NIST AAL2/3 compliance with Duo Mobile Proximity Verification
Multi-factor authentication (MFA) is a baseline security practice, but not all authentication methods are phishing resistant. This leaves organizations exposed to more advanced identity-based attacks when weaker authentication methods are configured. Across various industries and organizations of all sizes, we continue to observe identity attacks using adversary-in-the-middle (AitM), push bombing, and replay attacks to bypass traditional MFA, exploiting users’ trust to gain access. As a result, standards like NIST SP 800-63B, federal guidance, and cyber insurance requirements are starting to encourage adoption of phishing-resistant authentication, especially for critical applications and users.
To help customers navigate these expectations with confidence, we’re excited to share that Kantara Initiative, a global non-profit organization that audits and certifies identity solutions against NIST standards, has completed an independent assessment of Duo Mobile Proximity Verification. Their findings validate that the feature meets NIST AAL2 requirements, and, with additional configurations, is also able to achieve AAL3 protections.
Meeting NIST SP 800-63B AAL2/3 with Duo Mobile Proximity Verification
Duo Mobile Proximity Verification represents a significant step forward: strong phishing-resistant authentication with the Duo Mobile app that users love.
For a deeper dive with NIST mappings and test results, get the full Kantara Proximity Verification Assessment Report.
What are NIST AALs and why does it matter?
NIST’s Authenticator Assurance Levels (AALs), defined in SP 800-63B, outline the required strength of authentication for systems with different risk profiles. AAL2 requires strong MFA resistance to common phishing and replay attacks, while AAL3 represents the highest assurance, requiring hardware-backed, phishing-resistant authentication. These levels are widely referenced by government agencies, regulated industries, and organizations pursuing zero trust or cyber insurance requirements. For customers, aligning to NIST AALs provides a clear, measurable way to demonstrate that your authentication methods can withstand modern threats.
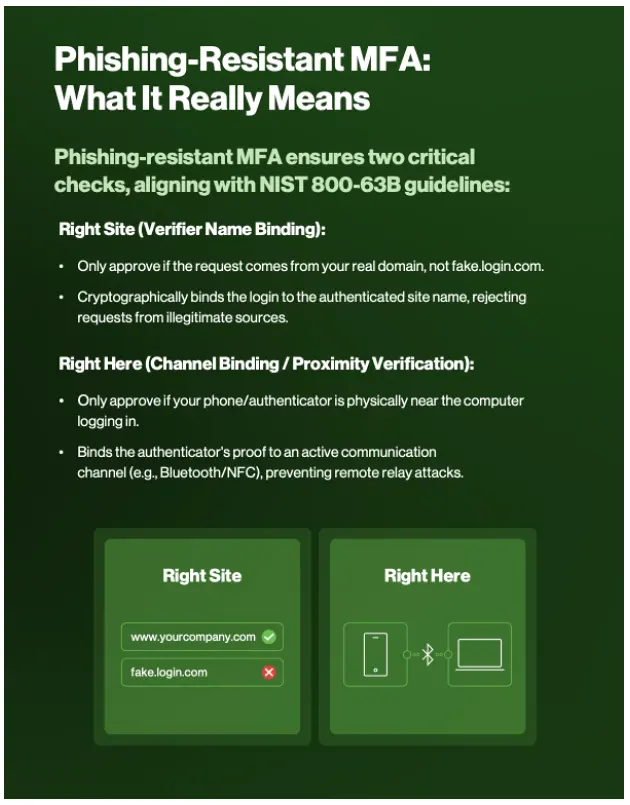
Two components of phishing-resistant MFA: Right Site and Right Here. Get the full infographic.
What Kantara Initiative validated
Kantara Initiative is a global non-profit that builds trust in digital services by providing certification against the world’s most rigorous standards for privacy and data security. A pioneer since 2009, Kantara is recognized by the U.S. government for certifying identity providers against NIST 800-63 standards, a requirement for federal agencies.
Kantara Initiative evaluated Duo Mobile Proximity Verification against the NIST 800-63B AAL2 and AAL3 criteria, reviewing authenticator strength, cryptographic protections, phishing resistance, and physical presence verification.
Key capabilities confirmed by Kantara Initiative
Phishing Resistance: BLE proximity checks prevent remote push phishing.
Verifier Impersonation Resistance: Duo Desktop ensures authentication requests originate from trusted domains, preventing AitM-style attacks.
Replay and Verifier Compromise Resistance: Private keys remain device-bound, and cryptographic signatures prevent tampering or reuse.
Authentication Intent: Duo Mobile requires explicit user approval, with optional biometric confirmation.
Kantara Initiative attests the feature aligns with NIST SP800-63B requirements for AAL2, and partially for AAL3.
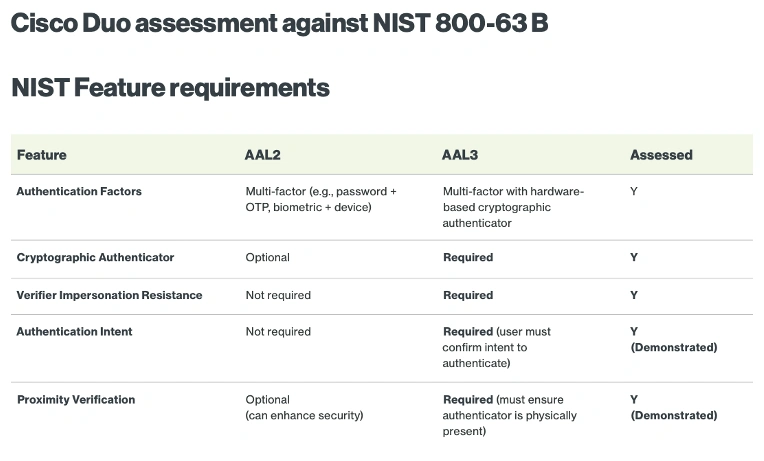
NIST 800-63B AAL2/3 requirements assessed by Kantara Initiative summarized. Full list of AAL2 ad AAL3 requirements and mappings available in the Report.
How does Duo Mobile Proximity Verification work?
Historically, achieving phishing resistance has been a story of compromise that trades user experience for security. It often meant managing the logistics of security keys and navigating complex configurations, creating friction for users and a deployment headache for IT teams.
Duo Mobile Proximity Verification is designed to prevent bad actors from bypassing MFA using Duo Mobile without compromising end-user productivity. By leveraging Bluetooth Low Energy (BLE) technology, this feature ensures a seamless and secure authentication using both Duo Mobile and Duo Desktop to mitigate the risk of phishing attacks and simplifies MFA experience for end users. Duo Mobile Proximity Verification defends against two categories of attacks:
Remote phishing resistance
Using BLE for proximity check ensures the access devices (with Duo Desktop installed) and the MFA device (with Duo Mobile installed) are close to each other, therefore greatly decreasing the likelihood of phishing attacks like social engineering targeting push-based authentication. Attackers with stolen primary credentials will not be able to trick users into approving the authentication request when they are accessing from a computer in a different location from end users.
Verifier impersonation resistance
Users can also click on a malicious link to an attacker-controlled website that mimics a company’s legitimate login portal and give up first and second factors unknowingly. Proximity Verification prevents this style of attack because every request begins by routing through Duo Desktop where we check the origin of the website that the request came from. If the request is not coming from a valid domain, we deny the authentication request. This is equivalent to verifier name binding in the FIDO2 specification and provides the same type of protection against adversary-in-the-middle attacks.
A scalable path to high-assurance authentication
Duo helps accelerate any organization’s zero trust journey with modern, manageable phishing resistance. In conversations with customers, we’ve picked up on a few tips for a scalable deployment.
Start small with pilot group testing
Deploying phishing-resistant authentication doesn’t need to be complex. We recommend starting with a custom policy that enables Proximity Verification and requires Duo Desktop, applying it first to a small pilot group such as IT. Duo Mobile and Duo Desktop will take users through the authentication flow with intuitive guidance.
Test BLE with Verified Duo Push with Bluetooth Autofill
If you're uncertain about Bluetooth availability on users’ endpoints, you can begin with Verified Duo Push with Bluetooth Autofill, which uses the same technology behind the scenes and allows users to enter a verification code when Bluetooth isn’t available, so users will not be blocked. The feature is a great starting point to move your users to a more secure authentication, and you can migrate to Proximity Verification and be truly phishing resistant when you are confident with the change.
Review authentication logs often
During the pilot, regularly review authentication logs in the Duo Admin Panel to monitor authentication results and error states. Once you are confident with the performance, you can expand the policy to high-risk user groups and/or high-risk applications first and ultimately the entire organization, achieving phishing-resistant MFA at scale without distributing new hardware.
Download the free Kantara Institute Report
Duo helps organizations secure every login, protect against the most advanced threats, and build a foundation of trust for your entire identity ecosystem.
See how authentication factors map to NIST Authenticator Assurance Levels and learn how Duo Mobile Proximity Verification can help demonstrate compliance with NIST AALs in the free Kantara Institute Cisco Duo Proximity Verification Summary Report!
Explore seamless user experience with the Proximity Verification Product Tour or get started with Proximity Verification today with our comprehensive policy documentation.

