Verified Duo Push makes MFA more secure
Editor's Note: We're excited to announce that Duo Verified Push is now generally available!
As a security focused organization, Duo is committed to giving our customers the best available tools to address their security concerns. So we listened when customers pointed out the weaknesses in the Duo Push—the notification Duo Mobile users approve when they want to log into protected accounts. We’re excited to announce early access release of the Verified Duo Push, which will increase the security of our push-based multi-factor authentication (MFA) solution. This, in turn, will help improve the resilience of your network against bad actors looking to exploit push harassment or push fatigue.
Access security is evolving
While some customers begin to move toward passwordless to improve their security posture, not all organizations have the infrastructure or resources to make that change. With modern phishing-resistant authentication methods, we need to ensure that organizations continue to have the best security around push-based MFA.
Working with our customers, we have identified that push-based authentication can be vulnerable to:
Push Harassment – Multiple successive push notifications to bother a user into accepting a push for a fraudulent login attempt
Push Fatigue – Constant MFA means users pay less attention to the details of their login, causing a user to mindlessly accept a push login
User training, device trust, and adaptive policies are all important, but Duo is committed to offering more for customers.
Introducing Verified Duo Push
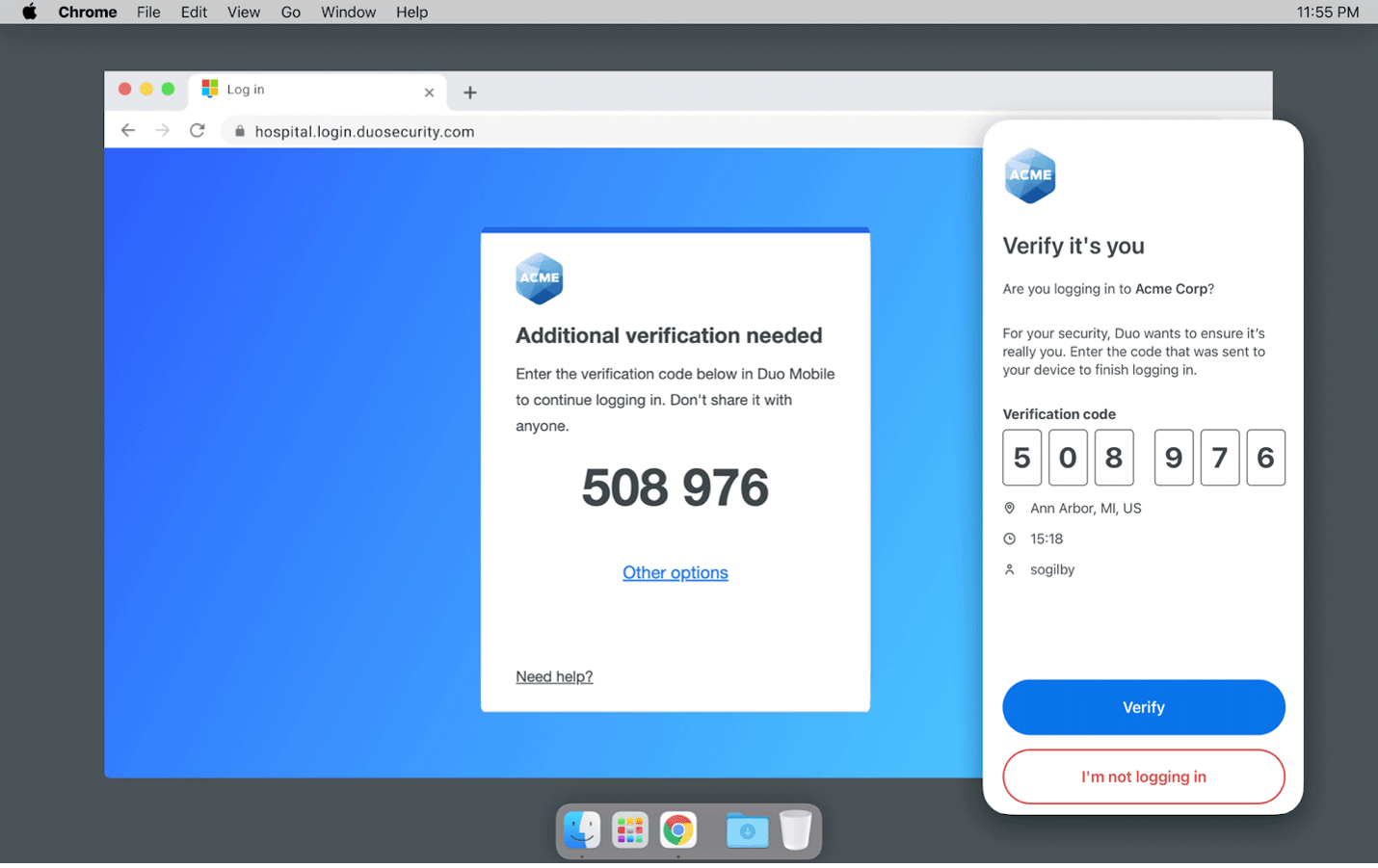
As a first step, we are excited to bring our customers Verified Duo Push, which stops these attacks by asking users to enter a verification code from the access device into the Duo mobile app during the push login process. By using a verification code, we ensure only verified users are able to log in, and prevent someone absent-mindedly accepting a push they did not request.
For example, imagine a key employee is vacationing and notices their phone has a Duo push. Ordinarily they would ignore it, but this time they deny it. They receive a second notification and assume it's simply their Virtual Private Network (VPN) at home reconnecting and accept the push.
With a standard push-based MFA solution, the bad actor now has access to the company network. However, with Verified Duo Push that same attack is immediately stopped because the bad actor is unable to complete the transaction—they cannot enter the unique code in the Duo app, and the employee is encouraged to alert their IT team with a fraud report.
By deploying this new authentication method as part of Duo’s adaptive policies you can harden your device enrollment process, secure sensitive applications, and protect your organization against the latest techniques from adversaries.
We aren’t stopping there
We are excited to bring our customers more secure authentications with the following roadmap investments landing right around the corner:
Risk-Based Authentication — Dynamically assess the authentication for push harassment and other threat patterns enhanced with anomaly detectors to automatically step up the authentication to the most secure methods including Verified Duo Push
Improved FIDO2 and Passwordless Support — Phishing resistant factors like FIDO2 and Mobile Biometric authenticators are the future and we want to make it easier for customers to deploy and manage
Device Enrollment Threat Detection and Response — Analyze, surface and quarantine risky device enrollments to ensure only valid devices can be used to authenticate

