Large websites like Facebook operate multiple web servers around the world to support all the users—too few servers and the site will not be able to handle the volume of users, and if they are not geographically distributed, some users will have lag and degraded user experience.
Companies operating large website setups or relying on content delivery networks have a specific challenge if they want to support HTTPS for those sites. Transport Layer Security (TLS) relies on digital certificates issued by a certificate authority and private/public keys to make HTTPS possible. Large websites have to put a copy of the site’s private key on each web server. Anyone hosting an HTTPS site on a CDN would have to upload the site’s private key, and the CDN would distribute the key to all its servers. That is a lot of copies of the private key floating around, and an attacker needs to breach any one of those servers to steal the private key. With the key, the attacker can impersonate any web server used by the company and intercept user traffic to that website until the certificate expires.
To tackle this TLS security challenge, Facebook, Mozilla, and Cloudflare proposed TLS Delegated Credentials, a new security protocol currently being considered for a standard at the Internet Engineering Task Force (IETF). Designed to work as an extension to TLS 1.3, TLS Delegated Credentials is intended for large website operations such as Facebook, or sites using CDNs, such as Cloudflare.
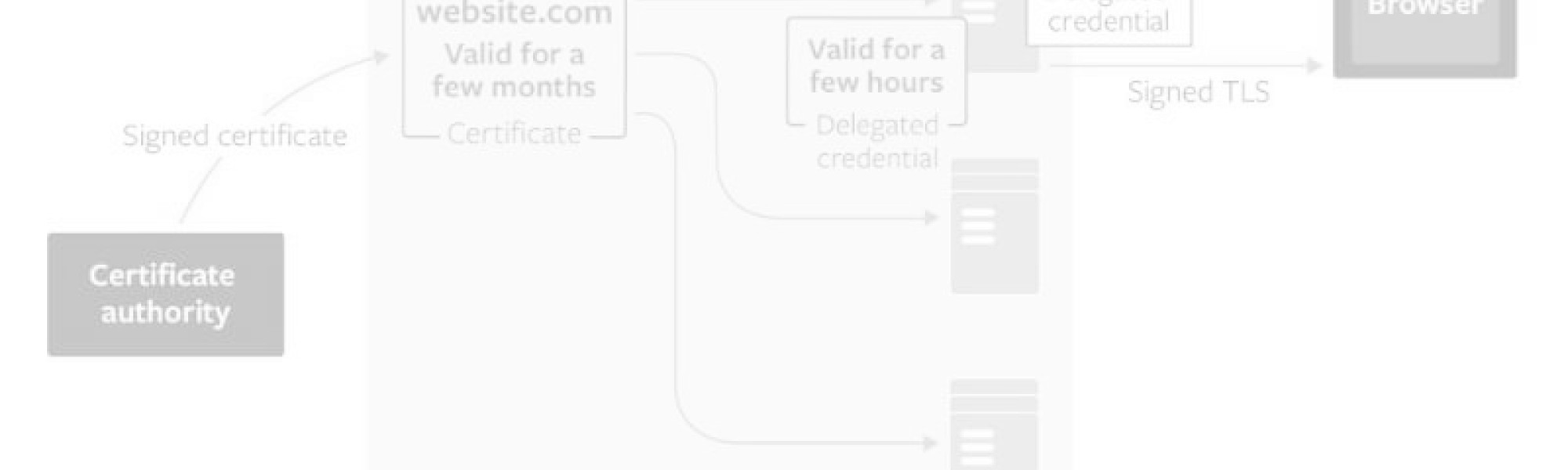
The TLS Delegate Credentials extension allows site owners to create and deploy short-lived TLS private keys to these servers instead of the real private key.
Called delegated credentials, these keys live up to seven days and can be rotated automatically once they expire. If an attacker somehow intercepts the private key from the web server, the attacker actually has the delegated credential and not the real private key. That delegated credential works for just a few days, which is better than months (or a year) for the real TLS private key. A new key can be created and pushed out to TLS servers before the current delegated credentials expires, which lets site owners keep up with the short expiration windows.
“They [delegated credentials] work like a power of attorney: your server authorizes our server to terminate TLS for a limited time,” Cloudflare’s head of research Nick Sullivan and cryptography engineer Watson Ladd wrote. “When a browser that supports this protocol connects to our edge servers we can show it this ‘power of attorney’, instead of needing to reach back to a customer’s server to get it to authorize the TLS connection,” Sullivan and Ladd said.
In current TLS setups, if a certificate’s private key is stolen before its expiration date, the server operator can either just wait out the clock for the certificate to expire, or have the certificate authority revoke the certificate. Even if a certificate has been revoked, each browser (and client device) has its own mechanism for learning what certificates are no longer valid—making certificate revocation a complicated process. This is partly why there has been a push to shorten certificate validity periods so that site operators don’t have to rely on revocation to protect themselves.
“The shorter the certificate lifetime, the less likely a certificate will need to be revoked before it expires.,” wrote Facebook engineers Subodh Iyengar, Kyle Nekritz, and Alex Guzman.
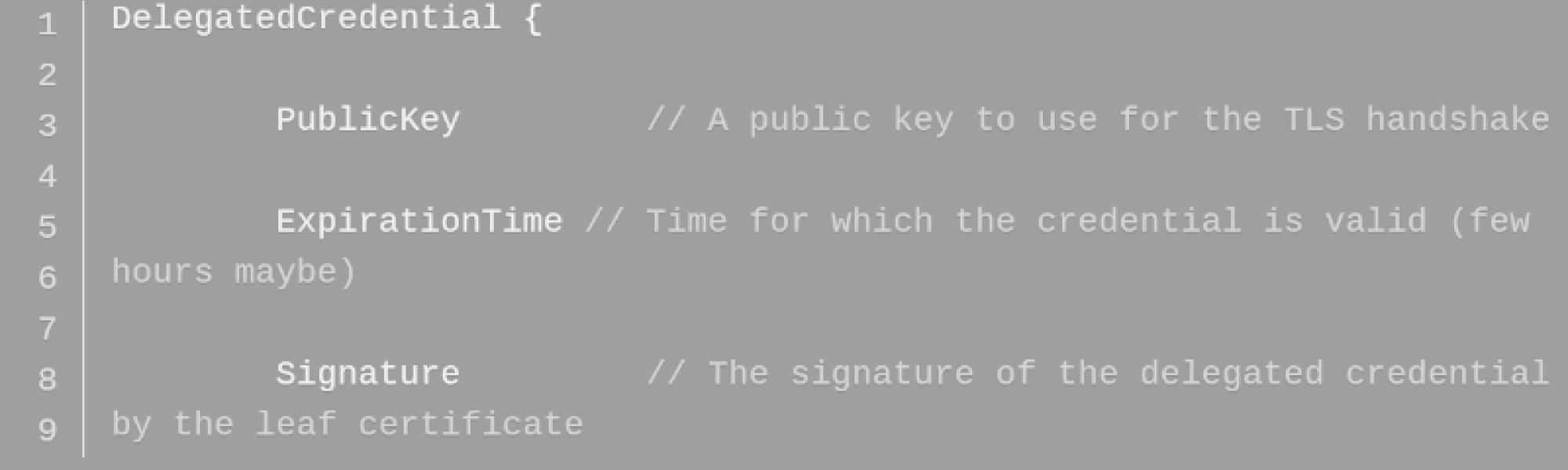
TLS delegated credentials are generated by the web server and not the certificate authority, so the site owner doesn’t have to depend on the CA to issue the new keys every few hours. The delegated credentials are composed of the key’s public key and the private key’s expiration date. The delegated credential is signed by the certificate (leaf certificate) obtained from the CA, and bundled with that certificate. The delegated credential has its own public key to establish secure connections and does not need the real TLS private key.
Site owners don’t have to put the real private key on each web server as they can use the delegated credentials instead. Even if an attacker successfully compromises a server and steals the private key, other web servers are still safe from man-in-the-middle attacks.
Mozilla implemented support for TLS delegated credentials in the Nightly versions of Firefox. The configuration can be activated through about:config via the security.tls.enable_delegated_credentials option. Mozilla has also set up a test site to show how the experience would look from the user’s perspective.
“As gratifying as it can be to solve a problem for ourselves and our customers, it can be even more gratifying to solve a problem for the entire Internet,” Cloudflare’s Sullivan and Ladd wrote.
