How to protect your Active Directory with Duo’s new MFA and visibility solutions
At Duo, we believe strong security should be foundational regardless of your identity architecture.
With over 20 years of history, Microsoft’s Active Directory (AD) remains a stalwart for identity and access. Its deep roots in operations make it indispensable to business continuity, and it continues to house high-value data for organizations of all sizes. However, these foundational on-premises systems, passed from owner to owner, tend to rely on older, less secure protocols and are not built with visibility in mind.
Active Directory is everywhere—but attackers know it too
Complexity and a lack of inherent security controls make on-premises identity a perennial top target for attack. Last year, Cisco Talos found that nearly half of identity-based attacks focus on AD1. Techniques like Kerberoasting and Pass-the-Hash leverage service accounts, misconfigurations, and weak or compromised credentials to move laterally and escalate privileges. Meanwhile, IAM and SOC teams are forced into a patchwork approach of defense that juggles point solutions and complex workarounds.
Introducing Duo for Active Directory Defense
Duo’s new Active Directory Defense solution strives to answer the call for modern identity protection that doesn’t leave legacy infrastructure behind. We’re excited to announce expanded defense in two critical functions: visibility & protection. Already trusted by thousands of organizations to protect their on-premises infrastructure, including popular integrations for Windows Logon and RDP, Duo now has visibility and risk analytics tied directly to AD and is combining that visibility with the powerful enforcement mechanism of MFA insertion into key AD authentication paths.
For a deeper dive into what’s new, reserve your spot with the Duo Product team in the upcoming live webinar: How to Close the Active Directory Security Gap, Finally.
Expanding Intelligence for on-prem identity sources
It's hard to protect what you can't see. Now, crucial data from Active Directory is finally a visible component of centralized identity analytics. Duo enables deep identity security posture management and threat detection that bridges data together from previously opaque on-prem identity sources.
In the Cisco Identity Intelligence (CII) dashboard, get visibility into on-prem AD identities including admin, guest, and non-human identities (NHI) like service accounts. Detect misconfigurations and risky identity anomalies with proprietary intelligence checks and report on improved security posture.
Run posture checks on your Active Directory in Cisco Identity Intelligence
“The ‘never logged in’ check is so valuable, I just clean up 150 AD accounts yesterday based on this check.” – Alpha customer
Identity Attack Path Mapping with SpecterOps BloodHound Enterprise
The sprawl of identities across and within platforms grows the surface of attack exponentially. Duo partners with SpecterOps to bring leading attack path intelligence with BloodHound Enterprise into one centralized identity security strategy. The partnership adds enriched Active Directory insights from Bloodhound for prioritized vulnerability remediation and the ability to double-click into known and novel attack paths at scale.
Learn more about Cisco and SpecterOps
Rarely is Active Directory the only IAM tool at play in an enterprise. “Identity drift” can result in disparities between on-prem AD and cloud-based identity environments as organizations adopt modern solutions. With simple set-up and quick integrations, Cisco Identity Intelligence brings together best-in-class security checks to turn cross-platform identity detections into tangible security upgrades.
Extending MFA for unprotected legacy authentication protocols
According to Gartner®, “over 50% of organizations use NTLM.”2 Legacy protocols remain prevalent in network and identity administration, but these types of logins are often susceptible to readily available attack tools. Now, Duo brings award-winning MFA directly to all Active Directory authentications—including command line interfaces (CLI) and legacy applications using Kerberos and NTLM.
Modernize on-prem identity and block unauthorized access to critical systems by brokering all secure authentications through a single identity and access management solution.
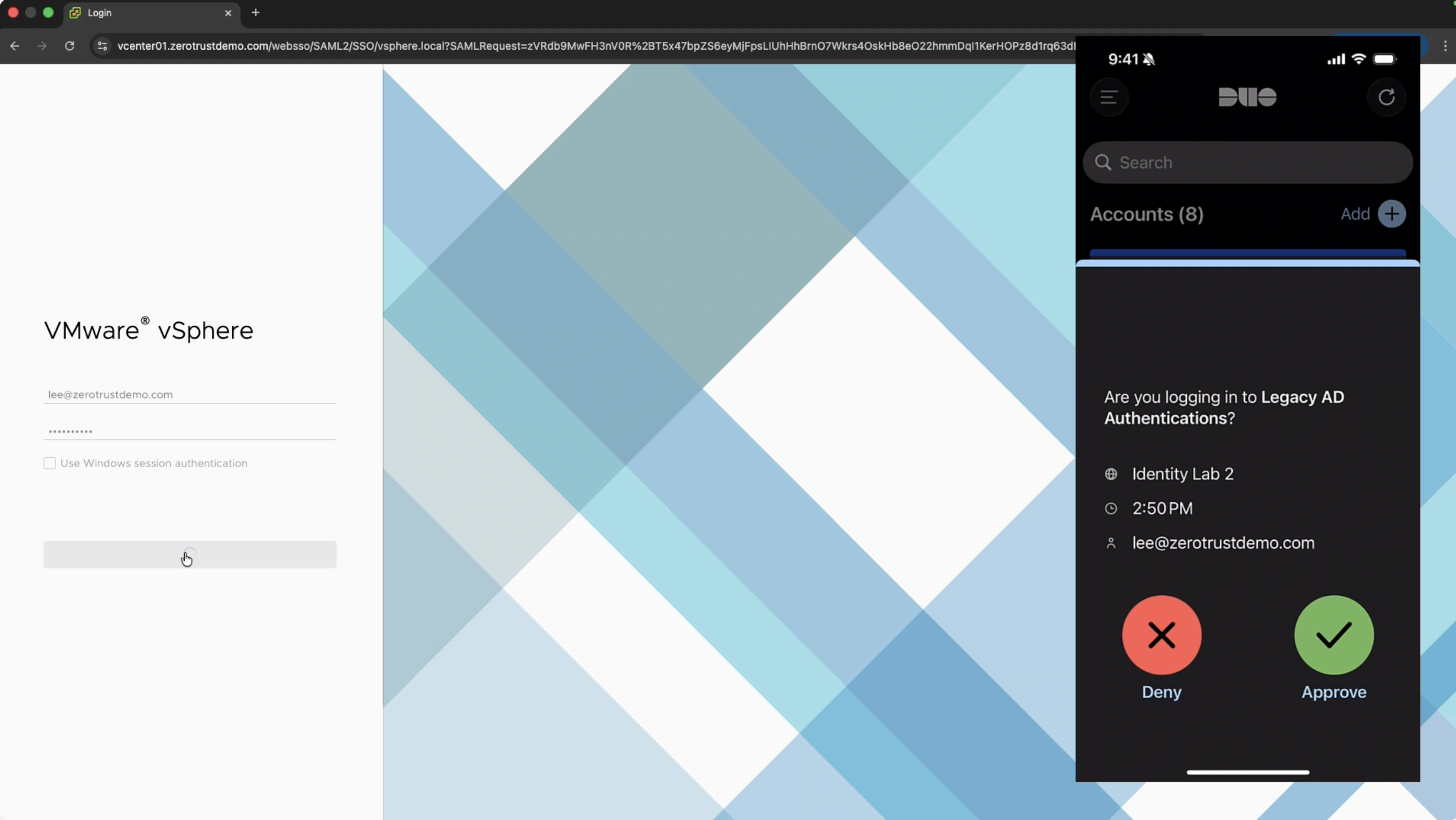
Use the Duo Mobile App to secure legacy authentications with MFA
What’s changed for identity compliance in 2026?
Auditors and insurers are raising the bar. Compliance now means full MFA coverage, unified reporting, and complete visibility. A rising ratio of non-human identities, spurred by agentic AI adoption, further complicates security with potential for excessive permissions and weak monitoring.
Duo gives you much-needed visibility into privileged and non-human accounts, so you can quickly spot misconfigurations and risky access attempts. Then, quickly comply with MFA “edge case” audit requirements for privileged access and generate reports with ease without increasing tool sprawl.
See how to defend the AD edge
Complex architectures and limited native controls make it hard for defenders to keep up. With Duo, elevate AD security without disrupting your business: no rip-and-replace, no costly workarounds, and the clean administrative and user experience Duo is known for.
Join us in our upcoming webinar How to Close the Active Directory Security Gap and learn more about how Duo can help your organization build a zero trust identity future—without leaving your legacy behind.
Gartner, Gartner IAM 2025 Presentation, Technical Insights: Active Directory May Be Old, But You Still Can’t Do Without It, Paul Rabinovich, December 10, 2025


