Cyber criminals don’t just rely on underground forums and criminal marketplaces to trade crimeware tools, sell stolen information, or rent out attack infrastructure. Some of the trading and buying activities happen in the open, using social media.
“[Instead] of wheeling-and-dealing using hidden servers on some mysterious dark web address, a surprisingly large number of cyber scofflaws prefer to operate right out in the open using social media,” researchers from Cisco Talos said.
Talos uncovered 74 Facebook groups—with a total of around 385,000 members—to sell stolen credit card numbers, lists of email addresses for spam and malware campaigns, and login credentials to different servers and applications. They also offered money laundering and transfer services, such as transferring large amounts of cash into an American bank without getting detected.
These groups weren’t hard to find, as they had names such as “Spam Professional” and “Buy Cvv On THIS SHOP PAYMENT BY BTC” (followed by two emojis of money). Anyone with a Facebook account would have been able to find these groups, just by searching with keywords such as “spam,” “carding,” or “CVV.” And once the user joined a group, Facebook’s suggested groups widget bubbled up similar groups for the user to join.
“Facebook’s own algorithms will often suggest similar groups, making new criminal hangouts even easier to find,” wrote Talos researchers Jon Munshaw and Jaeson Schultz.
Hard to Shut Down Groups
Talos initially used Facebook’s abuse reporting mechanism to take down some of these groups before working directly with Facebook’s research team. The abuse mechanism worked sometimes—other times, it was just individual posts which were removed and not the groups. Some of these groups have been around since 2011.
“However new groups continue to pop up, and some are still active as of the date of publishing,” the researchers said.
Facebook has struggled to prevent users from abusing the platform. Just last year, the social media giant deleted nearly 120 private discussion groups after Brian Krebs reported that these groups were offering services such as carding, wire fraud, tax refund fraud, and distributed denial-of-service attacks. The new groups found by Talos have names “remarkably similar, if not identical,” to the groups Krebs found.
“The underlying computer algorithms that help us connect, suggesting new friends or networks, are not intelligent enough to distinguish benign activities from the unethical or outright illegal,” Talos said.
Bigger Social Media Problem
While Talos focused on Facebook, this problem isn’t limited to just one social media platform. The fact that attackers hide bots and command-and-control servers in Twitter, and malware code can be found on GitHub is pretty well-known. Criminals trafficking in stolen credit card information, email addresses, and login credentials are “hiding in plain sight,” said Zach Allen, director of threat operations in technology at ZeroFOX.
“This is a large and persistent issue and much broader than just Facebook,” Allen said. “Carders are marketing across the full range of ‘social’ platforms.”
These platforms include YouTube, Eventbrite, Medium, Reddit, and Github. Allen found several examples on the ZeroFOX platform—which monitors social media, deep web, and dark web—of sellers offering stolen credit card information. Criminals advertised their carding services and stolen wares on Eventbrite landing pages, comments to YouTube videos, and posts on Medium and Reddit. Lists of stolen credit card information were saved in GitHub repositories. This was based on a quick search—an exhaustive analysis would have uncovered more platforms.
Impact on Enterprises
While some of the services being offered on the Facebook groups appeared to be criminals scamming other scammers, there were plenty of others that were real attacks impacting enterprises.
For example, Talos connected a spam message that showed up in customer inboxes with a specific spammer advertising in one of these Facebook groups. That message came with a PDF file that claimed to be an invoice for an Apple order, but was actually a malicious file containing a link to a phishing website. The phishing page was created using 16Shop, a phishing kit known to target Apple users, and the IP address used to host the page has hosted other suspicious-looking domains, Talos said.
“It's unclear based on these groups how successful or legitimate some of the users are,” Talos said.
While social media platforms should continue to identify and remove malicious groups, security teams and vendors need to “work together to actively share information, take action, and inform customers,” Talos said.
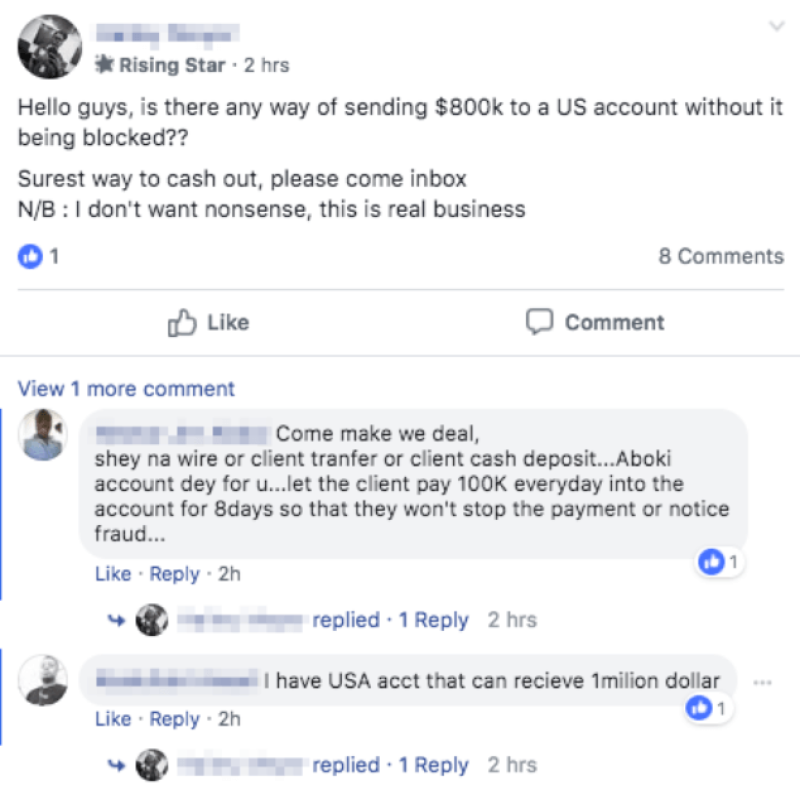
An example of a conversation between a buyer looking for transfer services and a potential seller. Source: Cisco Talos.

