There used to be a time when a signed Windows executable file meant it was a file from a legitimate organization and safe to use, and malware was typically unsigned. That assumption is no longer a good one as attackers are increasingly signing their attack tools with valid certificates purchased from well-known certificate authorities.
Thousands of malware samples uploaded to VirusTotal have been signed with a valid certificates from well-known certificate authorities, said researchers from Chronicle. Researchers identified 3,815 signed malware samples (hashes here) which had been uploaded to the scanning service over a one year period leading up to May 7. The certificates came from CAs such as DigiCert, Entrust, GlobalSign, Go Daddy, Sectigo, Symantec, Thawte, and VeriSign.
“Since its inception, the process of cryptographically signing a piece of code was designed to give the Operating System a way to discriminate between legitimate and potentially malicious software,” Chronicle wrote.
More samples are likely, as this is a conservative count. Researchers focused only on Windows portable executable (PE) files, excluded samples that had less than 15 detections, and filtered out any files considered borderline malicious.
This system of trust doesn’t work when malware authors can easily purchase certificates from certificate authorities and their network of resellers to give their code a sign of legitimacy.
"Code signing certificates establish trust for code, apps, containers, updates for everything from mobile phones to laptops to servers to airplanes," said Kevin Bocek, vice president of security strategy and threat intelligence at Venafi. "Code signing certificates are the type of machine identity that made Stuxnet so virulent and successful: they allow attacker to operate with impunity even in the most hardened security environments.
Chronicle found that Sectigo, formerly known as Comodo, had issued the highest number of digital certificates which were used to sign malware over the observed time period, with nearly 2,000 certificates. Thawte and VeriSign came in second and third most popular CA when it comes to signed malware. The top six CAs that signed certificates of 100 or more malware samples accounted for about 78 percent of the signed malware that had been uploaded to VirusTotal, Chronicle said.
Considering that Sectigo is the largest commercial certificate authority, it makes sense that a larger share of the market means that attackers are more likely to use that CA, as well.
Attackers aren’t even bothering to pretend to be an existing company, said Brandon Levene, the head of applied intelligence at Chronicle. Instead of spoofing a well-known company, the attackers are just signing the malware as themselves. “This study has indicated that the majority of samples are just buying Code Signing certs under the guise of quickly created LLCs (or other organizations),” Levene said.
There used to be a time when malware signed with a legitimate certificate was the mark of a sophisticated, nation-state-backed attacker. That is no longer the case, as attackers of all types can obtain valid certificates from certificate authorities just by claiming to be a business.
“Signed payloads are no longer solely within the domain of nation-state threat actors stealing code signing certificates from victims; they are readily accessible to operators of crime focused malware,” the researchers wrote. “Expect to see signed malware reported more frequently.”
There are plenty of opportunities for attackers to misuse code signing certificates, and even the most advanced security tools can be fooled by code signed with valid certificates, Bocek said.
“If there is a single cyberweapon that can inflict maximum damage it is code signing certificates," Bocek said.
CAs are revoking the certificates when they find out they are being abused, but the rate is still pretty low. About 21 percent of samples with abused certificates have been revoked, as of May 8, Chronicle said. It is possible that the number of revoked certificates is actually higher since the data set would reflect the change only if VirusTotal had rescanned the sample after the certificate was revoked. CAs may have their own procedures for monitoring how the certificates are being used, but it is more likely that they are revoking after they receive reports from outside parties about the fraudulent use.
"I have seen times where social media was used to call out CAs on specific malware samples and campaigns but am unsure what monitoring (if any) is in place for CAs to vet software their certs appear in,” Levene said.
Interestingly, Thawte had a higher rate of revoked certificates, as it had revoked 306 certificates, or about 60 percent of the fraudulently used certificates it had issued. Sectigo had revoked 293, or about 17 percent of the fraudulently used certificates.
The ease of getting the code-signing certificates from the CAs directly or through the network of resellers suggests there should be a more stringent process for validating the buyers. Some due diligence before selling the certificate would be better than revoking the certificate afterwards, so that malware signed with that certificate can't cause as much damage.
“While malware abusing trust is not a new phenomenon, the popular trend of financially motivated threat actors buying code signing certificates illuminates the inherent flaws of trust based security,” the researchers wrote.
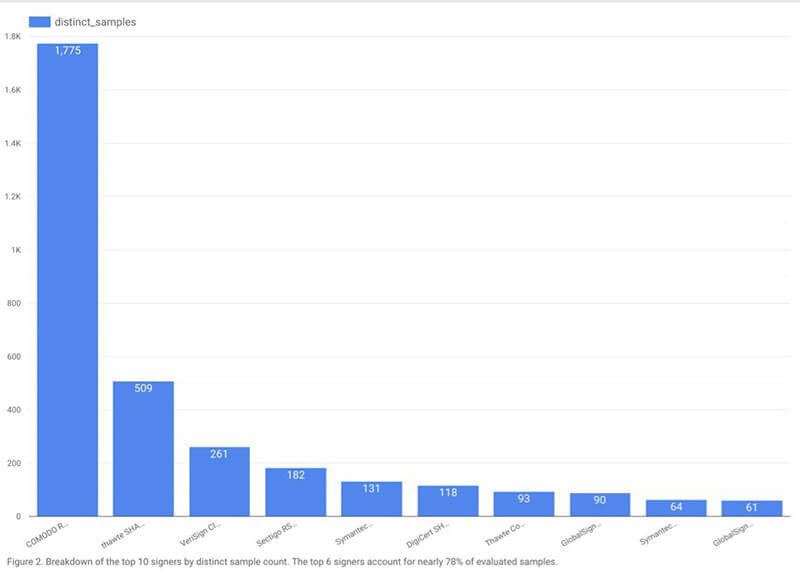
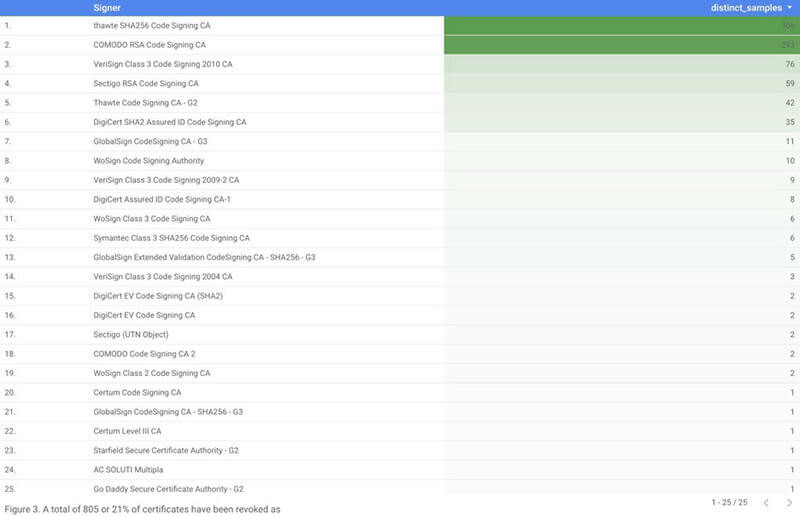
Sectigo (previously known as Comodo)—signed 3.5 times more samples than Thawte, which signed twice as many samples as VeriSign. However, Thawte revoked more certificates than Sectigo. (Source: Chronicle)
