BlueKeep is not the biggest threat currently facing Windows systems—attackers brute-forcing Remote Desktop Protocol connections pose a bigger problem.
A new botnet has brute-forced RDP credentials for more than 1.5 million Windows systems over the past few days, and that number is expected to increase, wrote Morphus Labs chief research officer Renato Marinho. The botnet is scanning the Internet for machines that have RDP exposed and trying out weak or reused passwords to see if it can gain access to the systems.
“After 6 hours, we received 2.1 million IP addresses from the C2 server from which 1,596,571 are unique,” Marinho wrote.
Marinho wasn’t able to specify how large the botnet really is, but said the botnet’s list of “brutable” RDP targets had increased over the last few days as the malware infected more devices and the botnet found new RDP endpoints to target.
When the botnet finds a Windows system with RDP, it attempts to guess the login credentials. If it succeeds in the brute-force attack, the botnet downloads a large zip file containing the bot code. The infected machine scans random IP addresses to find more hosts with exposed RDP servers and to report found endpoints to the command-and-control server.
Once the bot has identified 80 new hosts, it received a username-and-password combination from the c&c server to try against the identified list. The botnet assigned a different username and password combination to each bot, and the bot attempt to log in to each machine just once, making it harder for defenders looking for multiple incorrect login attempts to detect this kind of brute-force attacks.
Remote Desktop Protocol lets administrators and other users access machines without having to be physically at the machine. From a security viewpoint, however, it has never been a good idea for Windows systems to expose RDP directly onto the Internet. Shodan lists about 2.4 million exposed machines, Marinho said, and GoldBrute is compiling its own list as it scans the Internet and identifies vulnerable machines.
The botnet appears to be controlled by a single command-and-control server (which appears to correspond to a location in New Jersey), and bots communicate with the server via AES encrypted WebSocket connections to port 8333, Marinho said. The malware code includes a Java jar file called bitcoin.dll and port 8333 is frequently associated with Bitcoin connections. However, what the attackers behind GoldBrute hope to accomplish is a mystery—the current version of the malware code doesn’t do anything beyond scanning, infecting, and guessing passwords. It could be anything from cryptomining to selling access to other attackers to targeted attacks.
After Microsoft patched a critical remote code execution vulnerability (CVE-2019-0708) affecting older versions of the protocol in May, researchers noticed an uptick in Internet scanning looking for machines vulnerable to “BlueKeep.” Microsoft warned the vulnerability could be exploited by a worm, and there is a concerted effort to update the majority of vulnerable systems before an exploit becomes public. While BlueKeep is serious, GoldBrute highlights the fact that the bulk of scanning activity) for RDP isn’t BlueKeep related. When attackers can just bypass locked screens or guess weak RDP credentials, IT departments need to focus on making sure machines are not unnecessarily exposing RDP on the internet (putting a layer in between, such as a VPN, would help) and that users know how to use RDP properly.
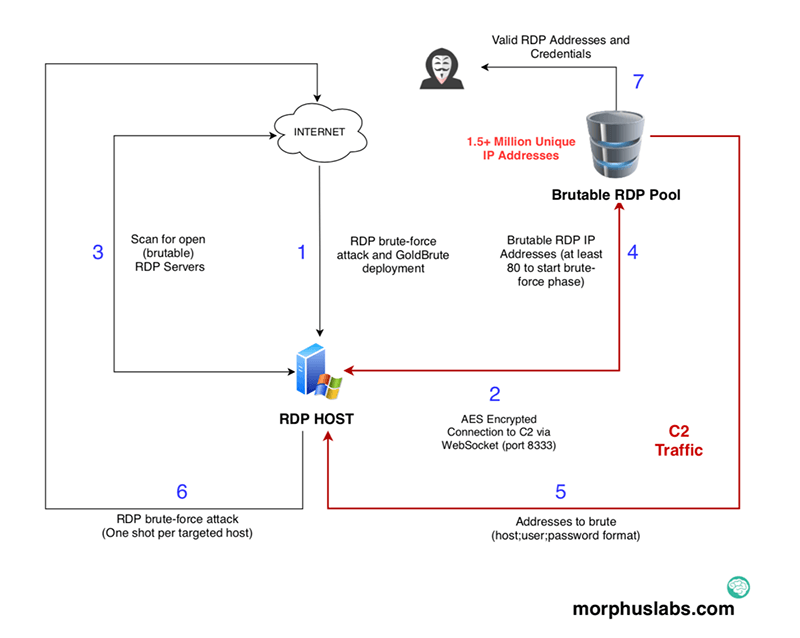
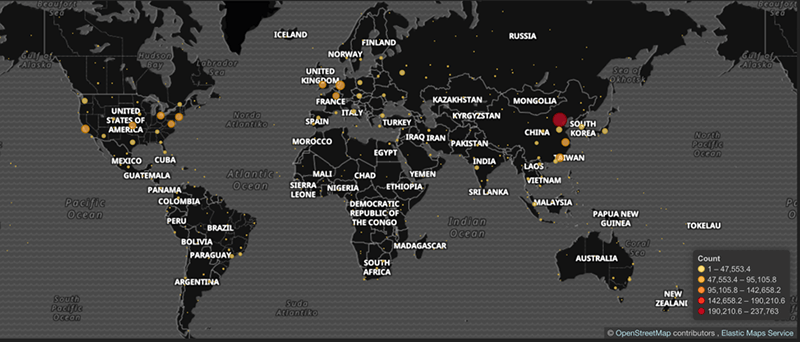
Morphus Labs illustrated how the bot receives instructions from the command-and-control server to scan the internet for vulnerable systems and how it sends information back to the server. Infected machines span the globe, as illustrated by the map.
