It is notoriously difficult to quantify security impact and risk—such as estimating how much money would be saved by deploying a certain security control, or the financial impact in case of a breach or attack. The latest research from Cyentia Institute provides security leaders with a solid starting point to answer some of these questions.
Security leaders need to be able to quantify security risk and rank it in relation to other risks in order to make informed decisions. In the Information Risk Insights Study (IRIS), Cyentia researchers analyzed the dataset spanning tens of thousands of security events over the last decade provided by insurance data provider Advisen to develop models which risk managers can use to make informed decisions regarding their cyber risk, said David Severski, a senior data scientist at Cyentia.
"We're never going to have perfect information, but we can use information that we have available to make better decisions and not just a finger-in-the-wind type of analysis," said Severski.
Cyentia analyzed organizational risk factors across multiple dimensions, including Fortune 1000 rankings, industry sector, market share, organization size, and annual revenue. The dataset includes both headline-grabbing major incidents and smaller, minor, less costly breaches that don't need to be disclosed and aren't "material enough for annual reports." The advantage of having such a large dataset is that organizations can use industry-tailored models to begin their conversations about the frequency and financial impact of incidents, Severski said. It is also a helpful way to compare an organization’s level of risk with industry peers.
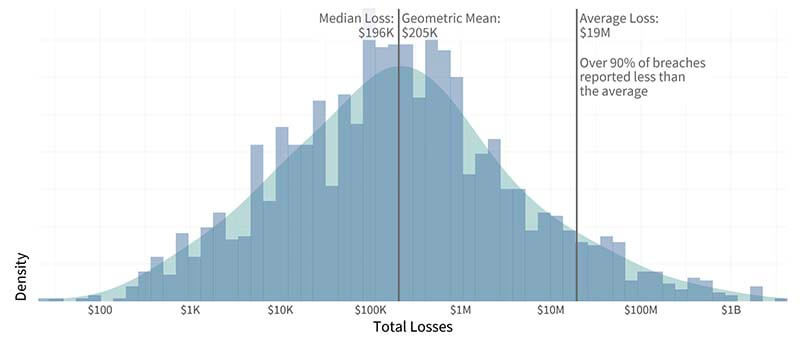
Distribution of breach losses over ten years: The average cost of a breach appears at $19 million, but 90 percent of breaches fall below that amount. That’s because actual losses incurred tend to have a long tail of really expensive incidents, which skews the mean. The median provides a better estimate of typical breach losses at around $200,000. (Source: Figure 10, IRIS, Cyentia Institute)
Estimating Breach Costs
Financial losses as a result of a security incident typically run about $200,000, according to the IRIS report. However, 10 percent of breaches exceeded $20 million in losses. This is why IRIS also grouped the datapoints to determine what losses looked like for a "typical" event and an "extreme" event. A large organization experiencing a "typical" security incident should expect losses of about $292,000, while a small-to-medium-business would see about $24,000.
Many security leaders rely on a “cost per record” metric in order to estimate losses after a breach. Severiski called this practice “flat-out harmful,” as it can result in $1.7 trillion of error due to overestimating and underestimating losses. (The calculation for this can be found in IRIS, Figure 14)
It is logical that total losses would correlate with the size of the breach, or the number of records compromised, but the data of known incidents and the losses reported for those incidents show that "losses increase by some percentage as the records affected increase exponentially," the IRIS report said. Larger breaches do cost more, but "but it’s definitely not a linear relationship," the report's authors wrote.
As part of the analysis, Severski took the each known event in the dataset and calculated the "cost-per-record" value. It turns out cost-per-record appear to be higher for smaller breaches. At a certain point, the economies of scale, the idea that the per-unit cost of something declines when there is enough of that something, kick in and the cost per record drops to mere pennies for large events. About a quarter of the cases cost $2,5000 per record, which is far more than the $150 figure commonly used in the industry calculations. The ransomware attacks against vulnerable MongoDB databases in 2017 came out to $0.0000003 per record in this model.
A single cost-per-record metric simply doesn’t work and shouldn’t be used," Severski wrote in the report. "It underestimates the cost of smaller events and (vastly) overestimates large events.
The point is not that organizations don't need to think about the number of exposed records in a breach. Instead of multiplying that number against an arbitrary number, Wade Baker, partner and co-founder of Cyentia Institute, recommended treating the figure as a probability. An exposure of 1,000 records have a 6 percent chance of exceeding $10 million in losses. A massive breach of 100 million records, on the other hand, has a greater than 50 percent chance of costing at least $10 million in losses.
The researchers also looked at differences across industries and found that government agencies, information services, financial firms, and educational institutions are the most likely to have a breach or attack. That risk could be higher because of the type of information they have—classified documents, intellectual property, financial details, personnel and customer records—but it could also be the fact that these industry sectors tend to be highly connected, with many systems connected to the network and Internet.
Information services and retail sectors show “abnormally high losses that exceed many other sectors by a factor of 10,” the report found.
Construction, agriculture, and mining are on the lowest end of the curve, and that may be because of the difference in the type of technology they rely on.
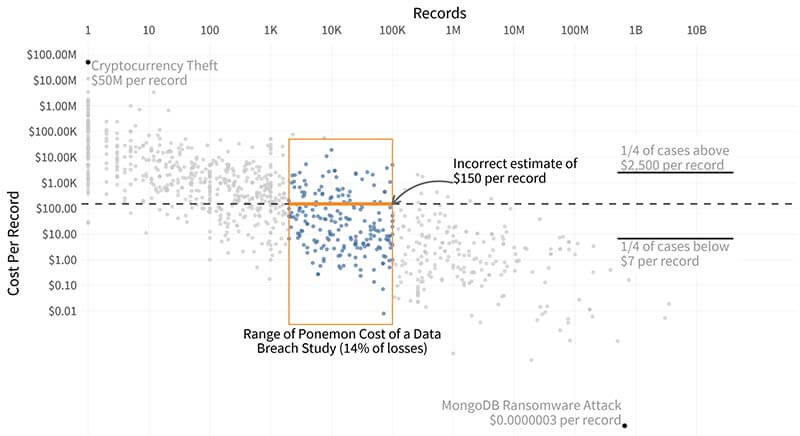
Calculating the cost-per-record value for each known event in the dataset showed that the cost-per-record appear was higher for smaller breaches. For larger breaches, the cost per record drops to mere pennies. (Source: Figure 13, IRIS, Cyentia Institute)
Size Matters, With a Twist
Based on Advisen data, researchers found that over 60 percent of Fortune 1000 companies experienced at least one cyber incident over the last decade. This makes sense, since larger corporations make bigger targets and are likely to have bigger incidents—and those are the ones that get reported, Baker said.
The likelihood of a Fortune 1000 firm would have an incident was one in four, or 25 percent, in a given year, according to the IRIS data. The likelihood of a Fortune 1000 company having to deal with 10 or more cyber loss events was 3 percent. When the researchers focused on the larger companies—those in the Fortune 250—the likelihood of experiencing an incident was higher, at 50 percent.
Not being a mega-corporation reduces the likelihood dramatically, since smaller companies have a 2 percent probability they will have even a single event. One in 1000 SMBs are likely to experience a breach or similar incident in a given year, and only one in 100,000 will wind up dealing with 10 incidents.
Yes, size matters, but that doesn’t mean SMBs don’t have to worry about an attack or a breach. The likelihood may be low, but as Severski wrote in the report, “There are a lot of SMBs out there.”
And size also matters when it comes to the financial impact, except in reverse. IRIS analyzed incidents to find the cost of a “typical” event and an “extreme” event—those that impacted 3 percent of the organizations. For the Fortune 1000 company, a “typical” event would lead to $750,000 in losses, and an “extreme” event $77 million. For an SMB, a typical event would be about $79,000 in losses and an extreme event would be $8 million.
In terms of actual dollars, the Fortune 1000 company would be the one harder hit, except they also have more revenue to help absorb the loss. For these large organizations, the incident cost for a typical breach was well under 1 percent of annual revenues, according to the IRIS study. In contrast, the incident cost for a typical breach for the SMB was a quarter of annual revenues.
The Fortune 1000 may be writing a larger check, but the SMB is the one that is going to be hurting.
Risk managers and analysts focusing on the the cost-per-record would miss the actual impact of the breach. A breach doesn’t necessarily have to mean a business-ending event, but it is a material event the organization has to report. Being able to estimate potential impact and assess anticipated costs will prevent organizations from overspending, and to make decisions that are actually in line with their risk tolerance, Baker said. Having a realistic cost for a breach is necessary for better planning, and can help guide response after a breach.
Risk isn’t one-size-fits-all, Baker said. Organizations can make better decisions about the risks they face once they take into account factors more than just the size of the incident.
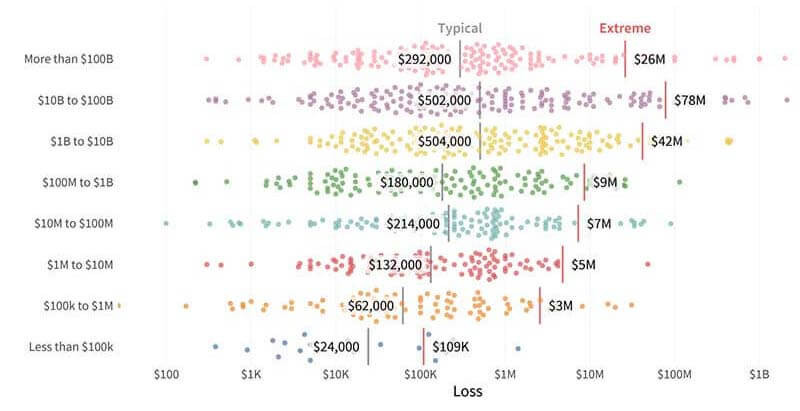
Distribution of breach losses by firm size (in revenue) with estimates for typical and extreme events: There is a difference between "typical" and "extreme" breaches. (Source: Figure 16, IRIS, Cyentia Institute)

