Vulnerabilities need to be patched, but security doesn’t stop with updates since the attackers may already be inside the network. Additional steps may be necessary, such as resetting passwords and looking for evidence of other types of infection or compromise.
That is the gist of the latest alert from the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency to organizations using Pulse Secure VPN. Organizations using Pulse Secure’s enterprise-grade virtual private network gateways should also change passwords for Active Directory accounts after making sure the latest updates have been applied, CISA said.
"Threat actors who successfully exploited CVE-2019-11510 and stole a victim organization's credentials will still be able to access — and move laterally through — that organization's network after the organization has patched this vulnerability if the organization did not change those stolen credentials," CISA said.
Last year, Pulse Secure fixed a critical remote code execution vulnerability in its SSL VPN gateways which could be exploited to allow remote unauthenticated attackers to run malicious code on the server and extract plain-text credentials for all active users on the network. It appears the attackers may have acted faster than some enterprise security teams, as they may have compromised the VPN gateways after the patch was released, but before the enterprise security team deployed the update, CISA suggested.
Just one vulnerable machine can cause a lot of damage to an organization's network.
The agency said it was aware of "incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance," which would suggest that the attackers remained in the network post-update. They are now moving laterally through the networks using compromised Active Directory accounts.
Exploiting the vulnerability is simple—the entry on Rapid7’s AttackerKB describes the impact of the flaw as, “Causes massive damage. If not patched, likely wrecked.”
Organizations should make sure their VPN gateways have the latest updates and change passwords for all Active Directory accounts, including administrators and services accounts, the agency said in its alert. CISA also released a check-your-pulse tool to help network administrators to review Pulse Secure VPN server logs for evidence that any of the systems on the network had been exploited via this vulnerability. The tool scans for IP addresses and user-agents known to be associated with other attack groups that have exploited the VPN servers. Other suggestions include removing any unapproved remote access programs and inspecting scheduled tasks for scripts or executables that may allow an attacker to connect to an environment.
“CISA strongly urges organizations that have not yet done so to upgrade their Pulse Secure VPN to the corresponding patches for CVE-2019-11510,” according to CISA’s alert. “If—after applying the detection measures in this alert—organizations detect evidence of CVE-2019-11510 exploitation, CISA recommends changing passwords for all Active Directory accounts, including administrators and services accounts.”
This alert is not the first time CISA has had to remind organizations to apply the patch, which was released in April 2019. An advisory in October, two months after the proof-of-concept code became publicly available, warned of ongoing attacks, and the January alert said the unpatched servers “continue to be an attractive target for malicious actors.”
Bad Packets reported “mass scanning activity” looking for vulnerable Pulse Secure VPNs last week.
Bad Packets has been scanning for vulnerable Pulse Secure VPN endpoints each week since August and continues to find unpatched gateways. In August, four months after the security update was released, Bad Packets 14,500 vulnerable Pulse Secure VPNs. As of end of March, almost a year after the updates were released, 2,099 servers remain vulnerable.
While Pulse Secure told SecurityWeek last August that majority of its customers had updated the servers and were no longer vulnerable, it is clear that non-trivial number of VPNs needed to be updated over the past few months, and there are plenty left that still needs attention.
Just one vulnerable machine can cause a lot of damage to an organization's network. Cybercriminals exploited the VPN vulnerability to infect the networks of foreign currency exchange and travel insurance firm Travelex with the Sodinokibi (REvil) ransomware. The pre-authentication arbitrary file read vulnerability has been broadly exploited by nation-state attack groups as well as ransomware gangs.
“CISA encourages network administrators to remain aware of the ramifications of exploitation of CVE-2019-11510 and to apply the detection measures and mitigations provided in this report to secure networks against these attacks,” the advisory said.
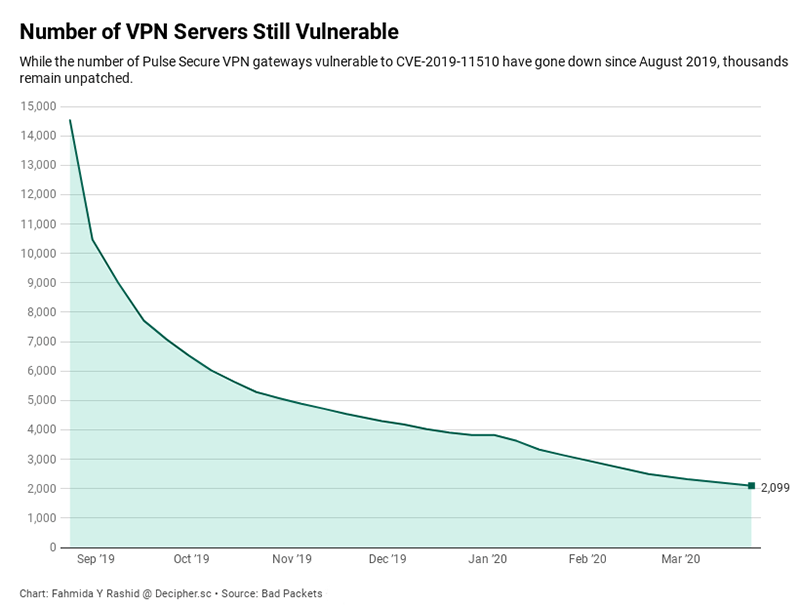
Bad Packets started scanning for vulnerable Pulse Secure VPN servers in August 2019. While the number of VPN gateways vulnerable to CVE-2019-11510 have dropped from 14,500 since August, there are still almost 3,000 servers that can be exploited. (Source: Bad Packets)
