The latest Cyentia Institute research shows that even the most costliest mega-breaches or crippling sophisticated nation-state attacks don't impact victims equally. And even if most organizations won't experience these types of catastrophic security incidents, understanding the factors that led to them and the outsized impact they have on victims is a valuable lesson to learn.
Back in March, the data scientists at Cyentia Institute analyzed a dataset spanning tens of thousands of security events over the last decade provided by insurance data provider Advisen to understand the frequency and financial impact of security incidents. The Information Risk Insights Study (IRIS) found that financial losses as a result of a security incident typically ran about $200,000, but 10 percent of the breaches exceeded $20 million in losses. IRIS found differences other than financial losses between “typical” and “extreme” events. The IRIS 20/20 Xtreme report followed up on that research by narrowing the focus just the “extreme” events in the last five years.
“Our primary goal remains the same as the IRIS 20/20—to clear the fog of fear, uncertainty and doubt (FUD) surrounding cyber risk and help managers see their way to better data-driven decisions,” Cyentia Institute wrote in the report.
Just 103 incidents truly fit the definition of an extreme event, which the Cyentia team defined as the number of records exposed—at least 20 million records—and total financial losses—at least $20 million. Both cut-off points came from the original IRIS research. Just 0.5 percent of incidents in the IRIS dataset involved that many records, and 10 percent cost organizations that much. IRIS Xtreme focused on 56 security incidents over the last five years with “publicly discoverable losses of or above $20 million” and 47 incidents where at least 20 million records were exposed.
Taken in aggregate, these events totalled $18 billion in reported losses and resulted in 10 billion compromised records. Loss includes expenses incurred during response and remediation, losses associated with lost productivity, and fines and judgements after the incident. In one incident, the researchers included the impact of a cancelled IPO, which was an example of “softer opportunity costs that also need to be considered.” The median loss among “extreme” incidents in IRIS Xtreme was $47 million, with just over one-in-four exceeding $100 million, Cyentia Institute said. Five organizations—Facebook, Merck, FedEx, Equifax, and Experian—experienced incidents with $1 billion or more in losses.
Per the Wall Street Journal, both Merck and FedEx were hit by the 2017 NotPetya ransomware attack. Cyentia found that NotPetya alone accounted for 75 percent of all the extreme events in its dataset from mid-2017.
By collecting additional data points associated with these events, Cyentia was able to break down the costs, categorize incident types, identify actors and the actions they took, and understand how these events impacted the victim organizations.
It sometimes feels like the attacks are getting more destructive over time, and there is some evidence that extreme events grew more common between 2015 and 2020 in the data, but not yet enough to say so conclusively. The data doesn’t suggest that extreme events are becoming more costly over time, although that may change as regulators start enforcing their rules and applying larger fines, such as under General Data Protection Regulation (GDPR).
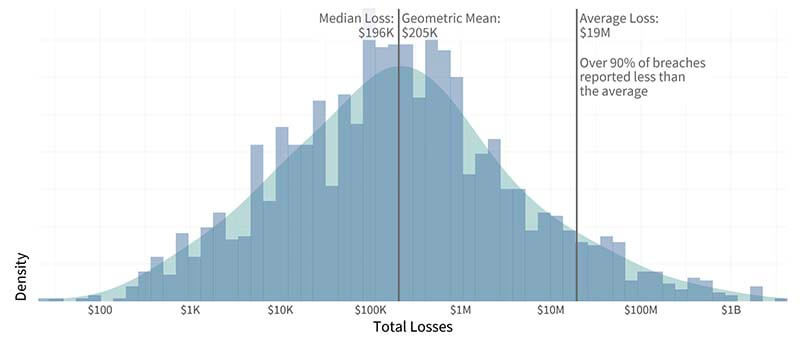
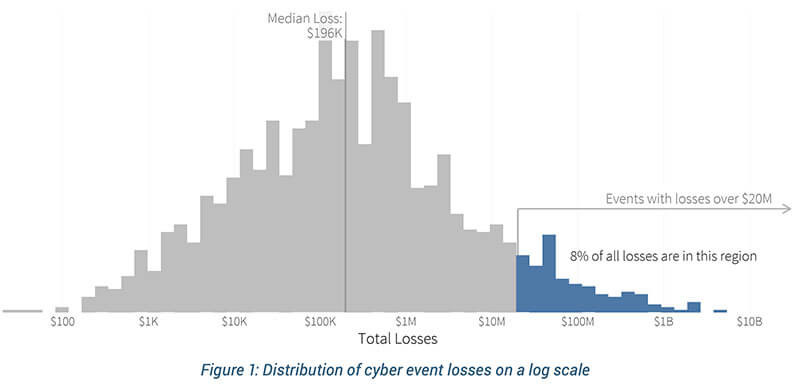
The above figure shows the distribution of breach losses over ten years, and the median breach loss of around $200,000. (Source: Figure 10, IRIS 2020, Cyentia Institute) There is a long tail of really expensive incidents, and the below figure shows that less than 10 percent of the incidents had losses of $20 million or more. (Source: Figure 1, IRIS 2020 Xtreme, Cyentia Institute)
Impact is Not Equal
Even among these extreme incidents, there were some outliers. For some, they were devastating, costing nearly 100 times the organization’s annual revenue, and for others, the impact was easier to shrug off, costing less than 0.1 percent. The researchers found a “clean 70/30 split” in the data, with 70 percent of the incidents had losses amounting to 10 percent or less of annual revenue. The “unlucky” 14 percent experienced costs exceeding annual revenue.
The Fortune 1000 may be writing a larger check, but the SMB is the one that is going to be hurting.
The original IRIS analysis found that larger organizations—the Fortune 1000—would be likely to have higher losses in terms of actual dollars compared to smaller organizations, but the larger organizations would have the financial cushion to absorb the loss. The disproportionate impact on the SMB—those with less than $50 million in annual revenue— was even more stark in IRIS Xtreme.
“Major cyber loss events cause far greater relative harm to small and medium-sized businesses (SMBs) than larger enterprises,” Cyentia wrote.
Impact isn’t measured in just dollar amounts. “Consequences like executive churn, organizational bankruptcy, and SEC scrutiny can make board members sit up and pay attention more than any single dollar value can,” Cyentia noted. Cyentia found that 27 incidents were reported in Securities and Exchange Commission filings and 23 prompted some form of government inquiry, such as Congressional hearings. About a quarter of the incidents led to changes in executive leadership, as people resigned or were fired for their role in the incident (either for the incident happening under their watch or how they handled the response). The fear of going out of business because of a security incident is a big concern, but in this dataset, there were only three events that led to the organization to shut its doors.
Focusing on total losses also obscures the fact that the impact is uneven throughout the organizations It is difficult to find detailed breakdown of losses, but Cyentia was able to piece together a “hypothetical invoice of misery” using financial reports, public records, and other sources. The median value for productivity and revenue loss among these extreme events was $68 million, while the median response cost was $24 million. Many times, the focus after a security incident is on how much the organization spent responding to the incident, but the analysis suggests that is not the biggest part of the price tag. Even replacement costs—getting new servers or upgrading systems to avoid a repeat of the incident—have a higher median value, at $32 million.
Cyentia found that how well a firm responded to the incident impacted total losses incurred. It makes sense: Equifax was excoriated for how it handled the massive data breach which impacted 143 million American consumers. In Cyentia’s analysis, how well a firm responded to the extreme event was a matter of perception, since not making public mistakes in its response doesn’t mean there were no issues internally. The median total loss in events where the organization was perceived as handling response poorly was $109 million, compared to the median total loss of $39 million where the organization didn’t display any clues about how well it handled response.
It is far easier to find information about costs incurred during response, losses associated with lost productivity and revenue, and fines that arise from regulatory actions and lawsuits. While reputational damage and competitive disadvantage is something that gets regularly mentioned as part of the costs of a data breach, Cyentia did not uncover data indicating what those losses would look like.
“Losses caused directly from the event itself are more common—or at least more discoverable— than those incurred by the reaction of outside parties,” Cyentia said. As a result, businesses may benefit from investing in insurance policies specifically for cybersecurity incidents and having incident response teams on retainer (or having in-house teams).
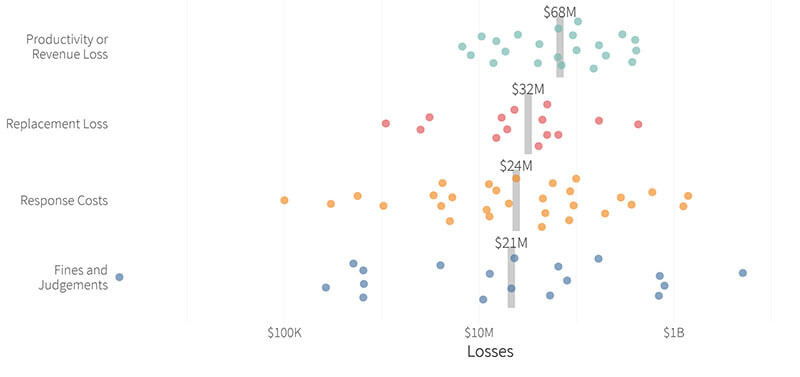
When looking at where most of the losses are being incurred, productivity and revenue losses tend to be the costliest part of an incident, with a median value of $68 million. (Source: Figure 1, IRIS 2020 Xtreme, Cyentia Institute)
Extreme Events Aren’t...Fancy
To hear organizations describe it, data breaches are the result of sophisticated and complex attacks. The data, however, shows that even among these most damaging attacks, most of them were the result of stolen credentials, followed by remote access malware.
Credential-related attacks showed up in 46 extreme events and $10 billion in losses. Remote access malware—backdoors—were used in 31 events. About a quarter of incidents involved web application attacks, such as SQL injection or cross-site scripting, and exploits against known software vulnerabilities (not zero-days!) were used in 22 events. Phishing or pretexting was used in 18 incidents.
Prompter patching may have avoided half of all costs across all events in this study, the researchers noted. The high prevalence of credential related attacks showing up in this report should be the strongest sign that organizations should be using multi-factor authentication.
In case anyone still had doubts that ransomware was a big problem, 21 incidents in IRIS Xtreme involved ransomware. A single ransomware campaign—the NotPetya attack in 2017—accounted for 20 percent of the losses, or $3.5 billion, across all events in this report.
Considering the report looked at some of the most damaging incidents in the last 5 years, it was surprising that only one in five were attributed to state-affiliated actors. So while they’re responsible for 43 percent of all monetary losses in this report, nation-state adversaries aren’t the biggest threats.
It’s easy for organizations to get bogged down with the headlines of catastrophic cyberattacks and then shrug them off because they are too small or too insignificant or too different to experience these types of incidents. Cyentia’s analysis suggests that the dividing line between garden-variety attacks and these extreme events is not all that wide.
The analysis in IRIS Xtreme suggests the organization’s industry sector would be a better indicator of whether an extreme event is something to worry about. Financial, information and manufacturing sectors were victims in more than half of the 103 incidents, according to the report.
“To paraphrase a famous quote from bank robber William Sutton, extreme events occur where the money (or the data) are found,” the researchers wrote. “The Finance and Information sectors have both in abundance.”
Despite being more frequently targeted, the financial sector (22 incidents out of 103) was fifth in terms of total losses, compared to the information sector, which had the highest total losses in this dataset. The researchers speculated that the financial services’ history of risk management helped in mitigating the impact of these incidents.
It is valuable to look at these extreme incidents because “they are happening with surprising regularity,” wrote Derek Vadala, CEO of VisibleRisk, a joint venture between Moody’s and security company Team8, and the report’s sponsor. “There were some very business-relevant events existing in the gray area between commonplace events and the worst kinds of cyber breaches that live at the very edge of the curve.”
Boards need “to know what a significant, adverse cyber event would look like for their organization,” Dr. Jack Freund, the head of methodology at VisibleRisk, wrote at the end of the report. Boards can use the total losses associated with extreme events to determine if they have set aside enough money in their capital reserve (“rainy day fund”) to survive a serious incident and assess if their insurance policies are adequate. “Only then can they truly understand what is required to protect their organization in a holistic way.”

