A security vulnerability in Microsoft Exchange that was fixed in February is still unpatched on hundreds of thousands of Exchange servers, according to the latest numbers from Rapid7.
Rapid7 used Project Sonar to compile a list of of internet-facing Exchange servers on March 24, and found over 350,000 servers running a vulnerable version of Exchange. The team looked for publicly-facing Exchange Outlook Web App (OWA) services, and found 357,629 vulnerable servers out of 433,464 Exchange servers, said Tom Sellers, the manager of Rapid7 Labs. That means only about 17 percent of the Exchange servers in this analysis had been updated.
Microsoft released the security update for CVE-2020-0688 on Feb. 11. An attacker with any stolen Exchange user account could trigger the vulnerability and remotely execute arbitrary code with system-level privileges. In many environments, the attacker could potentially compromise the entire Exchange environment—which includes email—and all of Active Directory.
Attack groups like to go after email servers such as Exchange because it lets them read all of the organization’s communications and plans, and control what the organization says. An attacker could “divulge or falsify corporate email communications at will,” Simon Zuckerbraun, a security researcher with the Zero Day Institute, wrote in a description of the vulnerability.
Under Attack
The remote code execution vulnerability occurs when the Exchange Control Panel web application does not generate a unique cryptographic key during installation, resulting in deserialization of untrusted data. The security update fixes how the cryptographic keys are generated for Microsoft Exchange Server 2010, 2013, 2016 and 2019.
In March, the Cybersecurity and Infrastructure Security Agency called the flaw “an attractive target” for attackers, noting that advanced persistent threat actors were already targeting unpatched servers. Troy Mursch, chief research officer at Bad Packets, observed mass scanning activity for servers vulnerable to this flaw. Threat intelligence and incident response company Volexity “observed multiple APT actors exploiting or attempting to exploit on-premise Exchange servers.”
Microsoft originally rated the vulnerability as “important” in severity because the attacker needs a legitimate Exchange account in order to authenticate against the server before exploiting the flaw. However, that isn’t a significant obstacle, since pretty much any user within the enterprise would have a valid Exchange account. This means attackers can phish Exchange credentials from a very wide pool of potential victims. Attackers can also use LinkedIn and other public sources to figure out potential addresses and launch credential stuffing attacks to try to gain access, suggested security researcher Kevin Beaumont on Twitter.
Volexity Threat Research said some of the attackers “appear to have been waiting for an opportunity to strike with credentials that had otherwise been of no use.” The groups may have obtained valid Exchange credentials previously, but had been unable to use them because of security controls that were in place (such as two-factor authentication), the research team wrote. The attack groups were exploiting the vulnerability to run system commands to conduct reconnaissance, deploy webshell backdoors accessible via OWA, and executing exploitation frameworks in memory.
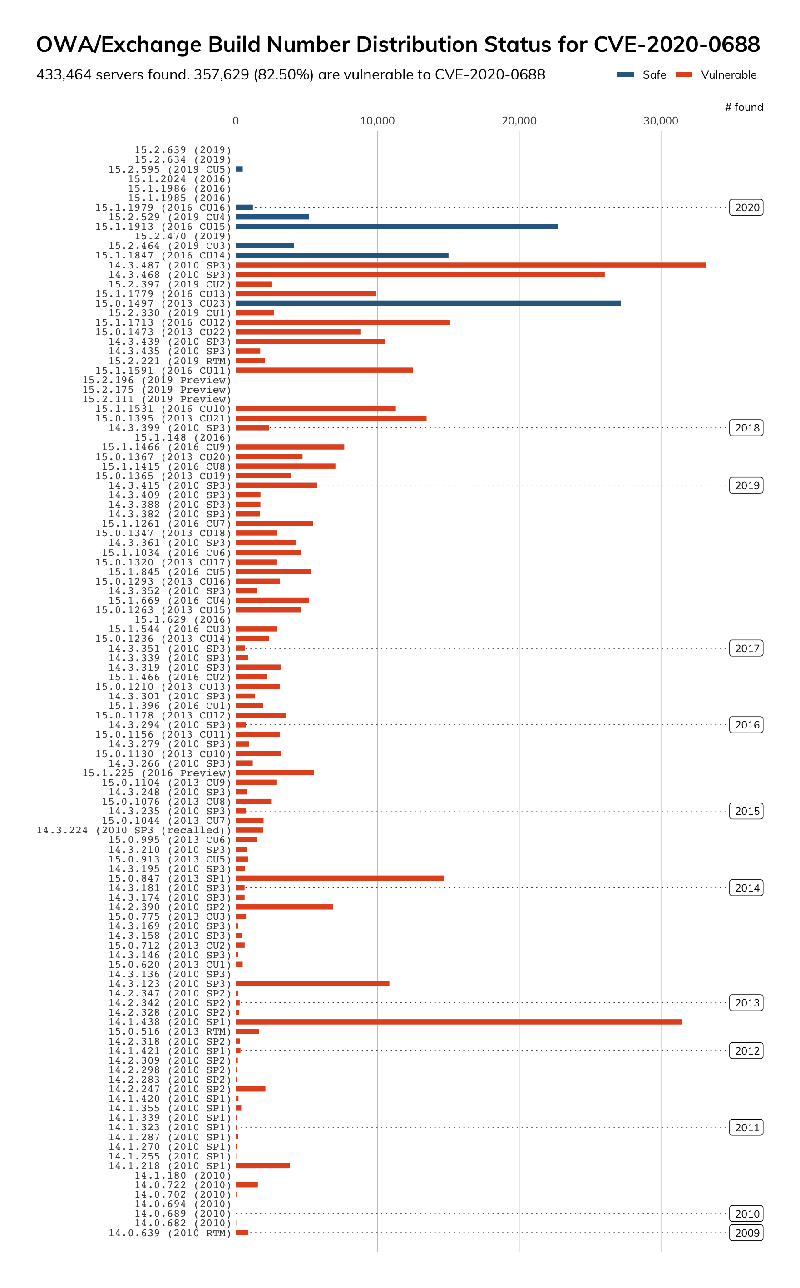
Different version numbers of Exchange servers with Internet-accessible OWA services running. The year indicates the last time the server was patched. Source: Project Sonar, Rapid7
The Project Sonar highlights other worrying issues other than the low number of servers that have applied the February update. There were over 31,000 Exchange 2010 servers which has not been updated since 2012, and nearly 800 Exchange 2010 server that have never been updated, Sellers said. There were 10,731 Exchange 2007 servers—it is a good thing this version doesn't have the vulnerability because a patch would not be available. Add in the 166,321 Exchange 2010 servers (originally scheduled to be sunsetted in January, but now scheduled for October) that have not yet been patched, and that is a lot of vulnerable servers currently accessible on the Internet.
“That’s a staggering number of enterprise class mail systems that will be unsupported in a few months,” Sellers said.
The analysis may not have uncovered all the vulnerable servers because the checking method the research team was using didn’t “provide the version precision we’d need,” Sellers said. Some of the servers the team had designated as “safe” could actually be vulnerable, and since some of Microsoft’s updates didn’t update the operating system’s build number, the analysis had a “degree of uncertainty.”
Administrators have to be very careful about updating mission-critical servers because they can’t afford to have systems offline for any amount of time. Even a few minutes of downtime for an email server can have a pretty severe impact on the organization—such as lost sales and delayed communications with customers. Throw in a situation where many of the administrators don’t have ready access to the data center, and there may be even more reluctance to risk bringing down the mail server for maintenance.
Typically, Microsoft server patches are deployed much faster than other vendor updates, with patching rates as high as 50 percent of the servers patched within 30 days.
It's unclear if this is abnormally slow for Exchange at this moment, but, given the state of affairs around COVID-19, uptime on mail servers is incredibly important right now," said Jonathan Cran, head of research at Kenna Security. "Patch cycles have almost certainly been delayed across many products.
Organizations should update servers running software that is no longer supported to a newer version. If updating the Exchange server is not an option, administrators should force a password reset for all Exchange accounts so that stolen credentials cannot be used at this time.
[Updated to reflect information from Sellers about Exchange 2007 not being vulnerable to this vulnerability]
