More than a week after LockerGoga infected the Norwegian aluminum manufacturer Norsk Hydro, researchers are still trying to figure out the ransomware’s delivery mechanism. As LockerGoga evolves with new features, researchers are left trying to understand what the group behind the ransomware is really after.
Along with Norsk Hydro, LockerGoga is believed to have infected the networks of French engineering consultancy Altran Technologies in February and chemical manufacturing facilities Hexicon and Momentive. The earliest known sample of LockerGoga—used in the attack on Altran—was submitted to VirusTotal on Jan. 24, and there have been a number of updates made since then, wrote Unit 42, the threat research group at Palo Alto Networks. Unit 42 has identified 31 variations of the ransomware to date.
“Like other active software projects, the LockerGoga ransomware is under constant development with new variants being developed and used to attack victims. All these variants share similar characteristics and just like other professional development, each release contains improvements or new capabilities,” Unit 42 said.
On the surface, LockerGoga behaves much like any other ransomware, encrypting files on an infected machine and displaying a message warning the victim that only the attackers have the key to unlock the files. The only way to get the key is to pay a ransom in Bitcoin. However, there are some differences that make LockerGoga different from the garden-variety ransomware.
Point of Origin
For starters, researchers have not yet figured out how LockerGoga infected its targets, and after the initial infection, how it spread through the network. Unlike NotPetya and WannaCry, LockerGoga doesn’t have wormlike capabilities that would let it self-propagate across networks. Potential delivery mechanisms include using stolen remote desktop protocol (RDP) credentials, brute-force attacks to get on the network or the endpoint, phishing, or exploits targeting unpatched software, Unit 42 said. While many ransomware attacks do begin with a phishing message, investigators have not yet publicly identified the attack emails.
“We have observed LockerGoga moving around a network via the server message block (SMB) protocol, which indicates the actors simply manually copy files from computer to computer," Unit 42 said.
The variant that hit Hydro used the manufacturer’s Active Directory services to spread the ransomware to different endpoints, Norway’s Computer Emergency Response Team said.
Destruction vs Ransom
Later variants of LockerGoga appear to focus more on making the system unusable rather than collecting ransoms. Even before the files are encrypted, the ransomware changes the password of all administrator-level accounts and then forcibly logs the user out of the current account. The user can’t back into the system and administrators can’t help reset the passwords.
“The consequence is that in many cases, the victim may not even be able to view the ransom note, let alone attempt to comply with any ransom demands,” researchers from Cisco Talos said in their analysis.
In some of the samples analyzed by Trend Micro, LockerGoga encrypted the Windows Boot Manager, which is needed to start the operating system. With boot manager encrypted, the machine can no longer be used, which means these samples essentially act as a wiper, destroying the machines entirely.
More recent versions use undocumented Windows API callls and manipulate WS2_32.dll, a dynamically linked library in Windows used to handle network connections. It is possible the ransomware would eventually evolve to having command-and-control capabilities.
“These features raise more questions about the actor's intent as ransomware is typically one of the least advanced forms of malware,” Unit 42 wrote. “Are they motivated by profits or something else? Has the motive change over time? Why would developers put such effort into their work only to partially encrypt files? Why do they include an email address and not seek payment through more frequently used cryptocurrencies?”
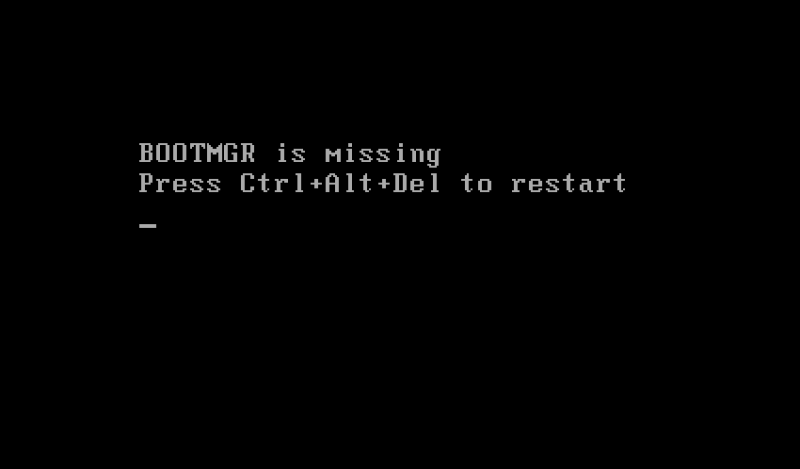
Some LockerGoga samples encrypted the Windows Boot Manager, making it more of a wiper malware than ransomware. (Source: Trend Micro)
Encryption Scheme
Ransomware’s first job is to encrypt the files on the infected machine, but LockerGoga’s developers made some curious decisions. Most ransomware families use the Windows’ CRT library functions, but LockerGoga rellies on the less commonly used Boost library. It doesn’t change the ransomware’s effectiveness—but the relative unfamiliarity makes the job of analyzing it harder, wrote researchers from F-Secure Labs.
The algorithm used by LockerGoga to encrypt the files is computationally intensive, which means it slows down significantly when encrypting large files. To get around this issue, LockerGoga splits the file into chunks of 80,000 bytes and encrypts every other group. Putting in the effort to encrypt the files but deciding to encrypt only parts of the files stumped researchers since that meant partial recovery of large files may be possible.
“Its file encryption routine could be considered less consequential since LockerGoga already locks the user out of the system by changing the accounts’ passwords,” Trend Micro researchers said in their analysis.
Before it kicks off the encryption process, the ransomware uses its blacklist of file types it excludes from the process to identify which files on the machine should be left alone. One of the excluded file types is .lnk—a Windows shortcut file—and the malware terminates without encrypting any files if it encounters a malformed .lnk file, said Alert Logic Threat Research. A .lnk file with errors—because of an invalid network path or missing RPC endpoint—raises an exception the ransomware cannot handle.
“Once the malware encounters an unhandled exception it is terminated by the operating system (as is standard procedure),” Alert Logic said.
Money or What?
Hydro said it had no plans to pay the ransom, and instead would take the time to rebuild the systems and restore data from backups. The process is slow and expensive—Hydro has already spent 350 million kr (Norwegian krone), or approximately $40 million, over more than a week and not all the systems are back online. The costs include revenue losses and IT costs of rebuilding the systems and recovering the data.
The final amount is expected to be higher, since the company’s Extruded Solutions division—which produces extruded and rolled aluminum products—is still running at 70 percent to 80 percent capacity. This unit was hard hit by the infection, and incurred the bulk of financial loss.
“Our global IT organizations, operators and support functions have done a tremendous job during this period. And through their impressive determination, ingenuity and experience, they found new and alternative ways to keep our wheels turning despite the impact on our IT capabilities,” said CFO Eivind Kallevik.
While there is an insurance policy, it isn’t known at this time whether the policy would cover lost revenue as well as the remediation cost, nor is it clear whether the attack fell under the policy’s scope.
As a point of comparison, NotPetya cost Danish shipping company A.P. Møller - Maersk between $200 million to $300 million, and United Kingdom-based pharmaceutical and household goods manufacturer Reckitt Benckiser approximately $129 million.
“We do not know if any of the victims have paid the ransom and were able to successfully retrieve their data. We do know that this ransomware has caused significant harm,” Unit 42 wrote. “The damage could increase significantly if the attackers continue to refine this ransomware.”
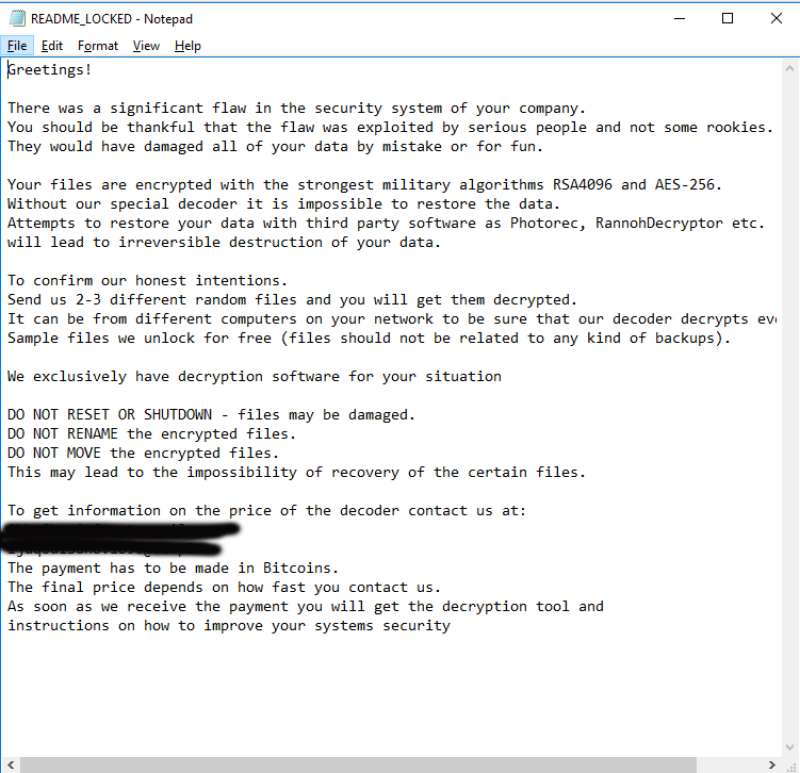
LockerGoga leaves behind the ransom message on the desktop after encrypting the files. (Source: Cisco Talols)
