Understanding the new PCI DSS 4.0 requirements
The Payment Card Industry Data Security Standard (PCI DSS) recently updated their standards from PCI DSS 3.2.1 to PCI DSS 4.0. It is the first major revision in some time. There is more flexibility built into 4.0 for companies to implement security that works with their security framework. There were 60 changes made, with new rules around multi-factor authentication (MFA) being one of the most significant.
The changes to MFA now more closely align with NIST SP 800-63B Digital Identity Guidelines. PCI DSS 4.0 focuses on developing stronger authentication requirements around NIST Zero Trust Architecture guidelines. PCI DSS 4.0 now mandates that MFA must be used for all accounts that have access to the cardholder data, not just administrators accessing the cardholder data environment (CDE).
What Is PCI DSS?
The Payment Card Industry Security Standards Council (PCI SSC) regulates the PCI DSS standards and is composed of the five major credit card companies: Mastercard, Visa, American Express, Discover, and JBC. The Payment Card Industry Data Security Standard is a set of security standards designed to ensure that ALL companies that accept, process, store or transmit credit card information maintain a secure environment. These standards are meant to protect a consumer transactions by credit, debit or cash cards from misuse of their personally identifiable Information (PII) with safeguards that make stealing identities difficult.
How does MFA fit into the updated PCI DSS 4.0 standards?
There are three accepted multi-authentication methods including:
Something you know (like a password)
Something you have (like a mobile phone)
Something you are (like a biometric)
A minimum of two of the three factors is required for authentication.
Previously, if you worked from home and connected to the CDE through a VPN that required MFA that one challenge was enough, now MFA is required for all access into the CDE as outlined in 8.4.2. MFA will be required every time there is an attempt to access the CDE.
If an individual first connects to the entity’s network via remote access, and then later initiates a connection into the CDE from within the network, per this requirement the individual would authenticate using MFA twice, once when connecting via remote access to the entity’s network and once when connecting via non-console administrative access from the entity’s network into the CDE. (PCI DSS 4.0)
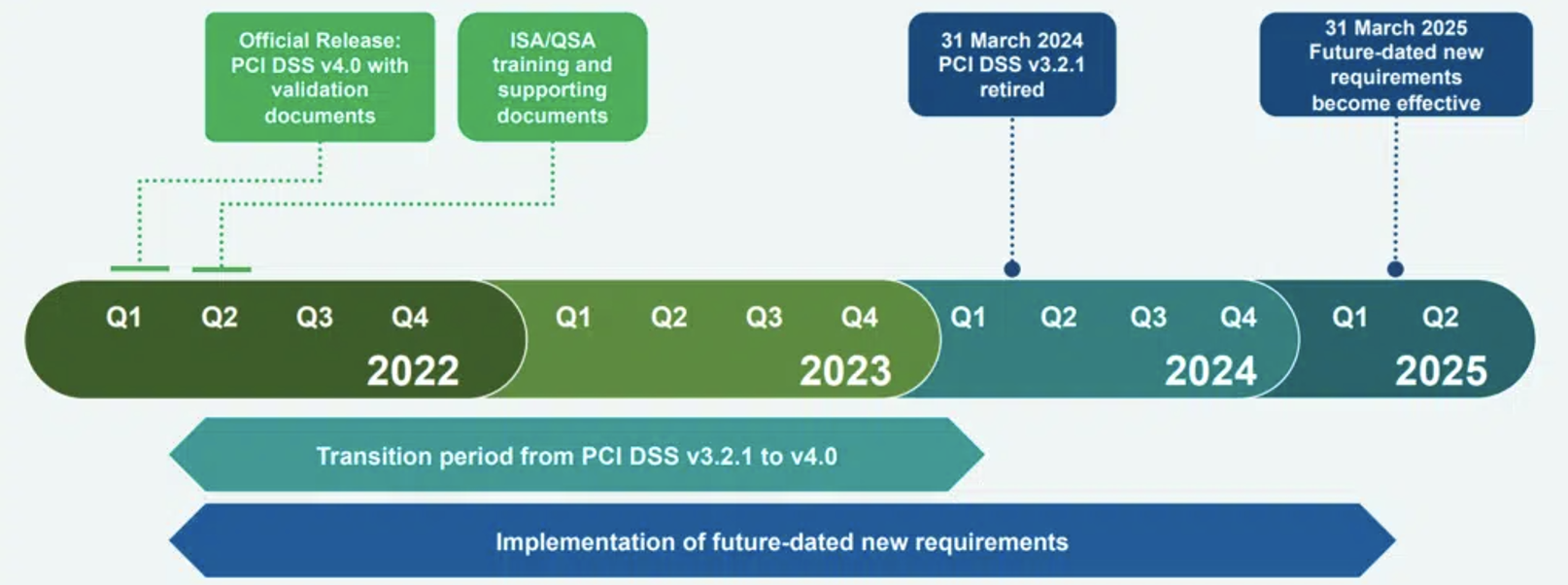
The new requirement is best practice until March 31, 2025, after which it will be required and must be fully considered during a PCI DSS assessment. While the requirement is about three years out, the industry as a whole is quickly moving towards Zero Trust. It is worth looking at an improved solution prior to an incident or a compliance requirement.
8.4.2 indicates MFA will need to be in place for all kinds of system components including:
Endpoints
Servers
Cloud environments
Hosted systems
On-prem applications
Network security devices
Workstations
In 8.4.1 Administrative access to the CDE cannot be obtained by the use of a single authentication factor and if a user has been idle for more than 15 minutes the user is required to re-authenticate and to re-activate the terminal or session as outlined in 8.2.8.
DarkReading reports PCI DSS 4.0 considers:
Multi-factor authentication (MFA) usage for all accounts that have access to the cardholder data, not just administrators accessing the cardholder data environment.
Passwords for accounts used by applications and systems must be changed at least every 12 months and upon suspicion of compromise.
Use of strong passwords for accounts used by applications and systems, which must contain at least 15 characters, including numeric and alphabetic characters. PCI DSS requires that the prospective passwords be compared against the list of known bad passwords.
Access privileges must be reviewed at least once every six months.
Vendor or third-party accounts may be enabled only as needed and monitored when in use.
Compromised passwords are still the top threat from bad actors and MFA is considered the best tool for preventing authorized attacks. Soon every entry point will require MFA protection. MFA is the first step toward a zero trust framework. Companies will have until 2025 to implement the changes.
Want to learn more about Duo's MFA and trusted access platform?
Download our guide on retail cybersecurity today!

