Many companies offer bug bounties to security researchers to find vulnerabilities in their applications. Microsoft is going one step further with its new Microsoft Identity Bounty Program by offering researchers bounties for finding and reporting vulnerabilities in OpenID standards.
Modern security and strong digital identity goes hand in hand. Users need to be able to access online services and tools and enterprises need to know what is happening across multiple systems within a network. Companies like Microsoft have invested heavily in identity services (Microsoft Account for consumers and Microsoft Entra ID for enterprises) to let registered users use a single account to access different applications. Weaknesses in how identity is handled can lead to stolen information and financial loss. The last thing Microsoft wants is for criminals to exploit a security flaw in its digital identity products.
“A customer’s digital identity is often the key to accessing services and interacting across the internet,” principal security group manager Phillip Misner wrote on the Microsoft Security Response Center blog.
Misner touted Microsoft’s contributions to “the creation, implementation, and improvement of identity-related specifications that foster strong authentication, secure sign-on, sessions, API security, and other critical infrastructure tasks.” To illustrate the company’s continued commitment to the industry identity standards, the Microsoft Identity Bounty Program will extend beyond Microsoft Account and Microsoft Entra ID “to cover those certified implementations of select OpenID standards.”
Microsoft’s decision to include specification vulnerabilities will help strengthen its own identity services, but it will also benefit the broader identity ecosystem. OpenID is an open standard that describes how users can use an existing account to log in to other services without having to create new passwords for each one. Microsoft uses OpenID Connect in its identity services, and so do other tech companies, including Google, Ping Identity, and Salesforce.
Vulnerabilities in specifications are really tricky, because they are in the design, not code. These vulnerabilities exist because of a missing top-level requirement, someone didn’t consider the implication of what would happen with an existing requirement, or changes in the technology or use case uncovered a new situation that no one thought of during the original specification design. Developers implement the specification differently because they are writing their own code. So a vulnerability in the implementation--the actual product--may not exist in other implementations, but a vulnerability in the specification will be present in every implementation that relies on that specification. Exceptions exist, since developers could have coded that part of the specification to address the issue for their own implementation.
For the most part, specification vulnerabilities specification has far-reaching consequences since every implementation has to be checked to verify whether it has the flaw and the issue fixed independently. When Armis Security discovered BlueBorne, a family of vulnerabilities in the Bluetooth specification which could have let attackers hijack any device using Bluetooth, researchers reported the flaws and worked with Google, Microsoft, Apple, Samsung, and the Linux kernel team.
If Microsoft had just focused on its own products in the bounty program, any reported issues would be fixed in its own OpenID implementation. By extending the program to include specification vulnerabilities, Microsoft can help highlight issues that affect non-Microsoft OpenID products as well.
We are extending our bounty to cover those certified implementations of select OpenID standards.
The bounty program doesn’t cover every vulnerability in every OpenID standard--just the ones that Microsoft uses in its implementations. Even so, that is a pretty strong list, as it includes the family of OpenID Connect products (OpenID Connect Core, OpenID Connect Discovery, OpenID Connect Session, OAuth 2.0 Multiple Response Types, and OAuth 2.0 Form Post Response Types). Microsoft’s [certified implementations] (http://openid.net/certification) of the OpenID standards will also be covered.
“Identify an original and previously unreported vulnerability in listed OpenID standards or with the protocol implemented in our certified products, services, or libraries,” the company wrote in the Identity Bounty Program description.
The program will accept reports of issues affecting login and account pages on Microsoft domains including Windows, Microsoft Online, Live, Azure, Active Directory, and Office, as well as in the latest versions of the Microsoft Authenticator app for iOS and Android. The program will not accept reports related to denial-of-service problems, Web applications affecting unsupported browsers and plugins, or ways to bypass two-factor authentication that require having physical access to a logged in device. Microsoft will also not pay for reports from from automated tools or scans.
Submissions must be for original, previously unreported vulnerabilities that can lead to the takeover of a Microsoft account or Microsoft Entra ID account. Payouts start at $500 for incomplete submissions related to cross-site request forgery, authorization flaws, or sensitive data exposure. High-quality submissions for multifactor authentication bypass or standards design vulnerabilities can lead to $100,000 payouts.
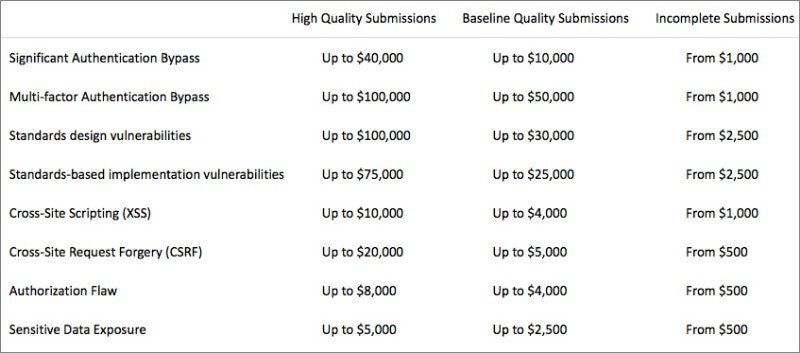
Microsoft will pay up to $100,000 to researchers who submit standards design vulnerabilities to the Microsoft Identity Bounty Program.
