There’s something for everyone in Verizon’s Data Breach Investigations Report. Hacking remains the primary attack method, and the use of malware is declining. While external attackers perpetuated the majority of the data breaches in the report, the industry breakdown shows that insider threats accounted for half of the incidents in healthcare. Money continues to be the primary motivator for these attacks, and data breaches as a result of misconfigured systems are on the rise.
Attackers are more likely to use stolen or lost credentials than malware in their attacks, Verizon said in its Data Breach Investigations Report. Malware infections dropped from almost half of all security breaches in 2016 to 22 percent, which is the lowest it has been in all the years the DBIR team has been tracking this statistic. Hacking—which includes brute-forcing passwords—remains the primary attack method at 45 percent, and social attacks—including social engineering—was found in 22 percent of the reported incidents.
In its 13th year, the DBIR research team analyzed incidents Verizon’s incident response team investigated as well as reports received from 81 contributing organizations from 81 countries. Out of the 157,525 reports analyzed, 32,002 met the team’s definition of an incident, and 3,950 were confirmed breaches. The report differentiates between an incident, which is a security event that “compromises the integrity, confidentiality or availability of an information asset,” and a breach, which is an incident where data is confirmed to have been exposed to an unauthorized party. In the case of an incident where data could potentially have been exposed, but hasn’t been confirmed that it was, that incident would not be considered a breach under DBIR’s definitions.
Of the breaches that was the result of hacking as the primary method, 80 percent involved brute-force or using lost or stolen credentials, the report said. Attackers are sitting on a collection of billions of credentials amassed from past data breaches and leaked password lists over the past few years.
“We think that other attack types such as hacking and social breaches benefit from the theft of credentials, which makes it no longer necessary to add malware in order to maintain persistence,” said researchers.
As far as the criminals are concerned, there is little to no risk in reusing the list of stolen credentials, and plenty to gain when one set of credentials actually works, said Bob Rudis, chief data scientist at Rapid7. This type of attack will continue to be used until organizations become more consistent about implementing multi-factor authentication across the board.
“Zombie credentials never die, they just get re-used in every gosh darn attack,” Rudis said.
Among social attacks, phishing was the top method. Those credentials may have been stolen using phishing—which was the most common form of social attack—or exposed at an earlier time in a different attack. The report also found that click rates on phishing rates are mere 3.4 percent, proving, yet again, that criminals don’t need a lot of victims to be successful with their phishing campaigns. They just need one person to let them into the network and they can use other techniques to move around and get what they need.
Lost or stolen credentials are much easier to obtain, but there is another reason why they are becoming more commonly used than malware. It is easier to bypass antivirus programs and other security software if the entry point looks like a benign user login. In cases where malware is used, the most common forms are password dumpers, data captures, and ransomware. Office documents and Windows applications are still preferred for malware.
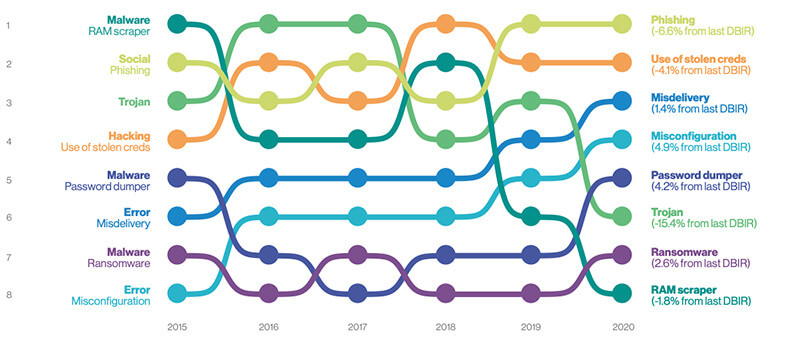
The main trends in the Data Breach Investigations Report have changed over the past few years. Malware attacks peaked in 2016, and since then have been declining, while phishing and credential theft are on the rise. (Source: Verizon Data Breach Investigations Report 2020, Figure 6)
The report suggested some improvements in overall enterprise patching strategy, noting that very few of the incidents in the report were due to a lack of patching or a missed patch. While there are lots of vulnerabilities discovered, "a relatively small percentage of them are used in breaches," the researchers wrote. While exploiting vulnerabilities remain the second common attack method for attacks that used hacking (as opposed to malware or social attacks), vulnerability exploits have not been a major cause of security incidents within the last five years, the report found.
"In our security information and event management (SIEM) dataset, most organizations had 2.5 percent or less of alerts involving exploitation of a vulnerability," the report found.
More companies appear to be patching their IT assets in a timely manner, which is helping to prevent attackers from exploiting known software vulnerabilities. The researchers determined this by looking at organizations with the Eternal Blue vulnerability present on their systems and those without. They found that systems that were vulnerable to Eternal Blue were also vulnerable to everything from the last decade or two. And organizations that patch seem to be able to "maintain a good, prioritized, patch management regime," the report said.
"Once again, no, each new vulnerability is not making you that much more vulnerable," the report said.
Industry Differences
External attackers were responsible for the majority of the data thefts the research team analyzed. In general, external attacks made up 70 percent of the data thefts, compared to 30 percent for insider threats. Over the past few years, Verizon’s researchers have noted the increase in insider threats, and in this year’s report, the team said the uptick is more likely due to increased detection and reporting, rather than any increase in the number of employees acting out of actual malice.
“It is a widely held opinion that insiders are the biggest threat to an organization’s security, but one that we believe to be erroneous.”
The industry snapshot is one of the most valuable parts of the DBIR, as the researchers map the overall trends against each industry sector. In the case of insider threats, the healthcare sector has a bigger problem than others, as the split is nearly 50 percent between external and insider attacks. Malicious insiders in healthcare include simple human error, and employee misuse, such as medical workers accessing patient records out of curiosity or entertainment.
The attack methods also differ by industry. The most common attack method against hospitality and food services used to be related to point-of-sale systems. Now the sector is more likely to be targeted by malware and web application attacks. Web application attacks were also a big problem for financial and insurance industries. Credential theft was the most pervasive in retail.
Ransomware is the top threat for the education space, as 80 percent of malware infections in the sector involved some kind of ransomware. Phishing attacks were used in 28 percent of breaches in the educational services industry, and 23 percent of the breaches were the result of lost or stolen credentials.
In previous years, misusing privileges was a big problem for the healthcare industry. Last year’s report saw 23 percent of attacks involving privilege misuse, compared to this year’s mere 8.7 percent.
“This year, we saw a substantial increase in the number of breaches and incidents reported in our overall dataset, and that rise is reflected within the Healthcare vertical,” said researchers. “In fact, the number of confirmed data breaches in this sector came in at 521 versus the 304 in last year’s report.”
Exposed Servers
Over the past year, there have been numerous reports of researchers uncovering misconfigured cloud servers or other systems, exposing data to anyone who happened to look. These incidents are now showing up in the DBIR, and misconfigured, or poorly configured systems make up more of the incidents in the DBIR than in previous years. Misconfiguration (17 percent) and data misdelivery (8 percent) combined exceeded the proportion of malware attacks in this year's data set. Most of these systems have been found by security researchers and unrelated third-party entities.
The report found that misconfigured systems are ubiquitous across industries. It isn't as if some sectors are more pront to make these mistakes than others.
“Errors definitely win the award for best supporting action this year,” the report said, noting they are “equally as common” as social breaches and more common than malware. Hacking is higher, but that is related to credential theft.
“It is no real surprise that naked S3 buckets and wide-open databases received a significant mention in the DBIR,” Rudis said, noting that the team finds “millions” of SMB servers, databases, and other inappropriately exposed services during its Project Sonar scans. While it may be the case that the number of systems being misconfigured isn’t necessarily on the rise, but just that people are getting better at finding them, organizations need to change existing processes to reduce configuration errors.
“Organizations must implement stronger controls and have finely honed practices and playbooks for deploying services safely,” Rudis said.
Faster Detections
An interesting silver lining in the DBIR: the number of copanies discovering incidents in days or hours continues to go up. Other industry reports have also recently highlighted this downward trend, although perhaps not to the extent shown in this report. One of the reasons for DBIR's more positive outlook may have to do with the fact that the report includes reports from managed service providers. A quarter of the organizations in the report still took months to detect the breach.
“All in all, we do like to think that there has been an improvement in detection and response over the past year,” said researchers.
The fact that breaches are detected sooner than before “matters little to ransomware attackers,” Rudis said. The criminals behind ransomware want the victims to know right away that the system has been compromised because they want to get paid.
“We need to keep improving this statistic, but also need to work even harder on preventing phishing attacks and shoring up internal configurations,” Rudis said.
Denial-of-service attacks spiked over the past year, while cyber-espionage campaigns are trending downwards. DoS attacks are increasingly showing up in the cybercriminal toolbox, as they made up 40 percent of security incidents reported. It’s not just the number of attacks that are increasing, but the severity of the attack. Bits per second, tells the size of the attacks, and packets per second tells the throughway of the attack. This is consistent with the various DoS botnets that have popped up recently, such as Kaiji and Mirai variants.
The DBIR confirms that most successful breaches were opportunistic attacks, said Tim Mackey, principal security strategist at Synopsys CyRC. “This means that we could see a material reduction in breaches if basic principles such as securing S3 buckets, applying password security to databases, having a patch management strategy and applying reasonable malware protections were in place,” Mackey said.
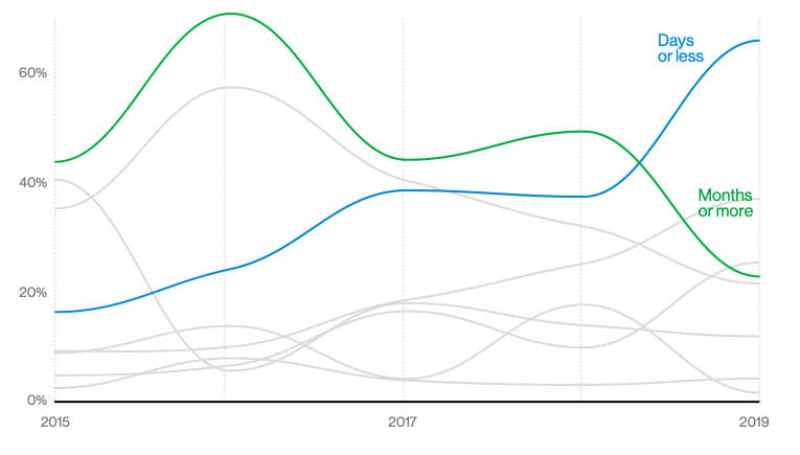
While a quarter of the organizations in the DBIR took months or more to detect the incident, the number of organizations that took just days are increasing. (Source: Verizon Data Breach Investigations Report 2020, Figure 44)
