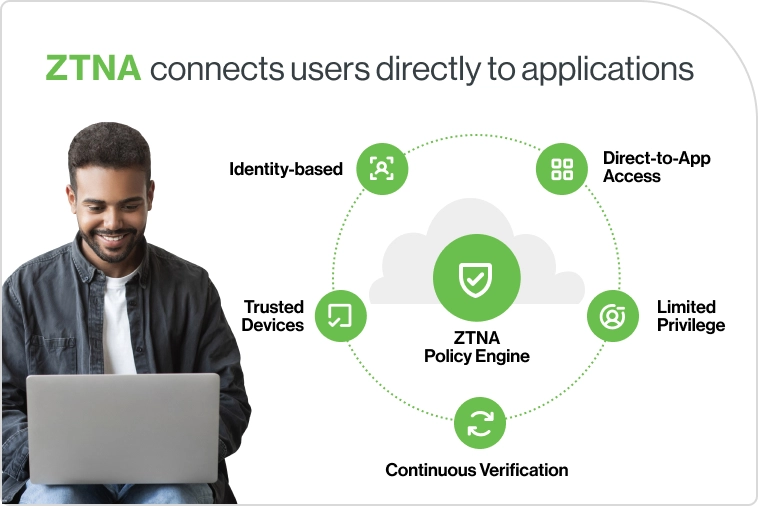
5 tips for evaluating ZTNA VPN solutions
Choosing the right solution means balancing your organization’s current needs with its long-term security strategy. Here’s what to look for when comparing a ZTNA framework vs. VPN tools:
1. Integration with existing IAM
Your ZTNA framework will work best when it integrates with your existing identity providers, ensuring consistent authentication across all applications.
Duo Security’s solutions are designed to plug into leading IAM platforms without heavy configuration, reducing deployment time and complexity.
Always confirm compatibility with your current and planned identity sources.
2. MFA and phishing-resistant authentication
Strong authentication is at the heart of any zero trust model, but not all MFA is created equal. Many VPNs support MFA, yet it’s typically a single checkpoint at login, leaving sessions vulnerable if credentials are stolen or compromised.
Duo goes further. With phishing-resistant MFA methods like FIDO2 security keys and platform biometrics, Duo enforces stronger identity assurance and applies MFA adaptively throughout a session when risk signals change. This aligns with ZTNA principles, ensuring users and devices are continuously verified, not just once when logging in.
By contrast, competitors that rely on traditional one-time passcodes can’t deliver the same level of resilience against phishing or lateral movement, leaving gaps in both VPN and ZTNA framework deployments.
3. Visibility and reporting capabilities
ZTNA isn’t supposed to only grant or deny access; it should give IT teams detailed insight into every interaction, including:
Who is accessing (the specific user identity)
What they’re accessing (applications, files, or systems)
When they connect (timestamps, duration, unusual login times)
Where they’re coming from (device type, location, network)
This level of detail makes it easier to spot suspicious behavior quickly and generate the compliance reports SMBs often need.
Imagine a small accounting firm with a mix of remote employees and contractors. With VPN access, IT might only see that “a connection” was established. With a ZTNA approach, they can confirm that Jane, using her company laptop, accessed the payroll app from Minneapolis at 10 a.m. If, later that afternoon, someone using her credentials tries to log in from an unrecognized device in another country, the system can flag or block the attempt immediately.
4. Device posture and risk assessments
The ZTNA framework is designed to continuously check the device's health before and during access. That means examining factors such as whether the operating system is up to date, whether security patches are applied, and whether endpoint protection is running. If a device doesn’t meet these requirements, access can be blocked or limited until it’s remediated.
VPNs, by contrast, usually only verify whether the VPN client is installed and configured correctly when the connection is first set up. They don’t reassess device health after that, which leaves room for risk if the device becomes outdated or compromised.
For remote and hybrid teams, especially those using personal devices for work, these posture checks give IT a way to enforce baseline security without rolling out full device management (MDM). That’s a major advantage for SMBs that want to protect business data without intruding on employees’ personal devices. Still, organizations handling highly sensitive or regulated data may need to combine ZTNA checks with stricter device management to close any remaining gaps.
5. Scalability and licensing
A ZTNA approach is designed for cloud-scale deployment, enabling organizations to expand capacity quickly without investing in more VPN concentrators or network hardware. Licensing models often align with user counts rather than network capacity, simplifying cost planning.
Over time, ZTNA can reduce the operational overhead and total cost of ownership (TCO) compared to scaling VPN infrastructure.