Duo Passwordless
Last updated:
Overview
Duo Passwordless uses passkeys and platform authenticators, security keys from access devices, or Duo Push to secure web-based application access without passwords, reducing the risk surface and administrative burden associated with passwords while improving the user experience. With Duo Passwordless, users no longer have to remember or type long, complex passwords. Instead, they can log in securely with a single gesture that provides the security of two authentication factors.
Duo Passwordless enablement for your organization relies on Duo Single Sign-On (SSO), which can authenticate Duo Directory hosted users, or users in your existing Active Directory or an external single sign-on identity provider you may already use, such as AD FS, Okta, or PingFederate. The browser-based applications your users sign in to with Duo Passwordless may be federated with Duo SSO or with your existing SSO identity provider.
Duo Passwordless is available to Duo Premier, Duo Advantage, and Duo Essentials plans customers.
Why Go Passwordless?
Passwordless authentication for web-based applications offers...
- Phishing-resistant FIDO2 passkey authentication.
- A faster, more secure user experience.
- Modern compliance standards.
With complete passwordless from Duo, your users don't have to set a login password at all, but the option to have them do so is there if you need it.
Learn more about the benefits of passwordless authentication, and explore The Administrator's Guide to Passwordless for technical details.
Passwordless Quick Start
Follow our recommended journey to launch passwordless adoption in your organization.
Passwordless for Duo Single Sign-On Applications
-
We've enabled Duo as an authentication source for Duo Single Sign-On applications by default. This means you can store your users in Duo without the need for any other user directories or identity stores.
- [Optional] If you’d like to require that your users set a login password in Duo, configure your enrollment policy to require a password.
You can also add your existing on-premises Active Directory as an SSO authentication source.
If you already have an existing SSO identity provider in place — like Okta, Microsoft Entra ID (formerly known as Entra ID), or PingFederate — you can still use Duo Passwordless by chaining your organization's existing SAML identity provider (IdP) to Duo SSO.
Find more information about using your existing IdP with Duo Passwordless in the Duo Passwordless and SAML External Identity Providers step of the deployment instructions below.
If you have multiple authentication sources in your organization, plan your SSO routing rules so that users authenticate against the right identity store.
-
Federate your SAML or OIDC service provider applications with Duo SSO as the identity provider. Choose an SSO application from our catalog, or use our generic SAML or OIDC apps if your SSO app isn't listed.
-
Enroll your pilot users in Duo. You can create your test users and groups manually, or import them from CSV files or an existing external directory.
-
Configure an authentication method policy that enables passwordless-compatible methods and apply it to pilot users and applications.
-
Authenticate to web-based SSO applications with a passwordless authenticator. Duo's passwordless authenticators options include:
- Platform authenticators - WebAuthn passkey authenticators integrated into their device hardware and operating system, like the Touch ID fingerprint reader on a Mac, to authenticate.
- Roaming authenticators - FIDO2-compliant WebAuthn passkey security keys.
- Duo Push - authentication requests sent to Duo Mobile on an iOS or Android device.
When a user has a platform or roaming authenticator available, Duo nudges them to complete inline passwordless enrollment. If they have Duo Mobile activated for Duo Push authentication, they can use that as the passwordless authenticator.
- Monitor passwordless adoption by your pilot users with the reporting available in the Duo Admin Panel, and plan a phased rollout to more users and applications.
When your organization is ready to go completely passwordless:
-
Update your authentication methods policy to prevent password fallback by disabling all the "2FA authentication methods" and apply it to your complete passwordless pilot users and applications. Leave the authenticators in the "Passwordless authentication methods" policy enabled, including bypass codes (to aid passwordless users with account recovery).
-
If you have an enrollment policy in effect that asks users to set a Duo password, update it to remove the password requirement (or create a new custom enrollment policy without passwords) and apply it to the pilot user groups. New users will enroll into Duo without ever setting a password.
Complete passwordless users who need help with account recovery do so using a bypass code issued by a Duo administrator. Bypass codes used for passwordless logins require endpoint verification of the device accessing the application for extra security.
Passwordless for Windows OS Logon
Passwordless for Operating System (OS) Logon offers the option to logon locally to Windows systems without providing a password. It relies on a Bluetooth connection to a device with Duo Mobile installed and activated for Duo Push as the passwordless authenticator.
This is a distinct deployment, enrollment, and authentication experience from passwordless for Duo SSO applications as described on this page.
Learn how to deploy Passwordless for Windows OS Logon.
Enable Duo Passport for a seamless authentication experience from OS logon to SSO application logins.
Enrollment and Authentication Experience
When a user without a passwordless authenticator accesses a Duo Single Sign-On application which has a passwordless policy applied, the user enters their username and password as usual and completes Duo two-factor authentication (2FA). When an authentication method supported by Duo Passwordless is used for 2FA then the user receives a notification that they can log in without a password in the future with that method. Otherwise, the user sees the option to enroll in Duo Passwordless by registering their first platform or roaming passwordless authentication method for that access device if these options are enabled in your authentication methods policy.
After that, the user experiences passwordless login for the application or applications subject to the passwordless policy when using that access device. Instead of entering a password, the user's registered passwordless authenticator supplies identity verification.
A user without a Duo password who has completed Duo enrollment of a passwordless-compatible authentication method with an emailed enrollment link, an enrollment code provided by an administrator, or by authentication against an SSO external authentication source or with a temporary password can then use that enrolled authentication method for passwordless logins.
If a user has an Android or iOS device with Duo Mobile activated for Duo Push login request approval, then they can use that same device as a Duo Push passwordless authenticator.
If a user's registered passwordless authenticator isn't available at application sign-in, Duo falls back to the username and password plus 2FA authentication flow. If you opt to disable password fallback, an administrator can issue a bypass code to the user to help them regain access.
The end-user's browser language settings determine the language. No extra language configuration steps are necessary for Duo administrators or users. Administrators may also configure translated custom help desk messages in User Communication settings. The "Language" setting selected in the Admin Panel has no effect on the language shown in Duo Passwordless.
- Supported languages: Catalan, Chinese (Simplified), Chinese (Traditional), Czech, Danish, Dutch, English (US), Finnish, Hindi, Indonesian, Italian, Korean, Norwegian, Polish, Portuguese (Brazil), Portuguese (Portugal), Swedish, Thai, Turkish, and Vietnamese.
Remembered Devices
Passwordless logins may be subject to the same remembered devices policy as 2FA-only application logins. Users can opt to trust the browser when logging in to the application.
Passwordless remembered devices sessions have a maximum duration of seven days (168 hours), even if your policy setting specifies a greater number of hours.
Supported Identity Sources
Duo Passwordless supports:
- Duo-hosted users (Duo Directory). We recommend this option for the quickest deployment.
- Active Directory when configured as an external authentication source.
When you opt to allow Duo Passwordless authentication for users from Active Directory external authentication sources, users with expired Active Directory passwords or with locked-out AD accounts may log in to SSO applications. Learn more about Duo Passwordless for external Active Directory users in the Active Directory authentication source documentation.
- A SAML identity provider (IdP) — like Microsoft Entra ID, Okta, or PingFederate — as an external authentication source.
- Find more information about using your existing SAML IdP with Duo Passwordless in the Duo Passwordless and SAML External Identity Providers step of the deployment instructions below.
Supported Authentication Methods
Duo Passwordless supports a diverse set of end-user authenticators and phishing-resistant passkeys for web-based application logins, including:
- Windows Hello on compatible Windows devices.
- Touch ID on compatible macOS devices.
- Face ID or Touch ID on compatible iOS and iPadOS devices.
- Android Biometrics, such as Pixel fingerprint or facial recognition, or Samsung fingerprint or facial recognition.
- WebAuthn FIDO2 security keys with biometric or PIN verification, like those from Yubico or Feitian.
- Duo Push authentication request sent to Duo Mobile on Android or iOS when the mobile device is secured with biometric, PIN, or passcode to unlock.
Supported Applications
Duo Passwordless supports SAML and OIDC applications which show the Duo Universal Prompt in a browser or in a client application which renders the prompt using an embedded browser or the system browser.
Supported Browsers
Duo Passwordless supports Chrome (Desktop and Mobile), Safari (Desktop and Mobile), Edge, and Firefox. Not all browsers support all verification methods on a given operating system, so for the widest compatibility we recommend Chrome or the browser that came with your operating system.
Check the tables below for supported browser versions and Duo verification option compatibility. While other browsers may work with Duo Passwordless, Duo actively tests and supports the browser minimum versions listed in the tables.
We define "platform authenticators" as the authentication methods integrated into to your device hardware and operating system, like the Touch ID fingerprint reader on a Mac, and "roaming authenticators" as authentication methods that can be inserted into or paired with your device and then removed, like a USB security key.
The access device's browser must be able to store cookies to use Duo Push as a passwordless authenticator.
Windows 10 and Later
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Edge | 79 | Yes 1 | Yes | Yes |
| Chrome | 73 | Yes1 2 | Yes | Yes |
| Firefox | 66 | Yes | Yes | Yes |
-
Windows Hello not supported in Chrome Incognito or Edge InPrivate browsing sessions.
-
Use of passkeys as platform authenticators requires Windows 11 and Chrome 108 or later.
macOS 11 and Later
You must sign in with the same iCloud account and enable iCloud Keychain sync on all the Apple devices you plan to use with Duo and passkeys. See the iCloud documentation for instructions specific to your device types:
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Safari | 14 | Yes 1 | Yes | Yes |
| Chrome | 70 | Yes 1 | Yes | Yes |
| Firefox | 114 | Yes 2 | Yes 3 | Yes |
-
Use of passkeys as platform authenticators requires macOS 13 and Safari or Chrome 108.
-
Firefox 122 or later is required for platform authenticators.
-
Firefox on macOS cannot prompt to create a security key's PIN. Security keys that already have a PIN set can be used to authenticate in Firefox.
iOS/iPadOS 16.0 and Later
You must sign in with the same iCloud account and enable iCloud Keychain sync on all the Apple devices you plan to use with Duo and passkeys. See the iCloud documentation for instructions specific to your device types:
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Safari | 14.5 | Yes | Yes | Yes |
| Chrome | 95 | Yes | Yes | Yes |
| Edge | 95 | Yes | Yes | Yes |
| Firefox | 68 | Yes | Yes | Yes |
Android 11 and Later
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Chrome | 95 | Yes 1 | Yes 2 | Yes |
| Firefox | 68 | Yes 3 | No 4 | Yes |
-
Passkey support with Google Password Manager.
-
Chrome on Android 11 cannot prompt for the security key's PIN to fulfill the passwordless user verification requirement.
-
Firefox on Android 11 does not support Android biometric enrollment.
-
Firefox on Android cannot prompt for the security key's PIN to fulfill the passwordless user verification requirement.
Linux
Linux has no supported platform authenticators.
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Chrome | 73 | No | Yes | Yes |
| Edge | 79 | No | Yes | Yes |
| Firefox | 114 | No | Yes | Yes |
ChromeOS 108 and Later
| Browser | Minimum Supported Version | Platform Authenticator | Roaming Authenticator (Security Keys) |
Duo Push Authenticator |
|---|---|---|---|---|
| Chrome | 108 | Yes | Yes | Yes |
Passwordless Settings in Duo Policies
Some available policy settings have explicit settings that do or do not affect passwordless authentication.
When a policy section applies to multi-factor (MFA) authentication only and has no effect for passwordless logins, the policy editor's "Dependencies and warnings" information states "Does not apply to passwordless authentications" when you edit the configuration for that policy section.
Some individual options in a policy section may only affect MFA authentication. The descriptions of these settings will note that they do not apply to passwordless authentications.
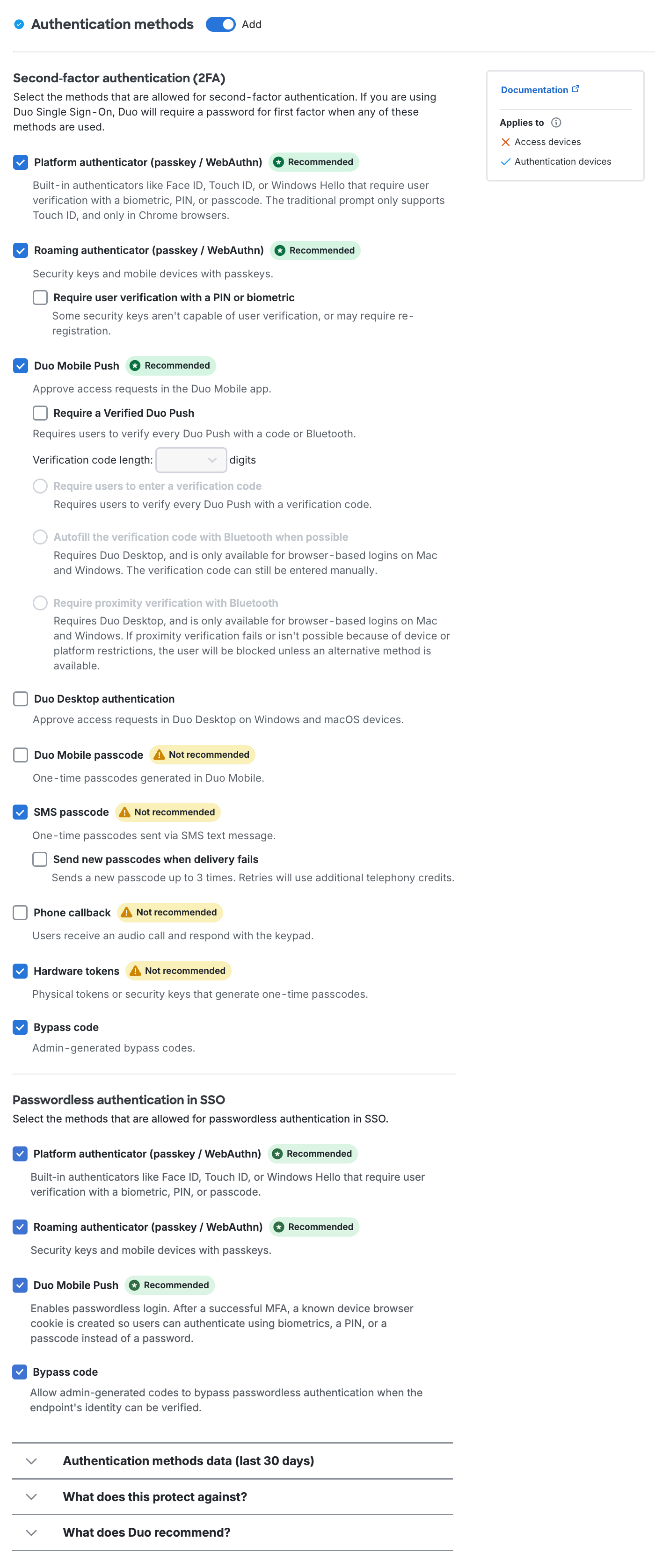
Authentication Methods
The authentication methods policy distinguishes between 2FA methods and passwordless methods. Enabling any of the passwordless methods in a policy permits use of passwordless authentication for any Duo Single Sign-On application subject to that policy. The passwordless authentication methods settings have no effect for non-SSO applications, as those applications do not support passwordless logins today.
Disabling all 2FA authentication methods in a policy applied to SSO applications means that password fallback for passwordless users is unavailable. Users must have their enrolled passwordless authenticator available for SSO application access, or they will need a bypass code issued by a Duo administrator to temporarily log in to the application.
If you started your Duo account before June 2025, then the passwordless authentication methods for SSO won't be enabled in an existing policy until you enable them. If you create a new policy or revert your Global Policy to default settings, all passwordless authentication methods will be enabled by default in those policies.
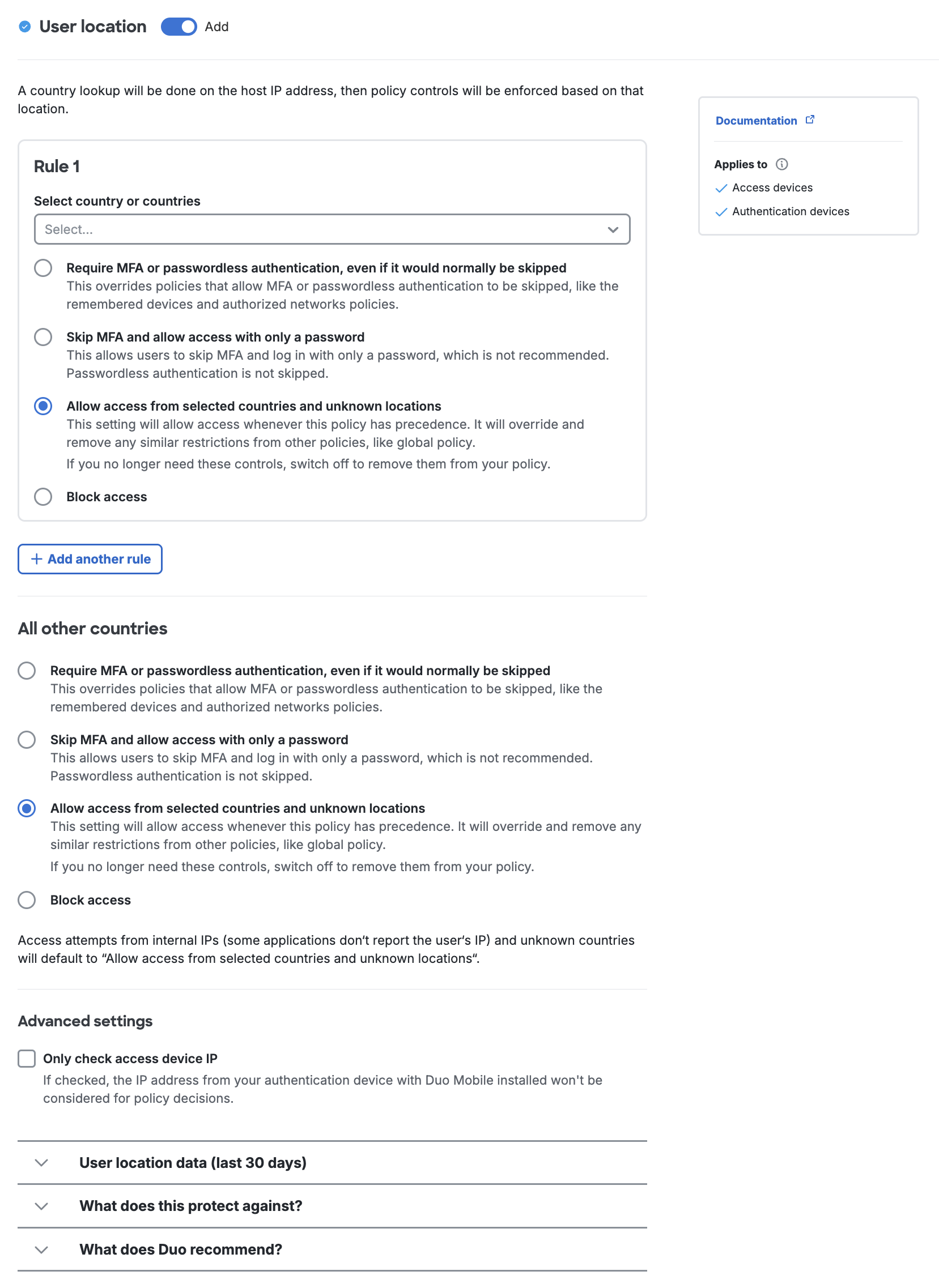
User Location
The user location policy notes that some options apply to both multi-factor authentication and passwordless authentication or only to MFA.
Authorized Networks
The authorized networks policy can't be used to allow access to an application without completing passwordless authentication, but the "deny" policy options do apply to passwordless authentication.
The Duo Essentials plan authorized networks policy only permits specifying a network to bypass Duo Essentials for regular (not passwordless) authentication, and does not include the require or deny options.
Passwordless Features
Supported Duo features include:
-
Complete passwordless: users do not need to set a password and password fallback at login is disallowed.
-
Automatic fallback to password login with two-factor authentication in scenarios where passwordless isn't available if allowed by policy.
-
Support for WebAuthn FIDO2 security keys as a passwordless authenticator.
-
Support for platform authenticators and passkeys from various vendors like Microsoft, Apple, Google, Samsung, etc.
-
Support for Duo Mobile as a passwordless authenticator on Android and iOS devices.
-
Self-service initial registration of access device passwordless authenticators after successful password verification and two-factor authentication.
-
Self-service management portal for passwordless and MFA devices accessible from the Duo Passwordless authentication prompt when the self-service portal has been enabled for the application being accessed.
-
Duo Administrators may view and delete users' platform and roaming passwordless authenticators from the Duo Admin Panel.
-
Verified Duo Push for passwordless logins with Duo Push.
-
Support for Authorized networks policy.
-
Support for Remembered Devices policy at passwordless login.
-
Support for these Duo authorization policy settings: User Location, Operating Systems, Browsers, and Anonymous Networks.
-
Support for Duo Duo Desktop policy checks at passwordless login.
-
Support for Trusted Endpoints device trust policy with management systems that rely on Cisco Secure Endpoint verification, Duo Duo Desktop trust verification, Duo Mobile Verification, or Duo Mobile managed devices.
- Trusted device verification using certificates or Google Verified Access is not supported.
-
Reporting for passwordless deployment and penetration in the Passwordless dashboard and passwordless authentication details in the Authentication Log.
Requirements
To deploy Duo Passwordless in your organization, you need the following:
-
A Duo Admin with the Owner or Administrator admin role.
-
Target applications for Duo Passwordless that support OIDC or SAML 2.0 authentication.
-
Passwordless authentications available for your user access devices: WebAuthn passkey platform or roaming authenticators such as Face ID or Touch ID on Apple iOS and macOS devices, Windows Hello on Windows devices, Android biometrics, or FIDO2 WebAuthn security keys; or Duo Mobile installed on Android or iOS devices and activated for Duo Push.
Prerequisites
To use Duo Passwordless, be sure you have:
-
Duo Single Sign-On (SSO) set up and working with Duo Directory as the authentication source, or an Active Directory (AD) external authentication source, and an SSO service provider application.
You can use Duo Passwordless if you have an existing SSO IdP. You'll federate your existing SAML IdP with Duo SSO to add passwordless authentication. Refer to the Duo Passwordless and SAML External Identity Providers for more details about this configuration. You do not need to reconfigure applications already federated with your existing SSO identity provider to point to Duo SSO.
-
If using an external Active Directory, your Duo Single Sign-On AD authentication source must use Duo Authentication Proxy version 6.5.1 or later, with the latest version recommended. Refer to the instructions for upgrading the Authentication Proxy servers used by Duo SSO to the current release version.
- We've raised the minimum Duo Authentication Proxy version needed for SSO authentication from 5.5.1 due to the 2026 Duo certificate authority bundle expiration. Please visit Duo Knowledge Base article 9451 for more information and guidance.
-
A SAML service provider (SP) application federated with Duo Single Sign-On, with both SSO primary authentication and Duo two-factor authentication working.
We recommend activating the Universal Prompt for your target OIDC or SAML application to provide users with a seamless experience and common look and feel between regular and passwordless authentication.
Duo Passwordless and SAML External Identity Providers
If you don't plan to use Duo Passwordless with an existing external SAML identity provider, you can skip this section and proceed to Configure Passwordless Policy.
You can use Duo Passwordless with your existing SAML identity provider in one of these ways:
-
Import your external SAML identity provider users into Duo with an inbound sync, so they exist in Duo. The default routing rule specifies Duo as the authentication source for SSO. Federate your external identity provider as a service provider app to Duo SSO. If necessary, in your IdP you will construct an authentication policy that delegates to Duo. This solution does not require Active Directory as an external authentication source.
-
If you have an Active Directory to use as an external authentication source for Duo Single Sign-On, you can chain your organization's existing SAML identity provider (IdP) as a generic SAML application in Duo SSO to provide passwordless login to the applications already federated with your IdP.
Service provider applications (like Salesforce, Microsoft 365, etc.) remain federated with your existing identity provider. You do not need to change the federation configuration for those applications to point to Duo SSO instead.
No additional IdP configuration steps are necessary when Duo Single Sign-On is your identity provider for OIDC or SAML applications and you have Duo-hosted users.
You will add Duo SSO as a new claims provider in AD FS. You must have an Active Directory external authentication source configured in Duo SSO.
Create the Duo SAML Application
-
Locate the entry for Generic SAML Service Provider with the "SSO" label in the catalog. Click the + Add button to start configuring Generic SAML Service Provider. See Protecting Applications for more information about protecting applications with Duo and additional application options. You'll need the information on the Generic SAML Service Provider page under Metadata later.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
In a new browser tab or window, navigate to your AD FS server's federation metadata at https://Your-AD-FS-Server/FederationMetadata/2007-06/FederationMetadata.xml. This downloads a FederationMetadata.xml XML metadata file to your computer.
-
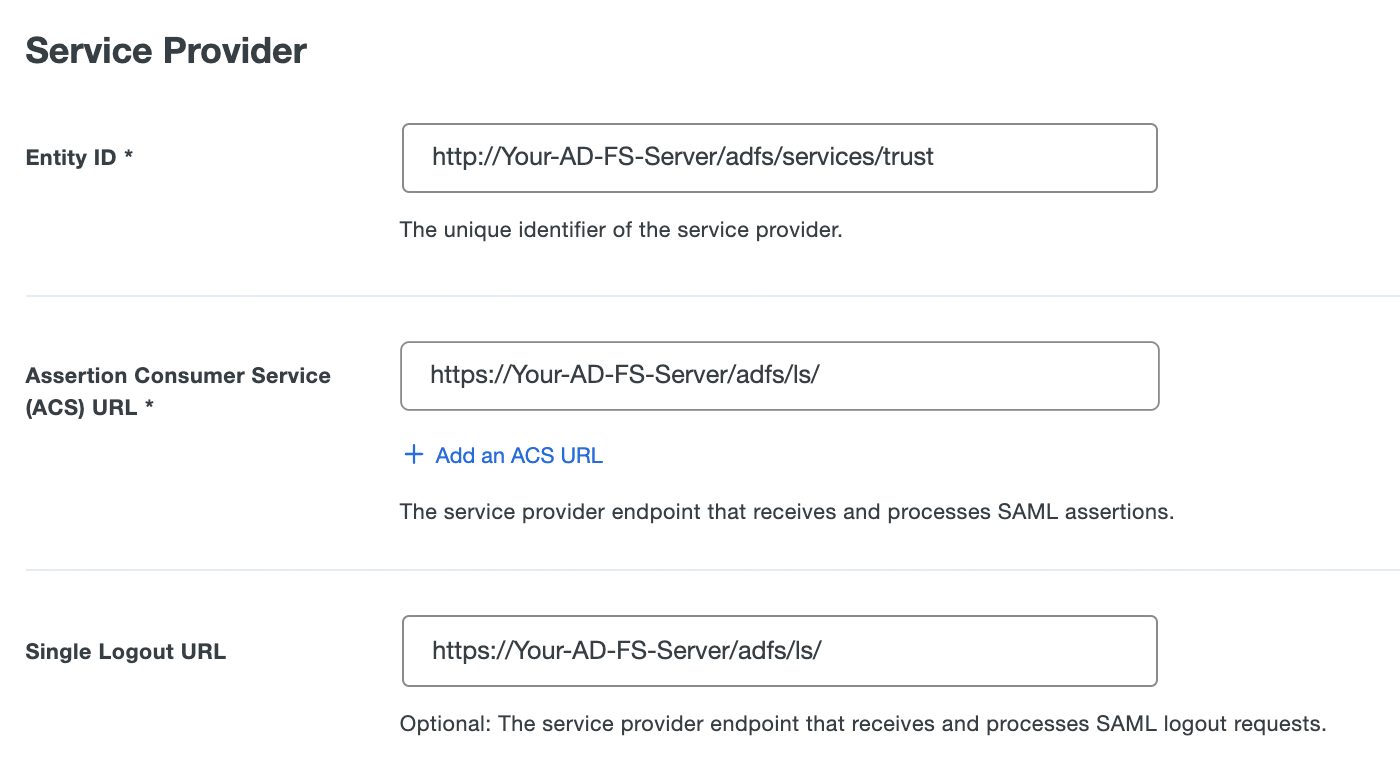
Open the FederationMetadata.xml file obtained from your AD FS server in a text editor. Use the information from the XML file to complete the Duo Generic SAML Service Provider application's Service Provider section as follows:
Name Description Example Value Entity ID The entityID parameter from the XML file. http://Your-AD-FS-Server/adfs/services/trustAssertion Consumer Service (ACS) URL The AssertionConsumerService Location parameter from the XML file. https://Your-AD-FS-Server/adfs/ls/Single Logout URL The SingleLogoutService Location parameter from the XML file. http://Your-AD-FS-Server/adfs/ls/Leave other settings in this section unchanged.
-
Make the following selections in the Duo Generic SAML Service Provider application's SAML Response section:
Name Value NameID format Select urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified. NameID attribute Type in the complete attribute name userPrincipalNamefollowed by pressing Enter.Signature Algorithm Use the default selection of SHA-256. Signing Options Enable both Sign response and Sign assertion. Leave other settings in this section unchanged.
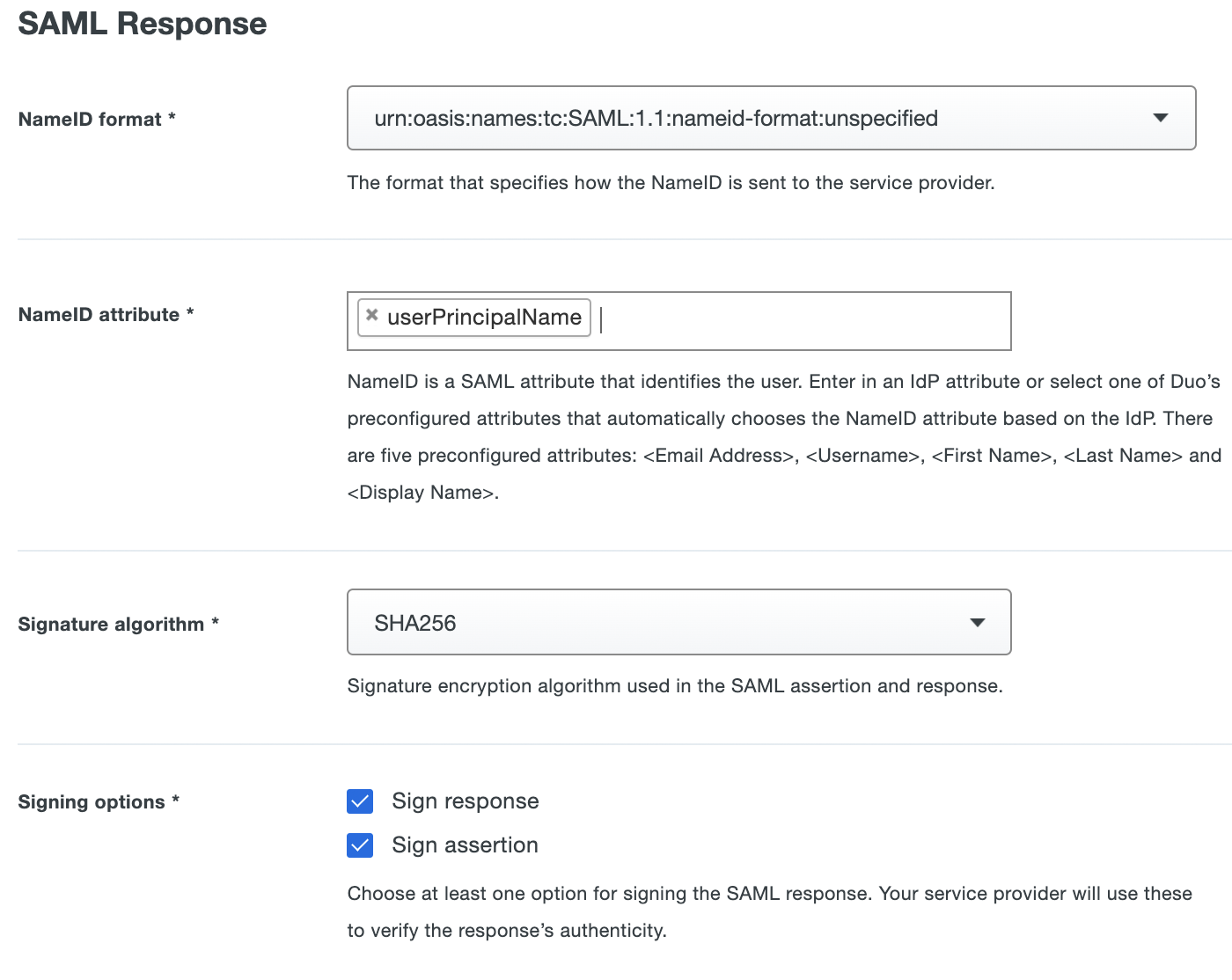
-
Scroll down on the Duo Generic SAML Service Provider application's page to the Universal Prompt section and select Show new Universal Prompt if not already selected.
-
Scroll down to the "Policy" section and apply a group or application policy that permits passwordless authentication methods.
-
Scroll down further to the "Settings" section. Enter a descriptive name for this application, like "AD FS Claims Provider Trust".
-
Click the Save button at the bottom of the page.
-
After saving the application configuration, scroll down to SAML Metadata in the "Downloads" section. Click the Download XML button. The XML file you download will have the same name that you gave this application in Duo.
-
Copy the XML file you downloaded from Duo to your AD FS server.
Create the AD FS Claims Provider Trust
-
Log in to your AD FS server and launch the AD FS Management console. Navigate to AD FS → Claims Provider Trusts.
-
Click the Add Claims Provider Trust... action in the "Actions" pane on the right.
-
Click Start on the first page of the "Add Claims Provider Trust Wizard".
-
On the "Select Data Source" page, select the Import data about the claims provider from a file option, and browse to the XML file you downloaded from the Duo Admin Panel and copied over to the AD FS server. Click Next after selecting the Duo XML file.
-
Enter a descriptive name for the Duo claims provider on the "Specify Display Name" page, and any additional information in the "Notes" field to help you identify this trust, and click Next.
-
Make no changes on the "Ready to Add Trust" page and click Next.
-
When you reach the "Finish" page, enable the Open Claim Rules option and then click Close.
-
On the "Edit Claim Rules for ..." page click Add Rule.... A new window will appear.
-
On the "Select Rule Template" page select Transform an Incoming Claim from the drop-down and click Next.
-
On the "Configure Rule" page type Name ID to UPN into the "Claim rule name" field.
-
Select Name ID from the "Incoming claim type:" drop-down.
-
Leave the "Incoming name ID format:" value as Unspecified.
-
Click the drop-down next to "Outgoing Claim Type" and select UPN.
-
Click Finish. If you receive a warning about passing claim values, click OK. You'll return to the "Edit Claims Rules for ..." window.
-
Click OK. The window will close and you'll return to the AD FS Management console.
Learn more about creating claims provider trusts at the Microsoft site.
Create a Claim Issuance Policy for Office 365
If you have Office 365 federated with AD FS, and you want to extend Duo Passwordless to Office 365 logins, follow these additional steps:
-
In the AD FS Management Console, go to AD FS → Relying Party Trusts
-
Right-click on the Microsoft Office 365 Identity Platform relying party and select Edit Claim Issuance Policy....
-
On the "Edit Claim Rules for ..." page click Add Rule.... A new window will appear.
-
On the "Select Rule Template" page select Send Claims Using a Custom Rule from the drop-down and click Next.
-
Name the new claim rule Send UPN as ImmutableID and enter in the following into the "Custom Rule" text box:
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"] => issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/claims/UPN", "http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID"), query = "userPrincipalName={0};userPrincipalName,objectGUID;YOURDOMAIN.COM\adfs_service_account_name", param = c.Value);IMPORTANT Make sure to update the service account information specified in the rule from
YOURDOMAIN.COM\adfs_service_account_nameto match your actual domain and the service account used to run the AD FS service on your server. -
Click Finish. You'll return to the "Edit Claim Issuance Policy for Microsoft Office 365 Identity Platform" window.
-
Click OK. The window will close and you'll return to the AD FS Management console.
If you do not have an on-premises Active Directory, you can use Duo as the authentication source for Duo SSO in conjunction with Entra to offer a complete passwordless experience.
Passwordless without Active Directory
Important Considerations
-
You must federate your entire Entra ID domain with Duo SSO using the Duo Microsoft 365 SAML application.
-
You must require that your imported Entra ID users set a password in Duo if you want them to be able to use Duo Push for passwordless authentication. If you do not want users to set Duo passwords, then do not enable the Duo Push passwordless authentication method in the effective policy, and only enable the platform authenticator and roaming authenticator WebAuthn passkey passwordless authentication methods.
To use Duo Passwordless with Entra ID without an Active Directory SSO authentication source:
-
Import all your existing Entra ID users into Duo with Entra ID directory sync. Once you have run a full sync to import all your Entra ID users into Duo, delete the Duo Entra ID Sync. This will mark those imported users as not managed by any directory sync, so you can modify them or add them to Duo groups.
Disable Entra ID sync to mitigate potential conflicts created when Microsoft 365 provisioning pushes changes to Entra ID, and then Entra ID sync tries to pull changes from Entra back to Duo. If you are syncing users from a different domain or source in Entra ID, you can still leave this Entra ID Sync active.
-
Ensure you have a routing rule enabled for Duo SSO authentication that uses Duo as the authentication source. This is the default routing rule option.
-
Locate the entry for Microsoft 365 with the "SSO" label in the catalog. Click the + Add button to start configuring Microsoft 365. See Protecting Applications for more information about protecting applications with Duo and additional application options. You'll need the information on the Microsoft 365 page under Metadata later.
Do not complete the federation steps yet.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
Apply a policy to the Microsoft 365 Duo application which has passwordless authentication methods enabled.
-
Configure automated provisioning for the Duo Microsoft 365 application and ensure that information is pushed from Duo to Entra ID.
This is necessary because once you federate an Entra ID domain with an external identity provider, like Duo SSO, you can no longer make changes to user objects in Entra. With Microsoft 365 automated provisioning in place, admins can manage and update users directly in Duo and changes will be pushed back to Entra.
-
Complete federation of the Entra ID domain to Duo SSO via the Duo Microsoft 365 application.
With these steps completed, the authentication flow for Entra ID users from the federated domain will be:
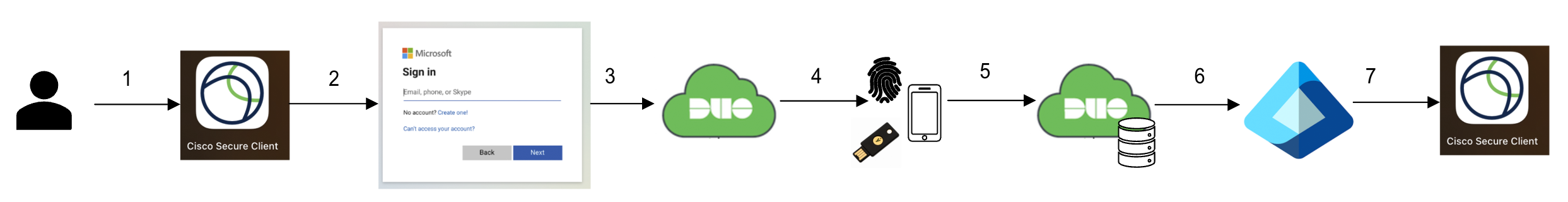
- User tries to access an application that uses Entra ID as the identity provider.
- The application redirects the user to Entra ID, where they enter their email address (if not remembered by the Microsoft Online sign-in page).
- Microsoft Online redirects the user to Duo Single Sign-On.
- Duo prompts the user to complete passwordless authentication.
- Duo validates the passwordless authentication. If the authentication was successful, the attributes necessary for completing Entra authentication are retrieved from within Duo's cloud service.
- Duo redirects the user back to Entra with a valid WS-FED response.
- Entra sends the user back to the initial application with a valid SSO response.
Passwordless with Active Directory and Entra ID
No additional IdP configuration steps necessary when you federate Microsoft 365 with Duo Single Sign-On using an on-premises Active Directory as the authentication source. Users in the federated tenant will redirect to Duo SSO for passwordless login.
Delegation between Duo SSO and PingFederate requires entering information from the Duo Admin Panel into PingFederate and vice-versa. Please refer to Ping's documentation for Managing IdP Connections and identifying identity providers in PingFederate for more details about this process.
You must have an Active Directory external authentication source configured in Duo SSO.
Create the Duo SAML Application
-
Locate the entry for Generic SAML Service Provider with the "SSO" label in the catalog. Click the + Add button to start configuring Generic SAML Service Provider. See Protecting Applications for more information about protecting applications with Duo and additional application options. You'll need the information on the Generic SAML Service Provider page under Metadata later.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
Make the following selections in the Duo Generic SAML Service Provider application's SAML Response section:
Name Value NameID format Select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress. NameID attribute Select <Email Address>. Signature Algorithm Use the default selection of SHA-256. Signing Options Enable both Sign response and Sign assertion. Leave other settings in this section unchanged.
-
In the Map attributes section, enter this mapping:
IdP Attribute SAML Response Attribute <Username> userid -
Scroll down on the Duo Generic SAML Service Provider application's page to the Universal Prompt section and select Show new Universal Prompt if not already selected.
-
Scroll down to the "Policy" section and apply a group or application policy that permits passwordless authentication methods.
-
Scroll down further to the "Settings" section. Enter a descriptive name for this application, like "PingFederate Service Provider".
-
Click the Save button at the bottom of the page.
-
Scroll up the page to the "Downloads" section of your generic SAML service provider's page and click Download XML to download the Duo Single Sign-On XML metadata file. You will import this file into PingFederate.
Add the Duo Application to PingFederate
Perform the remaining steps in the PingFederate administrative console. Refer to the PingFederate OpenToken Adapter documentation for more information about these configuration steps. You should have an adapter configured in PingFederate for your target service provider (SP) application (the application with which you want to use Duo Passwordless).
-
Log in to the PingFederate administrative console and navigate to Authentication → Integration → IdP Connections and create a new SAML 2.0 IDP connection for Duo, using the Import Metadata file selector to upload the metadata XML file you downloaded from the Duo Admin Panel. This will populate PingFederate with information about the Duo IdP, such as the Entity ID and connection name.
-
Go to Browser SSO and configure the SAML profiles to allow so that IDP-Initiated and SP-Initiated.
-
Go to User-Session Creation and configure it with your desired Identity and Account Mappings.
-
Go to Target Session Mapping and map your SP application adapter, including mapping attributes between systems (such as mapping
subjecttocn). -
Complete adapter mapping on the "Adapter Mapping Summary" tab and proceed to the "User-Session Creation Summary" tab to continue, clicking Done to accept your changes.
-
Go to Protocol Settings to configure the protocol settings. The SSO Service Endpoint URLs should be populated as a portion of the Duo EntityID metadata attribute, for example
/saml2/sp/DI73P00LD4DLMLNR9M00, and the SAML bindings should allow Post and Redirect. -
Use SAML Standard signature policy and no encryption. Proceed to the "Protocol Settings Summary" to continue, clicking Done to accept your changes.
-
Go to Credentials and verify the Duo IdP signing certificate and key was imported from the Duo metadata file.
-
Proceed to the "Activation and Summary" tab to make the connection active, and the save.
-
Test logging in to the SP whose adapter you selected during configuration; you should be redirected to Duo SSO.
If you use policy contracts you may need to create a new policy contract for Duo SSO and then create a new authentication policy tree in PingFederate, using the Duo Generic SAML application's IDP connection and the policy contract you just created as part of the authentication flow.
The Ping document Connecting Okta as an IdP through SAML to PingFederate as an SP is a step-by-step example of similar configuration that can be used as a guide to configuring Duo's SSO IdP as an SP in PingFederate.
If you do not have an on-premises Active Directory, you can use Duo as the authentication source for Duo SSO in conjunction with Okta to offer a complete passwordless experience.
Passwordless without Active Directory
Important Considerations
-
To test with a small group, you must configure Okta’s routing rules to identify the correct test users and send them to Duo. The easiest way to do this is defining a custom attribute on the user and using Okta’s routing rules to selectively send users with that attribute to Duo as an external identity provider.
-
You must require that your imported Okta users set a password in Duo if you want them to be able to use Duo Push for passwordless authentication. If you do not want users to set Duo passwords, then do not enable the Duo Push passwordless authentication method in the effective policy, and only enable the platform authenticator and roaming authenticator WebAuthn passkey passwordless authentication methods.
To use Duo Passwordless with Okta without an Active Directory SSO authentication source:
-
Import Okta users into Duo with Okta inbound SCIM. The default attribute selections include the required attributes necessary for authentication.
-
Ensure you have a routing rule enabled for Duo SSO authentication that uses Duo as the authentication source. This is the default routing rule option.
-
Locate the entry for Okta with the "SSO" label in the catalog. Click the + Add button to start configuring Okta. See Protecting Applications for more information about protecting applications with Duo and additional application options. You'll need the information on the Okta page under Metadata later.
Be sure that you chose the Okta application with the "SSO" label from the Duo Application Catalog. The Okta application with the "MFA" label does not use Duo SSO and provides multi-factor authentication only.
-
No active Duo users can log in to new applications until you grant access. Update the User access setting to grant access to this application to users in selected Duo groups, or to all users. Learn more about user access to applications. If you do not change this setting now, be sure to update it so that your test user has access before you test your setup.
This setting only applies to users who exist in Duo with "Active" status. This does not affect application access for existing users with "Bypass" status, existing users for whom the effective Authentication Policy for the application specifies "Bypass 2FA" or "Skip MFA", or users who do not exist in Duo when the effective New User Policy for the application allows access to users unknown to Duo without MFA. -
Apply a policy to the Okta SSO Duo application which has passwordless authentication methods enabled.
-
Complete configuration in Okta to use the Duo Okta application.
-
In the Okta console, go to the "Identity Providers" page and click the Routing Rules tab. Click Add Routing Rule.
-
Configure the new routing rule's logic to scope Duo Passwordless authentication to specific applications and/or specific users. For example, you may want to create a rule that routes any user assigned to a Salesforce app federated with Okta to your new Duo identity provider for passwordless authentication.
-
Click Create Rule to save your new rule. Once you save it you can drag it up or down your rules list to change its priority during rule evaluation.
With these steps completed, the authentication flow for Okta users subject to an Okta routing rule for Duo Passwordless will be:
- User tries to access an application that uses Okta as the identity provider.
- The application redirects the user to Okta, where they enter their email address.
- Okta redirects the user to Duo Single Sign-On.
- Duo prompts the user to complete passwordless authentication.
- Duo validates the passwordless authentication. If the authentication was successful, the attributes necessary for completing Okta authentication are retrieved from within Duo's cloud service.
- Duo redirects the user back to Okta with a valid WS-FED response.
- Entra sends the user back to the initial application with a valid SSO response.
For other IdPs not listed here by name, refer to the Duo Single Sign-On for Generic SAML Service Providers documentation for creating a Duo SAML SP application that you will then configure as a delegated identity provider in your organization's IdP.
Configure Passwordless Policy
Role required: Owner or Administrator
The next step in deploying Duo Passwordless is to update your existing Duo policies to enable passwordless authentication methods. Before making any policy changes you should decide if you want to allow fallback to password authentication or use complete passwordless, enable passwordless authentication for specific users or SSO applications, or for all users and compatible SSO applications.
If you create a new policy or revert your Global Policy to default settings after enabling Duo Passwordless, all passwordless authentication methods are now enabled by default as of June 2025.
The authentication method options for passwordless logins are:
-
Platform authenticator (passkey / WebAuthn): This enables end-user authentication using biometric sensors built into their devices, such as Touch ID or Face ID on Apple devices, Windows Hello on Windows 10 and 11 systems, or Android biometrics. Enabling platform authenticators prompts just those users with compatible access devices to register a passwordless authenticator when they log in.
-
Roaming authenticator (passkey / WebAuthn): This enables end-user authentication using FIDO2-compliant WebAuthn security keys, like those from Yubico or Feitian. Enabling roaming authenticators prompts all users to register a passwordless authenticator whenever they log in.
-
Duo Mobile Push: This enables end-user authentication by approval of a login request pushed to Duo Mobile on a user's Android or iOS device.
When a user has previously activated a device for Duo Push in order to perform two-factor authentication, or if a user performs first-time enrollment enrolls Duo Push, they can use that same device for Duo Passwordless authentication without repeating the enrollment process. In order to approve Passwordless Duo Push login requests the device with Duo Mobile installed must have its security settings configured to require biometric identification (like Face ID or fingerprint), PIN entry, or passcode entry to unlock the device.
Duo Push authentication for Duo Passwordless is enabled for the specific browser used to log in to a protected application from a given access device. Successful registration of Duo Push as a passwordless authenticator is accomplished by placement of a "known-device" browser cookie i.e. when a user logs into an application with Duo Push allowed for Passwordless using Chrome, Duo sets the "known-device" browser cookie for Chrome on that device.
The first time a user attempts to authenticate with Duo Push for passwordless login, they must perform a verified Duo Push. This means entering the six-digit code displayed in the Duo browser authentication prompt into Duo Mobile on their Android or iOS device. The user must also perform biometric or PIN/passcode verification while they approve this login request.
If the user opts to trust the browser after this first login, then future passwordless logins from that browser do not require entry of the six-digit verification code.
-
Bypass code: Users enter a numeric bypass code generated by a Duo administrator. This is useful when no other previously-registered authentication methods are available. When you configure complete passwordless, this is the only option for logging in when a user does not have access to their registered passwordless authenticators, as password fallback won't be available. Bypass codes used for passwordless logins require endpoint verification of the device accessing the application for extra security, either with a browser cookie present from a previous successful Duo authentication, or Duo Desktop collected a signed device health report during authentication.
Important Information for Passwordless Authentication Methods
-
When you enable platform authenticator passwordless methods in your policy, then users with devices that do not have a compatible platform authenticator do not receive the prompt for passwordless registration because their device does not support it. If you also enable 2FA platform authenticators then they will continue to log in with their password. If you don't also enable the 2FA platform authenticators method, users must have another passwordless method available or a bypass code to log in.
-
When you enable roaming authenticator passwordless methods in your policy, then users cannot register platform authenticators but they will still be offered the opportunity to register a security key. They will need access to a supported roaming authenticator to complete passwordless registration. Don't enable roaming authenticators if your users do not have access to compatible WebAuthn security keys with PINs or biometrics.
-
If a user previously registered a platform or roaming authenticator while subject to a different policy, they would not be able to use it to access an application when the effective policy only permits the type of passwordless authenticator they did not register, and will fall back to username and password authentication if a 2FA authentication method is also enabled. Otherwise, they will need a bypass code to log in.
Passwordless Authentication for Complete Passwordless
Assign Enrollment Policy with no Passwords
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to the Policies → User Enrollment and Account Management page.
-
Choose whether to enforce the Duo password requirement for your complete passwordless users in the Global Enrollment Policy or in a custom enrollment policy.
-
The default Duo password policy option disables requiring passwords. If this option is already disabled in your Global or custom enrollment policies, then no further action is needed.
If your Global or custom enrollment policies do require users to set a password, either update these policies to disable Require password, or create a new custom enrollment policy without Require password selected and apply it to the user groups you want to use complete passwordless authentication.
Enable Passwordless Methods with Application-Group Policy
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Policies → Policies and click + Add Policy. The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name on the "Name & details" tab, and then click the Authentication methods policy item on the left.
-
By default, all passwordless authentication methods are enabled. Deselect any methods you do not want users to authenticate with:
-
Platform Authenticators enables passkey authentication by your users with authenticators or biometric sensors built into their access devices.
-
Roaming Authenticators enables passkey authentication by your users with FIDO2-compliant WebAuthn security keys attached to their access devices.
-
Duo Push enables authentication by your users with Duo Mobile push request approval on Android and iOS.
-
Bypass code permits users to log in with a numeric code generated by a Duo administrator.
-
-
Disable all 2FA authentication methods enabled in the policy to prevent password fallback. When a user's passwordless authenticator isn't available they can use a bypass code instead.
-
Click the Save button to save the settings and create the new policy.
-
Navigate to Applications → Applications or use the search bar at the top of the Admin Panel to find the Single Sign-On application to which you want to apply your new Passwordless policy. Open the details page for that SSO application.
-
Scroll down on the SSO application's details page to the "Application-Group policies" section and click Apply a policy to groups of users to assign the new Passwordless policy to a test group.
-
Select the Passwordless authentication methods policy you just created from the Policy drop-down list.
-
Start typing in the pilot group's name in the Groups field and select it from the suggested names.
-
Click the Apply Policy button. The application page shows the new group policy assignment.
For more information about creating and applying group policies, see the Policy documentation.
Enable Passwordless with Application Policy
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Policies → Policies and click + Add Policy. The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name on the "Name & details" tab, and then click the Authentication methods policy item on the left.
-
By default, all passwordless authentication methods are enabled. Deselect any methods you do not want users to authenticate with:
-
Platform Authenticators enables passkey authentication by your users with authenticators or biometric sensors built into their access devices.
-
Roaming Authenticators enables passkey authentication by your users with FIDO2-compliant WebAuthn security keys attached to their access devices.
-
Duo Push enables authentication by your users with Duo Mobile push request approval on Android and iOS.
-
Bypass code permits users to log in with a numeric code generated by a Duo administrator.
-
-
Disable all 2FA authentication methods enabled in the policy to prevent password fallback. When a user's passwordless authenticator isn't available they can use a bypass code instead.
-
Click the Save button to save the settings and create the new policy.
-
Navigate to Applications → Applications or use the search bar at the top of the Admin Panel to find the Single Sign-On application to which you want to apply your new Passwordless policy. Open the details page for that SSO application.
-
Scroll down on the SSO application's details page to the "Application policies" section and click Apply a policy to all users to assign the new Passwordless policy to all users of this application.
-
Select the Passwordless authentication methods policy you just created from the Policy drop-down list.
-
Click the Apply Policy button. The application page shows the new policy assignment.
For more information about creating and applying application policies, see the Policy documentation.
Passwordless Authentication with Password Fallback
Assign Enrollment Policy with Passwords
You may skip these steps if you use Active Directory as the external authentication source for Duo Single Sign-On.
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to the Policies → User Enrollment and Account Management page.
-
Choose whether to enforce the Duo password requirement for your passwordless users in the Global Enrollment Policy or in a custom enrollment policy.
-
The default Duo password policy option disables requiring passwords. If your Global or custom enrollment policies don't require users to set a password, either update these policies to enable Require password, or create a new custom enrollment policy with Require password selected and apply it to the user groups you want to use passwordless authentication with passwords plus 2FA as a fallback.
If this option is already enabled in your Global or custom enrollment policies, then no further action is needed.
Enable Passwordless Methods with Application-Group Policy
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Policies → Policies and click + Add Policy. The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name on the "Name & details" tab, and then click the Authentication methods policy item on the left.
-
By default, all passwordless authentication methods are enabled. Deselect any methods you do not want users to authenticate with:
-
Platform Authenticators enables passkey authentication by your users with authenticators or biometric sensors built into their access devices.
-
Roaming Authenticators enables passkey authentication by your users with FIDO2-compliant WebAuthn security keys attached to their access devices.
-
Duo Push enables authentication by your users with Duo Mobile push request approval on Android and iOS.
-
Bypass code permits users to log in with a numeric code generated by a Duo administrator.
-
-
Disable all 2FA authentication methods enabled in the policy to prevent password fallback. When a user's passwordless authenticator isn't available they can use a bypass code instead.
-
Click the Save button to save the settings and create the new policy.
-
Navigate to Applications → Applications or use the search bar at the top of the Admin Panel to find the Single Sign-On application to which you want to apply your new Passwordless policy. Open the details page for that SSO application.
-
Scroll down on the SSO application's details page to the "Application-Group policies" section and click Apply a policy to groups of users to assign the new Passwordless policy to a test group.
-
Select the Passwordless authentication methods policy you just created from the Policy drop-down list.
-
Start typing in the pilot group's name in the Groups field and select it from the suggested names.
-
Click the Apply Policy button. The application page shows the new group policy assignment.
For more information about creating and applying group policies, see the Policy documentation.
Enable Passwordless with Application Policy
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Policies → Policies and click + Add Policy. The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name on the "Name & details" tab, and then click the Authentication methods policy item on the left.
-
By default, all passwordless authentication methods are enabled. Deselect any methods you do not want users to authenticate with:
-
Platform Authenticators enables passkey authentication by your users with authenticators or biometric sensors built into their access devices.
-
Roaming Authenticators enables passkey authentication by your users with FIDO2-compliant WebAuthn security keys attached to their access devices.
-
Duo Push enables authentication by your users with Duo Mobile push request approval on Android and iOS.
-
Bypass code permits users to log in with a numeric code generated by a Duo administrator.
-
-
Disable all 2FA authentication methods enabled in the policy to prevent password fallback. When a user's passwordless authenticator isn't available they can use a bypass code instead.
-
Click the Save button to save the settings and create the new policy.
-
Navigate to Applications → Applications or use the search bar at the top of the Admin Panel to find the Single Sign-On application to which you want to apply your new Passwordless policy. Open the details page for that SSO application.
-
Scroll down on the SSO application's details page to the "Application policies" section and click Apply a policy to all users to assign the new Passwordless policy to all users of this application.
-
Select the Passwordless authentication methods policy you just created from the Policy drop-down list.
-
Click the Apply Policy button. The application page shows the new policy assignment.
For more information about creating and applying application policies, see the Policy documentation.
Test Your Setup
Access your federated service provider application as a user whose effective authentication methods include passwordless authenticators from an access device that has a supported platform or roaming authenticator available. Log in with username and password if using an external authentication source, and then complete Duo two-factor authentication.
Passwordless Registration During Enrollment
When your users complete first-time Duo enrollment and register a passwordless-compatible authentication method, they're all set to perform passwordless authentication into your protected applications.
Automatic Passwordless Registration
If you sign in to Duo SSO using a platform authenticator for two-factor authentication, such as Touch ID or Windows Hello, then you'll automatically be able to use that same authentication method for Duo Passwordless login in the future without any further setup.
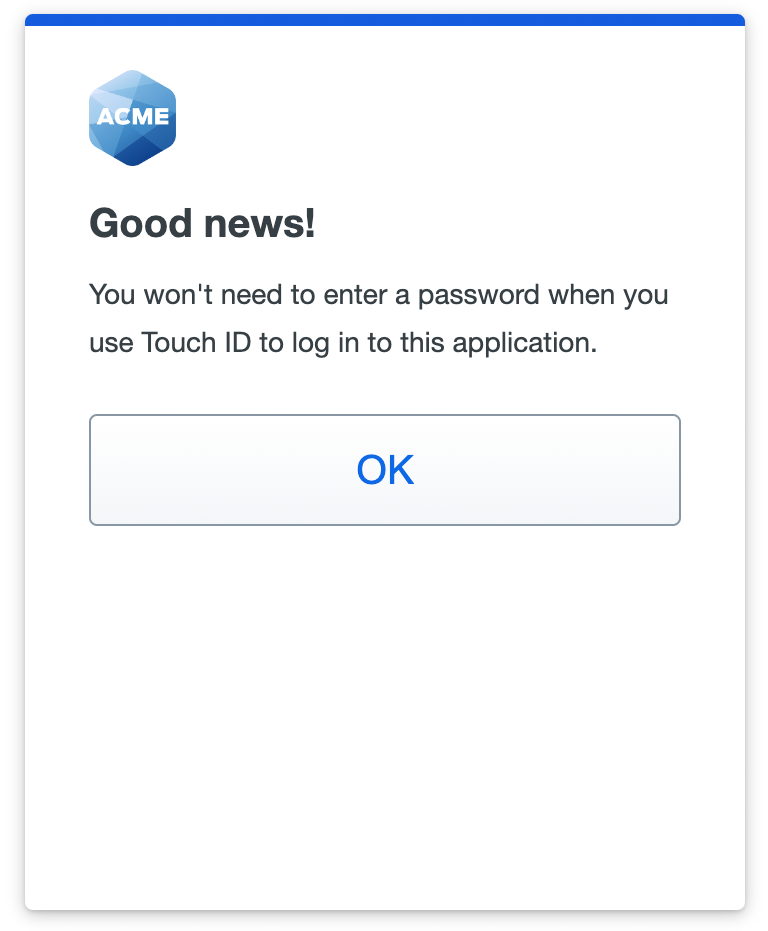
Signing in to Duo SSO applications using other Duo 2FA options will prompt you to begin passwordless registration.
Platform or Roaming Authenticator
After performing Duo authentication with an authentication method that doesn't support passwordless authentication (like an SMS passcode), Duo prompts you to begin passwordless registration. Click or tap Continue to begin. To delay passwordless setup click or tap Skip for now; you won't be asked again to set up Duo Passwordless in that browser for seven days.
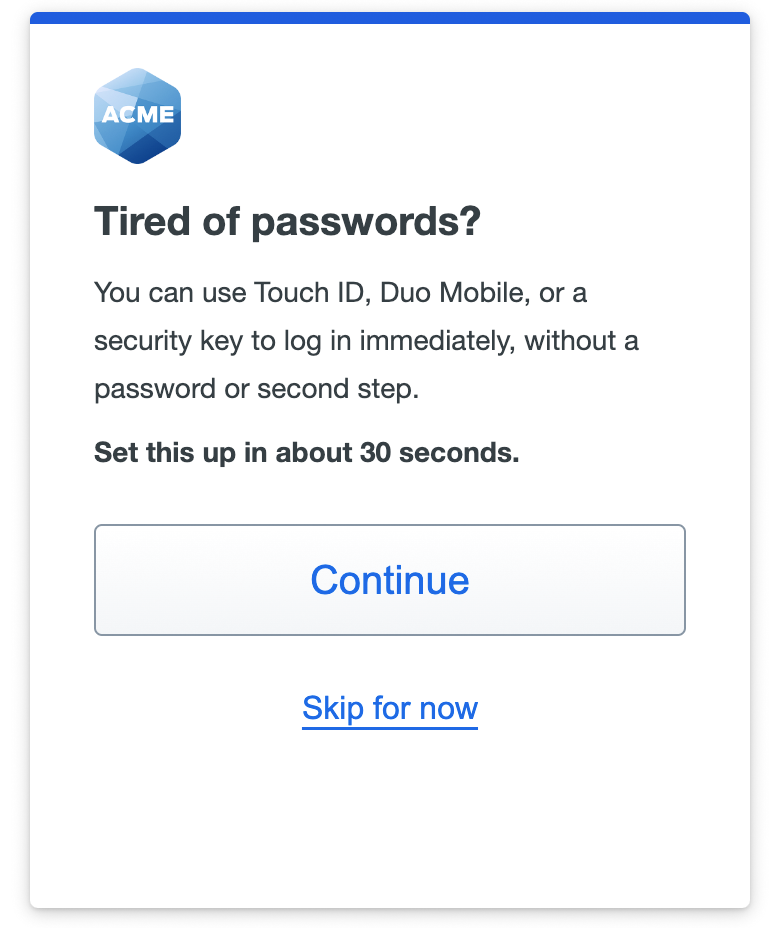
Choose which passwordless authenticator type to register. The options shown here correspond to the access device authenticators you enabled in your passwordless policy. In this example the policy allows platform, roaming, and Duo Push authenticators and the access device is a MacBook with Touch ID.
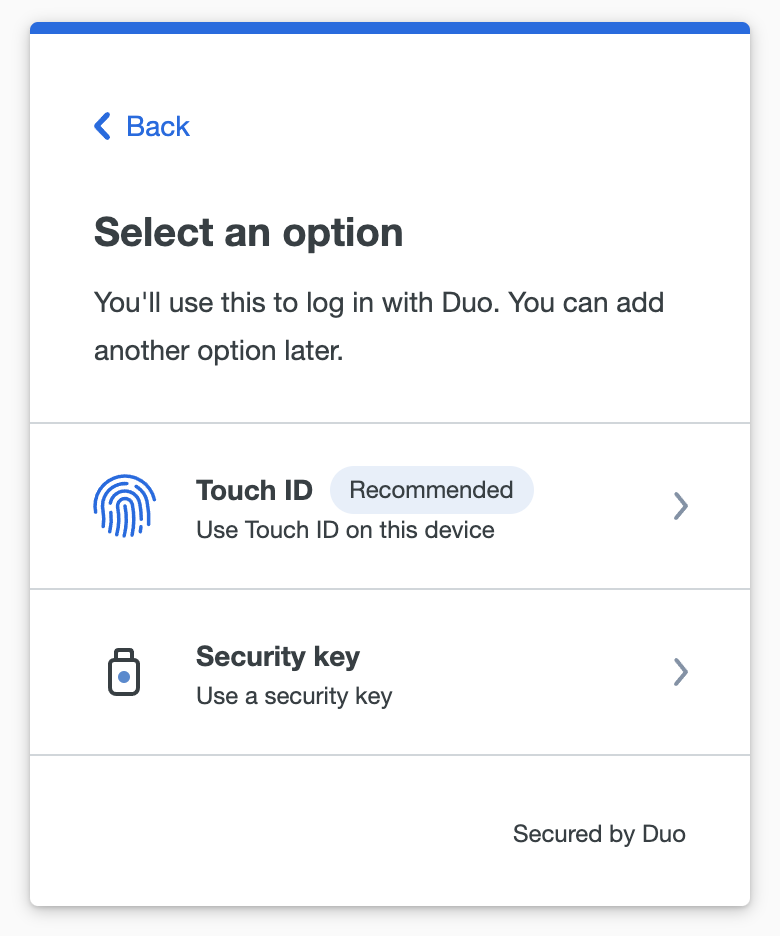
Follow the on-screen prompts to set up that device for Duo Passwordless. Depending on the type of authenticator you're registering, you will need to scan your fingerprint or face, enter a PIN, or tap a device. Continuing the Touch ID example, you'll tap the Touch ID reader when prompted.
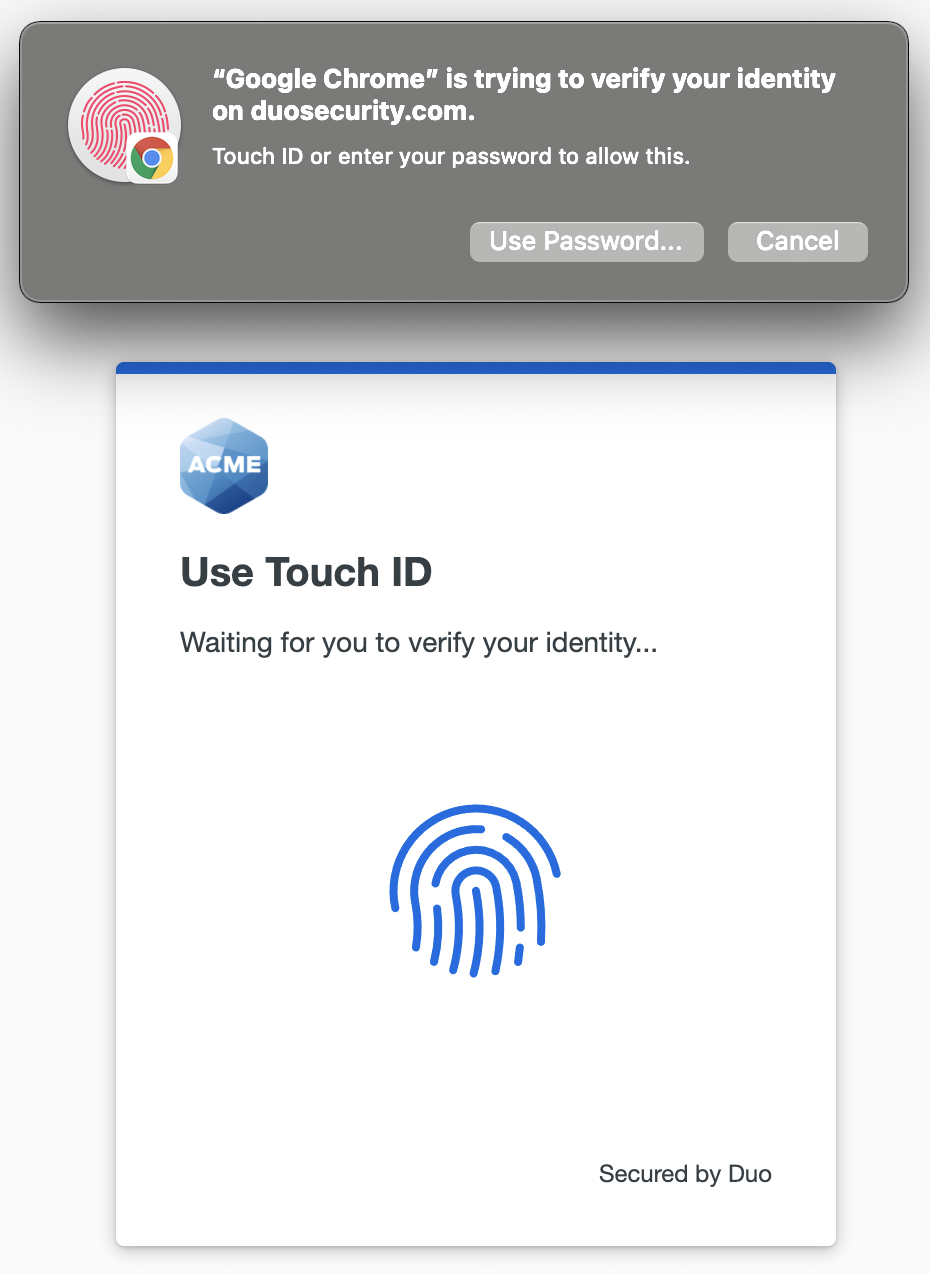
When you receive confirmation that you've registered the passwordless authenticator successfully, you can continue on to the application.
The next time you log into the SSO application from that access device, you will enter your email and then interact with your registered authenticator instead of typing in your password.
Duo Push Authenticator
Duo Passwordless uses a "known device" browser cookie to enforce strong channel binding. Duo sets this browser cookie after a user completes a successful 2FA authentication on a specific device. We then check for that browser cookie in later authentication attempts for that user. This approach ensures that only previously authorized devices can use a passwordless push, preventing scenarios where an unauthorized user could log in with just an email address and a push.
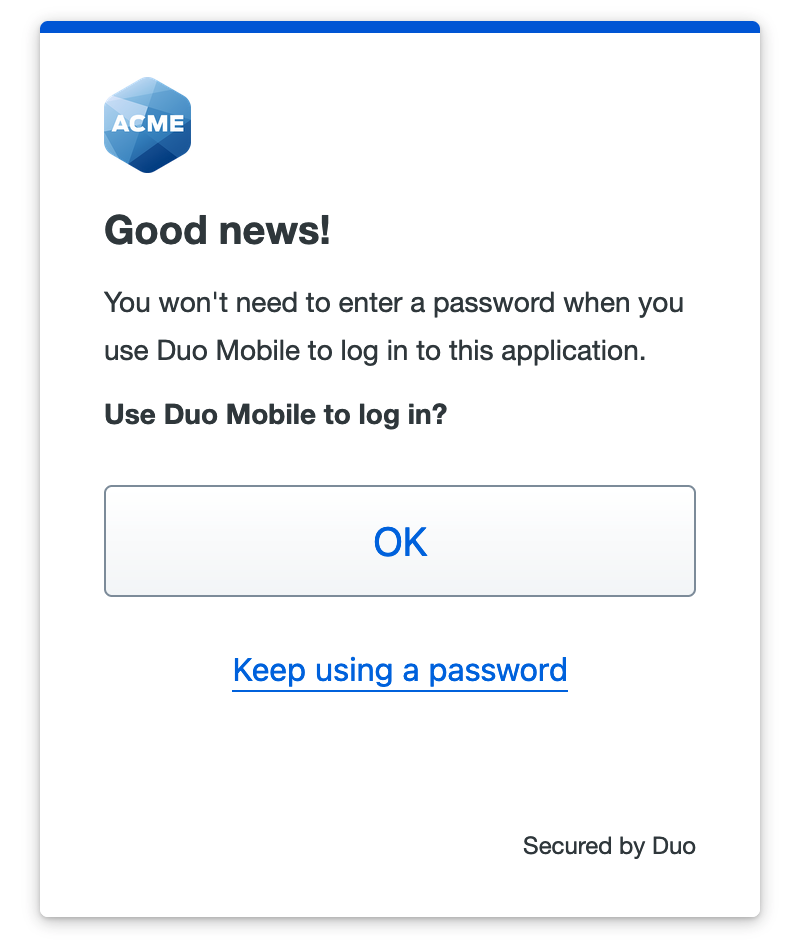
If you previously activated Duo Mobile for two-factor authentication and do not have an existing passwordless roaming or platform authenticator enrolled then your existing Duo Push device is automatically enabled as an authenticator for Duo Passwordless when you log into the SSO application with your username and password and use Duo Push to perform Duo two-factor authentication.
The next time you log into that application from the same access device and browser you'll see a notification that you can now use Duo Mobile to log in without a password.
When you opt to use Duo Push for passwordless login for the first time you will be shown a six-digit verification code in the Duo browser prompt. Enter this code into the Duo Mobile login request on your Android or iOS device.
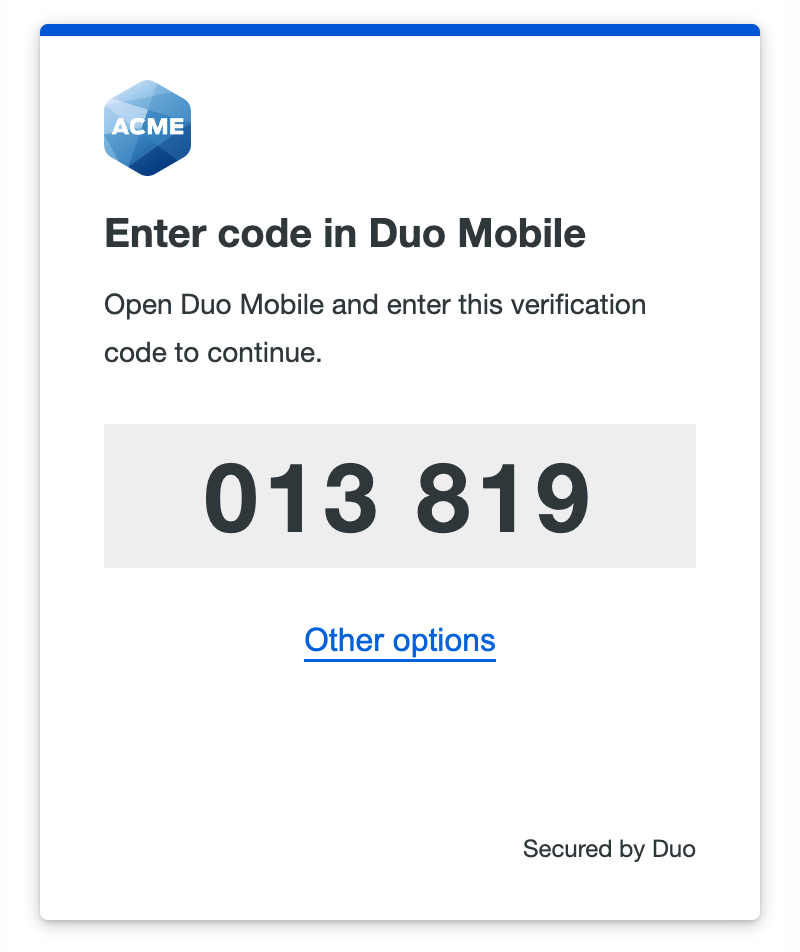
Next, you'll need to perform an additional verification step when approving the push request. After you enter the code from the browser prompt in Duo Mobile and tap Verify on the authentication request, perform Face ID verification or scan your enrolled finger at the Touch ID or Android fingerprint prompt to confirm the authentication approval. If you are unable to authenticate with a biometric factor you can fall back to your device's PIN or passcode.

When you successfully approve the Duo Push authentication with verification code and device biometric or PIN/passcode approval, you have the opportunity to remember your current browser. If you remember the browser now then next time you use Duo Push as the passwordless authenticator from that browser you will not need to enter the six-digit verification code; just complete device biometric or PIN/passcode verification while approving the Duo Push request. If you don't remember the browser, future passwordless Duo Push authentication requests will require both the six-digit verification code from the Duo Universal Prompt and device verification to approve the login request.
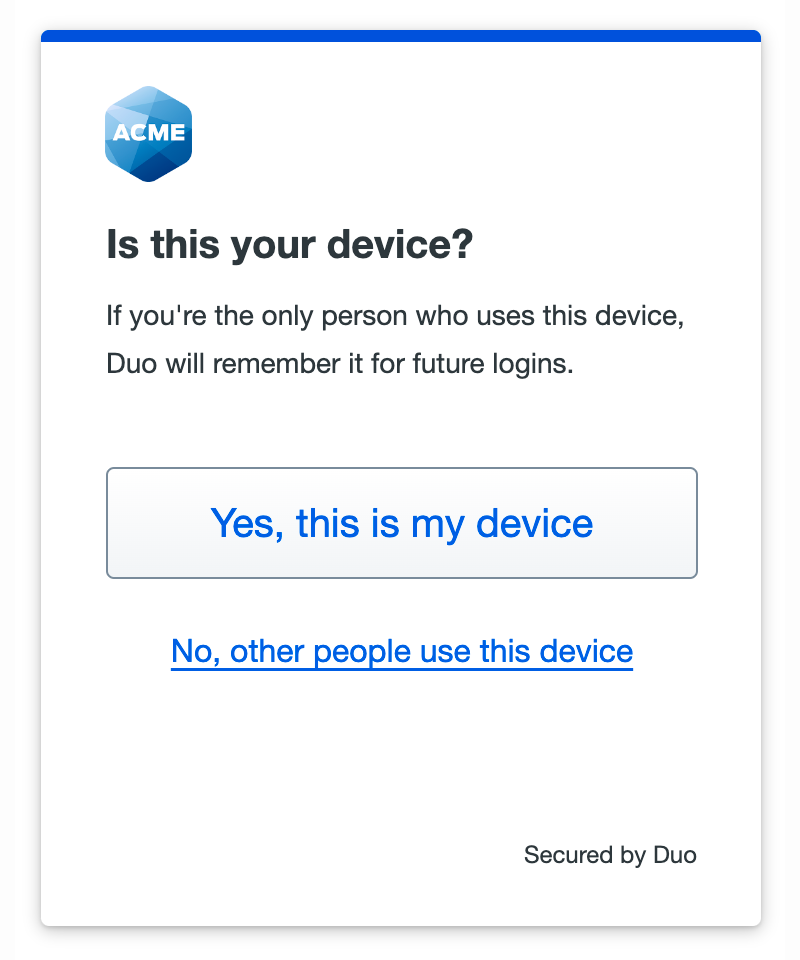
Note that if you have platform authenticators enabled in your policy and your access device has a WebAuthn platform authenticator available (like Touch ID), or if you have enabled WebAuthn roaming authenticators in your policy, then Duo prefers these more secure passkey methods over Duo Push. You'll see the beginning of the WebAuthn device setup process for Duo Passwordless.
After you complete registration of your passkey as a passwordless authenticator your existing Duo Push device is also enabled as a fallback authenticator for Duo Passwordless in that browser for that access device (but you won't see a message saying that you can now use Duo Mobile to log in to the application).
When you log in again to the application, Duo Passwordless selects your enrolled platform or roaming authenticator by default, but you can cancel the request in progress and click Show other options to select Duo Push for this passwordless application login.
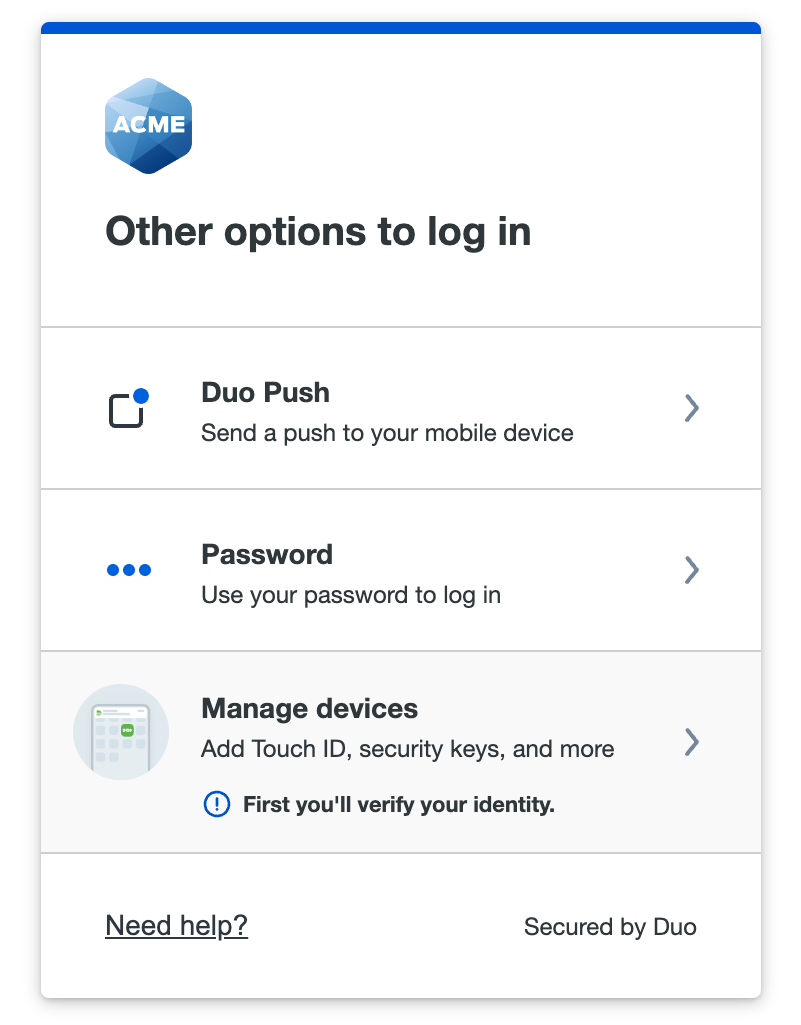
If you clear the "known-device" cookie from your access device's browser, log in from an Incognito or private browsing session that does not share or store cookies, use a different browser on the same access device, or switch to a different access device, then Duo Push won't be offered for passwordless authentication. You'll need to provide your password and approve a two-factor authentication request to repeat the process of enabling Duo Push for Passwordless for the browser you're now using.
Device Verification with Duo Mobile
When the effective trusted devices policy requires a trust check, and you log in from a mobile device, Duo prompts you to verify your device identity with Duo Mobile. Tap Open Duo Mobile, which opens the Duo Mobile app on your phone for the device check. After device verification succeeds you can then use a platform or roaming authenticator or Duo Push to log in to the application.
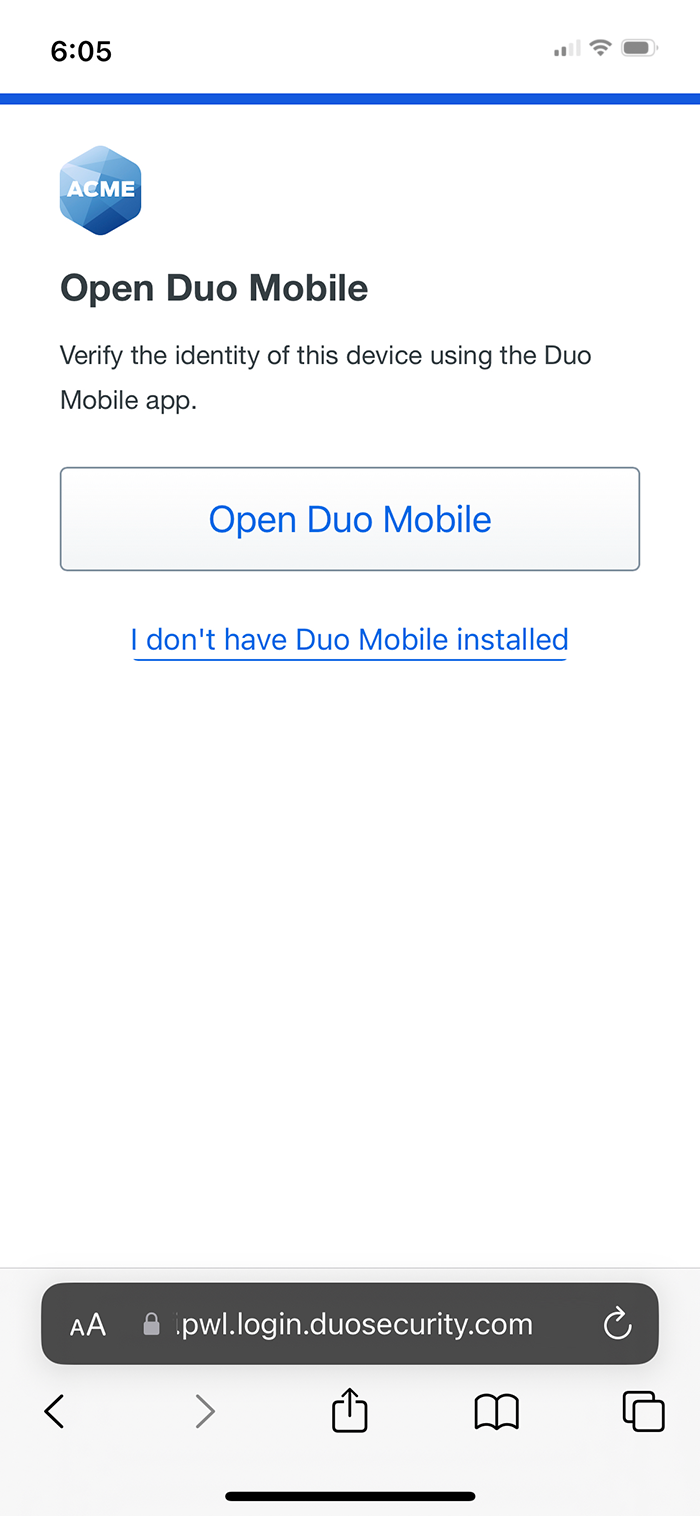
If you do not have Duo Mobile on your mobile device you can tap I don't have Duo Mobile installed. This lets you complete Duo Passwordless authentication, but if your organization policy blocks access from unverified devices you cannot access the application.

If you do have Duo Mobile installed but not activated for Duo Push then you can tap My account isn't activated to skip directly to Duo Passwordless authentication, but may still be blocked by the trusted device check.
Grant Access to Users
If you did not already grant user access to the Duo users you want to use this application be sure to do that before inviting or requiring them to log in with Duo.
Manage Passwordless Authenticators
You can view and delete a user's registered platform and roaming passwordless authenticators from the Duo Admin Panel.
-
Log in to the Duo Admin Panel and search for the user from the search bar at the top of the page. You can also navigate to Users → Users in the left sidebar and then select a user by clicking their username.
-
Scroll down to the Passkeys table on the user's details page. Any passwordless authenticators registered by the user do not contain "(2fa only)" in the registration information.
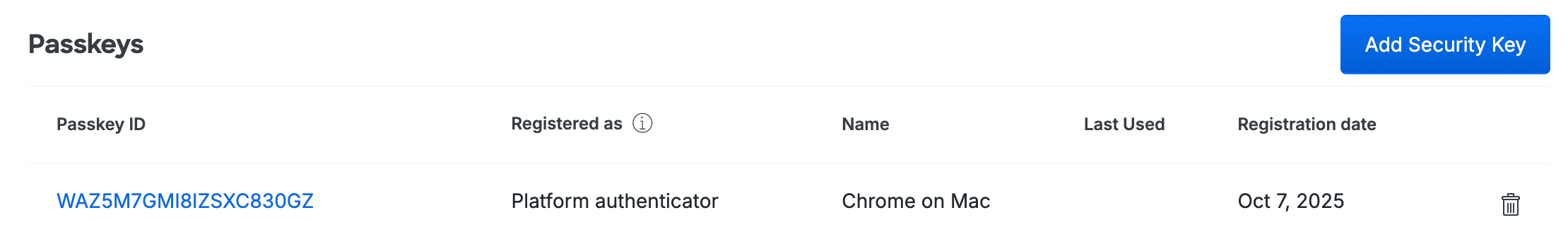
-
To delete a user's passwordless authenticator, click the trash icon to the right of the device's information in the table.
When you delete the authenticator, the user will need to use a different registered passwordless authenticator to log in to applications. If no more passwordless authenticators remain registered for the user they will log in with their password, or Duo Push as a passwordless authenticator enabled in the access device browser if they have a phone with Duo Mobile activated for 2FA.
Because Duo Push as a passwordless authenticator is enabled at the access device via browser cookie, Duo Push authenticators aren't shown as a passwordless authenticator when viewing a user's properties. Removing the user's Android or iOS device which has Duo Mobile activated from the 2FA "Phones" section effectively removes it as a possible Duo Push passwordless authenticator as well.
To view and manage all your users' registered passwordless authenticators in the Admin Panel, navigate to Devices → Passkeys. See Manage Passkeys for more information about this page and actions you can take.
Tracking Passwordless Adoption
To track passwordless adoption, see the Passwordless Deployment report.
Passwordless Reporting
View authentication reporting for passwordless logins in the Authentication Log. The "Authentication Method" information shown will include "passwordless" when a passkey or Duo Push passwordless authentication method was used.
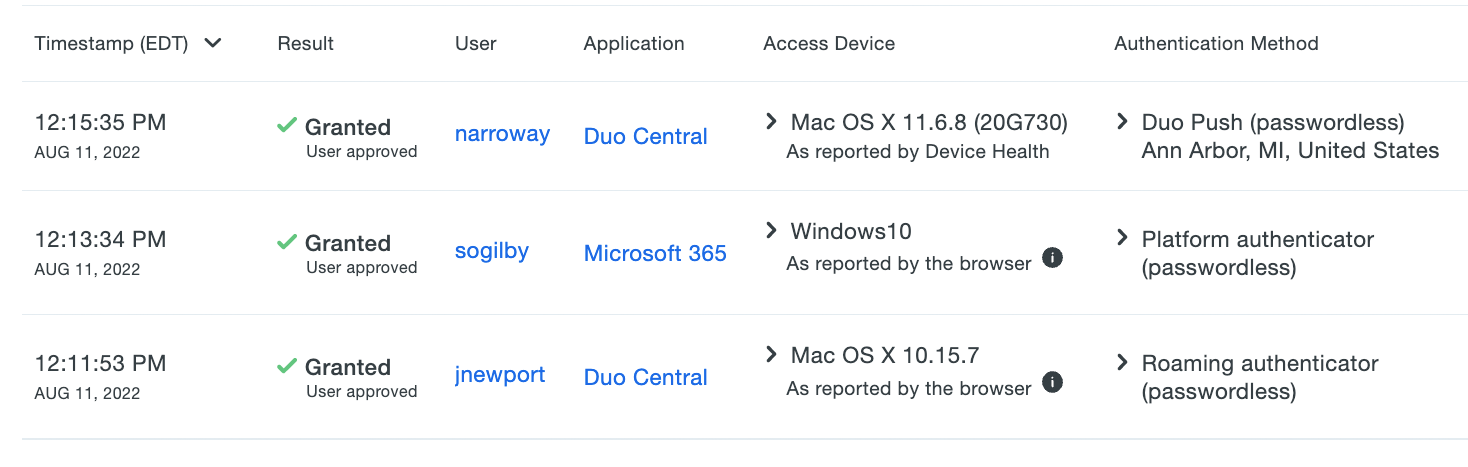
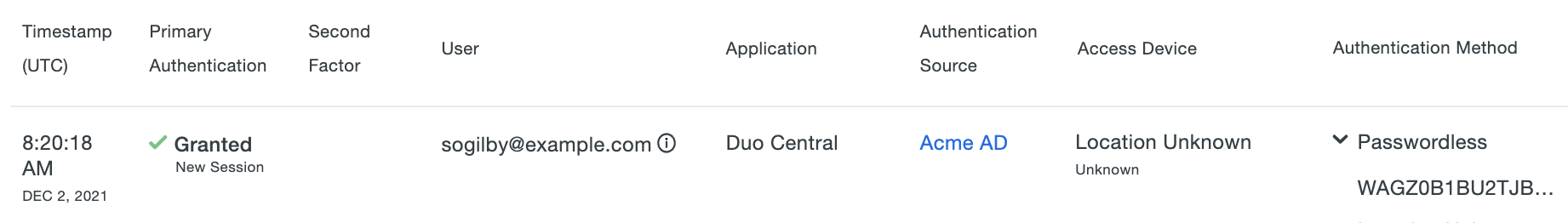
Passwordless access of OIDC and SAML applications is also found in the Single Sign-On Log, as a new primary authentication session with no second factor listed and "Passwordless" plus the passkey credential's key or the phone ID value if Duo push was used in the expanded information view for the "Authentication Method".
Troubleshooting
Need some help? Take a look at our passwordless Knowledge Base articles or Community discussions. For further assistance, contact Support.
