Now that the initial flurry of excitement around the data breach statistics has died down, enterprise defenders should revisit Verizon's 2019 Data Breach Investigations Report and take a deeper look at the charts and data analysis to understand the threats they face. The 2019 DBIR gives enterprise defenders the details about how attackers actually behave in real-world attacks.
Verizon’s DBIR is a combination of information about actual breaches and incidents the Verizon Enterprise Solutions team investigated in 2018, as well as information voluntarily provided by 73 partners. The twelfth edition of the report analyzed 41,686 security incidents, including 2,013 confirmed breaches, from 86 countries. Verizon defines a breach as an incident that results in confirmed disclosure or exposure of data. The distinction is important, since a distributed denial of service attack would be an incident but not a breach because data was not (usually) exposed. The report helps enterprises better understand what attackers are doing and are most likely to attack next.
“This [report] is going to be useful for defenders, CISOs, security leaders on the defense side, to figure out if they are spending time, money, and resources, in the right direction,” said longtime security practitioner Adrian Sanabria. “They can pore over the report and say, ‘Oh, no, we poured in way too much money on this thing,’ and adjust accordingly.”
What We Knew
The DBIR validated a lot of the things security professionals already knew—such as the fact that the majority of attacks are carried out by outsiders. Of the data breaches Verizon investigated in 2018, 69 percent were external attacks. A little more than half of the breaches, 52 percent, involved some kind of compromise (or hacking, as the report calls it), followed by 33 percent which involved social engineering. About 28 percent of the breaches used malware.
Passwords continue to be the weak spot for enterprises, as 32 percent of the breaches involved phishing and 29 percent involved the use of stolen credentials. Web application attacks continue to be the most common attack vector for data breaches, but this category includes both compromising the application through some kind of vulnerability and attackers simply logging in with stolen credentials. The report said over half of breaches associated with web application attacks involved attackers using stolen credentials.
Even though there have been a lot of indictments and research discoveries uncovering espionage operations, the overwhelming majority of attacks—71 percent of data breaches—are still because the perpetrators are trying to make money. One of the upsides of financial institutions in the United States switching to EMV payment cards (chip-and-sign in the United States, chip-and-PIN elsewhere) is that card-present fraud involving compromised point-of-sale terminals and card skimming operations fell by 57 percent. But, as expected, attackers have shifted to card-not-present fraud by targeting web applications to capture payment card details. In some cases, card-not-present fraud is now more extensive than card-present fraud, the report found.
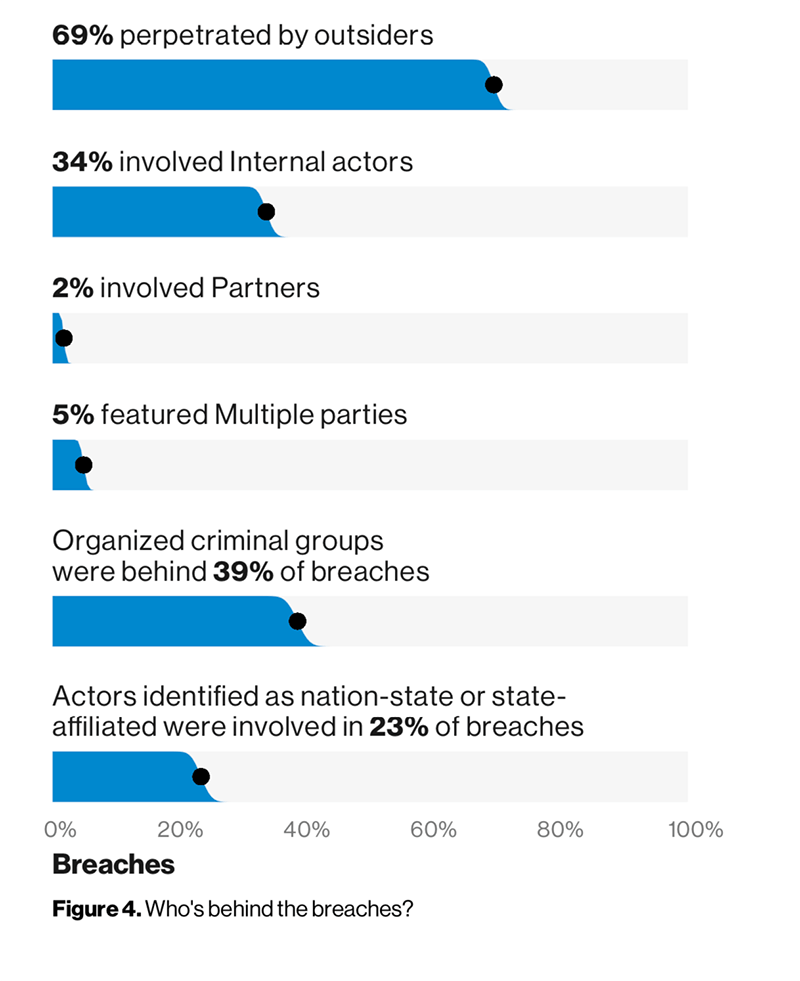
The majority of attacks come from outside actors. Figure 4: 2019 Data Breach Investigations Report
Need to Understand Paths
The DBIR introduced “attack paths” in the report, which attempts to document the steps the attackers used in an incident or breach. The attack path shows all the different ways attackers took getting from the initial compromise to finding information to achieving their goal at the final point. Attackers also don’t plan out a long campaign with many steps if they don’t have to. Attack paths are much more likely to be short than long, the report found. “[Defenders] fail to stop short paths substantially more often than long paths,” the report found. “Short attacks work.”
“Think: Cyber Kill Chain, but from a Threat Intel perspective,” wrote Lance Spitzner, the director of SANS Security Awareness at the SANS Institute.
While hacking—such as exploiting software vulnerabilities—was the most common first action in an incident, “it could be almost anything,” the report said, including social engineering or human error. However, malware was frequently used in the middle and at the end of the line—attackers are still relying heavily on malware to carry out their attacks.
“We got really good at stopping malware from getting in, so they use other paths to get in, turn off antivirus, and then use malware anyway,” Sanabria said.
This section of the report used golf as the metaphor. “Malware is usually not the driver you use to get off the tee; remember that most is delivered via social or hacking actions...[Malware] may not be the opening shot, but it is the trusty 7-iron (or 3 wood, pick your analogy according to your skills), that is your go-to club for those middle action shots...While social attacks are significant for starting and continuing attacks...they’re rarely the three-foot putt followed by the tip of the visor to the sunburned gallery.”
The report’s authors described how the course creator builds sand traps and water hazards along the course to make the game challenging for the players, and used this metaphor as a way to show that enterprises rely on defenses and mitigations to deter, detect, and defend their networks from attacks. The problem with this metaphor, is that it overemphasizes how many enterprises are putting in these kind of defensive layers, or even the amount or roadblocks the defenders are putting in. The report makes it sound like “most enterprises have sand traps or water hazards, when they do not,” Sanabria said.
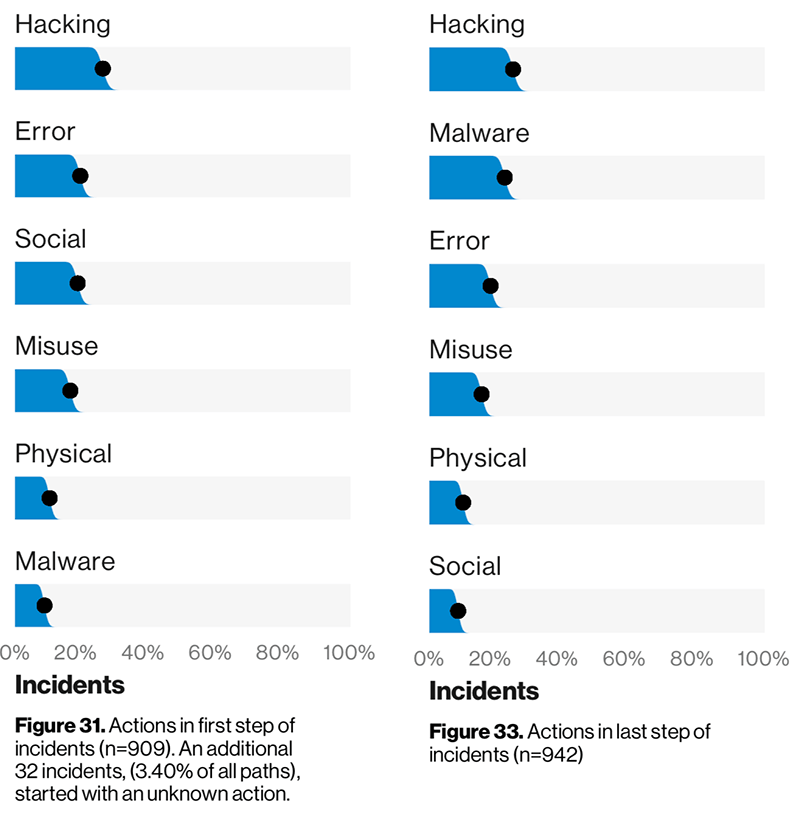
Attackers will use any method to try to get a foothold in the target's environment and will frequently use malware as the last step. Source: Figures 31 and 33 from the 2019 Data Breach Investigations Report.
Even so, the section on attack paths is the “most valuable part of this year’s report,” Sanabria said. “It’s the first time I’ve seen a report break out the steps this way.”
Information security talks a lot about the kill chain, but is rarely mapped against the actual breach. Most data breach conversations talk about the initial point of compromise, but that is only one single point in time and leaves out details on how the rest of the attack unfolded. Take Equifax for example—the company was initially skewered over not patching the Struts vulnerability in the affected server, but the detailed post-mortem report afterwards revealed how complex the situation was, and highlighted the challenges organizations have with legacy infrastructure.
When defenders have just a “snapshot of an attacker’s process,” they have to guess what the attackers did before and after that point in time. Those guesses have an impact on how the defenses are put together, the Center for Internet Security wrote in the report.
“Defending against malware takes a different approach if the malware is dropped via social engineering, a drive-by download, or brought in by an insider via a USB device,” CIS said.
Post-mortems are valuable for defenders to learn from other people’s mistakes, but are in-depth ones are generally difficult to find. Seeing some of that analysis in the report will help defenders understand how to prioritize some of their defenses.
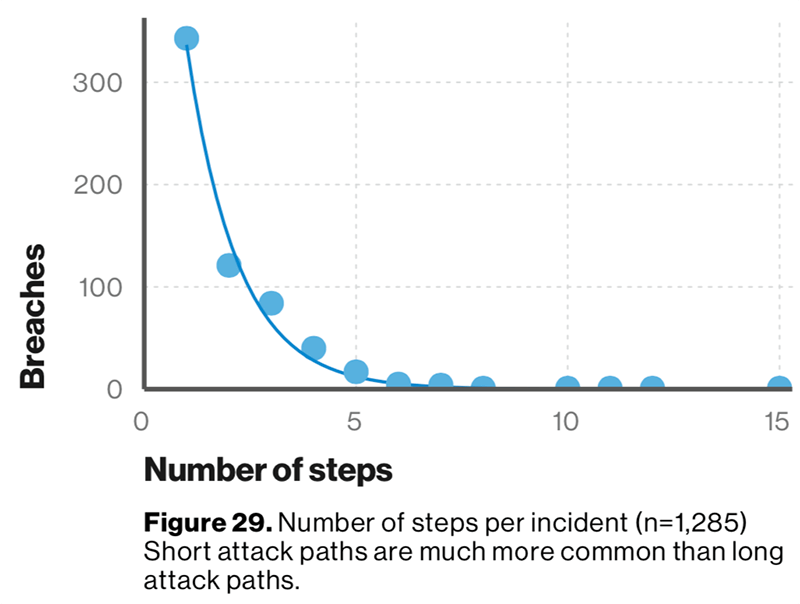
Attack paths are much more likely to be short than long, and defenders have a harder time stopping short attacks. Source: Figure 29 of 2019 Data Breach Investigations Report.
What We Need to Know
The data confirmed that attackers are not interested in doing more work than they have to do to reach their goal. Attackers are increasingly targeting corporate executives, and business-to-email compromise attacks are on the rise, the report found. The DBIR grouped CEO fraud and other attacks against corporate executives as Financially Motivated Social Engineering Attacks (FMSE). The end goal of these phishing attacks aren’t to get the victims to click on links or open malicious attachments, but rather to transfer money to the attackers.
“For the criminal it’s all about bang for your buck,” Sanabria said. “Sending an email and saying, ‘Please direct your money here,’ is pretty easy.”
Executives are six times more likely to be a target of a social engineering campaign than they were just a year ago, and C-level executives are 12 times more likely to be targeted. Committing tax fraud with stolen W2 forms have practically disappeared. Senior executives are trying to review and act on emails quickly, so suspicious emails are more likely to slip through.
DBIR also provides hard data on which assets the attackers are going after, giving defenders insight into what to protect, Sanabria said. While workstations have long been targeted, web applications and mail servers are increasingly being targeted as well. Attacks trying to steal credentials most often involved cloud-based mail servers and there was an uptick in attacks trying to compromise victim email accounts, the report found. Breaches with compromised payment cards were increasingly the result of compromised web servers.
How attackers use malware has completely changed in the last five years, Sanabria said. Flash-based malware used to be the most prevalent and was a surefire way to infect people, but as browsers got more secure, Flash-based malware is no longer that common. Email remains the most common way to distribute malware, but as the attach paths section showed, enterprises have to also think about cases where the attackers gain a foothold through other means and then directly install the malware.
Ransomware was the second most prevalent malware affecting all industries, but the researchers noted that ransomware isn’t treated the same across industries. Healthcare organizations are mandated by HIPAA regulations to report ransomware infections as data breaches because data is involved—but that isn’t the case for other industries. Ransomware as a whole accounted for 24 percent of data breaches in Verizon’s data set, but when looking only at healthcare data, ransomware jumps to 70 percent of data breaches, according to the DBIR. That suggests that the number of infections are being undercounted, and that the threat ransomware poses is underestimated.
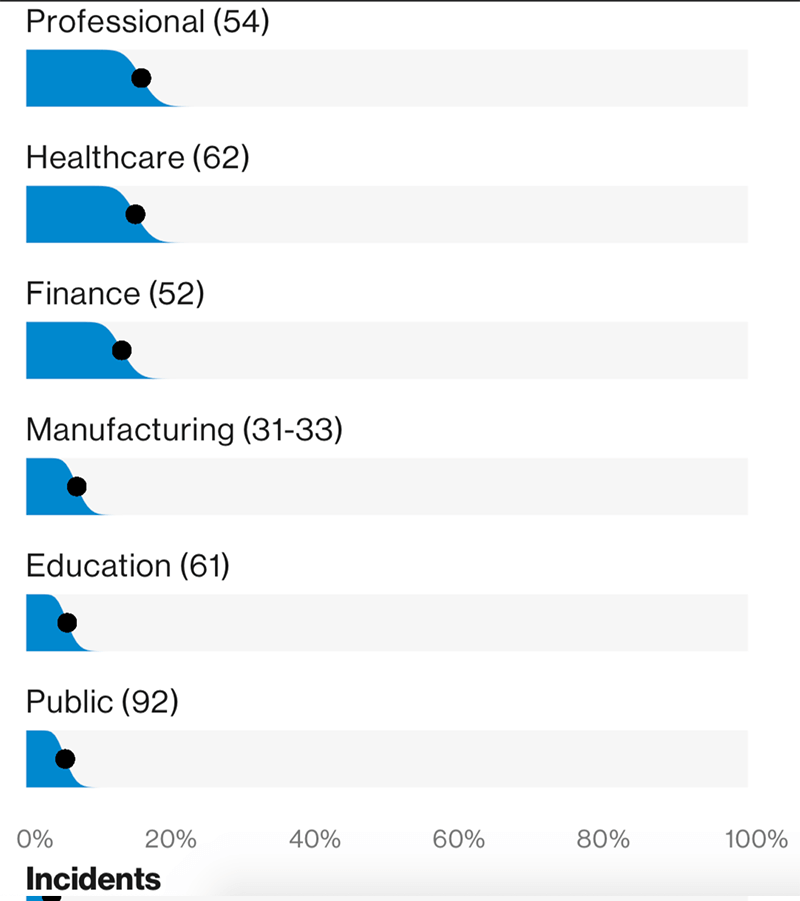
FMSE incidents disproportionately affect Professional Services, Healthcare and Finance. Source: Adapted Figure 40 from the 2019 Data Breach Investigations Report.
What We Didn't Know
Because DBIR is based on actual investigations, its findings help debunk some of the myths that persist in information security, Sanabria said. The report makes it clear that about a third of the breaches—34 percent—involved internal employees, but most of these breaches were not the result of someone acting maliciously. Misconfigured cloud-based file storage accounted for 21 percent of data breaches caused by errors.
“[While] the rogue admin planting logic bombs and other mayhem makes for a good story, the presence of insiders is most often in the form of errors,” the report said. “Please, close those buckets!”
Errors include misconfiguring servers to allow unauthorized access, publishing data to a server where it should not be visible to everyone, and emailing sensitive files to the wrong person.
“Just teaching people to double check the TO: address in their email draft before hitting the “send” button could reduce almost 10% of all breaches globally,” Spitzner wrote.
Insider attacks were more prevalent in health care than external attacks. In medical data breaches where an internal employee was involved, 14 percent were more likely to be a medical professional such as a doctor or nurse.
What May Be Hype
While there has been a surge in the number of cryptomining attacks, cryptomining malware did not break the ten most popular forms of malware. There were 39 cases in Verizon’s data set, which is “more than zero, but still far fewer than the almost 500 ransomware cases this year,” the report said. “The number in this year’s data set do not support the hype.”
One reason why cryptomining may not be showing up that much in Verizon’s data sets is that it may not be getting reported as often. Cryptomining is using resources so it is more annoying, rather than malicious in the same sense as data theft, Sanabria said. Many organizations may not even notice unless the malware was on a cloud server and it generated an expensive bill.
The idea that most attacks in the manufacturing sector are for espionage is widely accepted, except the data doesn’t bear that out. “For the second year in a row, financially motivated attacks outnumber cyber-espionage as the main reason for breaches in Manufacturing, and this year by a more significant percentage (40% difference),” the report said. However, the team stopped short of saying that espionage is no longer a problem in manufacturing (or education, another popular vertical) and noted that it could just be a bias in the data that was collected.
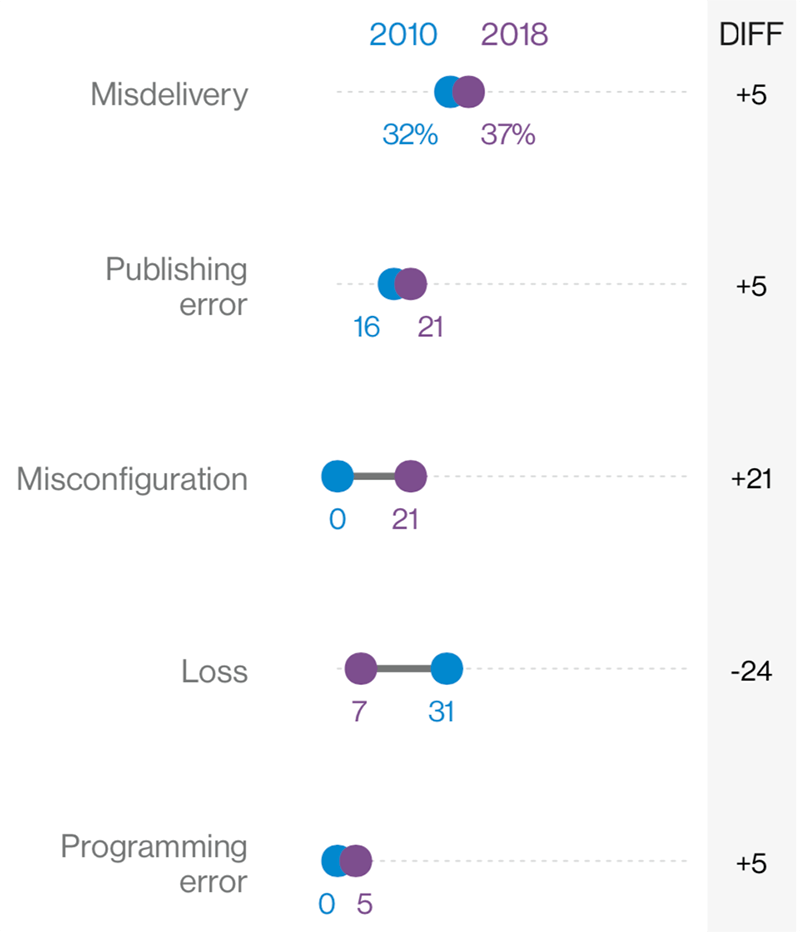
Errors continue to be a big problem, including sending data to the incorrect recipients, exposing data on a public website, and misconfiguring an asset to allow unwanted guests. Source: Figure 24 from the 2019 Data Breach Investigations Report.
We used to say that a fraction of companies needed to worry about nation-state attackers. It looks like we can’t say that anymore.
The report also paints an interesting picture of the state of defense today. The assumption in the past was that only a small number of companies who had to worry about nation-state attacks needed nation-state-caliber defenses. The report showed that nation-state attacks are on the rise across all sectors, because the attackers are going to go after any target that has information that may be valuable for them. Even small businesses are now targets if they have information that someone wants. For example, nation-state attackers may go after a restaurant's surveillance camera if some high-level political figures regularly eat at that restaurant.
“We used to say that a fraction of companies needed to worry about nation-state attackers. It looks like we can’t say that anymore,” Sanabria said. “Maybe everyone has to worry about state stuff—but that will be a hard bar for the SMB to clear.”
“The purpose of this study is not to rub salt in the wounds of information security, but to contribute to the ‘light’ that raises awareness and provides the ability to learn from the past,” Verizon’s research team wrote in the report. “Use it as another arrow in your quiver to win hearts, minds, and security budget.