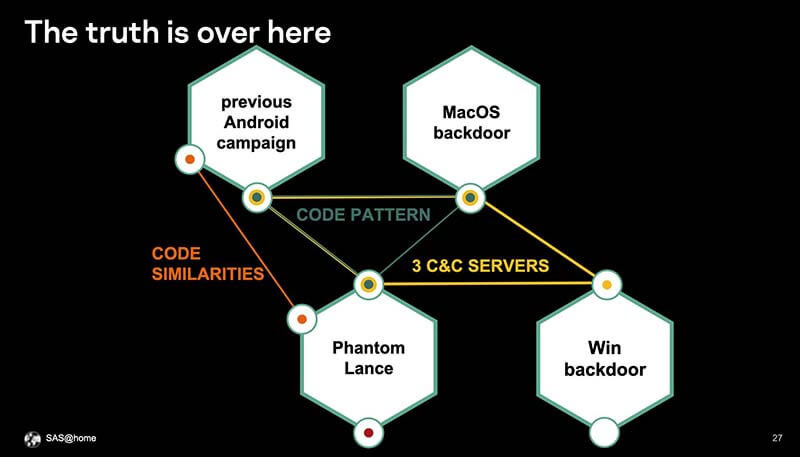
The attack code used in PhantomLance had enough similarities and overlaps with the code previously attributed to OceanLotus APT, prompting Kaspersky to say with "medium confidence" OceanLotus is behind PhantomLance. Source: Kaspersky, SAS@Home.
