Defending against identity-based threats using the Shared Signals Framework
For the past few years, we’ve observed an increase in identity-based attacks across all sectors. To illustrate the point, last quarter our own Cisco Talos team saw “a surge in password-spraying attacks.” In one of their documented cases, an organization reported that 13 million authentication attempts were made in 24 hours against known accounts. In the case of password spray, looking for startling increase in authentication traffic can be vital.
However, other identity-based techniques are difficult to detect because uncovering one stolen credential in a sea of valid sessions is like finding a needle in a haystack. IT environments are increasingly complex, and applications, security products, and identity providers don’t speak the same language, leading to more silos, even when everything was designed in the name of simplicity.
The Shared Signals Framework is a standard from the Open ID Foundation that seeks to solve this problem. The framework provides a secure way for entities involved in identity management to exchange signals that help ensure the integrity, trustworthiness, and security of user activity, even post-login. Service providers can broadcast any anomalies that could indicate session hijacking, account takeover, or fraud, so that other providers can quickly take action to verify that the user account is safe.
Cisco has played a key role in the development of the Shared Signals Framework, and we plan to continue our investment in the evolution of the standard. In 2021, we launched SharedSignals.guide to help developers learn about the framework and how to adopt it. One of our principal engineers serves as a co-chair of the Open ID Foundation’s Shared Signals Working Group, where he helps with the development of the standard. Most recently, in December of 2024, we attended the Gartner IAM conference interoperability event, where we demonstrated the power of Shared Signals in detecting and preventing session theft, a top security concern for our customers.
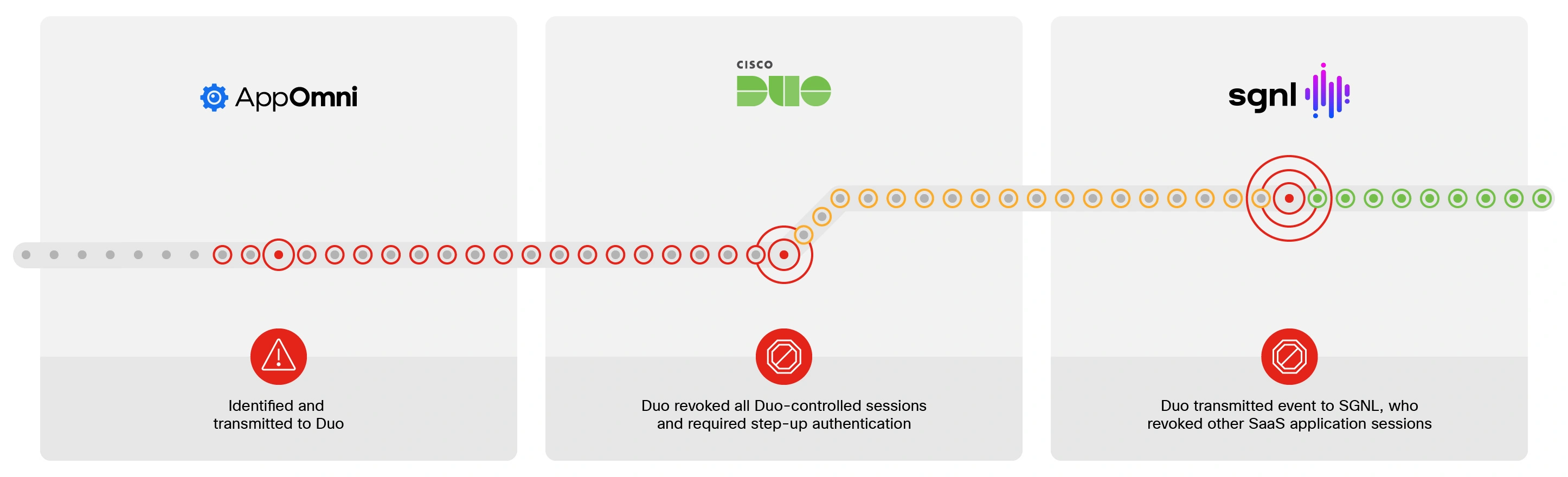
We partnered with AppOmni and SGNL to showcase a powerful story in which AppOmni identified a risky and compromised session and transmitted that event to Duo. Duo then revoked the Duo session and required the user to authenticate with a more secure factor via step-up authentication. In the final part of the demo, Duo transmitted the event to SGNL, who revoked the user’s SaaS application sessions. This helps security teams reduce the potential for lateral movement once a user’s credentials have been compromised, and importantly, significantly reduces the time to resolution. Attackers have easy access to toolkits that allow them to exfiltrate large amounts of data faster than a human can reasonably respond to. The Shared Signals Framework allows customers to respond to threats in real-time and ensure that the user is who they say they are.
Session theft is just one threat that the Shared Signals Framework can help protect against. Many different kinds of security vendors participated in the interop event in December, highlighting the capabilities of this new framework. We saw demos from MDM products, IGA vendors, and other identity providers that showed how Shared Signals can be used to dynamically change user permissions based on risk. If risk is detected on a device, for example, Shared Signals can help an organization minimize possible damage by locking down the identity and application sessions. Today, this would take a lot of correlation and time, all the while allowing the attacker to try and gain access to more sensitive resources, but Shared Signals makes this enforcement happen in real-time.
We are also exploring how Shared Signals helps deliver a better experience across Cisco products. Customers who use multiple Cisco security products together can look forward to Duo sharing identity data to a variety of products all in real-time for better security outcomes. Imagine, for example, that Duo detects a pattern of logins that are highly suspicious from a particular user. With Shared Signals, Duo could send that data to Cisco XDR to help enrich the detections happening there. With Cisco Secure Access, Shared Signals can help Duo communicate risk to cut off access to the network. We are very excited to see how Shared Signals with Duo can help on your identity security journey.
If you’d like to learn more about how Duo and Cisco are using Shared Signals—please feel free to reach out to your account team or contact us.

