Cybercriminals continue to use remote login credentials in their attacks because it is a highly successful method for getting into networks and compromising systems.
Remote access tools are highly useful because it allows administrators to manage systems without being in front of the machines, such as deploying updates and providing technical support, and lets employees access systems in the office while they work from home. Attackers can exploit RDP to get access to the system with the same level of permissions and access that a legitimate user on the same machine would have. The permissions would also let the attacker move around the network to find other vulnerable systems or to find (and steal) sensitive information.
Recent research from ESET found that attacks against Remote Desktop Protocol grew by 768 percent in 2020—a sign of the attacks’ effectiveness. Attackers are also using RDP to launch distributed denial-of-service attacks and compromise enough machines to lock down the network in a ransomware attack. ESET said there were 29 billion attempted RDP attacks in 2020.
“One of the most pressing reasons to pay attention to RDP security is ransomware, commonly deployed through RDP exploits, and posing a great risk to both private and public sectors,” ESET researchers wrote.
A “majority” of all ransomware attacks gain access to the network by exploiting weaknesses in Remote Desktop Protocol (RDP) software, or the way it is deployed, according to Malwarebytes Labs.
Last October, Jeremiah Grossman, CEO of Bit Discovery analyzed 102 top United States companies across nine industry sectors to look for assets—devices which could be accessed over the Internet—that had open RDP ports at some point that month. For his purposes, asset referred to a domain name, subdomain, or IP address of the system that was visible from the Internet.
Each pair of bars represents a single industry, which is a collection of data from approximately 10 top—as defined by revenue—companies based in the United States, Grossman said. In the top chart, which shows the overal asset inventory size, gives an idea of how many assets these organizations have. Retailers and financial services organizations typically have larger number of assets than insurance firms (as of October 2020), according to this chart.
Both the mean and median are tracked because some organizations are outliers with extremely large number of assets in their inventories. That was the case with the figures for the hotel industry—Grossman said the outlier in this case was Marriott. Having both numbers help get a better understanding of the size of asset inventories. In the case for food & grocery, four companies had “far larger inventories” than others in the category, which skewed the mean significantly.
Bit Discovery actively tracks approximately 4.5 billion devices—the systems belonging to organizations which are visible from the Internet, from outside the corporate network. There are “too many systems with too many vulnerabilities,” Grossman said. Organizations often have that “one weird system” that they think is fine because attackers will never find it.
“They’ll find it,” Grossman warned.
In the bottom chart, Grossman looked at the same companies across the industries and counted the number of open RDP ports that onth. A “top” United States hotel was likely to have a median of three open RDP ports last fall. (The mean for hotels is much higher because of Marriott’s massive inventory, and by implication, more exposed RDP ports.) A “top” retailer was likely to have four open RDP ports.
An open port doesn’t necessarily mean a vulnerable port, Grossman cautioned. If it is configured to require authentication and the credentials are protected, then the fact that there is an open RDP port may not be as big an issue for that organization.
But for many of these organizations, they may not even know they have these ports open, or that there may be a problem.
Attackers are “jiggling a doorknob, and want to just find one that opens,” Grossman said. “There are a lot of assets, a lot of doorknobs.”
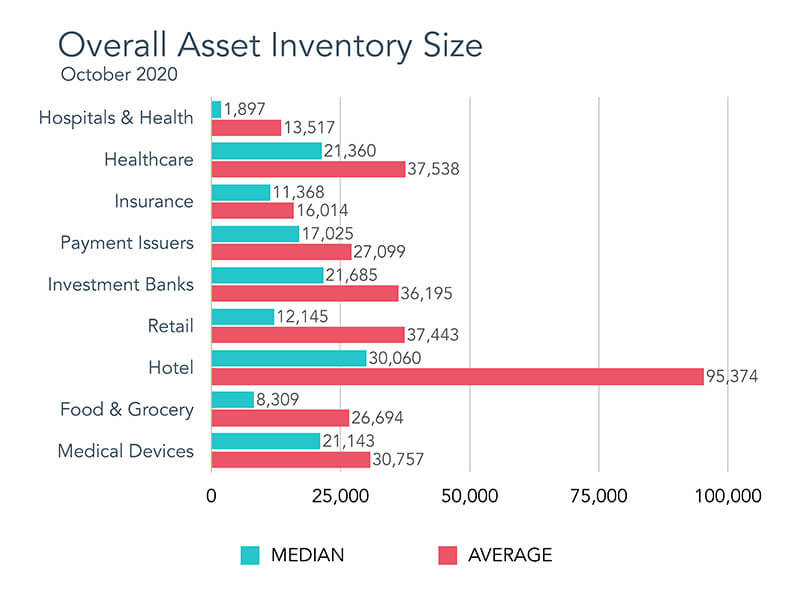
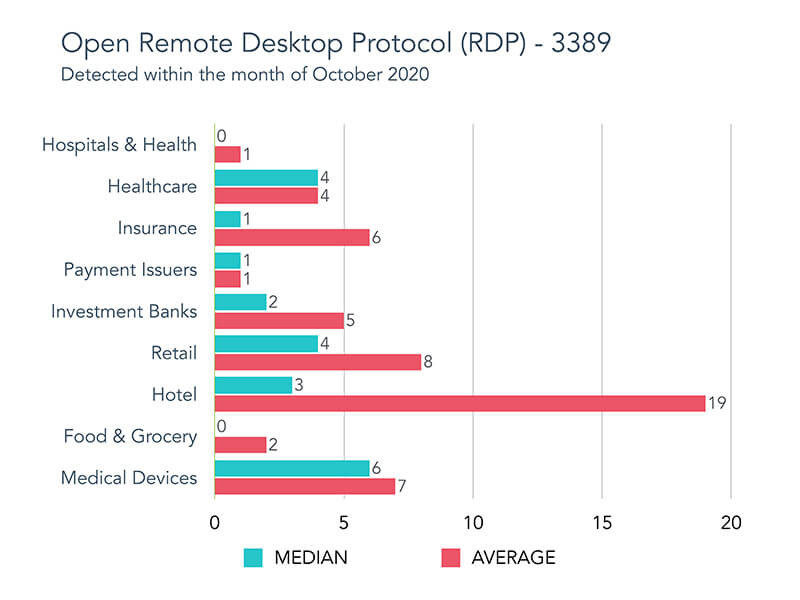
In the top chart, BitDiscovery looked at the overall asset inventory sizes for "top" companies based in the United States across nine industries. The bottom chart shows how many of those systems had open RDP ports at some point in October 2020. Source: Jeremiah Grossman, BitDiscovery.
Grossman's analysis was based on an statistic in the H1 2020 Cyber Insurance Claims Report from cyber insurance provider Coalition: an analysis of the claims data from policyholders with cyber insurance showed that phishing, remote access, and social engineering were used in attacks listed for 89 percent of the claims. More specifically, 29 percent of claims involved remote access--such as RDP--Coalition said in the report.
Insurers are absolutely looking at RDP, Grossman said. A carrier may decline to underwrite a policy if there too many RDP ports open, or may allow a policy but decline coverage the next year if the problem with RDP persists.
"Organizations that are particularly vulnerable [to ransomware attacks] often manage sensitive data, enable Internet-exposed remote access tools (e.g., Remote Desktop Protocol), and use third-party IT providers," Coalition said in its report.
In the past, attackers took advantage of the fact that RDP was enabled on machines even when it wasn’t needed. So along with emphasizing multi-factor authentication and strong password security (instead of using the admin/admin combination, or even worse, blank passwords), a common piece of advice was to disable RDP ports on machines unless there was a specificc reason to have it enabled. With so much of the workforce relying on remote access over the past year, RDP has become much more necessary, which means there are more machines that actually need to have open RDP ports. Configuring RDP securely-- password security and other security controls--is more crucial than ever.
“The truth is that simply telling people to harden RDP isn’t working fast enough,” Malwarebytes Labs said.
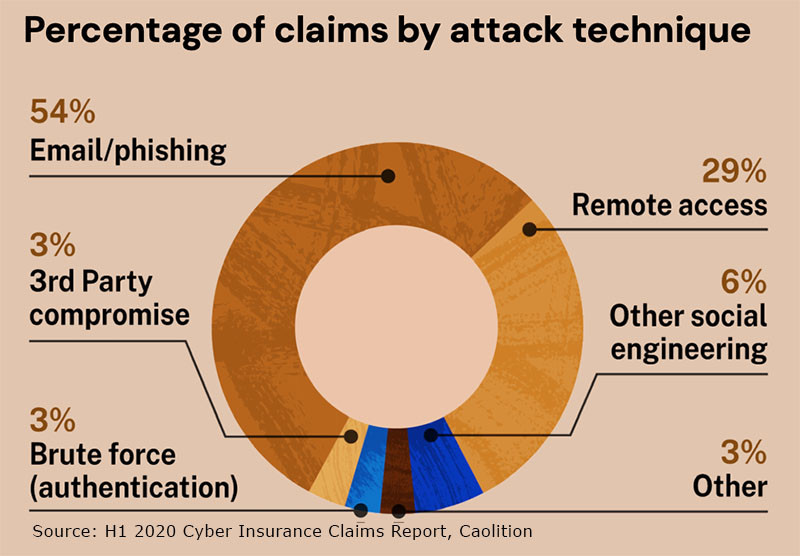
In an analysis of cyber insurance claims from its policyholders, Coalition found that 29 percent of the incidents used remote access. Source: Coalition's H1 2020 Cyber Insurance Claims Report.

