Facebook has a new tool to help domain owners find phishing domains with spoofed URLs.
Criminals employ various tricks to make their phishing sites look legitimate, from using the same color palette and images to creating fake domains that look very similar to legitimate websites. Anti-phishing training emphasizes verifying the URL, to catch phishing attempts from sites such as helpdesk-facebook.com, faceb00k.com, faecbook.com.
It also doesn’t help that just as most of the web is moving to HTTPS, so are the criminals. They obtain valid TLS certificates so that browsers would display the site as “secure” or a padlock icon.
However, the shift to HTTPS gives enterprise defenders an edge: they can use Certificate Transparency to find fraudulent domains.
Launched by Google in 2013, Certificate Transparency adds a degree of accountability to certificate authorities issuing TLS certificates. CAs are required to maintain a public and verifiable log of each TLS certificate they issued, and anyone could look through the entries and verify which certificates have been issued for which domain. Certificate Transparency logs are useful for finding all certificates issued for a particular domain, and owners can figure out if any had been issued mistakenly. The logs can be used to find certificates for any domain, so owners can look for domains that look like their own.
However, looking at CT logs can be a challenge, given the high volume of certificates being issued (over 846 million entries made to the set monitored by Google, as of the end of 2017). There are also many public CT logs, and the list can change over time, so monitoring means periodically fetching all certificates from all logs in order to have the most up-to-date view. There are tools to make it easier to search Certificate Transparency logs for specific domains, or to find potential phishing domains but they all tend to be fairly manual and time-consuming.
Facebook's new service
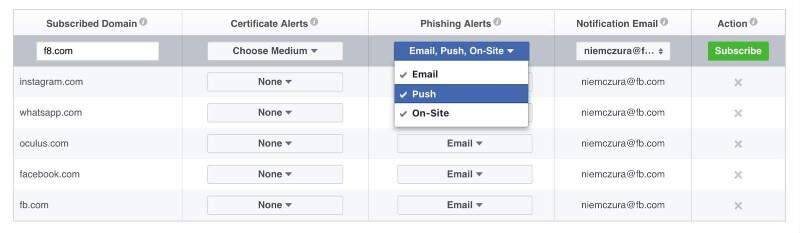
The sheer number of possible variations makes finding and shutting down phishing domains even more manual and frustrating. Facebook launched its Certificate Transparency Monitoring Tool back in 2016 to let domain owners easily see all certificates associated with their domains and be notified when new ones were issued. The company extended the tool with a phishing domain monitoring service to make it easier for domain owners to see spoofed domain names.
“By taking action to shut down bad domains that are created solely to trick people, legitimate website owners can protect their sites and help prevent others from falling for harmful scams,” wrote Facebook engineers David Huang, Bartosz Niemczura and Amy Xu.
The service looks for domains names that look similar to legitimate names and flag them as malicious. For example, the tool can detect homograph domains, such as if the letter “o” was replaced by the number “0,” as in “faceb00k.com” or if the the “o” was the Cyrillic small letter (0x43E), and not the Latin "o" (0x6F). It can also detect combo-squatting attempts such as helpdesk-facebook.com, or typo-squatting with misspelled names, as in faecbook.com. There are also too-long domain names that are harder to read on mobile devices, such as facebook.com.long.subdomain.that.will.not.be.fully.shown.on.mobile.devices.com.
The UI is set up so that the developer, or the domain owner, just needs to specify the domain name and the tool takes care of finding possible variations, said Huang. The tool uses a combination of techniques including regexp and other approaches. Facebook will continue to refine the tool to expand its detection capabilities. This takes the guesswork and manual entry out of the process.
Owners of the legitimate domains who subscribe to the free phishing domain monitoring service will receive notifications about the malicious domains via email, push, or on-site notifications. Developers can also use the newly-extended Webhook API to integrate the feature into their own systems and be notified whenever a phishing attempt is detected.
Facebook is just providing notifications with this tool. Domain owners will still have to reach out to domain registrars (suspend bad domains for intellectual property infringement), browser vendors (blacklist domains for deceptive websites), and certificate authorities (revoke certificates) after receiving a notification about a potentially malicious domain. Users also need to be warned about potential attacks using the domains.
Facebook has caught phishing sites trying to impersonate Facebook services with this tool, such as ɯhatsapp.com and facеbook.ml (they look legitimate but are actually using Unicode characters that are different from the original domains), and instagram.com-verify.me.
“We have been using these logs to monitor certificates issued for domains owned by Facebook and have created tools to help developers take advantage of the same approach,” the engineers wrote.