From an attacker’s perspective, the wider the net cast, the more number of potential victims caught. So it’s no surprise that attack campaigns continue to rely heavily on exploits targeting Microsoft applications.
Eight of the top 10 most exploited vulnerabilities in 2018 were vulnerabilities in Microsoft software, according to Recorded Future’s analysis of exploit kits, phishing attacks, and malware campaigns deployed during 2018. The data was culled from code repositories, underground criminal forum postings and sites, and other metadata. An Adobe Flash flaw and an Android bug rounded out the rest of the list.
A security update is available for every single one of the vulnerabilities on this list. Of the eight Microsoft vulnerabilities being exploited, two were fixed in 2018, four in 2017, one in 2016, and one in 2012. Attackers are taking advantage of the fact that there is a lag between when the updates are released and when the security teams finishing testing and deploying them.
Don't beat the patch-patch-patch drum. Testing patches is a time-consuming process, especially since the security team has to take into account potential software and hardware conflicts. In many cases, business reasons may prevent the security team from scheduling a maintenance window during a critical time period to roll out the updates. The security team may not have control over some of the machines.
Update Which, First?
Security teams have to prioritize which vulnerabilities need attention, and Recorded Future’s goal is to help by highlighting where attackers are focusing the bulk of their efforts. Previous research by Kenna Security has shown that vulnerabilities that already have attack code available are more likely to be used in attacks and should take priority when patching. Considering that seven of the top 10 flaws on the list were already exploited in the wild at the time the patches were released, it makes sense that they were so prevalent in Recorded Future’s analysis.
“It is imperative that security professionals have insight into those vulnerabilities that impact a company’s technology stack and are included in exploit kits, used to distribute a remote access trojan (RAT), or are currently being used in phishing attacks,” Recorded Future said.
Don't beat the patch-patch-patch drum.
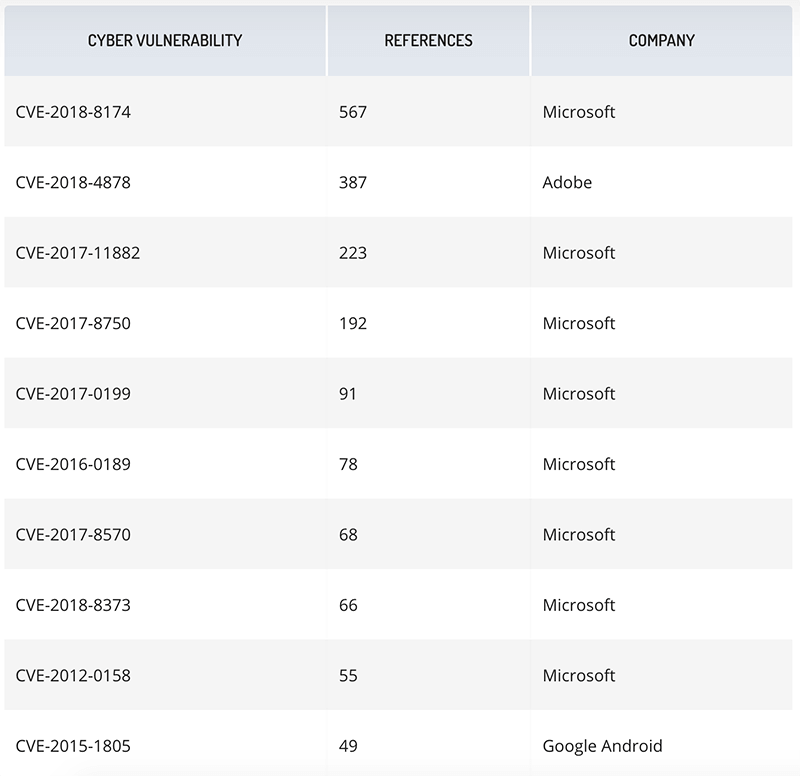
List of 10 most exploited vulnerabilities in 2018 and the company associated with the software. Source: Recorded Future
The top exploited vulnerability was a remote code execution flaw (CVE-2018-8174) residing in Windows VBScript (Double Kill) which can be exploited through older versions of Internet Explorer. Double Kill has been included in four exploit kits—RIG, Fallout, KaiXin, and Magnitude—and have been used to drop banking Trojans and ransomware on victims.
The third most commonly exploited vulnerability was the flaw in Microsoft Office which enables arbitrary code execution when a booby-trapped document is opened (CVE-2017-11882). It has been used in various campaigns and exploit kits, including keyloggers AgentTesla and Hawkeye, password-stealing malware Loki, the Andromeda botnet, the BondUpdater Trojan, PowRunner backdoor, QuasarRAT, REMCOS RAT, ThreadKit, and LCG Kit.
Exploit Kits, Old Bugs
Exploit kits in previous years took advantage of vulnerabilities in Adobe products, but that attack surface has been dwindling. Many web browsers block Flash applications by default and open PDF files in their own sandboxed containers. Only one Adobe Flash vulnerability (CVE-2018-4878) made the top 10 in 2018, likely the result of more web browsers adopting the auto-update mechanism and the fact that many applications are moving off Flash Player before Adobe shuts it down for good in 2020.
While attackers continue to rely on exploit kits, there is a marked decline in exploit kit development. Just five new exploit kits came on the scene in 2018, down from 10 new ones in 2017, and 62 in 2016, Recorded Future found. Only two of the new kits—Fallout and LCG Kit—exploited the vulnerabilities listed in the top 10 list. Remote Access Trojans also followed the same pattern, as 35 new RATs were released in 2018, compared to 47 in 2017, and only one new RAT, Sasfader, was associated with a top 10 exploited flaw (CVE-2017-8750, Microsoft Office).
“The development of new exploit kits has continued to drop amid the shift to more targeted attacks and less availability of zero-day vulnerabilities,” Recorded Future said.
For attackers, it is far more effective to rely on phishing campaigns to steal credentials than to develop (or buy) remote code execution exploits to deliver malware.
Attackers are fully aware that there is a delay between when patches are released and when they are applied, and continue to include older vulnerabilities in their campaigns. While the average lifespan of a vulnerability is seven years, Recorded Future’s research shows that attackers adopt newer flaws and rely less on older ones. The top exploited vulnerability in 2017 also impacted Microsoft Office (CVE-2017-0199), but dropped down to fifth on the 2018 list, and only because it is still included in the ThreatKit exploit kit.
The top vulnerability in 2016 was a zero-day flaw affecting multiple versions of Internet Explorer (CVE-2016-0189) and was the second most exploited in 2017. It was the sixth most exploited in 2018, thanks to its inclusion in five different exploit kits (Grandsoft, KaiXin, Magnitude, RIG, and Underminer). The fact that the Microsoft Internet Explorer Scripting Engine Remote Memory Corruption vulnerability remains prevalent three years later suggests that despite Microsoft’s efforts, older systems running vulnerable versions of the web browser remain a problem. Two other Microsoft issues in the top 10 also affect Internet Explorer.
The other reasons for the 2016 zero-day’s versatility has to do with the fact that “there are no mitigating factors available to prevent CVE-2016-0189—the only workarounds are restricting access to two common dynamic-linked library files: VBScript.dll and JScript.dll,” Recorded Future said.
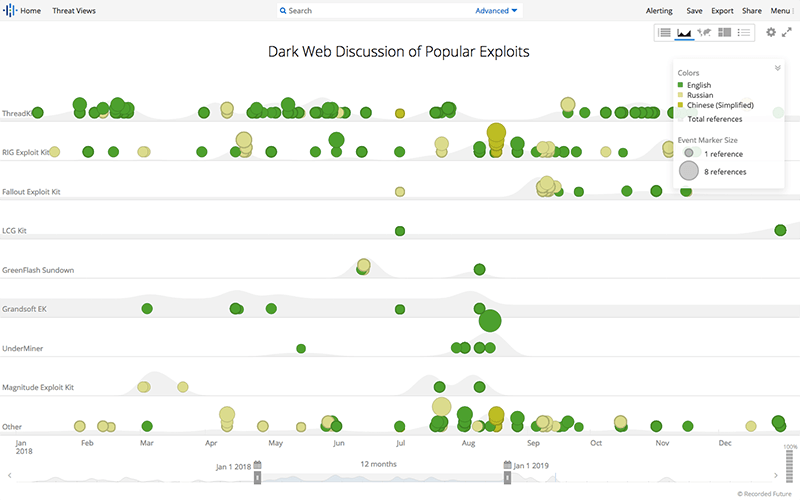
ThreadKit stood out because it was consistently the most referenced exploit kit associated with 2018's top vulnerabilities on criminal underground forums and discussion groups. Source: Recorded Future
Priority Lists
When trying to decide which updates to apply first, Recorded Future's research suggests that it makes sense to deploy the newer ones and then work back to the older ones. It's an ongoing list, since new updates are being released on a regular basis, but if attackers are evolving attack methods to include newer exploits, the defenses need to be there.
Older exploits still can cause a lot of damage, so ignoring the patches just because they are over a year or two old would be detrimental.
While a number of exploits developed by nation-state entities were leaked online in 2018, Recorded Future did "not see evidence that these exploits were highly used by the criminal underground." The ETERNALBLUE exploit was often mentioned, but was not used by the criminal underground or offered for sale as a part of other exploit kits, Recorded Future said. Spectre also got a lot of attention and its name appeared in a number of phishing campaigns, but was not heavily used by cybercriminals. Recorded Future speculated that the more sophisticated exploits are difficult to use, making them less prolific.
Microsoft Office is widely used for a reason, and enterprise defenders need to keep their focus on this suite to make sure the attackers can't use it, either.
"Official vulnerability databases, and even scanning tools, cannot arm organizations with one key metric: the overlap between the vulnerabilities in the systems you use and the ones that are being actively exploited by threat actors," Recorded Future said.
However, the decline of new exploit kits and the recent increase in phishing and credential-stuffing attacks suggest attackers are shifting their tactics. If attackers can steal user credentials, such as for Remote Desktop Protocol (RDP) or VPN, then they don't need to worry about trying to download keyloggers or malware on to victim computers. Exploit kits that specialize in stealing credentials would still pose big problems for enterprises.
"Companies should deliver user training to encourage skepticism of emails requesting additional information or prompting clicks on any links or attachments," Recorded Future recommended.
