Speed—how fast attackers operate—is important to understand, but it is more than knowing the initial-time-to-compromise (time to find the vulnerability and compromise the endpoint) or dwell time (time attackers stay in the network to carry out their activities). CrowdStrike also considers “breakout time,” or the time it takes a threat actor to start moving laterally within a network after the first endpoint has been compromised.
Breakout time is the window when defenders can detect the initial intrusion before the attackers have had a chance to compromise other systems or cause any damage. “Breakout time is important because it represents the time limit for defenders to respond to and contain or remediate an intrusion before it spreads widely in their environment and leads to a major breach,” CrowdStrike wrote in its 2019 Global Threat Report. “While certainly not the only metric to judge sophistication by, this ranking is an interesting way to evaluate the operational capabilities of major threat actors.”
Depending on the kind of tools being used, CrowdStrike said that some cybercrime gangs can rival nation-state actors in their speed.
Attackers act quickly—CrowdStrike analyzed tactics, techniques, and procedures used over the past year and found that attackers were compromising other systems in the network within hours of getting that initial foothold into the network. Based on data from over 30,000 intrusion attempts by adversary groups tracked by CrowdStrike, the report found that average breakout times varied based on type of the attack group and motivation. The company, which looks at a lot of nation-state activity, found that Russian state-sponsored hackers took 18 minutes and 49 seconds to start moving laterally after the initial breach. North Korean threat groups were the second fastest, with an average breakout time of 2 hours and 20 minutes. Chinese actors took roughly 4 hours, and Iranian groups took 5 hours and 9 minutes, according to the report.
In comparison, cybercrime groups had an average breakout time of 9 hours and 42 minutes.
“While we certainly expected them [Russian threat groups] to come out on top, given how effective their tradecraft usually is in comparison with other threat actors, even we were surprised by the data and how fast they can move inside a network once they get a foothold,” CrowdStrike co-founder and CTO Dmitri Alperovitch wrote.
Cybercriminal Activity
Most enterprises have more to fear from cybercriminals than nation-state actors, and the fact remains that criminal gangs take less than half a day—a handful of hours to a little longer than the standard workday—to spread through the network. There is a wide range of skills among cybercrime groups, so some criminal groups can move much faster than others. Depending on the kind of tools being used, CrowdStrike said that some cybercrime gangs rival nation-state actors in their speed.
Miss an alert of a suspicious login attempt, and by the time the second shift comes on, or the next day, and the attackers are already entrenched in the organization.
The average breakout time across all groups in 2018 was 4 hours and 37 minutes, which is much longer than 2017’s average breakout time of 1 hour and 58 minutes. The difference is that there were more unskilled attack groups operating in 2018. The easy availability of attacker playbooks and access to ready-to-go infrastructure has made the barrier to entry much lower.
The window of opportunity for defenders is extremely narrow, so defenders have to be able to recognize the tactics, techniques, and procedures used by attackers. CrowdStrike mapped the tactics to the MITRE ATT&CK framework, a standard way to describe the different hands-on attack techniques used, from initial access all the way to exfiltration. Malware and botnet activity is not covered by ATT&CK, but CrowdStrike included them in this analysis.
“Successful cyberattacks do not end with an initial intrusion, regardless of whether they’re perpetrated via malware or malware-free attack vectors,” CrowdStrike wrote in the report. “Each attack has an ultimate objective, such as theft of data or computing resources, and the attack typically requires multiple steps along the way to reach that objective.”
CrowdStrike observed a “substantial use” of scripting techniques, including PowerShell, Office Document Macros, JavaScript, and command-line interface, to discover other systems in the network, establish persistence, and to move laterally. The fact that attackers are increasingly adopting common system administration tools means that traditional methods of protection, such as relying on hashes and basic file blocking, are no longer sufficient.
“Actions involved in discovery are easy to miss, as the attacker is typically using the same standard commands and tools that are often used for legitimate administration purposes,” the report said.
One way enterprise defenders can tackle this challenge is to watch for “unusual clusters of discovery activities, at unusual times,” CrowdStrike recommended. Using multi-factor authentication would thwart attempts to use stolen or brute-forced credentials.
Cybercrime groups are increasingly adopting tactics typically used in targeted attacks to deliver ransomware to large organizations, CrowdStrike found in its analysis. The report also noted an uptick in the amount of collaboration between sophisticated eCrime actors.
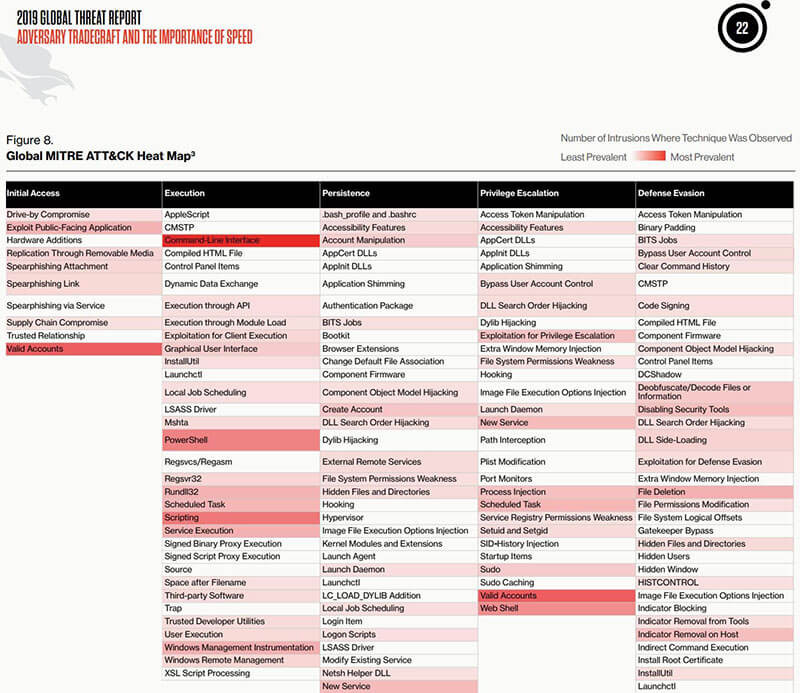
CrowdStrike mapped attacker tools and techniques against the MITRE ATT&CK framework to help enterprises focus their defenses. (Source: Figure 8 from CrowdStrike's 2019 Global Threat Report)
Defense Focus
CrowdStrike’s recommendations focused on IT hygiene, such as asset management to understand what systems and data exist in order to know what to protect, vulnerability and patch management to prioritize what to fix or mitigate, multi-factor authentication to protect accounts, strong privilege access management to align tasks with who actually needs to perform them, endpoint protection, and user awareness are still foundational. They still matter.
While malware remains a “significant component” of modern attacks, it is just one element in an overall attack campaign. A defense strategy that just looks for malware infections will miss a lot of attacker activity, especially as more groups focus on techniques “intended to hide or obscure attacker behaviors,” the report said. As endpoint protection get better at finding and stopping malicious behaviors, attackers are forced to get sneakier.
“Defenders must look for early warning signs that an attack may be underway, such as code execution, persistence, stealth, command control and lateral movement within a network,” CrowdStrike said.
CrowdStrike also noted attacker techniques varied geographically. Malware was significantly the most prevalent attack method in Latin America, while scripting was the most prevalent method for Europe, Middle East, and Africa. In North America, there wasn’t a single preferred attack technique, as malware, credential-dumping, and using data from the local system were prevalent. Just as enterprises have to understand the attacker profile—who is the most likely to target them—they also need to understand the techniques most likely to be used against them to properly prioritize their security investments.
The Verizon’s Data Breach Investigations Report peg the average dwell time for attackers at about six months, and CrowdStrike’s breakout time shows that the first day—the initial hours—are critical times to respond. That doesn’t mean if the defenders don’t act within that window that they can’t stop the attackers or reduce the impact of the attack.
Speeding up response is key, and breakout time can help benchmark the time it takes to detect, investigate, and remediate. CrowdStrike outlined a “1-10-60 rule,” to detect intrusions under a minute, perform a full investigation under 10 minutes, and eradicate the adversary in under 60 minutes. Being able to meet this 1-10-60 benchmark is still out of reach for most organizations, but they can start with making sure they are taking care of basic IT security principles. Improving visibility and automated analysis and remediation will go a long way towards reaching this benchmark.
