The end is finally near for antiquated versions of TLS. All the major web browsers—Firefox, Chrome, Safari, and Edge—will display warnings when users visit websites that only support Transport Layer Security (TLS) versions 1.0 or 1.1.
Starting with Firefox 74 on March 10, Firefox users will start seeing a “Secure Connection Failed” message and the error code SSL_ERROR_UNSUPPORTED_VERSION whenever they try to reach a website that uses only TLS 1.0 or TLS 1.1, Mozilla said in its reminder. For the time being, users will be able to ignore the warning and still reach the site using the override button at the bottom of the message, but that button will eventually go away. The timing is still unknown, as Mozilla engineers will look at how often the override button is used before deciding when to remove it entirely.
“We’re committed to completely eradicating weak versions of TLS because at Mozilla we believe that user security should not be treated as optional,” said Thyla van der Merwe, cryptography engineering manager at Mozilla.
Chrome started displaying the message “Your connection to this site is not fully secure. This site uses an outdated security configuration,” last month. The browser will begin blocking the sites with Chrome 81 on March 17. While Safari currently doesn’t show any warnings, Apple said, “Complete support will be removed from Safari in updates to Apple iOS and macOS beginning in March 2020.” Edge also does not show any warnings at the moment, but Microsoft is expected to start blocking with Edge 82 in April. Microsoft will also remove support from Internet Explorer "in the first half of 2020".
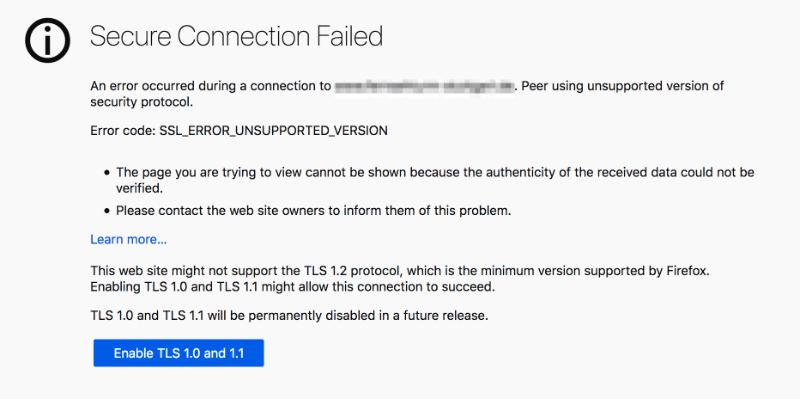
Mozilla will display this screen for websites using TLS 1.0 or 1.1. The override button will go away eventually.
TLS is the encryption protocol used to secure online connections—including secure SMTP, SFTP, and HTTPS. TLS sets up authentication, handles the exchange of session keys, and negotiates which cipher suite is used. In order to do all that, the website (via the web server) has to agree with the user’s web browser on which version of TLS to use. If the website can use only TLS 1.0 or 1.1, and the browser doesn’t support those two versions, then the secure connection cannot be established. TLS 1.2 is going to be the default going forward, although it would be a good idea for websites to go ahead and get to 1.3, as it is far more secure and optimized for modern web traffic. For those few websites that still rely on TLS 1.0 or 1.1, the choice is straightforward: enable TLS 1.2, or better yet, 1.3, or lose traffic because users will not be able to reach the site.
TLS 1.0, which dates back to 1999, and 1.1, which came along in 2006, do not support the latest cryptographic algorithms. The Internet Engineering Task Force (IETF) is formally deprecating TLS 1.0 and 1.1 and the National Institute of Standards and Technology (NIST) warns that it isn’t practical to patch the vulnerabilities in the older versions. Those versions are vulnerable to attacks such as BEAST, CRIME and POODLE. TLS 1.2 and 1.3 support the latest cipher suites and algorithms, removed insecure SHA-1 and MD5 hash functions, and are resilient against attacks such as LogJam and FREAK. PCI Data Security Standards (PCI DSS) requires at least TLS 1.2 to be PCI-DSS-compliant.
We’re committed to completely eradicating weak versions of TLS because at Mozilla we believe that user security should not be treated as optional
The plan to start blocking the older versions of TLS was jointly announced by the browsers back in October 2018. The impact of this change will not be that widespread because the majority of the sites appear to be able to negotiate a TLS 1.2 or TLS 1.3 connection. SSL Pulse analyzed Alexa’s most popular websites and found that of nearly 140,000 websites, the majority—71.7 percent—support TLS 1.2, and 25 percent support TLS 1.3. Just 3.2 percent failed to support protocols higher than TLS 1.0, and less than 0.1 percent were stuck at TLS 1.1. However, legacy applications still using older versions of TLS—such as those built with .NET Framework 4.5 and below—may have trouble connecting after March.
Google estimates that less than 1 percent of page loads still rely on TLS 1.0 and 1.1. Website owners uncertain about their configuration can use Mozilla Observatory to verify whether the site supports at least TLS 1.2.
“You don't necessarily have to remove support for these Legacy TLS versions, you simply have to make sure that you support at least TLSv1.2 for clients like Chrome/Firefox/Safari to be able to connect,” researcher Scott Helme wrote recently.
image credit: Photo by Hal Gatewood (@halgatewood) on Unsplash
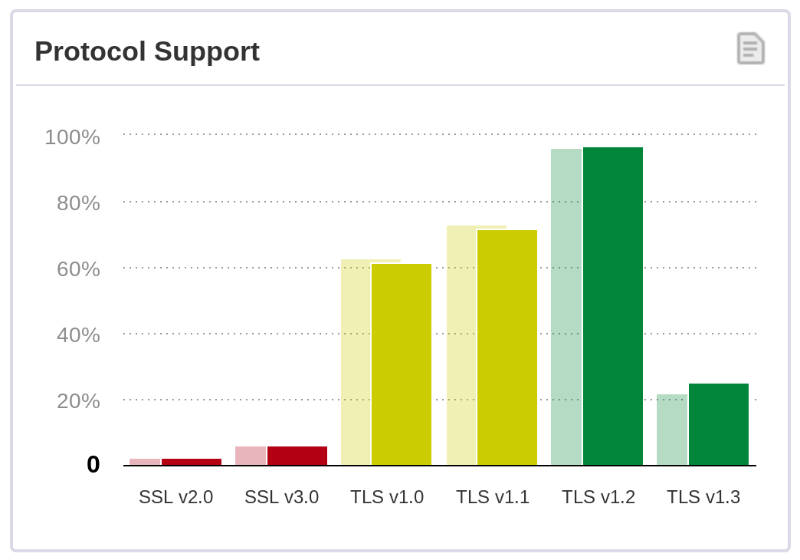
Majority of the websites support TLS 1.2 and TLS 1.3, although there are still some sites that cannot negotiate higher than TLS 1.1 or 1.0. Source: SSL Pulse