Duo Administration - Self-Service Portal
Last updated:
Overview
Duo's self-service portal saves time for both administrators and end users by eliminating the need to contact IT staff for authentication device changes. Your users can add, edit, and remove authentication methods from the Duo traditional prompt or Universal Prompt while logging in to protected applications.
Self-Service Portal Availability
The self-service portal feature is part of the Duo Premier, Duo Advantage, and Duo Essentials plans.
The self-service portal is an available option for Duo web-based applications, select VPN applications, Duo Single Sign-On and Duo Access Gateway applications, browser-based Microsoft applications, and any Duo applications that offer inline self-enrollment and authentication prompt via the browser.
Enabling the Self-Service Portal
Role required: Owner, Administrator, or Application Manager.
Duo's self-service portal is enabled on a per-application basis. To enable self-service for one of your applications:
-
Log into the Duo Admin Panel and navigate to Applications → Applications in the left sidebar.
-
Click an application's name to open that application's properties page.
-
The self-service portal configuration option is present under "Settings" if the application supports the self-service portal feature. Check the Let users manage their devices box to enable self-service for that application.
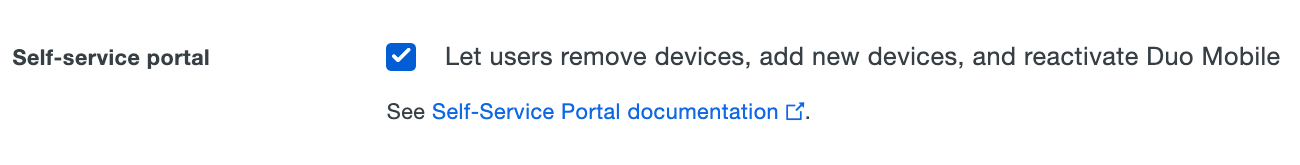
Click the Save button at the bottom of the application's properties page.
If you enable self-service for an application, consider disabling phone callback as an authentication method or applying some additional policy controls to the application, such as restricting User Location to your expected countries, or reducing your max credits per action telephony setting to only the credit amount needed for phone calls to your users' expected locations to avoid telephony misuse via the self-service portal.
Customize the Self-Service Portal
Role required: Owner or Administrator
You can apply a separate policy to the self-service portal within the Universal Prompt and Duo Central device management. This allows for stricter access while maintaining a different policy for normal application access. This policy will be applied anywhere the self-service portal is enabled. Access to the self-service portal is still enabled on a per-application basis.
To enable the self-service portal policy:
-
Log into the Duo Admin Panel and navigate to Policies → Self-Service Portal in the left sidebar.
-
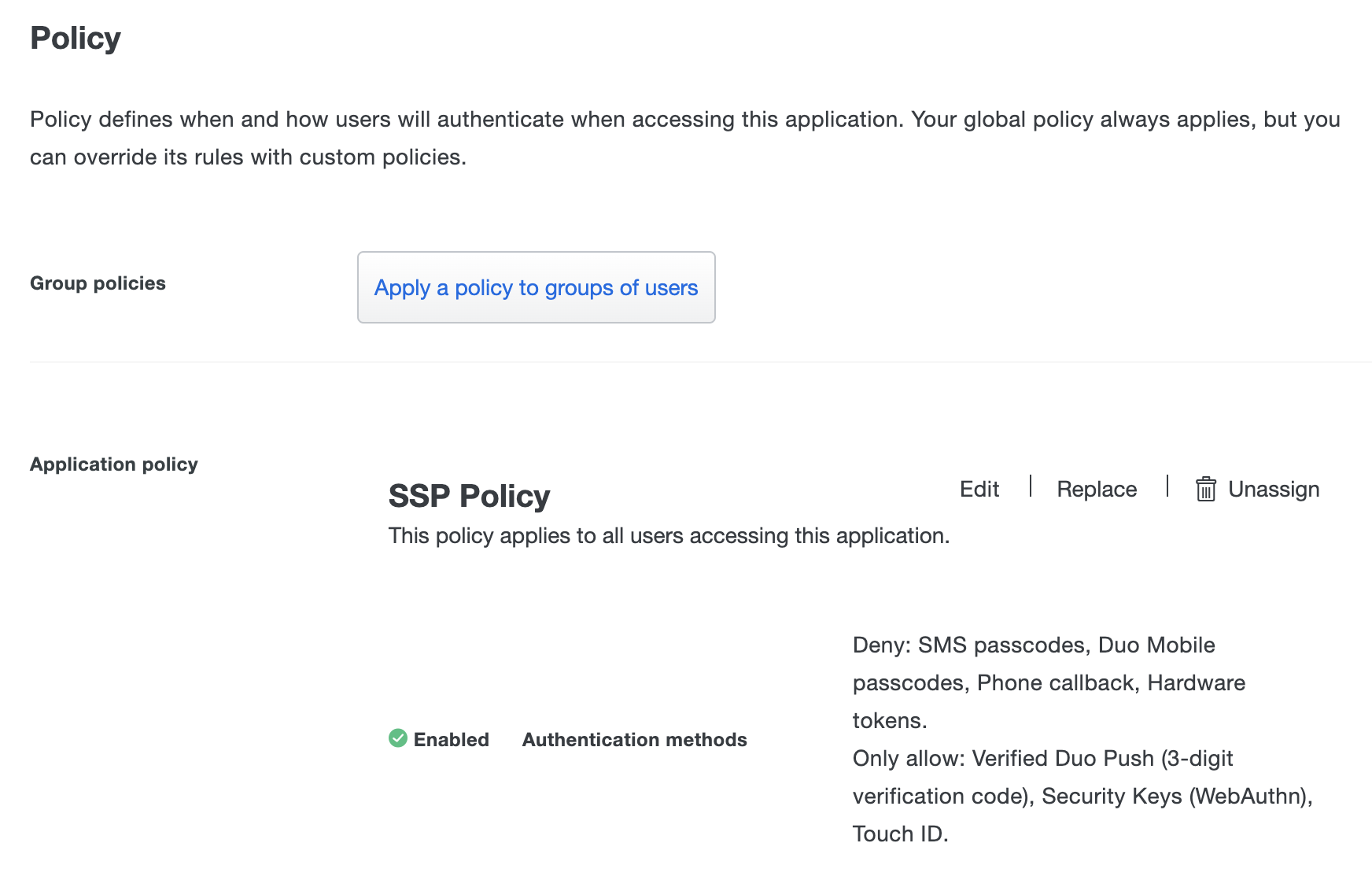
Under "Policy" click on Apply a policy to all users to apply a self-service portal policy for all users. Follow the policy documentation on how to create and apply a custom application policy.
Duo recommends only allowing more-secure authentication methods. We recommend only enabling the following authentication methods:
- Verified Duo Push
- WebAuthn (platform and roaming authenticators)
Learn more about the recommended settings for the self-service portal policy.
-
Scroll down to "Settings". These settings are a portion of the same settings seen in a 2FA application's settings. See application options for more information. Once you have configured the settings, click Save.
-
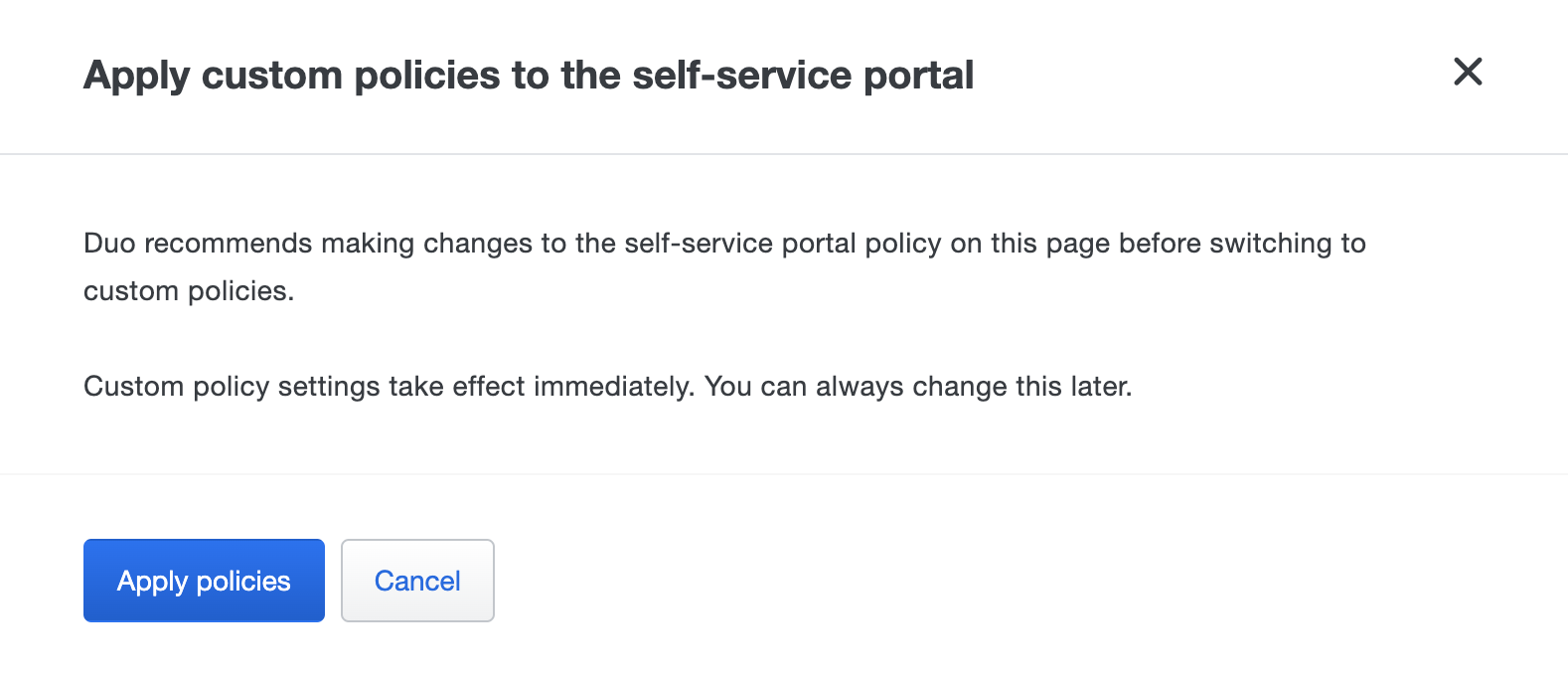
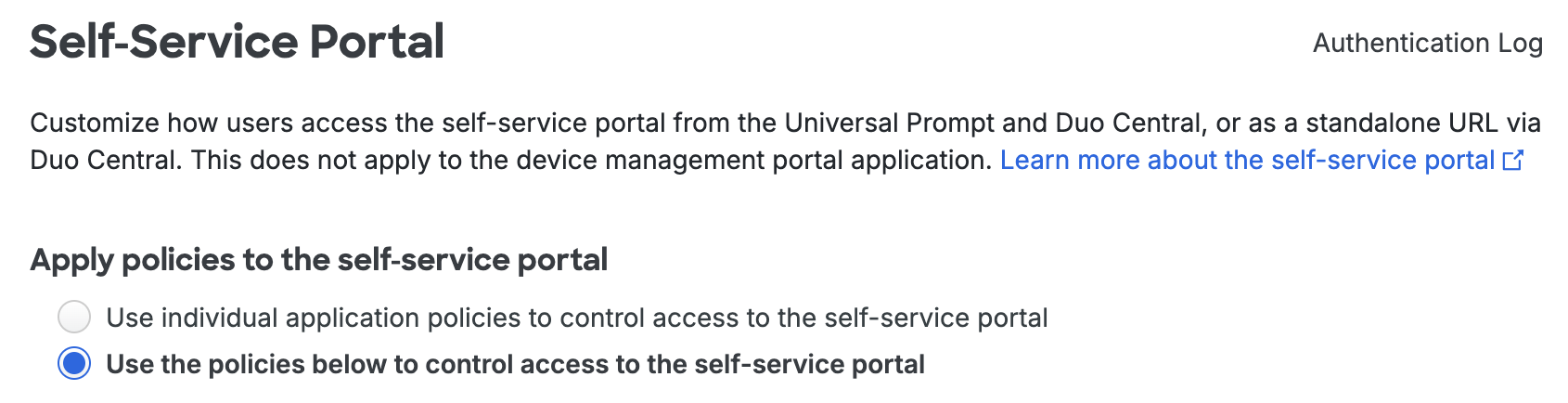
If self-service portal policy isn't already enabled, select the radio button next to Use the policies below to control access to the self-service portal at the top of the page.
-
Click Apply policies. The self-service portal page shows the policies enabled.
Please note the following restrictions:
- Remembered devices is disabled on the self-service portal as users should always have to authenticate to manage their devices. Even if you apply a remembered devices policy to the self-service portal, it will not take effect.
- Users in bypass status will be unable to access the self-service portal.
- Any policy that could bypass authentication will be ignored and all users will be required to authenticate (or blocked if specified in policy). These include:
- Remembered devices
- Authorized networks
- User location (you can use this policy to block use of the self-service portal, but not to bypass it)
- The self-service portal policy applies to access into the self-service portal but once a user has gained access, the authentication methods they can enroll are determined by the policy of the originating protected application. For example:
- If a user accesses the self-service portal while logging into the Office 365 Application, the authentication methods they can enroll are determined by the enabled authentication methods in the Office 365 application’s policy.
- Duo Desktop as an authentication method cannot be used to access the self-service portal. Even if you apply a policy that enables Duo Desktop authentication to the self-service portal, it will not take effect. Make sure to enable an additional authentication method when applying a policy that enables Duo Desktop authentication.
Once enabled, you can view when users access the self-service portal in the authentication logs.
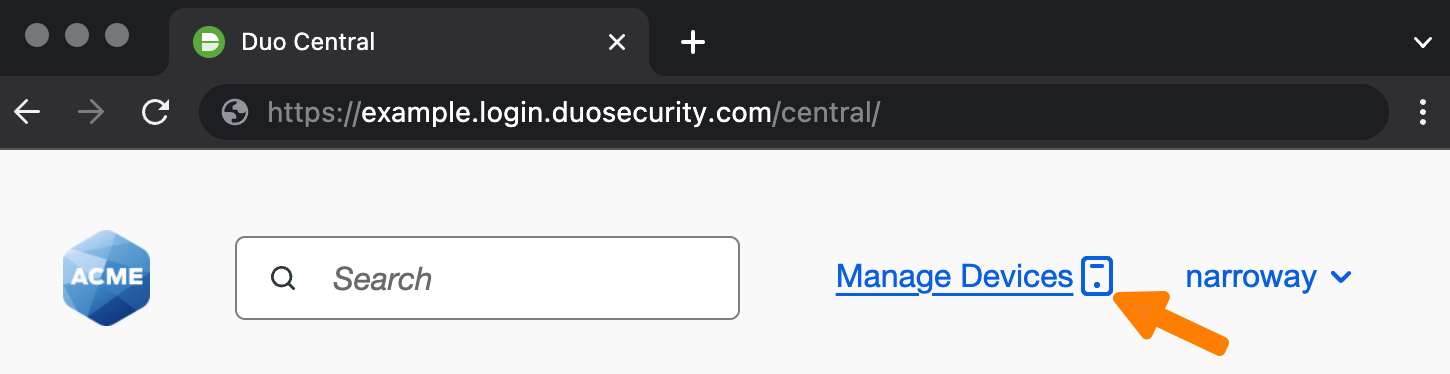
Duo Central Device Management
The self-service portal options for Duo Central, the application access portal for Duo Single Sign-On, go beyond device management during login, and provide access to the device management portal for users after completing primary and secondary Duo authentication from a convenient "Manage Devices" link in Duo Central, or from a standalone device management URL that can be provided directly to users.
Learn more about configuring Duo Central with self-service device management.
Experience for Users
Universal Prompt
In the Universal Prompt, users can register Duo Push for a new smartphone or tablet, add WebAuthn methods like Touch ID on a Mac or security keys from supported browsers, or add a mobile or landline phone for SMS and phone call verification. They can also rename or remove an existing Duo Push, security key, Touch ID, or phone device. Users may remove (but not add) hardware tokens from the device management portal as well. When self service is enabled for applications using the Universal Prompt, it also offers users a streamlined process for adding additional passkey authenticators during two-factor and passwordless authentication when the device they initially registered isn’t available.
After passing primary authentication, users click the Other options link shown on the Duo authentication screen to return to the device list. The Manage devices option is at the bottom of the device list. Duo authentication with a previously added authentication method or a bypass code provided by a Duo administrator is required to gain access to device management.
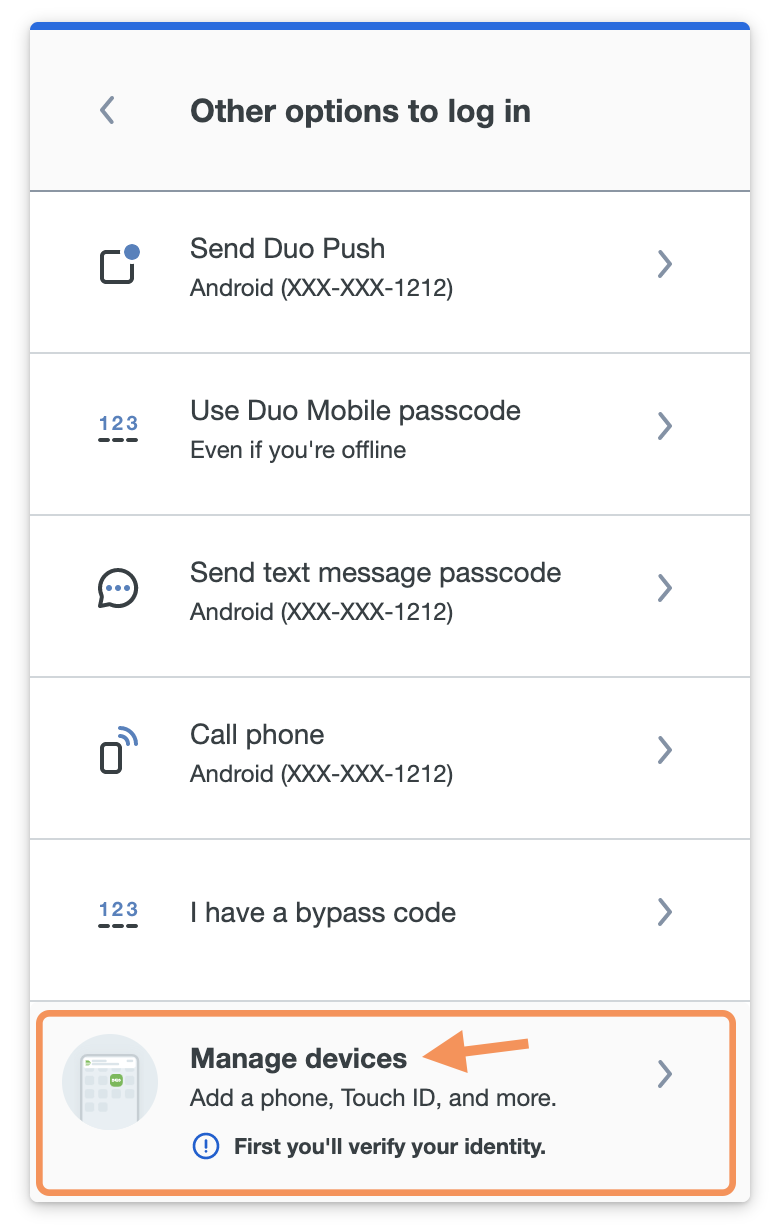
Users can rename or remove existing devices with the Edit options, or use Add a device to register another authentication device.
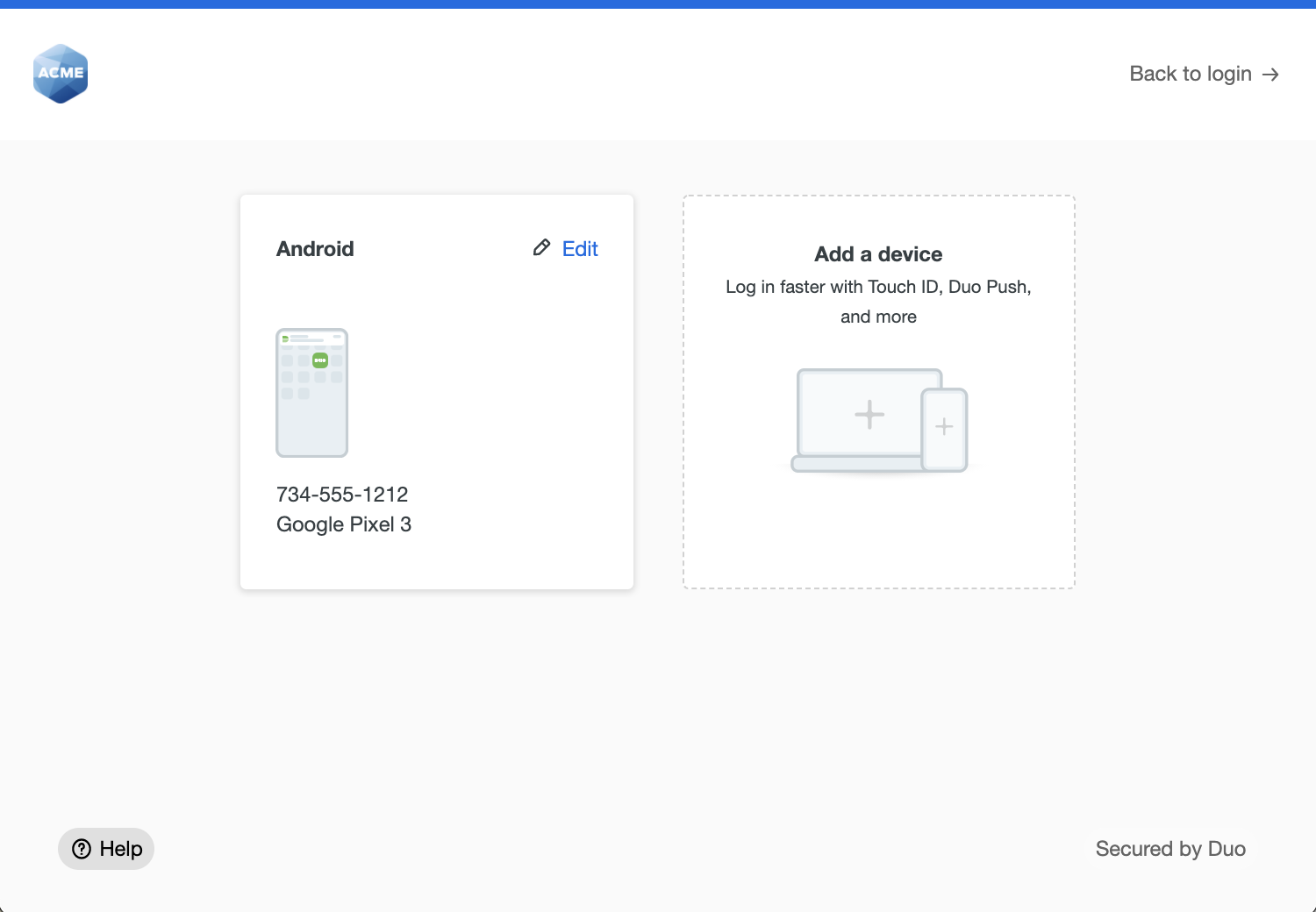
For additional information about device management from the Universal Prompt, see Add or Manage Devices After Enrollment in the Duo user guide.
Traditional Prompt
The iframe-based traditional Duo Prompt reached its end of support for most applications on March 30, 2024. Customers must migrate to a supported Duo application with Universal Prompt for continued support from Duo.
Learn more about the end-of-life of the traditional Duo Prompt and options for migrating applications to Universal Prompt and review the Duo End of Sale, Last Date of Support, and End of Life Policy.
With self-service enabled your users can enroll a new mobile phone, tablet, landline, security key, or Touch ID on a Mac. They can also rename an existing phone or tablet device, activate Duo Mobile, set a phone or tablet device as the default for Duo Push and phone call, or remove an existing device. Users may remove (but not add) hardware tokens from the device management portal as well.
After passing primary authentication, users see Add a New Device and My Settings & Devices links on the Duo two-factor authentication page. Duo authentication is required for access to the self-service pages.
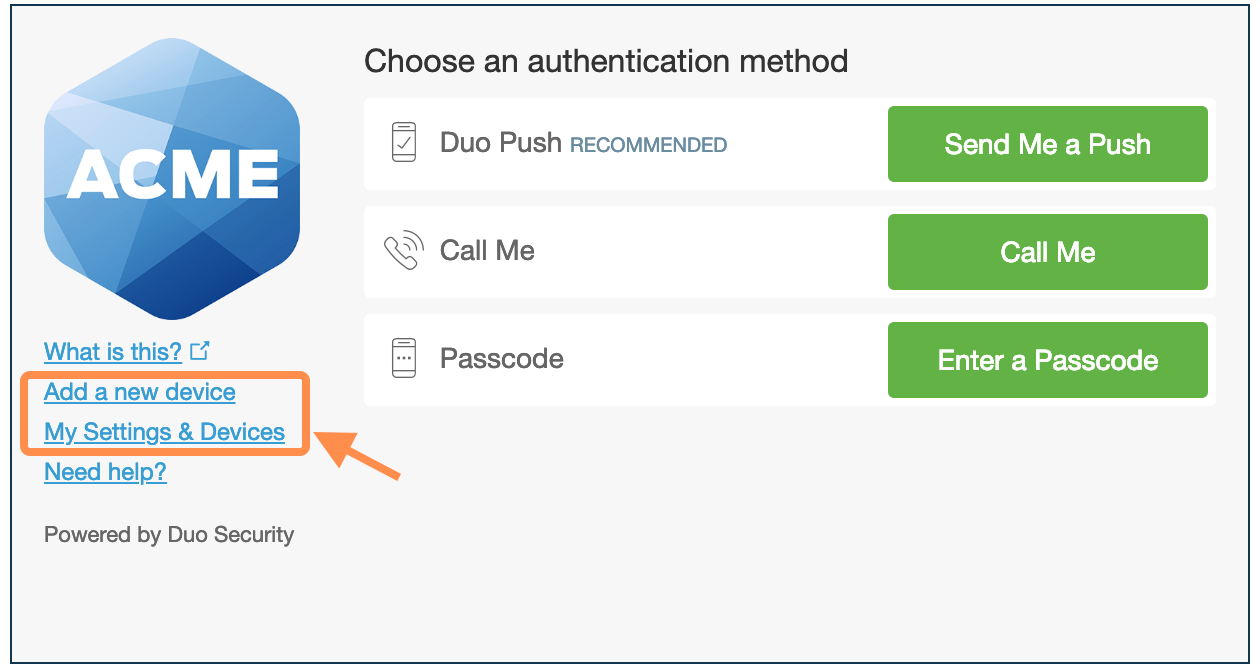
Your end users can quickly add another authentication device with the Add a New Device utility, while clicking My Settings & Devices prompts the user to complete two-factor authentication, then shows the device management portal.
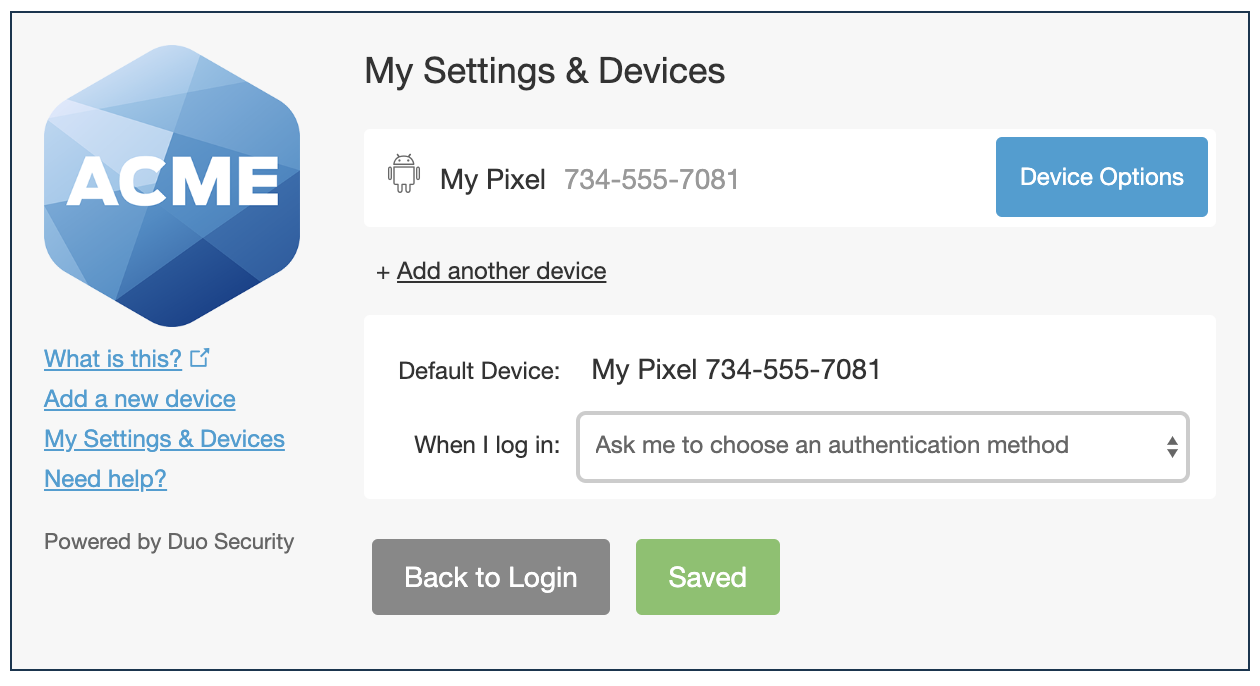
For additional information about using the self-service portal in the traditional Duo Prompt, see Add a New Device and My Settings & Devices in the Duo user guide.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
