Duo Administration - Endpoints
Last updated:
Overview
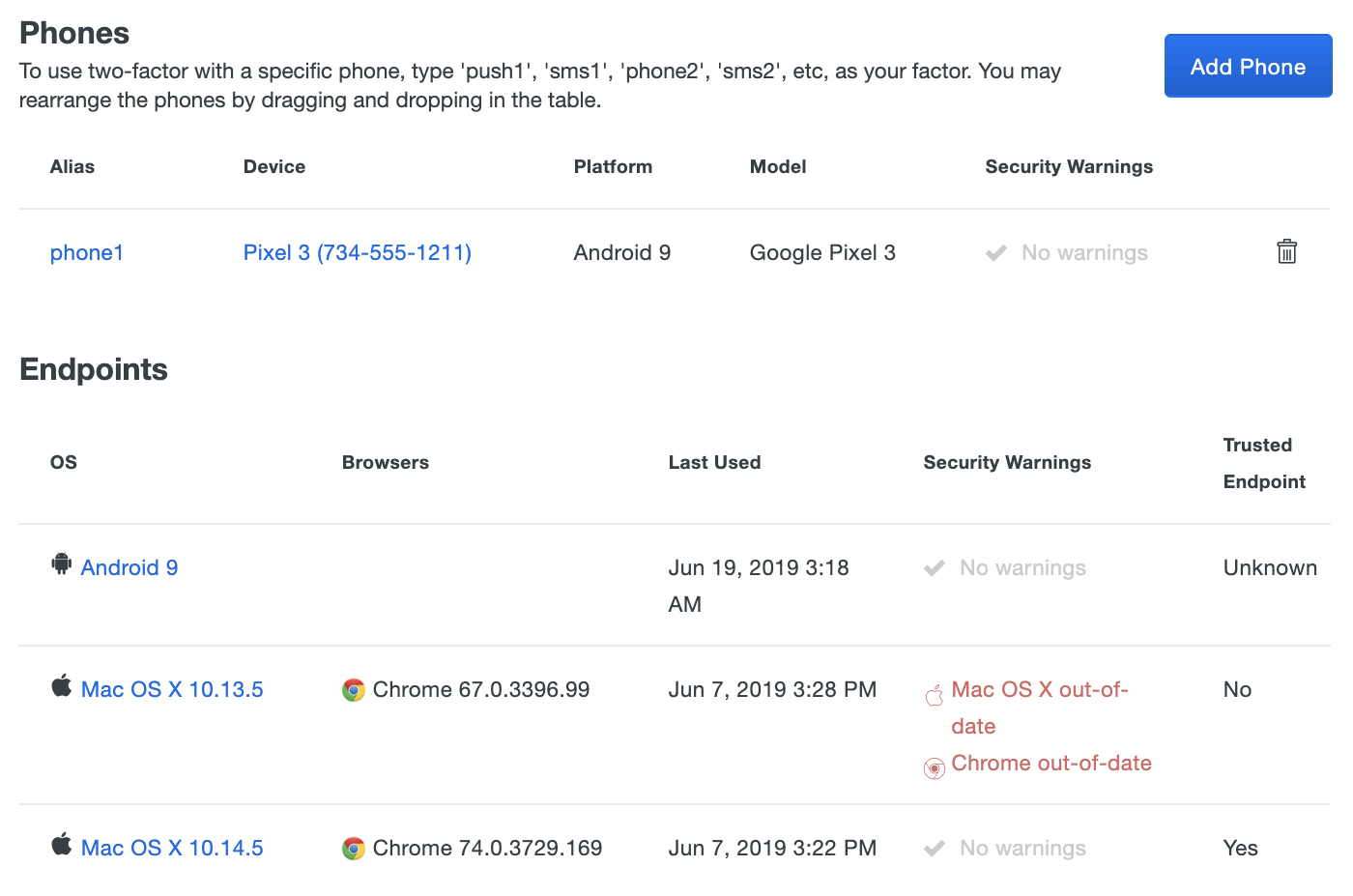
In Duo, Endpoints refers to the devices your end users use to interact with Duo. This includes both "access devices" (laptops, desktops, tablets, mobile phones, etc.) from which users access Duo-protected applications and services, and "MFA devices" (enrolled mobile devices and computers) where users receive and approve Duo authentication requests. Duo Premier and Advantage plan customers see information about the security status of your endpoints accessing your applications and approving application access by navigating to Devices → Endpoints in the Duo Admin Panel.
When users log in to protected apps with the web-based Duo Universal Prompt or traditional Duo Prompt, Duo gathers mobile device and computer operating system platform and versions, browser types and versions, and Java and Flash plugin versions if detected in the browser. Duo Premier and Advantage customers can view the Trusted Endpoints management status of a given endpoint from the Endpoints page and deny access to individual managed computer devices from that endpoint's details page.
Authentications from applications that do not show a web-based Duo prompt, like Duo Authentication for Windows Logon, do not populate the list of endpoints.
Information for a given endpoint is purged after 30 days of inactivity.
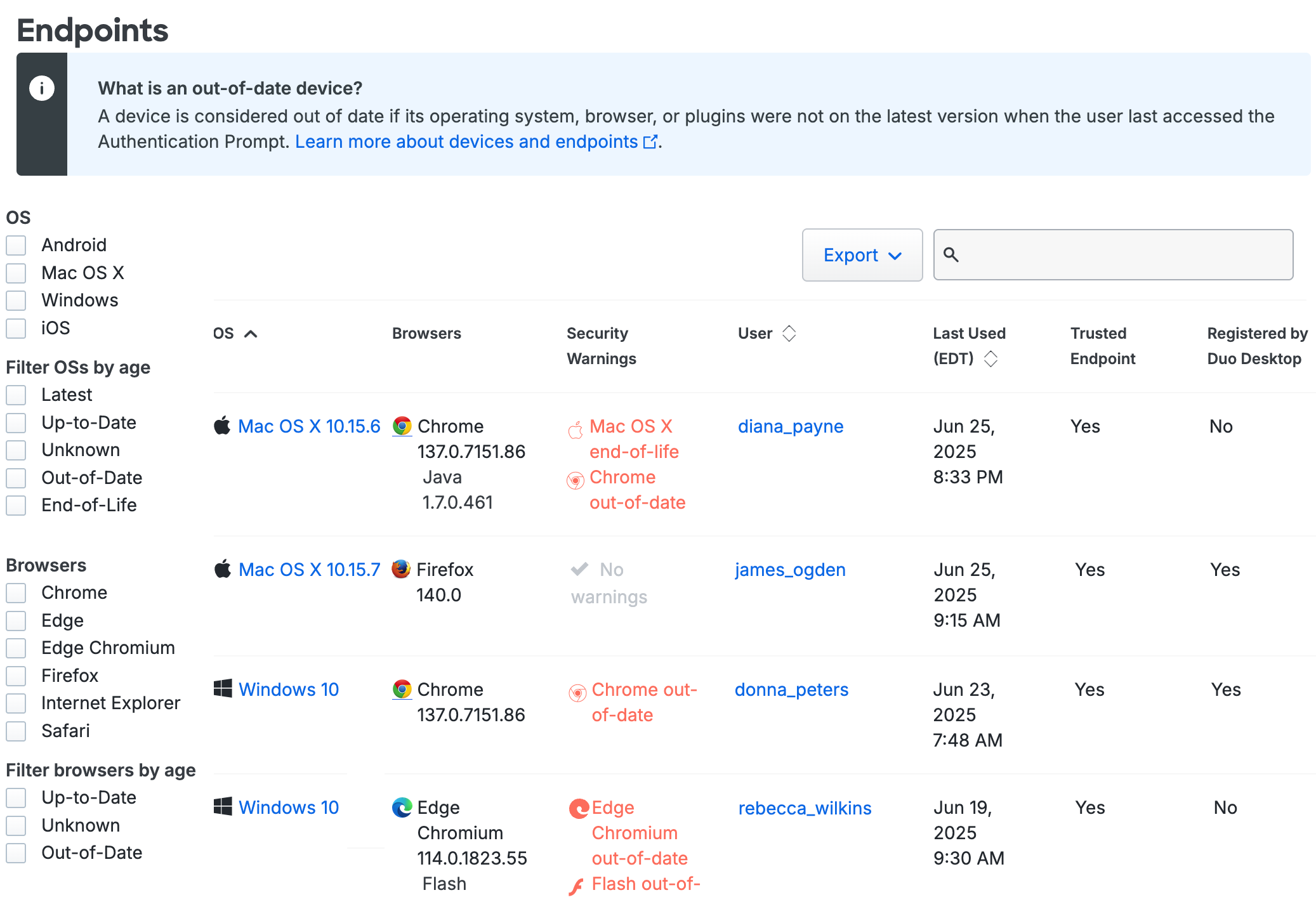
Filtering
You can filter the Endpoints list by selecting one of the filter options, such as operating system and version, browser type and version, installed plugins, Trusted Endpoint status, and more. For example, checking the boxes next to "Windows", "10", "Firefox", and "Java" on the left side of the Devices page then displays all PCs running Windows 10 that accessed your application using Firefox with the Java plugin enabled. Checking the Out of date filter option for browsers or plugins shows you all browsers and plugins not at the latest generally available version.
The "Trusted Endpoint" column shows the device's trust status: "Yes" if the endpoint passed Duo's managed system check, or "No" if it did not. "Unknown" status in the Trusted Endpoint column usually indicates that the endpoint hasn't been used to access the application that has the Trusted Endpoints policy yet.
The "Registered by Duo Desktop" column indicates whether the endpoint is a registered device.
Endpoint Details
Clicking on an endpoint's operating system takes you to that endpoint's details page. You can view which users have authenticated to Duo using that endpoint, as well as the operating system, browser, plugin, trusted endpoint and device registration status, device health information, and Duo Desktop authentication enrollment information.
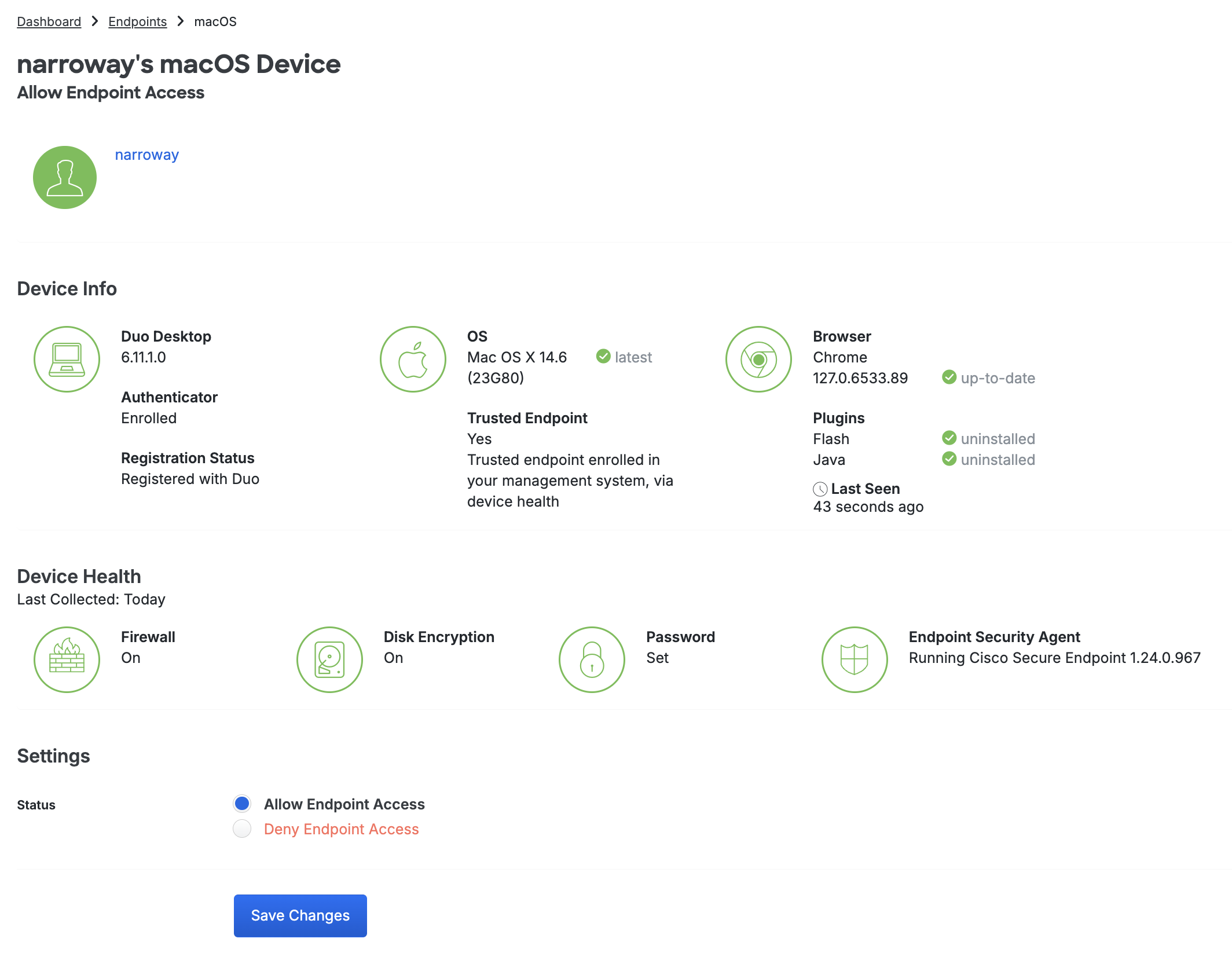
When the endpoint browsers and plugins are up to date, the various details are green. Information shown in red indicates a less secure status.
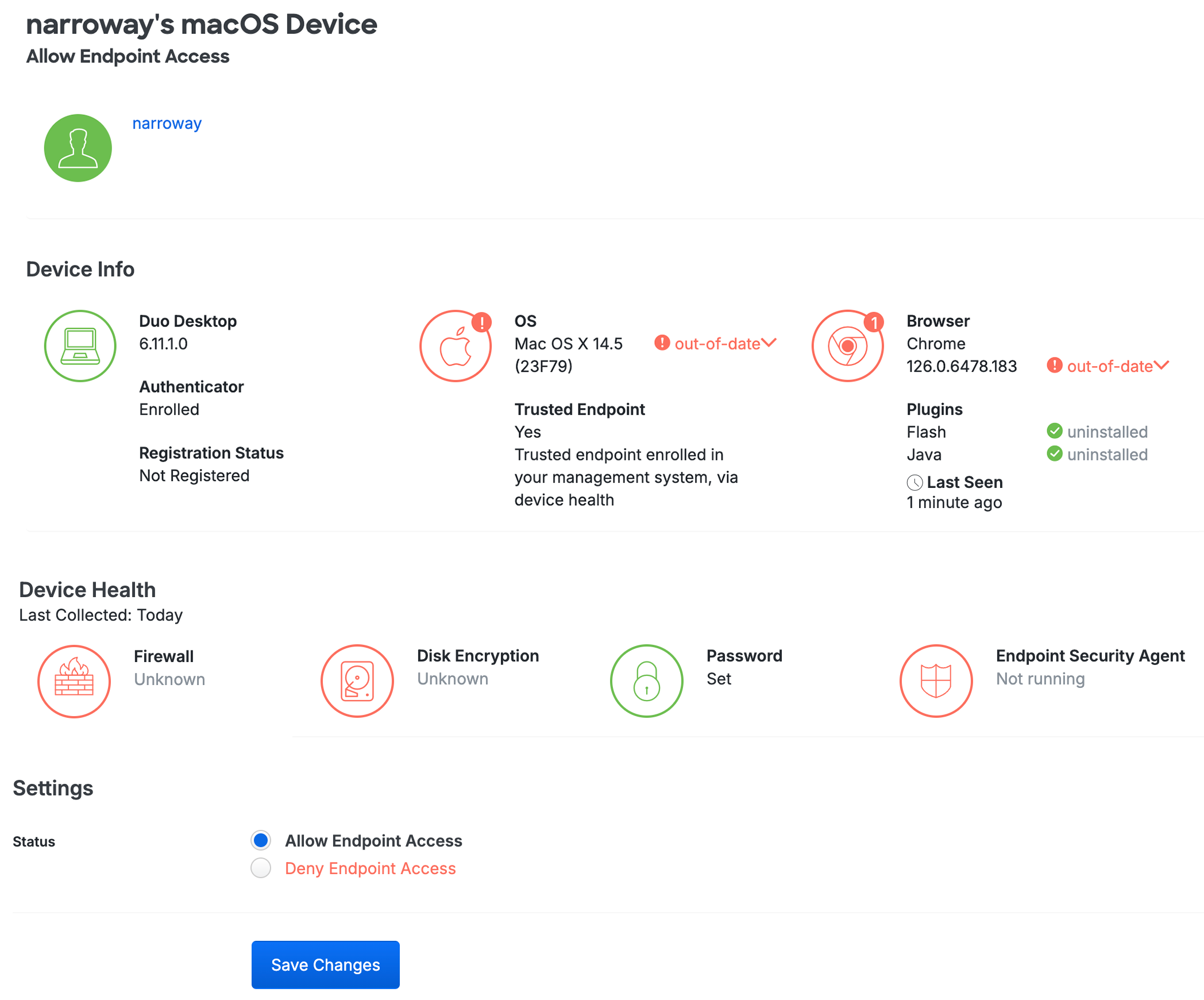
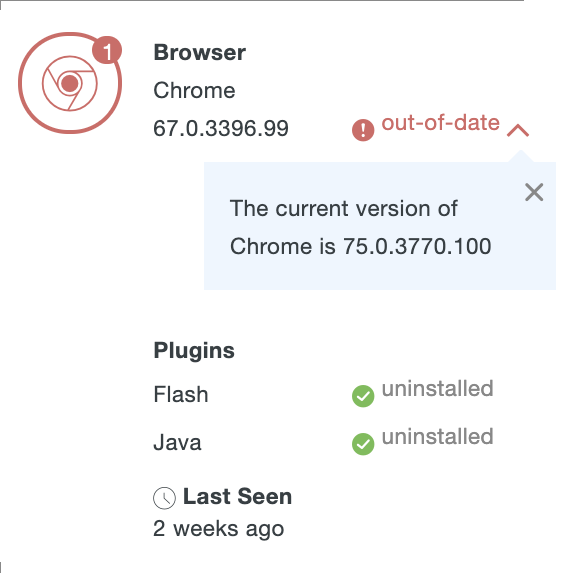
Click the out-of-date link to see the current version of the affected software.
Clicking on the username shown in the Endpoints table, or on the user tile on the endpoint's details page, takes you to the properties page for that user. Scroll down to the Phones and Endpoints tables to see platform, version, security warnings, trusted endpoint status, and other information about access and authentication endpoint devices associated with that user.
Access Control
Plan required: Duo Premier or Duo Advantage.
Use the Operating Systems, Browsers, Plugins, Duo Desktop, and Trusted Endpoints policy settings to restrict access and authentication from certain operating systems and versions, inform your users when their web browser or select plugins are out of date, verify the endpoint's security posture, and optionally block access to applications protected with Duo from unmanaged or insecure devices or devices with outdated software. Users authenticating via the Duo Prompt see notifications about any non-compliant properties of their endpoint. If you choose to block access to users based on endpoint policy settings, users are unable to complete authentication to access your applications.
Self-remediation notifications and access controls are available for the following:
- Operating Systems: Computer and mobile device platforms
- Select browsers
- Flash and Java plugins
- Firewall status
- Disk encryption
- System password set
- Select security agents
See the Policy & Control documentation for more information.
Deny Access to Endpoints
Role required: Owner, Administrator, User Manager, Security Analyst, or Help Desk.
Plan required: Duo Premier or Duo Advantage.
You can selectively block access to applications that have a Trusted Endpoints policy from individual managed computer endpoints. This is useful, for example, when a user loses their laptop and you want to make sure that it can't be used to log into applications unless it's recovered. Note that you may not deny access to applications for individual managed mobile endpoints.
To deny access to an individual computer endpoint, the Duo application's effective policy must be configured to block access from untrusted endpoints with the "Block endpoints that are not trusted" setting.
To deny access to an endpoint:
-
Log in to the Duo Admin Panel.
-
Navigate to Devices → Endpoints in the left sidebar and locate the trusted computer endpoint you want to block. Filter the list of devices by typing in the username associated with the endpoint to block in the filter box above the table.
You can also go to the Users page to locate the user account associated with the endpoint(s) to block. Click on the username to view their details page, and scroll down to the "Endpoints" section. Click on the endpoint to access its details page.
-
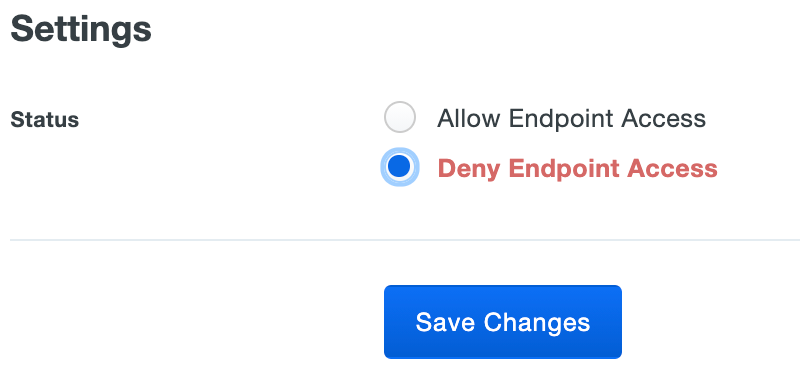
When viewing the trusted endpoint's details, scroll down to the "Settings" section.
-
Change the endpoint's status to Deny Endpoint Access and click Save Changes.
The endpoint's allow/deny status shows up at the top of the endpoint's details page.
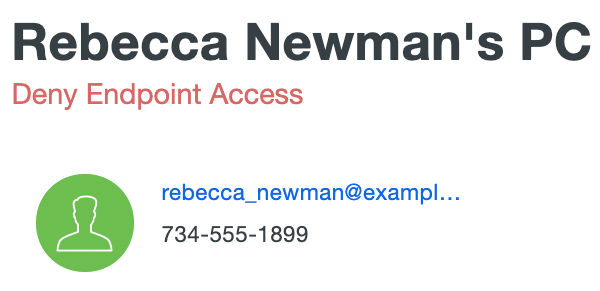
To permit access from that trusted endpoint again, revisit the details page for the endpoint, change the endpoint's status back to Allow Endpoint Access, and then click Save Changes.
Registered Devices
Role required: Owner, Administrator, Application Manager, User Manager, Security Analyst, or Help Desk.
Plan required: Duo Premier or Duo Advantage.
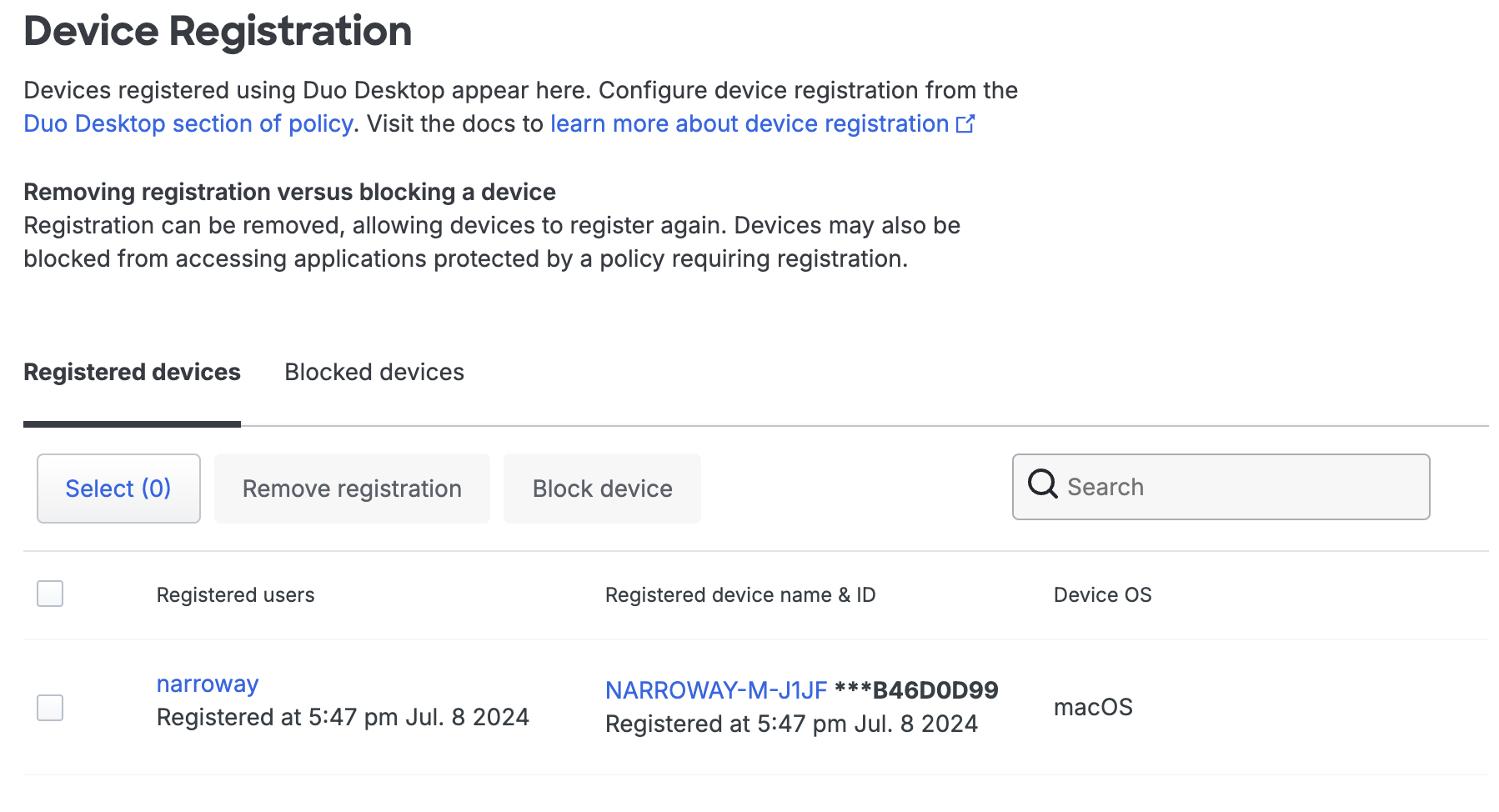
Use the tables on the "Device Registration" page to view and manage presently registered devices and their associated users. Information collected during the registration process from a device with the Trusted Platform Module (TPM) or Secure Enclave is formatted and displayed on this table.
Device registration requires the following:
- Active two-factor authentication through browser-based applications using the Universal Prompt.
- Device registration does not occur if the user bypasses two-factor authentication for any reason, such as access from a network permitted by the authorized networks policy setting, if the user has an existing remembered devices session, or bypass status set at the individual or group level.
- Windows and Linux access devices with Trusted Platform Module (TPM) 2.0 or Mac access devices with Secure Enclave.
- Duo Desktop 6.0.0/6.0.0.0 or later installed on Windows and macOS clients and Duo Desktop 3.0.0 or later installed on Linux clients.
- Enabling the Duo Desktop policy's Device registration option.
You can selectively remove devices. This helps resolve conflicts between a given device and outdated or incorrect registered device information.
Devices may also be blocked from accessing applications protected by a policy requiring registration. Associated users may still be able to access protected applications from other devices. Previously registered devices retain their original registration data.
On the Device Registration page in the Duo Admin Panel you can view tables with your "Registered devices" and "Blocked devices". From here you can choose to remove or block registered devices. If you haven’t enabled device registration in your Duo Desktop policy controls, the "Registered devices" table will be empty.
Remove Registered Devices
To remove registered devices:
-
Log in to the Duo Admin Panel.
-
Navigate to Devices → Duo Desktop Device Registration.
-
Select the device from the "Registered devices" table and click Remove registration. You can also use the search function to find devices by specifying any part of the device identifier or its description, as well as the username of any user registered with that device.
-
Click Remove registration to confirm. This removes the device and disassociates it from all users who had registered with Duo Desktop.
If a user logs in to a Duo-protected resource again from that endpoint, it will perform a new device registration (subject to the configured Duo Desktop device registration policy options).
Block Devices
To block devices:
-
Select one or more devices from the "Registered devices" table and click Block device.
-
Click Block devices to confirm. This will block the selected devices from accessing any applications protected by Duo policies that require device registration. Associated users may still be able to access protected applications from other devices. Previously registered devices retain their original registration data.
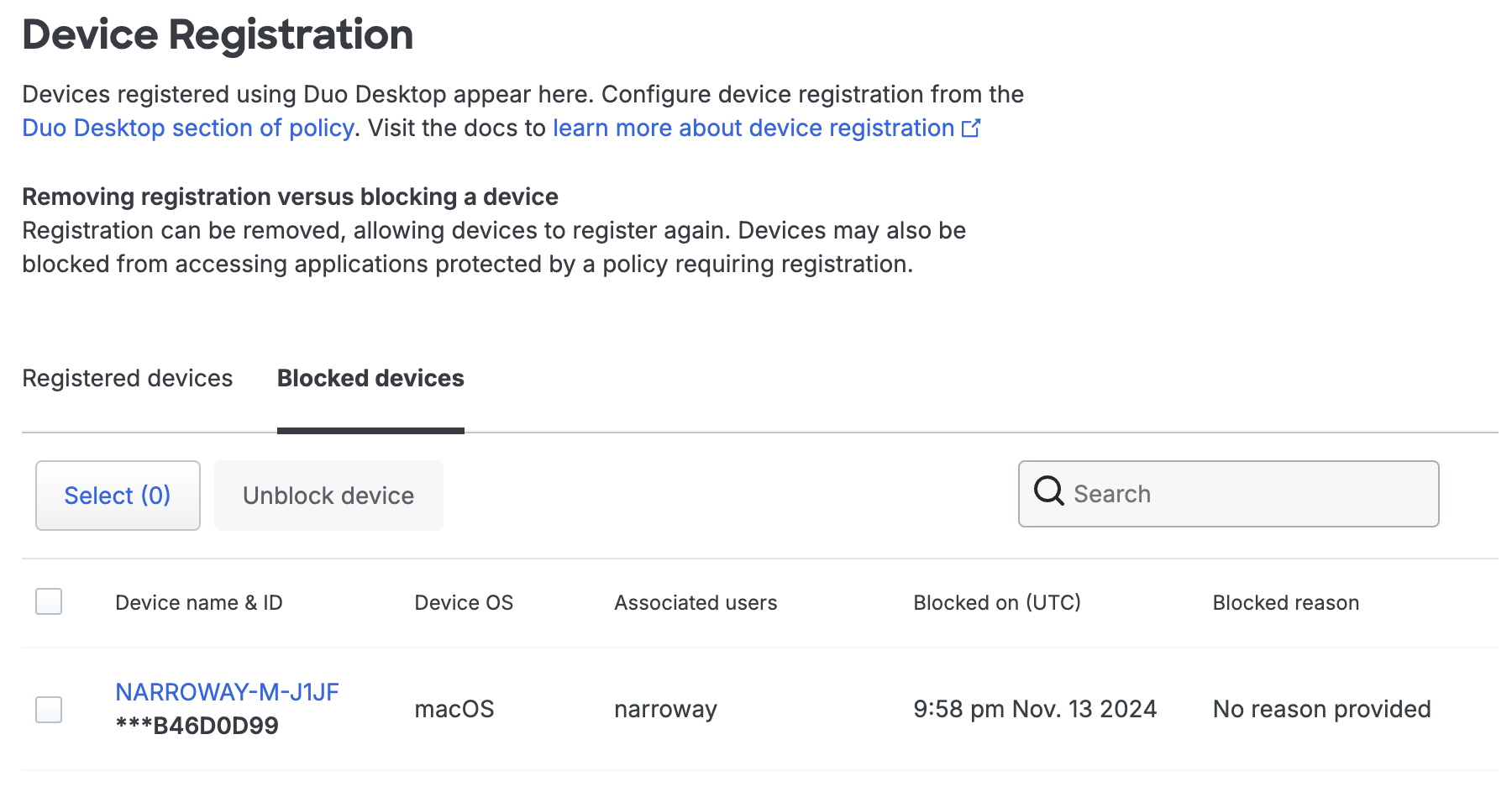
Unblock Devices
To unblock devices:
-
Select one or more devices from the "Blocked devices" table and click Unblock device.
-
Click Unblock devices to confirm. This will unblock the selected devices. Previously registered devices retain their original registration data.
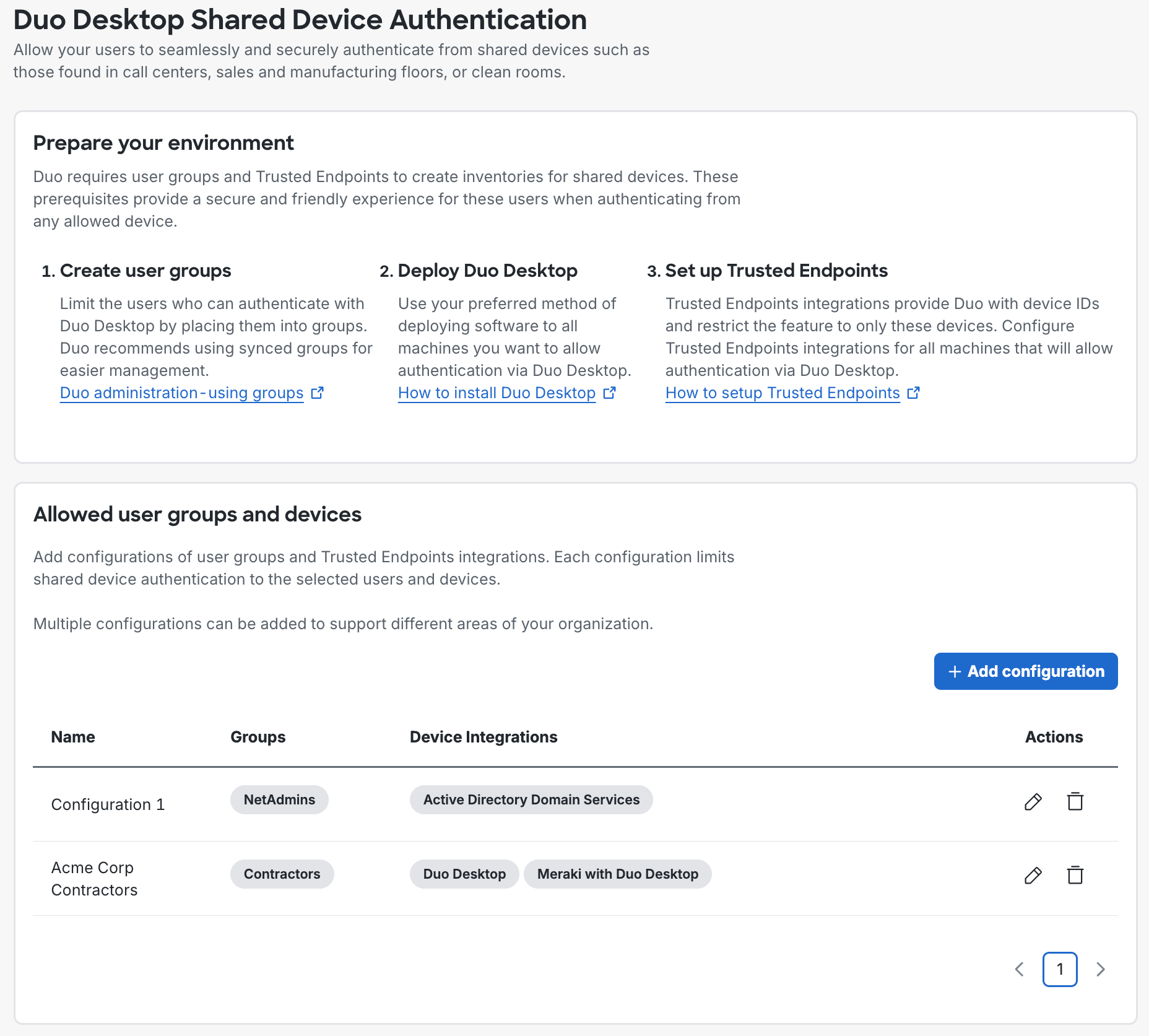
Shared Device Authentication
Shared device authentication eliminates repetitive Duo Desktop authentication setup for users without individual workstations. When enabled, designated users perform interactive authentication enrollment with Duo Desktop once from a trusted endpoint. Subsequent Duo Desktop authentication enrollments from additional computers happen silently.
In the Duo Admin Panel, navigate to Devices → Duo Desktop Shared Device Authentication to configure a user group and Trusted Endpoints integration for shared device authentication. See Shared Device Authentication for more information.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
