Duo Passport
Last updated:
Overview
Simplify application access and reduce logon fatigue with Duo Passport. Share remembered device sessions between your applications when accessed from a browser or from a desktop client with Duo Passport, Duo Desktop, and a remembered devices policy applied to applications. Duo Passport is supported with any Universal Prompt integration but enhanced with Duo SSO for primary and MFA sessions.
When you use Duo Passport with Duo Authentication for Windows Logon and Duo Single Sign-On, your users enjoy an enhanced experience where they will sign in to Windows with Duo and then seamlessly access browser and desktop applications without needing to re-enter their service credentials or repeat Duo two-factor authentication (2FA).
Duo Passport is part of the Duo Premier and Duo Advantage plans.
How Does it Work?
Without Duo Passport, Duo stores the trusted session information used by Duo authentication in apps accessed in a browser and Duo Authentication for Windows Logon locally on a user's access device, but this session information isn't shared between the browser, Duo for Windows Logon, and other applications installed on that computer that may also authenticate with Duo. This means users have to re-enter their credentials and possibly repeat Duo two-factor authentication for each browser and desktop application.
Duo Passport uses Duo Desktop installed and running on the user's computer to share the distinct Duo session information between browsers used to access applications, desktop clients, and Duo for Windows Logon. If a user logs into a web application from a browser, and opts to remember their access device during Duo 2FA, that trust session is accessible to the user's desktop applications as well. A desktop client application that accesses web services protected by Duo is able to verify the trusted device session established by the browser and skip repeated authentication.
Duo Passport leverages these Duo Desktop features:
- Automatic Registration - Duo Desktop completes initial device registration during two-factor authentication in the Duo Universal Prompt. If the device is not already registered, automatic registration occurs when a user accesses a Duo-protected application and successfully completes multi-factor authentication (MFA). Duo Desktop generates a cryptographic keypair, stores the private key on the access device, and sends the public key to Duo to store associated with the user, account and access device.
If any of those three attributes change, for example, if someone else uses the same access device to log into an application owned by the same Duo account, the registration process will repeat. This allows for many-to-many scenarios where multiple users share the same device, a single user can use multiple devices, and any or all of them can register with multiple Duo accounts.
- Payload Signing - The private key generated during device registration cryptographically signs the data payloads sent by Duo Desktop. The Duo cloud service verifies that signature using the public key sent at the time of registration. If the payload’s signature is invalid, either because it did not come from a legitimate DHA or it has been tampered with, Duo blocks the access attempt. By verifying this signature, Duo's services can have high confidence that the same computer generated two given health reports. Duo then looks up the remembered record for the computer and user to see if they have authenticated on the same device recently and permits skipping second-factor authentication.
Duo Passport for Duo Authentication for Windows Logon works in a similar way. Duo Desktop isn't able to generate a health report because it's not yet running when the user logs into Windows with Duo, so instead it uses a shared Duo cryptography system service to sign a request to Duo's service. By verifying this signature, Duo can create a remembered user record for the computer and user. When a user logs into their Windows operating system using Duo Authentication for Windows Logon, Duo creates a remembered user record. Subsequent Duo authentications from a browser or other desktop applications on that computer use the same remembered user record to skip secondary authentication.
(Beta) RDP Login Establishes Passport Sessions: Duo Authentication for Windows Logon (5.2.0 or greater) installed on a remote machine can create Passport sessions. The remote machine requires Duo Desktop, and all other Passport requirements apply. See Duo Knowledge Base article 9561 for more details.
Duo Passport Session Token Theft Protection significantly reduces the risk of session hijacking by minimizing the use of cookies. Instead of setting a cookie when detecting a Passport session for authentication, it submits the Passport session directly. Passport’s mechanism for identifying a user's sessions via signatures from Duo Desktop’s hardware backed keys eliminates the need for a remember-me cookie altogether.
Duo Passport complements existing Trusted Endpoints and Duo Desktop Device Registration policy configurations, but neither is required to use Passport.
Duo Passport Experience for Users
Duo Desktop and Remembered Devices
When you apply a policy which enables remembered devices for all browser applications, and install Duo Desktop on your Windows and macOS clients, remembered device sessions established during successful Duo two-factor authentication are shared between browsers accessing Duo-protected apps and desktop client applications accessing Duo-protected applications. The Duo-protected applications can be 2FA-only apps, or Duo Single Sign-On apps.
Example: A user logs into a ticketing system in their web browser, completes Duo authentication, and opts to remembers their access device. When they log into other Duo-protected web applications, like a Duo-protected email service from a mail client application, they are not prompted again for two-factor authentication.
Duo Desktop, Remembered Devices, and Duo Authentication for Windows Logon
Streamline Duo authentication even more with Duo Authentication for Windows Logon. When users sign in to Windows using Duo, that trust session is accessible to browsers and desktop applications.
Example: A user begins their day by logging into Windows. When they log into other Duo-protected web applications, like a ticketing system in their browser or a mail service using a standalone email client, they are not prompted again for two-factor authentication.
The trust session created persists until it expires per the duration configured in the effective remembered devices policy. Logging out of Windows, restarting the machine, or quitting the Duo Desktop app will terminate the Passport session as well.
Passport Enhances your Single Sign-On Experience
When Duo Passport, Duo Desktop, and Duo Authentication for Windows Logon come together, users can access Duo Single Sign-On applications without entering their usernames or passwords.
Example: A user begins their day by logging into Windows with Duo Authentication for Windows Logon. When they access a Duo Single Sign-On application, they do not need to enter a username and password because SSO can use the existing secure session. Users are not prompted again for two-factor authentication when accessing SSO and 2FA-only apps in browsers or desktop applications as long as the Passport session remains valid.
Prerequisites
- Windows access devices must support Trusted Platform Module (TPM) 2.0.
- MacOS access devices must support Secure Enclave.
Requirements
- A Duo Premier or Duo Advantage plan.
- Duo Desktop 6.6.0/6.6.0.0 or later installed on Windows and macOS clients.
- Note: Passport doesn’t require configuring any Duo Desktop policy options. If your existing policies already require Duo Desktop or device registration, you do not need to change these policies.
- Duo Passport support is not available yet for Linux clients.
- Optional: Duo Authentication for Windows Logon 4.3.1 or later installed on Windows clients. Required if you want to share trusted device sessions between Duo for Windows Logon and web applications.
- Shared trusted device sessions between Duo for MacOS Logon and web applications is not supported. - Supported Duo applications which feature Duo Universal Prompt.
- SSO isn’t required for Passport, but to create a trust session that handles primary and secondary login to Duo Single Sign-On applications you must have Duo SSO authentication configured to use either Duo or Microsoft Active Directory (AD) as the authentication source.
Duo Desktop authentication cannot be used as a factor for Duo Passport. Duo Desktop authentication will not start a Passport session and users will need to authenticate with Duo Desktop each time.
Browser and Application Support
The browser or client application communicating with Duo Desktop must be a signed executable, published by one of the following trusted vendors. Please contact Duo Support to request addition of your organization's preferred applications and vendors to this default list.
Windows Application Vendors
- Adobe Inc.
- Brave Software, Inc.
- Cisco Systems, Inc.
- Citrix Systems, Inc.
- Duo Security LLC
- Google LLC
- Microsoft Corporation
- Mozilla Corporation
- Opera Norway AS
- Palo Alto Networks
- Salesforce, Inc.
- Tableau Software LLC
- THE BROWSER COMPANY OF NEW YORK INC.
- Vivaldi Technologies AS
- Zscaler, Inc.
macOS Application Vendors
- Adobe Inc.
- Apple Software
- Brave Software, Inc.
- Cisco Systems, Inc.
- Citrix Systems, Inc.
- DuckDuckGo
- Duo Security LLC
- Google LLC
- JAMF Software
- Marvasol, Inc DBA LastPass
- Microsoft Corporation
- Mozilla Corporation
- Opera Norway AS
- Palo Alto Networks
- Salesforce, Inc
- Tableau Software LLC
- The Browser Company of New York Inc.
- Vivaldi Technologies AS
- Zscaler, Inc.
Install Duo Desktop
Duo Passport requires Duo Desktop version 6.6.0 or later installed on your Windows clients or 6.6.0.0 or later installed on your macOS clients. You can have users self-install Duo Desktop during Duo authentication in a browser or via emailed installer links, or push the install to managed Windows clients with your existing software deployment tools.
Please follow the steps for your chosen deployment method in the Duo Desktop installation instructions.
Remembered Devices Policy
Configure and apply a remembered devices policy to the applications you want to use Duo Passport, with these settings enabled:
-
Remember devices for browser-based applications with risk-based protection or Remember devices for browser-based applications set to your desired Duo session duration.
- If you choose Remember devices for browser-based applications do not select Remember devices on a per-application basis. While Duo Passport is compatible with the Remember devices on a per-application basis option, selecting it limits Passport’s functionality. It will prevent sessions initiated by one application from being shared with other applications, which includes sessions initiated by Windows Logon.
You can apply your remembered devices policy to an application or as an application-group policy for an application. If you choose to apply as an application-group group policy, note the groups you chose so you can make a matching group selection when you enable Passport.
Here's how you can create a new "Duo Passport" policy with the necessary remembered devices settings and apply it to a pilot group for an application:
-
Log on to the Duo Admin Panel as an administrator with the Owner or Administrator admin role.
-
Navigate to Policies → Policies and click + Add Policy. The policy editor launches with an empty policy.
-
Enter a descriptive Policy Name on the "Name & details" tab ("Duo Passport" in this example), and then click the Remembered devices policy item on the left.
-
Add this policy section and select the Remember devices for browser-based applications with risk-based protection or Remember devices for browser-based applications setting.
-
Enter your desired number of hours or days you want a remembered device's Duo Passport session to last.
-
For versions of Windows Logon 4.3.1 and earlier, if you plan to extend Passport to Duo for Windows Logon, also check the box which enables Remember devices for Windows Logon. Enter the same number of hours or days you specified in step 6 in the Allow users to remember their device for box.
For Windows Logon version 4.3.16 and newer, you can skip this step. In Windows Logon 4.3.16+, the Passport signature is sent for every local authentication regardless of whether local remembered devices is enabled or checked.
-
Click the Save button to save the settings and create the new policy.
-
Navigate to Applications → Applications or use the search bar at the top of the Admin Panel to find the application to which you want to apply your new Duo Passport policy. Open the details page for that application.
-
Scroll down on the application's details page to the "Application-Group policies" section and click Apply a policy to groups of users to assign the new Duo Passport policy to a test group.
-
Select the Duo Passport policy you just created from the Policy drop-down list.
-
Start typing in the pilot group's name in the Groups field and select it from the suggested names.
-
Click the Apply Policy button. The application page shows the new group policy assignment.

For more information about creating and applying application-group policies, see the Duo Policy documentation.
Enable Passport
These example steps enable Duo Passport for your pilot group:
-
In the Duo Admin Panel navigate to Policies → Passport.
-
In the "Enable Passport" section of the page select Enable Passport for only certain groups. Start typing in the pilot group's name in the Groups to include field and select it from the suggested groups.
-
Click Save.

Expand your Passport Enablement
When you're ready to extend Passport to more users, you'll return to this page where you can select additional groups to enable. If you're ready for all users to experience Passport when they access eligible applications with supported devices, select Enable Passport for all users.
Click Save after making any changes to your enablement selection.
Device Registration for Passport
When Passport-enabled users sign in with Duo, Duo Desktop performs automatic device registration when possible. That is, Duo Desktop will attempt to generate a key pair, register the public key with Duo, and use the key to sign further reports sent to Duo. If registration fails, authentication proceeds as usual with no error shown to the user, but the user will not experience shared Passport sessions between browser and desktop apps. The access device lacking TPM or Secure Enclave support or an attempt to register a device which is already registered are possible reasons why devices may not complete automatic device registration.
You can review your registered devices or selectively remove devices by navigating to Devices → Duo Desktop Device Registration in the Duo Admin Panel. You may wish to remove an endpoint if you want to require a user’s Duo Desktop app to generate and register a new set of signing keys for their device on their next successful authentication.
Learn more about registered devices in the Endpoint documentation.
Verify Passport with Browser and Desktop Applications
Test your Passport configuration from a Windows or macOS device.
-
Access some Duo-protected web application using a browser which shows the Duo Universal Prompt and has a remembered devices policy for all browser-based applications applied. Duo Desktop registers your device during this first authentication.
-
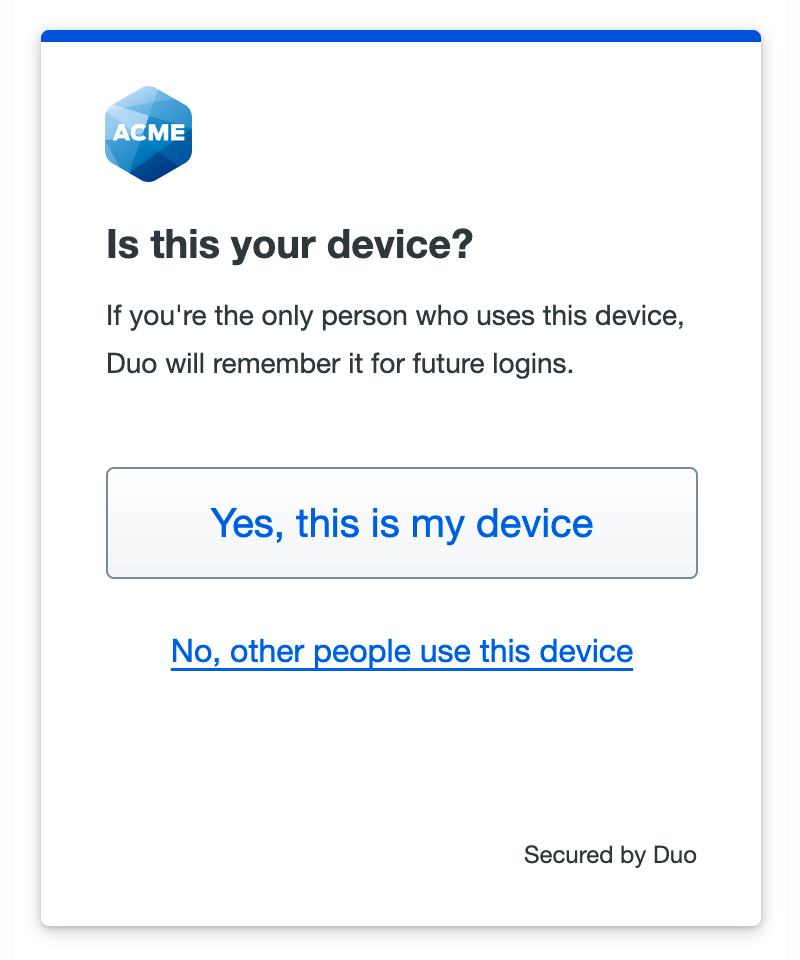
When you perform Duo authentication be sure to create a remembered devices session by choosing Yes, this is my device in the prompt.
-
Once you've logged into the browser application, launch a desktop app that accesses a Duo-protected application which shows the Duo Universal Prompt and has a remembered devices policy for all browser-based applications applied.
-
You're logged into the desktop application without repeating Duo two-factor authentication.
You won't have to repeat Duo 2FA again for the duration of the remembered devices session, unless you access an app that has an authentication methods policy applied which doesn't allow use of whichever Duo factor you used to create the remembered device session i.e. you created the session with Duo Push approval, and then access an app that only allows WebAuthn methods. In these scenarios you will need to perform Duo 2FA again, and you can establish a new trust session at that time.
Install Duo for Windows Logon
If you want to share Passport sessions between Windows, browsers, and desktop applications then you'll need to install Duo Authentication for Windows Logon on each Windows access device and make sure the application is subject to a remembered device policy that includes Windows Logon. If you did not already enable remembered devices for Windows Logon in a policy edit one to add that setting.
These steps describe assigning the policy you created earlier as a group policy to a pilot group for an existing Microsoft RDP application:
-
Log on to the Duo Admin Panel.
-
If you already have Duo for Windows Logon in use, look for your existing "Microsoft RDP" applications in the applications list.
-
Click on the Microsoft RDP application which you want to use with Passport to open its details page, and then scroll down to the "Policy" section of the page.
-
Click Apply a policy to groups of users and then select the policy you created with the remembered devices option set for browser applications.
For versions of Windows Logon 4.3.1 and earlier, be sure to also apply the policy that enables remembered devices for Windows Logon.
-
Use the Groups field to search for and select your Passport pilot group.
-
Click Apply Policy.
If you have no existing Microsoft RDP applications you'll have to create one.
Please follow the steps for installing Duo for Windows Logon 4.3.1 or later on your Windows devices in the Duo Authentication for Windows Logon and RDP installation instructions.
Verify Passport with Windows Logon
Test your Passport with Windows Logon configuration from a Windows device.
-
Log into a Windows system with Duo Authentication for Windows Logon and Duo Desktop installed.
-
Once you've logged into Windows, access a Duo-protected web application which shows the Duo Universal Prompt and has a remembered devices policy for all browser-based applications applied from a browser tab or desktop app.
-
You're logged into the browser or desktop application without repeating Duo two-factor authentication.
For versions of Windows Logon 4.3.1 and earlier, when you perform Duo authentication while logging into Windows be sure to create a remembered devices session by enabling the Remember me for... option in the prompt.
You won't have to repeat Duo 2FA again for the duration of the remembered devices session, unless you access an app that has an authentication methods policy applied which doesn't allow use of whichever Duo factor you used to create the remembered device session with Duo for Windows Logon. For example, browser-based apps that feature Duo Universal Prompt can use platform WebAuthn authenticators like Touch ID, but Duo Authentication for Windows Logon does not support platform authenticators today. If you use Duo Push or verified Duo Push to log in to Windows and then access an app that requires a platform authenticator you'll need to complete Duo authentication again.
Note that Risk-Based Factor Selection is considered a separate authentication method and will require the user to authenticate again after logging into Windows, even if the user is not in a stepped-up state.
Use Passport with Duo Single Sign-On Applications
Extend Passport to your Duo Single Sign-On (SSO) applications by applying policies that have remembered devices enabled for all web applications to your SAML and OIDC SSO applications, as well as Duo Central if you're using it. When you access these applications in a browser or desktop client application and create a remembered devices session when offered during Duo authentication, then SSO and non-SSO web applications accessed after that share the trust session and users do not need to repeat SSO login or Duo 2FA authentication.
Remembered device sessions established with Duo Authentication for Windows Logon sign users into Duo SSO applications without them entering their Duo Directory or Active Directory credentials. The Duo SSO session duration configured for Duo Directory or Active Directory authentication or the SSO session limit defined at an external SAML authentication source for SSO still applies.
Passport and Passwordless Authentication
SSO applications with Duo Passwordless enabled can also take advantage of Passport. When a user starts their day by performing Duo Passwordless login to a Duo SSO application and chooses to create a remembered device session during that initial authentication additional apps accessed from the browser as well as with desktop applications share that session and users do not need to authenticate again for the remainder of the remembered device session.
Passport and Passwordless for OS Logon
In the Windows Logon Beta version 4.3.16 and later, Passport supports Passwordless for Operating System (OS) Logon. If a user authenticates using Passwordless for OS Logon with Passport, applications protected by Duo Passwordless will not prompt the user to authenticate again for the duration of the remembered device session for browser-based applications. An authentication using Passwordless for OS Logon with Passport will allow users to access an app that requires Verified Duo Push without needing to complete Duo authentication again.
Passport Opt-Out
If a user ever wants to opt out of using Passport sessions between applications, they can turn it off in Duo Desktop's preferences:
-
Click the Duo Desktop in the macOS status bar or Windows system tray.
-
Click the menu icon and navigate to Preferences.
-
Toggle the Remember sessions in Duo Desktop option off.
Disable Passport on Individual Clients
You may wish to disable desktop sessions for certain client machines, like kiosk systems where multiple users share one OS logon (shared machines where each user logs on via separate profiles are compatible with Passport). You can disable Passport locally on these systems.
macOS
Disable Duo Passport sessions on macOS systems by creating a plist entry with the following command:
sudo /usr/libexec/PlistBuddy -c "add :DesktopSessionsDisabled bool true" /Library/Application\ Support/Duo/Duo\ Device\ Health/Config.plistTo reinstate Passport, use this command:
sudo /usr/libexec/PlistBuddy -c "delete :DesktopSessionsDisabled" /Library/Application\ Support/Duo/Duo\ Device\ Health/Config.plistWindows
Disable Duo Passport sessions on Windows systems by creating the string registry value HKLM\Software\Duo\Duo Device Health\AutoUpdater\desktop_sessions_disabled set to 1. Example reg command to create this value:
reg add "HKEY_LOCAL_MACHINE\Software\Duo\Duo Device Health" /v desktop_sessions_disabled /d 1 /fTo reinstate Passport, delete the previously created desktop_sessions_disabled registry value. Example reg command to delete this value:
reg delete "HKEY_LOCAL_MACHINE\Software\Duo\Duo Device Health" /v desktop_sessions_disabled /fTroubleshooting
Need some help? Take a look at our Passport Knowledge Base articles or Community discussions. For further assistance, contact Support.
See the Duo Knowledge Base article Guide to troubleshooting the Duo Passport error “Passport is not supported” in the Duo Authentication Log for more information about debugging common Passport errors.
