Windows systems with Remote Desktop Protocol exposed to the Internet make attractive targets because they provide adversaries with a simple and effective way to get initial entry into the targeted network. There are off-the-shelf tools to scan the Internet for exposed systems, and the password’s strength—uniqueness—will determine how easy it would be for the attackers to guess the login credentials.
Microsoft researchers found that out of about 45,000 Windows workstations that had both RDP public IP connections and at least one network failed sign-in attempt, on average, several hundred machines per day had high probability of undergoing one or more RDP brute-force attack attempts.
“Across all enterprises analyzed over several months, on average about one machine was detected with high probability of being compromised resulting from an RDP brute force attack every three to four days," the Microsoft research team said.
RDP as an Open Door
A built-in Windows component, Remote Desktop Protocol lets users log into a remote computer via a desktop-like interface using the computer’s IP address, over port 3389. RDP is particularly helpful for system administrators managing servers and workstations in remote locations and is also used by employees when they are away from their desks. Attackers don’t have to bother with sophisticated malware or advanced techniques if the machine with RDP isn’t protected behind virtual private networks or other security layers. All they need is that machine’s IP address.
In some cases, RDP may be set up without a password. Attackers can also make their way into the targeted machine and the network if the password is weak or easily-guessable, and multi-factor authentication is not enabled.
“On average about one machine was detected with high probability of being compromised resulting from an RDP brute force attack every three to four days,” Microsoft said.
In a brute-force attack, attackers use automated tools to cycle through different username/password combinations to try to guess the login credentials. Adversaries may compile frequently used usernames and passwords (such as admin/admin), valid credentials harvested from password dumps after breaches at various online services, or potential combinations stolen through other methods.
Identifying Attacks
As part of the analysis, Microsoft researchers collected both successful and failed login-related events for RDP (identifiers 4265 and 4264 in Windows events logs) and the usernames and IP addresses associated with those events. Many failed sign-ins (events with the ID 4625) occurring over very short time frequencies—in minutes or seconds—from a single IP address would suggest a brute-force attack in progress. However, the researchers found that attackers were spreading out the brute-force attempts over a longer period of time—a few combinations per hour rather than hundreds or thousands at a time—to avoid getting their IP addresses blocked.
Brute-force attacks against RDP typically lasted between two and three days, Microsoft researchers found. The majority, or 90 percent, of the attacks last for a week or less. Less than 5 percent last for two weeks or more.
A relatively large number of 4625-events appearing suddenly in the logs don’t automatically mean a brute-force attack is underway, as it could mean that the user is using a script with an expired password, for example. Other factors have to be considered, such as seeing failed login attempts for many unknown usernames, across multiple RDP connections, and originating from unknown IP addresses, Microsoft said.
“Knowing if the external IP has a high reputation of abuse, as can be looked up on sites like abuseipdb.com, can directly confirm if an IP is a part of an active brute force,” Microsoft said.
RDP Events for Defense
Microsoft suggested system administrators monitor for multiple signals to detect inbound brute-force traffic against RDP. Signals include time and day of week of failed attempts, timestamp of a successful login after multiple attempts, count of usernames that failed to sign in, count of attempts from external IP addresses, and counts of other machines having inbound connection attempts coming from the same IP addresses. Microsoft said it was possible to develop a time series anomaly detection model with these signals to accurately identify RDP brute force attacks.
"A key takeaway from our analysis is that successful brute force attempts are not uncommon; therefore, it's critical to monitor at least the suspicious connections and unusual failed sign-ins that result in authenticated sign-in events,” Microsoft said.
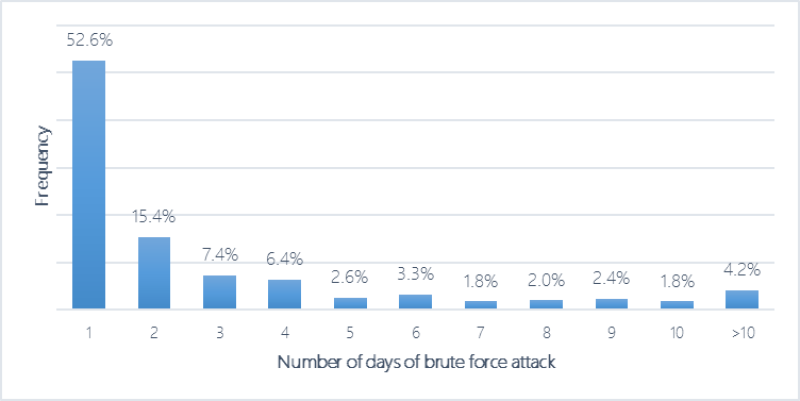
Empirical distribution in number of days per machine where we observed 1 or more brute force attacks. Source: Microsoft Defender ATP Research Team, "Data science for cybersecurity: A probabilistic time series model for detecting RDP inbound brute force attacks" (Dec 2019)
