End-to-end phishing resistance: Stretch goal or short-term reality?
Basics is no longer cutting it. Free is not stacking up. Even with multi-factor authentication (MFA) patrolling security’s new identity-based perimeter, phishing attacks remain one of threat actors’ favorite tools and demand stronger protection in identity and access management (IAM). MFA may make it harder to simply log into enterprise environments using lost, leaked, bought, weak, or stolen user credentials, but it’s clearly not impossible either.
That’s because user training and even basic MFA are not enough to ensure phishing resistance against modern campaigns that use new techniques to subvert or sidestep authentication:
AI-led campaigns use large language model (LLM) tools like ChatGPT to craft convincing emails that look and sound like trusted entities
Adversary-in-the-Middle (AiTM) attacks bait users into clicking fraudulent links that take them to proxy servers controlled by the bad actors
New multi-stage MFA fatigue campaigns are designed to capitalize on repeated user authentications to bypass and exploit weaker forms of MFA
Gaps in protections reveal themselves as attackers target supply chain and third-party access permissions, remote desktop protocol (RDP), or legacy applications
And that’s not all. Modern phishing attacks like the ones listed above now stretch beyond authentication, threatening session cookies and bypassing traditional defenses, making comprehensive phishing resistance essential—even for trained help desk pros.
Download the free guide
If all of that makes achieving end-to-end phishing resistance sound like a pipe dream, identity security leaders can take heart. In a new guide from Cisco Duo, you’ll learn what tools and strategies you can use to push your organization toward modern phishing resistance.
Ready to strengthen your organization's phishing resistance?
Download the free Guide to Building End-to-End Phishing Resistance now.
Let’s talk about what makes defending against modern phishing attacks so challenging.
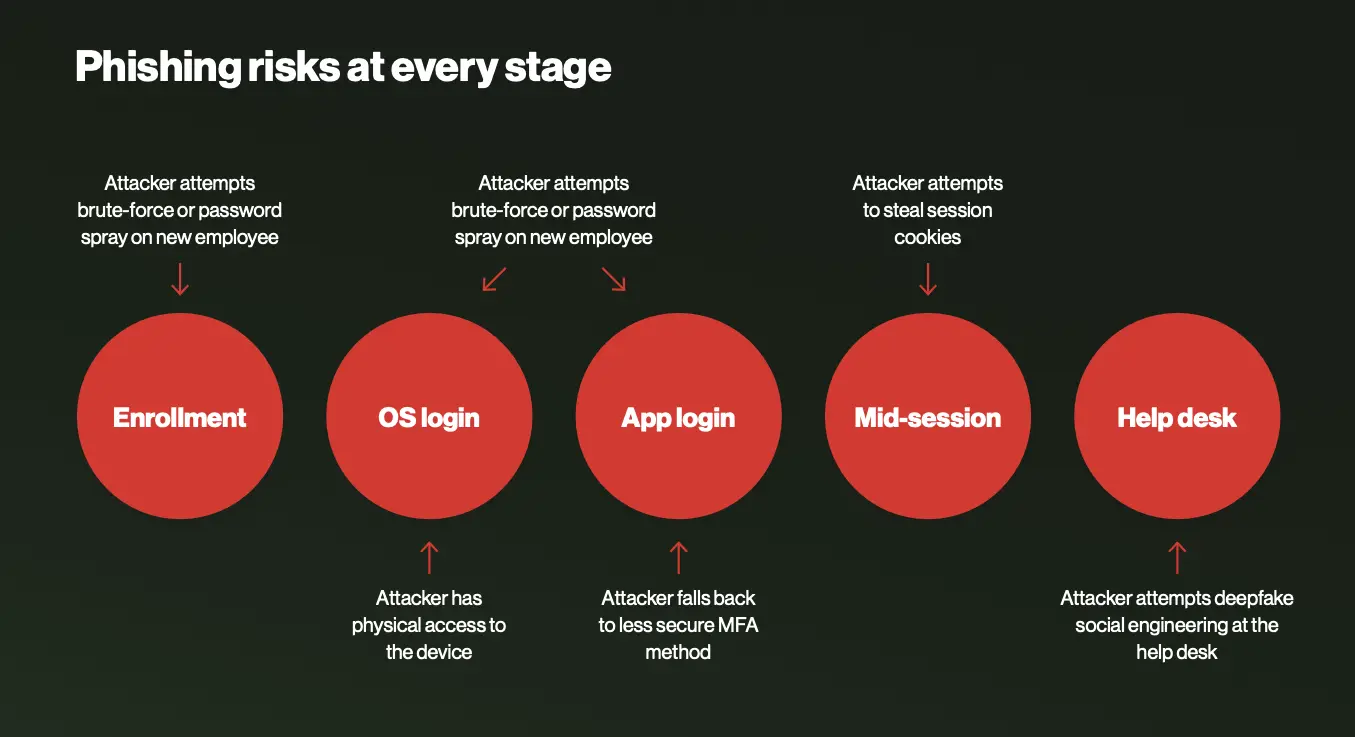
Why end-to-end phishing resistance matters across the identity lifecycle
There’s a lot more to consider when it comes to phish-proofing your organization, and new and existing regulations are not shy about pushing standards higher. To mitigate the risk from modern phishing attacks, regulators, zero trust guidelines, and cyber insurance companies now emphasize phishing-resistant MFA and robust identity security. Forward-looking regulations like Memorandum 22-09, from the Office of Management & Budget (OMB) in the US and the NIS2 directive in Europe now specifically prescribe “phishing-resistant MFA” as a best-practice strategy for safeguarding identity.
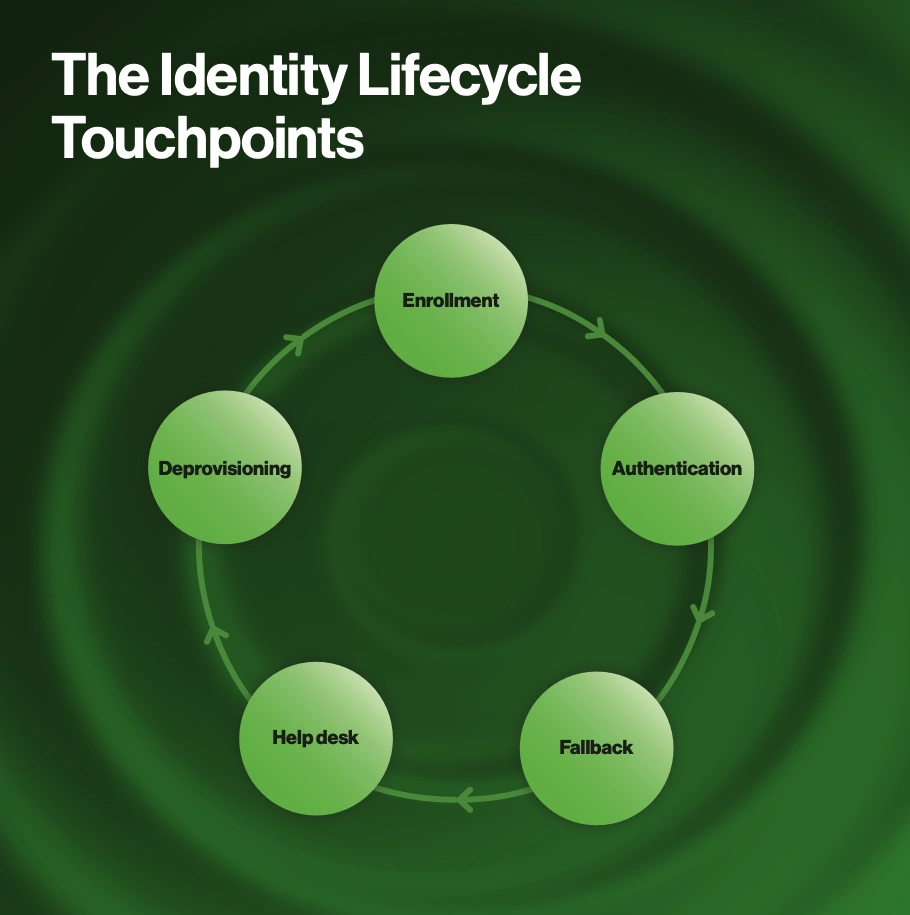
These evolving mandates concentrate on the strength of the factor, but IAM leaders already know their defenses must extend beyond the conventional app login. With more threat actors expecting to run into traditional SMS, and even push-based MFA, phishing-prevention strategies must illuminate exploitable blind spots throughout the entire identity lifecycle. That means starting at enrollment—where new, enthusiastic employees are susceptible to false HR emails—through critical points like help desk interactions, remote connections, and deprovisioning.
With headlines of AI-enabled deepfake and vishing (voice phishing), social engineering tactics grow trickier to detect. In many situations, organizations may revert to using passwords or basic security questions as a fallback option for verifying identity. Today’s identity security practices must rise to meet new challenges. For example, using an integrated identity verification service creates a more secure fallback option that equips help desk technicians to establish trust on the fly.
Source: End-to-End Phishing Resistance
"Who wants cookies?" Defending against mid-session token stealing
Many organizations use cookies to extend trust throughout a user’s entire working session. But if intruders can find a way to log in using active credentials, they can sometimes steal those “remember me” cookies to hijack active sessions and authenticate into other applications. Or, change or escalate privileges without triggering detection.
Attackers have become adept at stealing cookies through malicious JavaScript, infostealers like Redline and Emotet, or adversary-in-the-middle attacks. Once they have the session tokens, they can take over digital identities, bypassing passwords, MFA, and other security controls. Typical precautions like making sessions shorter and asking users to reauthenticate more often only add to productivity complaints and user frustration.
Security often comes at the cost of increased friction—especially challenging when end-users must interact with it several times a day for each of their applications. What if we removed the very thing that makes a session stealable? Duo’s patent-pending authentication without cookies paves the path for a dramatic reduction in user friction, delivers platform-agnostic protection (Windows and macOS) with no vendor lock-in or ecosystem limitations, and provides built-in hardware-backed phishing resistance.
Show how "stronger" can also mean "simpler"
Security only works if people use it, which they won’t do if MFA gets too complicated. Asking users to keep track of multiple passwords, rotations, authenticator apps, and physical tokens is a recipe for disaster and that new digital malady, MFA fatigue.
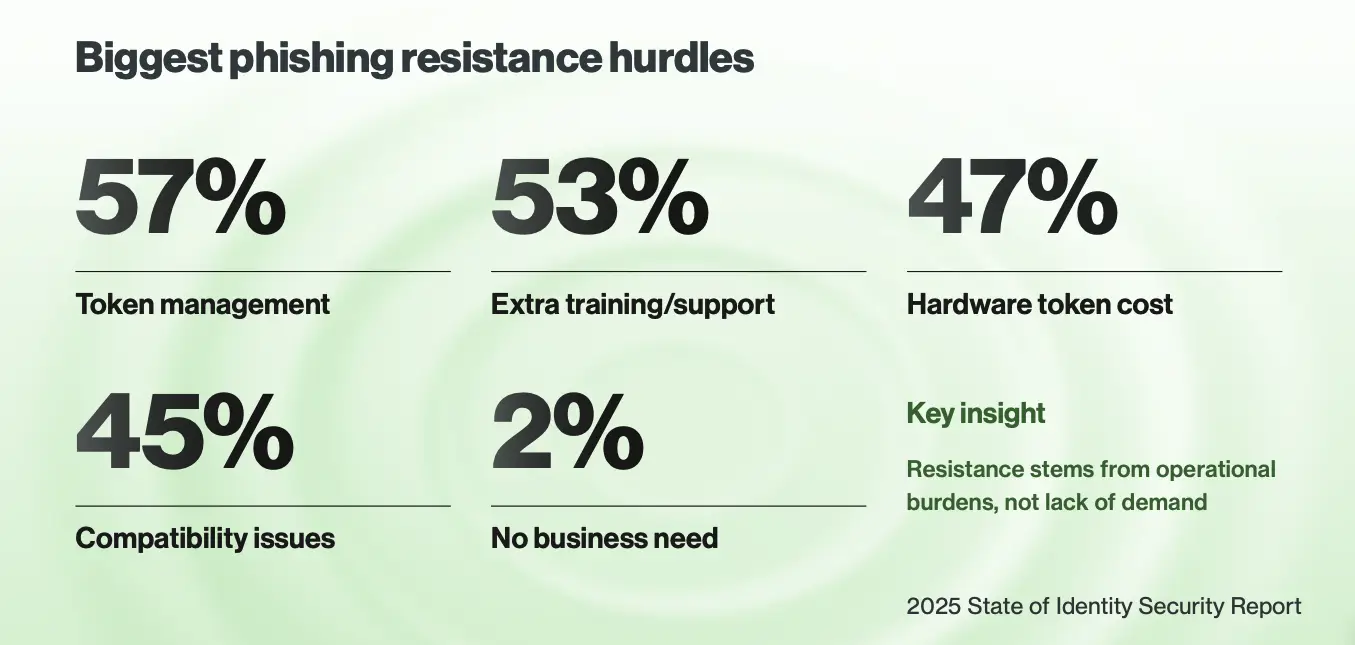
Overly complex controls also burden IT. According to the Cisco Duo 2025 State of Identity Security report, nearly 60% of security leaders cited token management as the biggest hurdle to phishing resistance. Most security and IAM leaders would like to make their MFA more phishing resistant but believe it might not warrant the time and effort.
Rolling out new methods of authentication (like biometrics and smart cards), buying and shipping hardware tokens to remote users, and fielding support calls all consume endless IT cycles that offset the value of IAM investments.
IAM strategies must overcome leaders’ top obstacles to deploying phishing-resistant MFA:
Cost and ongoing management of hardware tokens
Training and support
System compatibility
Resistance stems from operational burdens, not lack of demand. At the core of improving phishing resistance is making stronger security feasible to deploy for every user. After all, “if a security control isn’t deployable; it’s not usable. And if it’s not usable, it’s not protecting anyone.” For Duo, the breakthrough was adding the same proximity-based verification that hardware tokens provide on top of our familiar interfaces. No shipping hassle, no complex configurations, no added cost.
The flexibility to go phishing resistant with passwordless
It’s not uncommon to hear of passwordless authentication as an option to go phishing resistant and improve user experience at the same time. The pitch to go password-free is typically accompanied by plenty of caveats and challenges, yet many organizations committed to strengthening their identity security are already moving forward—streamlining authentications with single sign-on, enforcing device hygiene standards, and leveraging risk-based authentication (RBA) to cut down on repeated logins.
How passwordless authentication increases phishing resistance
With the past several years of innovation, regulators, cyber insurance companies, partners, and prospective customers are also headed towards passwordless, and for good reason: without credentials there’s nothing to phish. Even AI can’t steal passwords that no longer exist.
Is “complete passwordless” just another pipe dream? After all, complexities arise in the form of legacy applications, working with existing infrastructures, and initial directory enrollment. The new guide details how you can make the elimination of passwords—typically considered a ‘stretch goal’—a near-term reality (versus a “roadmap item”) at every stage of the identity lifecycle: enrollment, application and operating system logins, help desk support, and secure fallback.
5 steps to achieve end-to-end phishing resistance
Securely verify and onboard new users
Strengthen user authentication at every access point
Prevent session stealing even after users log in with cookie-free protections
Secure the "edge" cases like fallback, Help Desk calls, and deprovisioning
Move towards eliminating passwords completely
Stronger security is achieved in phases. Implementing end-to-end phishing resistance with identity verification, session theft protection, and phishing-resistant MFA ensures your organization is protected now and in the future.
Duo makes it easy to get started on the journey to complete end-to-end phishing without the high price tags and hidden costs. Download the guide now to learn how you can build seamless, reliable identity security and deliver a world-class end-user experience at the same time.
Get the free guide to achieving end-to-end phishing resistance today!