Don’t get hooked! 5 essential security tips to combat holiday phishing
The holiday season is in full swing, and that means cybercriminals are busy building and launching attacks to steal user credentials. Their ultimate goal? To use those valid credentials to gain network access and steal data, employee and customer information, and other valuable resources. They may even use compromised privileged credentials to launch a ransomware attack and hold your organization hostage for a hefty ransom.
Phishing is still one of the most common attack vectors, and the holidays provide an especially appealing time to launch an attack that’s been supercharged by modern natural language processing models and novel QR codes. While we tend to associate phishing emails more with our personal accounts, attacks targeting our work identities whether through socially engineered phishing, brute force, or another form, are very common.
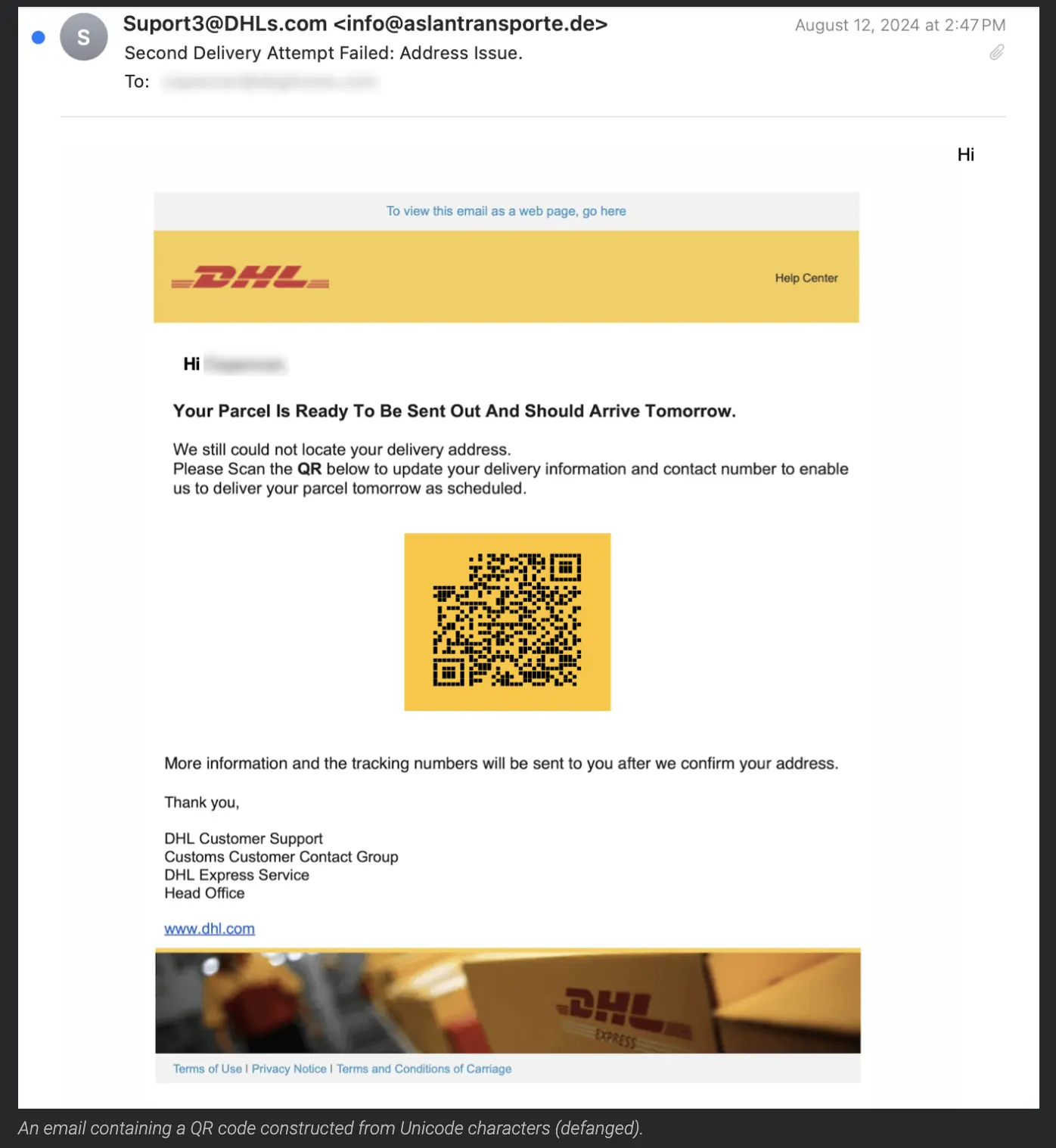
For example, this looks legitimate. What if it’s that nice swag box everyone on the team has been getting for the holidays? According to research by Cisco Talos, malicious QR codes are bypassing spam filters in increasingly clever ways. Scanning an unknown QR code is the modern equivalent of clicking on a suspicious link.
No industry is spared this phishing season, though some are targeted more often than others. According to the Cisco Talos Incident Response Team, organizations in the education, manufacturing and financial services verticals were the most affected by identity-based attacks during the third quarter of 2024. Combined, these sectors accounted for more than 30 percent of account compromises.
What you may not know is that once a user’s identity is stolen, bad actors don’t always use the credentials straight away. They’ll wait until a time when your IT and SOC (security operations center) teams are reduced such as over a holiday break or weekend.
In its 2024 Ransomware Holiday Risk Report, Semperis found that 86% of study participants who experienced a ransomware attack were targeted on a weekend or holiday. Why? Staffing during those times is lighter which means identifying and responding to threats will be slower.
In that same report, 85% of respondents stated they reduce their SOC staffing by as much as 50% on holidays and weekends. It’s easy to see why cybercriminals view this as a good time to strike. After all, why attack when it’s convenient for your victim?
Beyond staying extra vigilant over the holiday season and weekends, how else can you protect against attacks targeting your users’ identities? Here are five actions you can take with Duo to stop threats, with direct links to documentation to get started:
Deploy Phishing-resistant MFA — According to the CISA advisory on implementing phishing-resistant MFA capabilities, SMS and voice-based MFA are vulnerable to phishing, SS7 and SIM swap attacks.
Duo supports the only widely available phishing-resistant FIDO/WebAuthn authentication through Duo Passwordless, encompassing “roaming” physical token authenticators and “platform” authenticators embedded into laptops and smartphones. But we know that going completely passwordless is a journey. To level up mobile app MFA, turning on Verified Duo Push number matching is an excellent way to protect against MFA fatigue and push bombing attacks.
Bonus Tip! Since MFA/Push notifications are prompted after users enter their credentials, system administrators are advised to investigate fraudulent pushes as well as issue new user credentials. In Duo, see how to easily generate a Denied Authentications report through the Duo Admin Panel.
Reduce Your Reliance on Passwords — Fewer, stronger passwords can reduce the likelihood of re-used credentials or your users adding an exclamation point to the end of their password leaked one month ago.
Duo’s single sign-on solution (SSO), available in every edition, secures all your organization’s applications and offers inline user enrollment, self-service device management, and support for a variety of authentication methods. Combining passwordless and SSO decreases end-user login fatigue while still maintaining powerful security and incorporating frequent device health checks. With the newly announced Duo Passport, experience just one login and MFA prompt from the beginning of your day to the end.
Adapt and Respond — With Risk-Based Authentication, you can dynamically respond to changes in risk level by requiring a more secure authentication factor such as a Verified Duo Push or biometrics before granting access.
Verify Device Trust — Control access to resources on your network by allowing only devices that are part of your inventory of trusted devices — whether managed or unmanaged and company-issued or personal— and that are up to date and have a healthy security posture.
Gain Deeper Visibility — A key component of Duo’s Continuous Identity Security solution, Cisco Identity Intelligence provides deep visibility into identity-based attacks while also helping reduce gaps in your security coverage before, during, and after login.
This holiday season, spend less time on phishing training and more time perfecting your secret eggnog recipe. Try Duo at no cost with our free trial, or learn more about how to turn on Duo’s advanced identity security features with our on-demand value-maximizing webinar More Bang for Your Buck: Duo Advanced.


