Evolving to “Security-First” IAM — without starting from scratch
“Comprehensive security should be built in or enabled by default” — a statement implored by Patrick Optet, CISO at JP Morgan Chase. In an open letter to their third-party providers, Optet points out an erosion of strong authentication and authorization practices as software providers prioritize speed of development over security.
Complexity is the reality for organizations of all sizes. With an ever-distributed supply chain and increasingly modern software demands, security controls expand to defend a new perimeter: identities, from trusted employees to partner external accounts to experimental AI agents. Change is hard and adds pressure on traditional systems that prevent organizations from moving forward with even the most obvious decisions, like taking a “security first” approach to identity and access management (IAM). It’s simply challenging to justify ripping out what’s in place and start over.
Change is hard and adds pressure on traditional systems that prevent organizations from moving forward
Check out our latest guide to security-first IAM to see how Duo is restoring trust in identity.
Cisco Duo aims to eliminate the performance and compliance tradeoffs that drive up the cost and complexity of other solutions—like gaps in visibility and strong authentication coverage. Evolving to security-first IAM should be easy. With roots in both deep security research and exceptional user experience, Duo makes world-class identity security available by default, not as an add-on. To level-set, here’s what business and IT leaders can expect to gain and how they can jumpstart the process to putting security first.
What does it mean to put security first in IAM?
Modern cybersecurity strategies know that identity is the new perimeter, but many traditional IAM solutions don’t adequately protect those identities with security until later. As a result, organizations are forced to seek incremental control layers to protect their core directory solution and stretch to cover their edge cases. Between additional budgets and deployment hours, that’s too late.
When companies treat security as an afterthought, adding important protections drives up the basic cost and complexity of IAM solutions exponentially with deployment, maintenance, and upgrades. Security-critical upgrades may slide to the back burner, or worse yet, never get done at all.
Ensuring MFA is truly everywhere
Security-minded organizations have rolled out multi-factor authentication (MFA) to validate and protect identities as users log into their desktops, single sign-on (SSO) portals, SaaS and online applications. That’s a great start but leaves business-critical legacy, custom and remote applications unprotected. Because converting those systems to work with other MFA solutions is a heavy lift, companies continue to—perhaps unknowingly—rely on incomplete protections.
69% of leaders are worried MFA isn’t deployed across all apps and devices.
2025 State of Identity Security Report
Duo gives businesses an easy, affordable way to protect all applications for all users against sophisticated phishing attacks out of the box with industry-leading MFA and SSO included by default.
Managing trust in users and devices
Even with SSO, threat actors continue to log—versus “hack”—their way into systems with leaked or stolen credentials. Duo gives organizations a reliable way to validate trust in devices as well as users.
From day one, Duo helps organizations control which devices get access to which resources in your environment whether managed or unmanaged. Duo Device Trust avoids risk by gathering health and security posture before allowing devices to connect to organizational resources. If an accessing device fails to meet health requirements, the request is blocked—and the user is prompted to self-remediate with step-by-step costs. Enforce baseline device health at the access management level, extending protections without device-level agents.
Charting a path to complete phishing-resistance
Remote identity-based attacks have learned to take advantage of push-based MFA with repeated, annoying push-bombing. Proximity verification that confirms the device being used to log in is in the same physical location as the system being accessed acts a strong defense against remote phishing attacks. But for many organizations, requiring hardware tokens.
Organizations can’t stop phishing attacks while still relying on passwords. Duo’s advanced, end-to-end phishing-resistance includes complete passwordless authentication—even for MFA enrollment, fallback, and on-the-fly help desk calls—to meet modern requirements and deadlines for protecting identities.
The good news: You can get there from here
Putting security first means recognizing the reality that security teams want to step up protections but have too few dollars in the budget, and not enough hours in the day. Duo makes it easier to make security first a top priority by overcoming the main objections: that the pain of making a change outweighs the business benefits.
Nothing could be farther from the truth, and IAM teams can prove it by phasing in security-first IAM in three powerful use cases:
1. Make new users secure from the get-go
With the addition of powerful user directory capabilities and deployable end-to-end phishing-resistance, Duo creates “security-first” IAM that achieves forward-looking identity security at enrollment.
Duo offers the broadest possible MFA coverage with flexible options for every user, and no exceptions. Use Duo to quickly achieve 100% MFA, SSO, and device trust coverage and meet the needs of “edge” cases like first responders in healthcare and seasonal workers in retail. Duo works with legacy and custom applications adding visibility and protections that strengthen security and compliance quickly. With hundreds of integrations out-of-the-box, Duo delivers on speed to security that ensures your bases are covered for audits, compliance, and insurance.
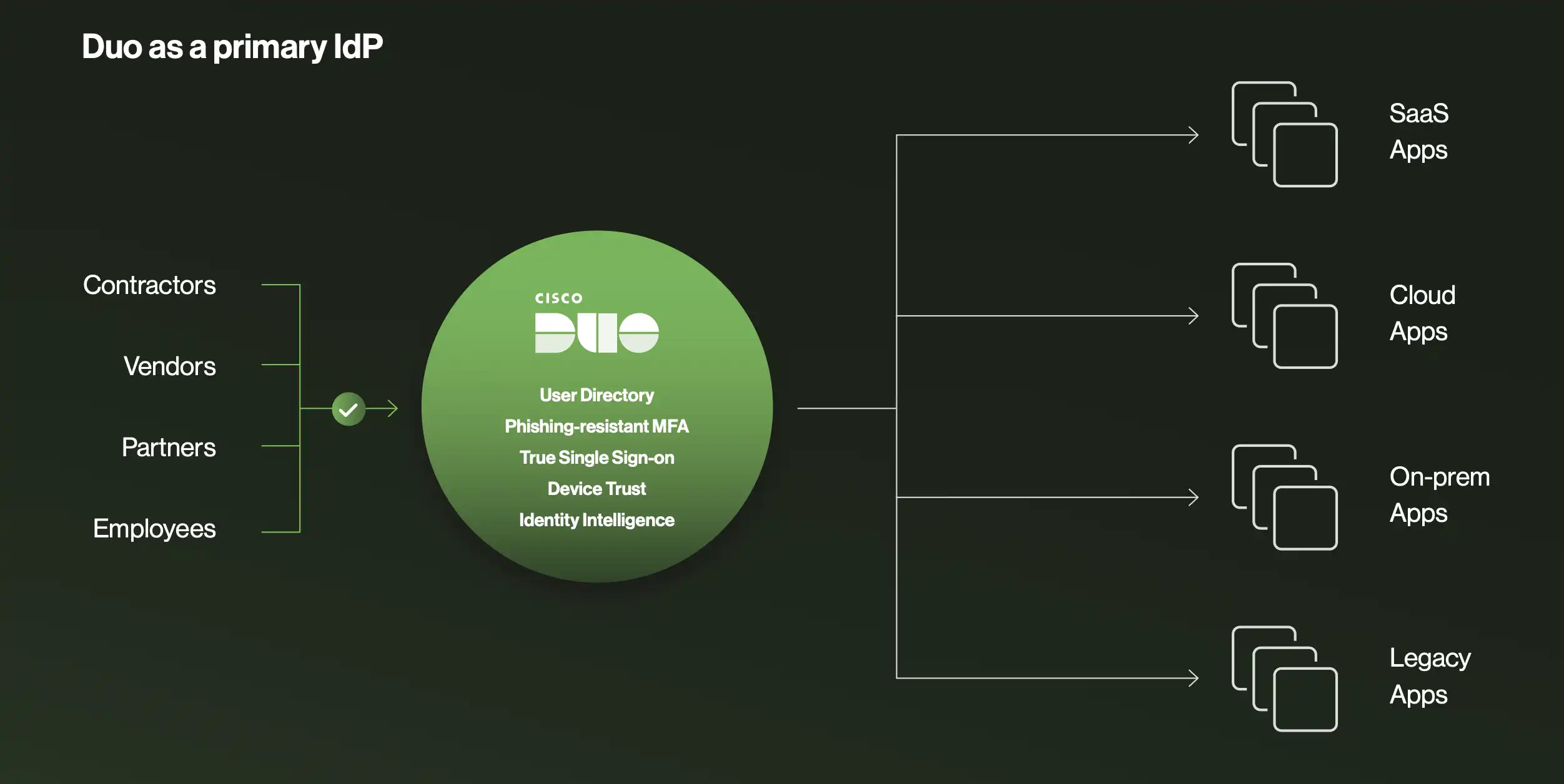
2. Bridge the gaps left by other solutions
Accelerate workforce consolidation during mergers and acquisitions (M&A) and other strategic initiatives using Duo’s IdP and routing rules capabilities to broker between them. Over time, Duo Directory streamlines the transition to a single identity provider (IdP) to centralize and unify operations or makes it easy and affordable to manage multiple directories seamlessly for as long as IT chooses.
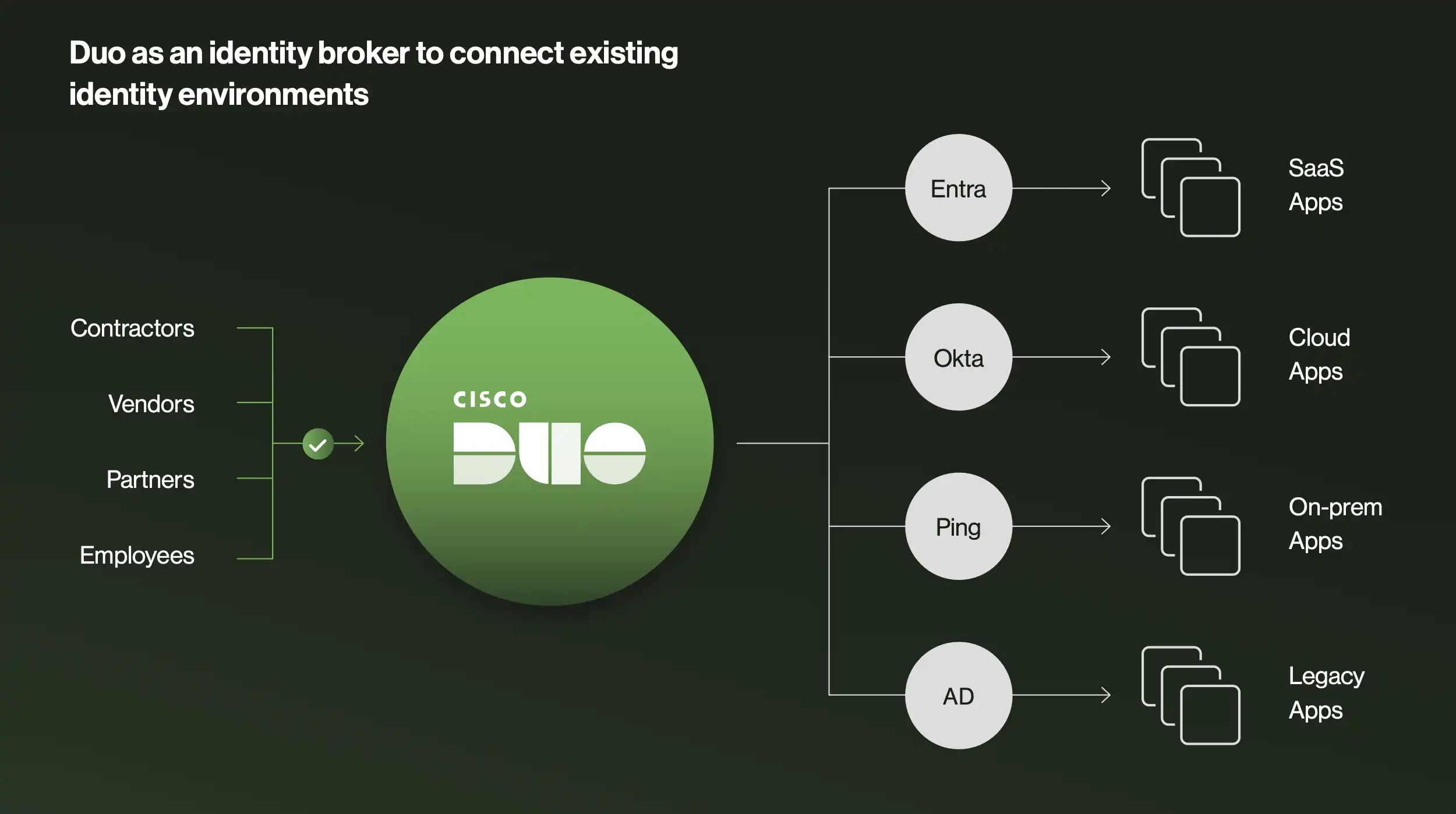
A key part of Cisco’s broader cybersecurity solutions, Duo leverages Cisco Identity Intelligence (CII) to streamline detection, response, forensics and reporting on identity-led attacks. Identity security posture management (ISPM) is another key function that helps make self-auditing habits easier. Identity Posture Scoring in CII detects gaps across your entire identity ecosystem and provides prioritized, actionable recommendations to help you effortlessly identify and address gaps in your organization's identity security hygiene. For example, see your distribution of enabled MFA methods or pull a list of identities that are dormant, shared, or missing from HR systems. Take the ISPM product tour.
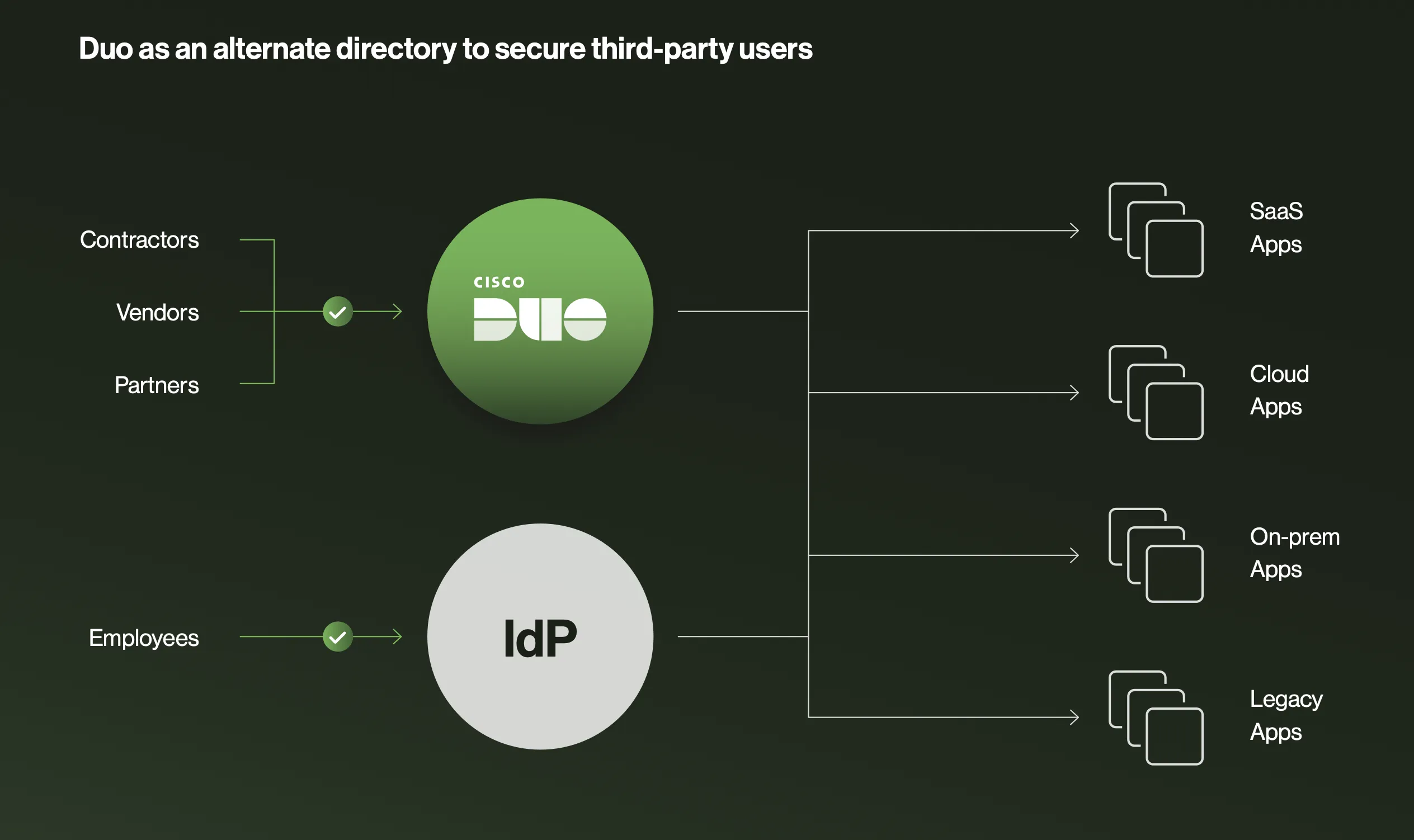
3. Manage third-party risk with a parallel directory
According to Verizon’s 2025 Data Breach Investigations Report, 30% of all breaches involve a third party. To minimize risks originating in your supply chain, manage vendor, customer and other third-party identities in a separate Duo Directory that comes with MFA and device trust out-of-the-box. A modern, secure storage for external identities, Duo gives admins visibility into whether devices are managed or unmanaged and applies the same security checks to third-party devices before allowing them to connect.
Duo prioritizes security first in IAM to keep your organizations safe
Solutions that demand full rip-and-replace fail to recognize the complex nature of identity in modern organizations. Hidden fees, from incremental feature upgrades to operational costs, add up for already-stretched IT teams.
Customers should be afforded the benefit of secure by default configurations, transparency to risks, and management of the controls they need to operate safely within a SaaS delivery model.
Patrick Opet
Chief Information Security Officer, JPMorganChase
Duo believes that securing IAM should not be an afterthought but a default. That translates into stronger protections against modern threats, better, faster performance with less friction for users, and an administrative experience built for IT teams to deploy, manage, and grow with ease.
See how Duo is restoring trust in identity with our latest guide to security-first IAM.

