Score one for the rule of law. U.S. law enforcement officials have taken down a complex ad-fraud operation that successfully bilked tens of millions of dollars from online advertisers.
The 13-count indictment from the United States Attorney’s office in the Eastern District of New York against eight defendants detailed how the gang created fake versions of thousands of legitimate websites and used botnets to generate fake traffic to those websites as part of the 3ve (pronounced “eve”) operation. The fake websites took bids from ad networks on which ads to display, and then used the fake click-throughs to collect ad revenue from the advertisers.
The companies paid the group for the ads that appeared on those websites, even though real humans never visited those sites, let alone saw any of the ads.
"At its peak, it controlled over one million IPs from both residential botnet infections and corporate IP spaces, primarily in North America and Europe,” Per Bjorke, a product manager for ad traffic quality at Google wrote on the Google Security blog.
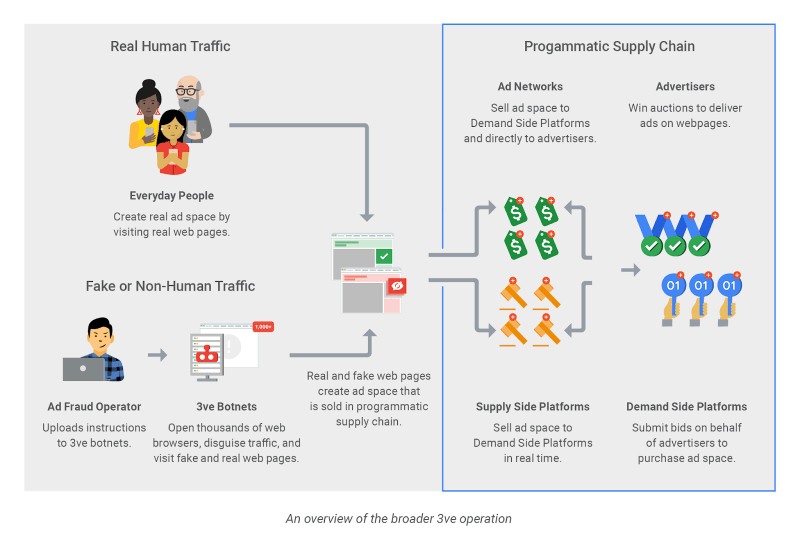
The 3ve operation abused the intricate system of trust between advertisers, publishers, ad networks, and demand platforms by placing ads on counterfeit sites and then simulating fake traffic from virtual visitors. (source: Google)
Google and White Ops outlined the “unique sub-operations” within 3ve in a joint summary of the takedown effort. The first sub-operation, which netted the group more than $7 million in advertising revenue between September 2014 and December 2016, centered around the Methbot network. Methbot had business arrangements with other ad networks to place ad placeholders on websites. Instead of putting these placeholders on real websites, they were placed on 5,000 counterfeit versions of those websites. The group then used the Miuref (also known as Boaxxe) malware to control more than 1,900 servers in commercial data centers in Dallas and elsewhere to create fake traffic. They leased more than 650,000 IP addresses, mapped them to the servers, and made it look like those addresses were actually endpoints belonging to individuals.
The simulation went beyond just making it seem like people were visiting the website, but also specific human-like behavior such as using a web browser, making it look like a mouse was moving around the page and scrolling down the screen, starting and stopping a video player, or even making it look like the “user” was logged into Facebook during the visit.
The group didn’t need millions of machines with Miuref since the servers in data centers are powerful and able to handle heavy loads, according to Symantec’s summary of the operation.
The companies paid the group for the ads that appeared on those websites, even though real humans never visited those sites, let alone saw any of the ads.
The second sub-operation, generating $29 million, developed an intricate infrastructure of command-and-control servers controlling 1.7 million computers. The machines were infected with the Kovter Trojan (an evolution of Windows fileless malware Poweliks, said Symantec), which would run a hidden instance of the Chrome web browser to load the fake websites. The malware installed only on systems that didn’t have security software running, and executed the click-fraud part of the operation only if its IP address was in a certain area with a specific internet service provider.
Google estimated 3ve at one pointed generated anywhere from three to 12 billion ad bids per day. 3ve wasn’t targeting a specific player, but was undermining th trust and integrity of the whole advertising ecosystem. Even so, Google’s Bjorke was careful to note that 3ve’s bid request volume was still just a small percentage of overall bid request volume.
"3ve’s sheer size and complexity posed a significant risk not just to individual advertisers and publishers, but to the entire advertising ecosystem," Google said.
Identifying and dismantling 3ve required coordination between multiple entities. A working group of 16 organizations, which includes vendors such as Google, White Ops, Proofpoint, Symantec, and Malwarebytes, as well as law enforcement officials from the U.S. Department of Homeland Security and the FBI’s Internet Crime Complaint Center, took part in the takedown effort. Law enforcement executed seizure warrants to sinkhole 23 internet domains and 11 search warrants at 11 different server providers to seize 89 servers that operated the Kovter-based botnet. Google said bid request traffic from 3ve’s infrastructure came “close to zero” within 18 hours of the takedown.
3ve wasn’t targeting a specific player, but was undermining th trust and integrity of the whole advertising ecosystem.
The indictment accuses eight defendants, from Russia, Ukraine, and Kazakhstan, of wire fraud, computer intrusion, aggravated identity theft, and money laundering. One was arrested last month in Malaysia and the other earlier this month in Estonia, the Justice Department said. One of the defendants—the “CEO” of the group, is Aleksander Zhukov, who was recently arrested in Bulgaria. They are all awaiting extradition to the United States. The remaining five remain at large.
Google wants to see industry initiatives such as the Interactive Advertising Bureau (IAB)’s ads.txt standard, and other anti-fraud efforts from Trustworthy Accountability Group (TAG), Media Rating Council, and the Joint Industry Committee for Web Standards to gain traction. Many buy-side platforms and exchanges offer refunds for invalid traffic, which help cut off the revenue stream for criminals.
“While ad fraud traditionally has been seen as a faceless crime in which bad actors don’t face much risk of being identified or consequences for their actions, 3ve’s takedown demonstrates that there are risks and consequences to committing ad fraud,” Bjorke warned.
