Some vendors are shipping Android devices with the debug port enabled, which lets anyone remotely connect to the device and and execute commands, security researchers warned.
The debug mode is called Android Debug Bridge and developers use it to install apps and launch a Unix shell to execute commands when troubleshooting Android devices, security researcher Kevin Beaumont wrote on Medium. Normally ADB wouldn’t raise security concerns because it is disabled by default in Android. To use ADB, the user would first have to physically connect the device over USB and then manually enable it in Android settings.
Unfortunately, some vendors are shipping Android devices with ADB already enabled. ADB listens on TCP port 5555 for troubleshooting instructions, so anyone scanning the Internet for that open port will find the device. Since ADB doesn’t require authentication, that means anyone can communicate with the device. No USB connection required.
“This is highly problematic as it allows anybody—without any password—to remotely access these devices as 'root'—the administrator mode—and then silently install software and execute malicious functions," Beaumont wrote.
Users should disable ADB—listed as “USB Debugging” on some Android versions—on their devices via Android settings. Mobile operators can also block scans of port 5555 to prevent attackers from using Internet-wide scans to find exposed misconfigured devices.
IT administrators can also use Metasploit’s adb_server_exec module to remotely probe the devices, and if ADB is listening on port 5555, the probe will return device information, such as product name and model number.
Rapid7’s Project Heisenberg and GreyNoise Intelligence’s scan data show “a massive increase in scanning for TCP port 5555,” on Feb. 1, Beaumont said. He observed nearly ten thousand unique IP addresses scanning within a 24-hour window, and over a hundred thousand IP addresses scanning within a 30-day period. Other services also use port 5555, so scanning on this port doesn’t automatically mean it is related to ADB.
Thousands of Android devices around the world are misconfigured, including smart TV sets, DVRs, and mobile devices. Beaumont even found US tankers in his analysis. The majority of exposed devices are in Asia, primarily China and South Korea. IoT search engine Shodan added a scan to look for devices exposed on the Internet with ADB enabled, and has already found over 15,600 such devices.
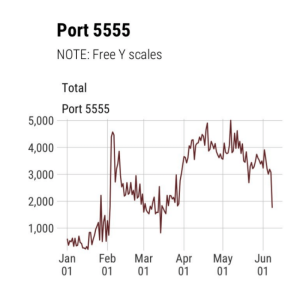
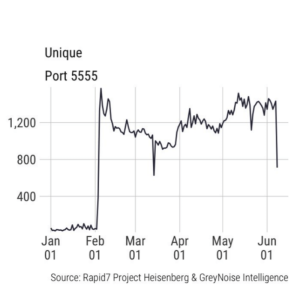
Threat intelligence data shows "massive increase" in scans for port 5555 on Feb. 1, 2018. Source: Rapid7’s Project Heisenberg, GreyNoise Intelligence
The problem is not with ADB, but rather in the fact that it is enabled by default. “ADB is not designed to be deployed in this manner,” Beaumont said.
Vendors should not be shipping products with ADB enabled over the network—and those who have should release updates disabling ADB and work with customers to ensure the updates are installed. Some of the problem also comes from people insecurely rooting their devices, Beaumont said.
“It’s very clear through digging through data and feeds that a huge number of misconfigured devices exist, hence all the scanning for port 5555,” Beaumont said.
Researchers from Chinese security company Qihoo 360 warned back in February that crypto-mining worm ADB.Miner was using ADB to spread from device to device. According to Qihoo 360 Netlab, the malware, a modified version of Mirai bolted onto a cryptominer, is still actively scanning for open ports to find devices to infect.
This isn’t simply a cryptocurrency malware issue. “If somebody wanted to, they could run something other than cryptocurrency mining,” Beaumont warned, noting that many of these misconfigured devices can be found in corporate networks or accessing corporate data.
Beaumont referred to the misconfiguration as “RootBridge, a situation every [sic] anybody can misuse devices.”
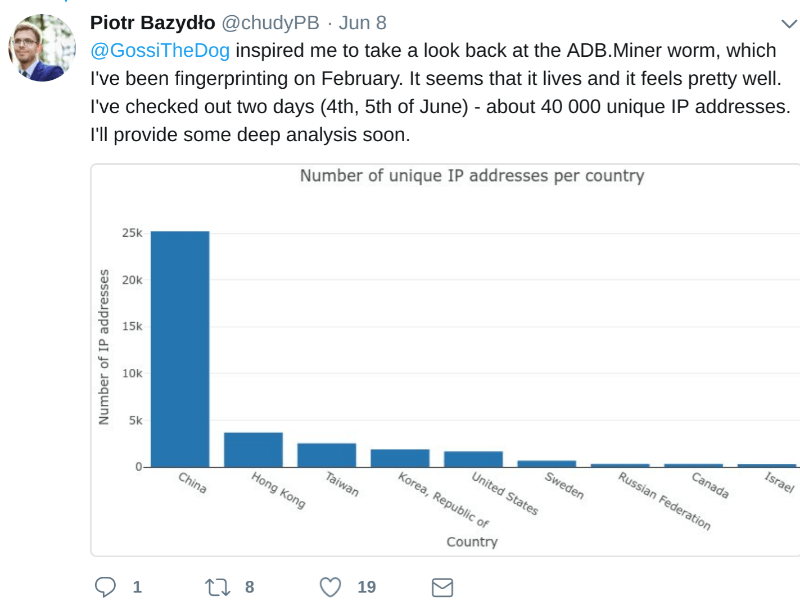
The ADB.Miner cryptocurrency mining malware is active, especially in China. Data from Piotr Bazydlo, head of R&D Network Security Methods Team at NASK a research and academic network in Poland. (Twitter: @chudyPB)

